命名性访问控制列表的配置实验
Posted
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了命名性访问控制列表的配置实验相关的知识,希望对你有一定的参考价值。
命名性访问控制列表的配置:创建ACL:
语法:
Router(config)# ip access-list { standard | extended }access-list-name配置标准命名ACL:
语法:
Router(config-std-nac)# [ Sequence-Number ] { permit | deny }source[ source-wildcard ]配置扩展命名ACL:
语法:router(config-ext-nacl)# [ Sequence-Number ] { permit | deny } protocol { source source-wildcard destination destionation-wildcard } [operator operan]标准命名ACL应用实例:
router(config)#ip access-list standard cisco
router(config-std-nacl)# permit host 192.168.1.1
router(config-std-nac)# deny any
//只允许来自主机192.168.1.1/24的流量通过查看ACL配置信息:
router#show access-list
Standard IP access list cisco
10 permit 192.168.1.1
20 deny anyDemo:
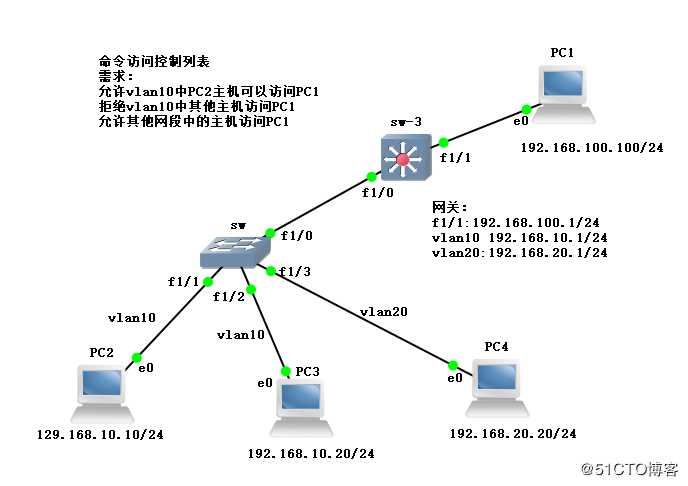
sw:
sw#conf t
sw(config)#vlan 10,20
sw(config-vlan)#ex
sw(config)#do show vlan-sw b
VLAN Name Status Ports
---- -------------------------------- --------- -------------------------------
1 default active Fa1/0, Fa1/1, Fa1/2, Fa1/3
Fa1/4, Fa1/5, Fa1/6, Fa1/7
Fa1/8, Fa1/9, Fa1/10, Fa1/11
Fa1/12, Fa1/13, Fa1/14, Fa1/15
10 VLAN0010 active
20 VLAN0020 active
1002 fddi-default act/unsup
1003 token-ring-default act/unsup
1004 fddinet-default act/unsup
1005 trnet-default act/unsup
sw(config)#int f1/3
sw(config-if)#sw mo acc
sw(config-if)#sw acc vlan 20
sw(config-if)#ex
sw(config)#do show vlan-sw b
VLAN Name Status Ports
---- -------------------------------- --------- -------------------------------
1 default active Fa1/0, Fa1/4, Fa1/5, Fa1/6
Fa1/7, Fa1/8, Fa1/9, Fa1/10
Fa1/11, Fa1/12, Fa1/13, Fa1/14
Fa1/15
10 VLAN0010 active Fa1/1, Fa1/2
20 VLAN0020 active Fa1/3
1002 fddi-default act/unsup
1003 token-ring-default act/unsup
1004 fddinet-default act/unsup
1005 trnet-default act/unsup
sw(config)#int f1/0
sw(config-if)#sw mo t
sw(config-if)#sw t en dot
sw(config-if)#ex
sw(config)#no ip routing //关闭路由功能SW3:
sw-3#conf t
sw-3(config)#int f1/1
sw-3(config-if)#no switchport
sw-3(config-if)#ip add 192.168.100.1 255.255.255.0
sw-3(config-if)#no shut
sw-3(config-if)#do show ip int b
Interface IP-Address OK? Method Status Protocol
FastEthernet0/0 unassigned YES unset administratively down down
FastEthernet0/1 unassigned YES unset administratively down down
FastEthernet1/0 unassigned YES unset up up
FastEthernet1/1 192.168.100.1 YES manual up up
FastEthernet1/2 unassigned YES unset up down
FastEthernet1/3 unassigned YES unset up down
FastEthernet1/4 unassigned YES unset up down
FastEthernet1/5 unassigned YES unset up down
FastEthernet1/6 unassigned YES unset up down
FastEthernet1/7 unassigned YES unset up down
FastEthernet1/8 unassigned YES unset up down
FastEthernet1/9 unassigned YES unset up down
FastEthernet1/10 unassigned YES unset up down
FastEthernet1/11 unassigned YES unset up down
FastEthernet1/12 unassigned YES unset up down
FastEthernet1/13 unassigned YES unset up down
FastEthernet1/14 unassigned YES unset up down
FastEthernet1/15 unassigned YES unset up down
Vlan1 unassigned YES unset up up
sw-3(config-if)#ex
sw-3(config)#vlan 10,20
sw-3(config-vlan)#int vlan 10
sw-3(config-if)#ip add 192.168.10.1 255.255.255.0
sw-3(config-if)#no shut
sw-3(config-if)#ex
sw-3(config)#int vlan 20
sw-3(config-if)#ip add 192.168.20.1 255.255.255.0
sw-3(config-if)#no shut
sw-3(config-if)#ex
sw-3(config)#int f1/0
sw-3(config-if)#sw mo t
sw-3(config-if)#sw t en dot
sw-3(config-if)#do shoe ip route
Codes: C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route
Gateway of last resort is not set
C 192.168.10.0/24 is directly connected, Vlan10
C 192.168.20.0/24 is directly connected, Vlan20
C 192.168.100.0/24 is directly connected, FastEthernet1/1
//三个网段配置成功
sw-3(config-if)#ex四台主机配置IP地址:
PC1:
PC1> ip 192.168.100.100 192.168.100.1
Checking for duplicate address...
PC1 : 192.168.100.100 255.255.255.0 gateway 192.168.100.1
PC2:
PC2> ip 192.168.10.10 192.168.10.1
Checking for duplicate address...
PC1 : 192.168.10.10 255.255.255.0 gateway 192.168.10.1
PC3:
PC3> ip 192.168.10.20 192.168.10.1
Checking for duplicate address...
PC1 : 192.168.10.20 255.255.255.0 gateway 192.168.10.1
PC4:
PC4> ip 192.168.20.20 192.168.20.1
Checking for duplicate address...
PC1 : 192.168.20.20 255.255.255.0 gateway 192.168.20.1此时PC2应该是全网互通的:
验证全网互通:
PC2> ping 192.168.100.100
192.168.100.100 icmp_seq=1 timeout
84 bytes from 192.168.100.100 icmp_seq=2 ttl=63 time=35.971 ms
84 bytes from 192.168.100.100 icmp_seq=3 ttl=63 time=41.517 ms
84 bytes from 192.168.100.100 icmp_seq=4 ttl=63 time=31.738 ms
84 bytes from 192.168.100.100 icmp_seq=5 ttl=63 time=35.188 ms
PC2>ping 192.168.10.20
84 bytes from 192.168.10.20 icmp_seq=1 ttl=64 time=0.505 ms
84 bytes from 192.168.10.20 icmp_seq=2 ttl=64 time=0.000 ms
84 bytes from 192.168.10.20 icmp_seq=3 ttl=64 time=0.000 ms
84 bytes from 192.168.10.20 icmp_seq=4 ttl=64 time=0.000 ms
84 bytes from 192.168.10.20 icmp_seq=5 ttl=64 time=0.000 ms
PC2> ping 192.168.20.20
192.168.20.20 icmp_seq=1 timeout
84 bytes from 192.168.20.20 icmp_seq=2 ttl=63 time=31.229 ms
84 bytes from 192.168.20.20 icmp_seq=3 ttl=63 time=37.597 ms
84 bytes from 192.168.20.20 icmp_seq=4 ttl=63 time=31.007 ms
84 bytes from 192.168.20.20 icmp_seq=5 ttl=63 time=40.123 ms注入命令访问控制列表规则:
sw-3(config)#ip access-list standard kgc
sw-3(config-std-nacl)#permit host 192.168.10.10
sw-3(config-std-nacl)#deny 192.168.10.0 0.0.0.255
sw-3(config-std-nacl)#permit any
sw-3(config-std-nacl)#ex
sw-3(config)#do show access-list
Standard IP access list kgc
10 permit 192.168.10.10
20 deny 192.168.10.0, wildcard bits 0.0.0.255
30 permit any
sw-3(config)#int f1/1
sw-3(config-if)#ip access-group kgc out //策略应用在网关此时联通结果如下:
PC2可以访问:
PC2> ping 192.168.100.100
192.168.100.100 icmp_seq=1 timeout
192.168.100.100 icmp_seq=2 timeout
84 bytes from 192.168.100.100 icmp_seq=3 ttl=63 time=35.353 ms
84 bytes from 192.168.100.100 icmp_seq=4 ttl=63 time=31.321 ms
84 bytes from 192.168.100.100 icmp_seq=5 ttl=63 time=31.239 msPC4可以访问:
PC4> ping 192.168.100.100
84 bytes from 192.168.100.100 icmp_seq=1 ttl=63 time=32.766 ms
84 bytes from 192.168.100.100 icmp_seq=2 ttl=63 time=31.240 ms
84 bytes from 192.168.100.100 icmp_seq=3 ttl=63 time=31.244 ms
84 bytes from 192.168.100.100 icmp_seq=4 ttl=63 time=31.329 ms
84 bytes from 192.168.100.100 icmp_seq=5 ttl=63 time=31.067 msPC3显示被拒绝:
PC3> ping 192.168.100.100
*192.168.10.1 icmp_seq=1 ttl=255 time=30.919 ms (ICMP type:3, code:13, Communication administratively prohibited)
*192.168.10.1 icmp_seq=2 ttl=255 time=16.133 ms (ICMP type:3, code:13, Communication administratively prohibited)
*192.168.10.1 icmp_seq=3 ttl=255 time=31.012 ms (ICMP type:3, code:13, Communication administratively prohibited)
*192.168.10.1 icmp_seq=4 ttl=255 time=22.354 ms (ICMP type:3, code:13, Communication administratively prohibited)
*192.168.10.1 icmp_seq=5 ttl=255 time=15.630 ms (ICMP type:3, code:13, Communication administratively prohibited)以上是关于命名性访问控制列表的配置实验的主要内容,如果未能解决你的问题,请参考以下文章