devops===》Jenkins(pipeline)+gitlab+sonar代码扫描漏洞扫描
Posted 一夜暴富--gogogo
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了devops===》Jenkins(pipeline)+gitlab+sonar代码扫描漏洞扫描相关的知识,希望对你有一定的参考价值。
一、sonar基本概念及使用
Sonarqube是一个开源的代码质量检测工具,可以单独使用,也可以作为一个检测步骤放在Jenkins的pipeline CI/CD 流水线。简单的理解,他通过一个snarqube scanner 的工具来扫描代码,然后把结果发给 sonarqube server,用户可以在这个sonarqube server的网页界面查看报告。
当我们把Jenkins和 sonarqube整合的时候,Jenkins调用 sonarqube scanner 扫描,把结果发送给sonarqube 服务器,然后服务器完成报告之后,通过 webhook再把结果发过Jenkins,Jenkins根据结果判断是否继续运行pipeline
1.sonar创建webhooks
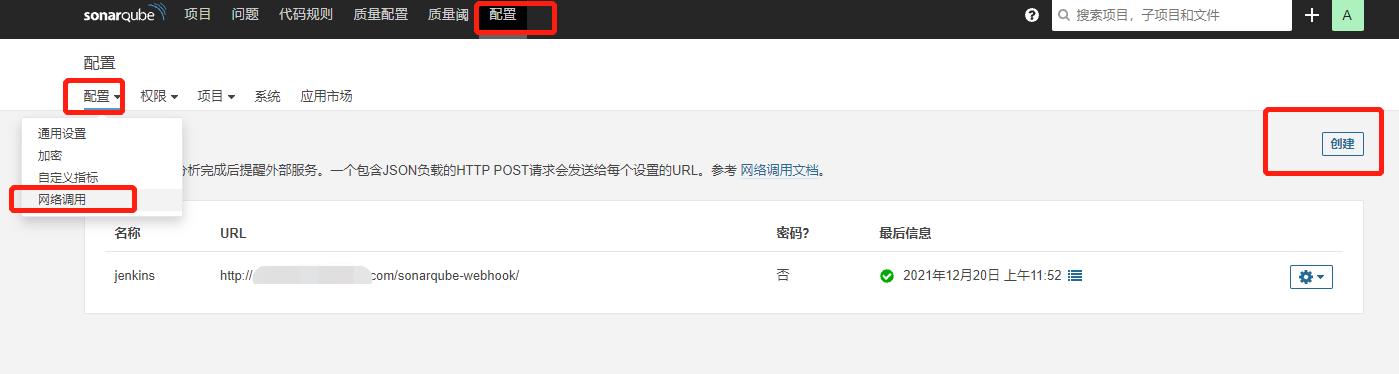
url填写jenkins的地址:http://jenkinsurl/sonarqube-webhook/(密码可不填)

2.Jenkins的pipeline
以Java代码为例(两种方法)
#1.第一种方法:在gitlab代码目录下上传sonar-project.properties文件,内容如下:
# must be unique in a given SonarQube instance
sonar.projectKey=test
# this is the name and version displayed in the SonarQube UI. Was mandatory prior to SonarQube 6.1.
sonar.projectName=test
sonar.projectVersion=0.0.1
# Path is relative to the sonar-project.properties file. Replace "\\" by "/" on Windows.
# This property is optional if sonar.modules is set.
sonar.sources=.
sonar.exclusions=**/test/**,**/target/**
sonar.java.source=1.8
sonar.java.target=1.8
# Encoding of the source code. Default is default system encoding
sonar.sourceEncoding=UTF-8
#####pipeline:
pipeline
agent any
parameters
gitParameter branchFilter: 'origin/(.*)', defaultValue: 'master', name: 'BRANCH', type: 'PT_BRANCH'
string defaultValue: 'mvn clean package -U', description: '打包命令', name: 'mvnArgs', trim: false
tools
maven 'MAVEN'
jdk 'JDK'
nodejs 'NODEJS'
stages
stage('pull')
steps
cleanWs()
checkout([$class: 'GitSCM', branches: [[name: "$params.BRANCH"]], doGenerateSubmoduleConfigurations: false, extensions: [], submoduleCfg: [], userRemoteConfigs: [[credentialsId: '0-4a15-b78d-708e01dfcc07', url: "ssh://git仓库地址"]]])
stage('SonarQubeanalysis') #代码扫描
steps
script
scannerHome = tool 'sonarscanner' #与Jenkins全局变量设置里名称一致
withSonarQubeEnv('sonarqube') #与Jenkins系统设置里name一致
sh "$scannerHome/bin/sonar-scanner -Dsonar.java.binaries=. -Dsonar.sources=."
stage("Quality Gate")
steps
script
sleep(10) //这里遇到一个坑 返回状态出现阻塞现象 加sleep 后正常
timeout(15)
//利用sonar webhook功能通知pipeline代码检测结果,未通过质量阈,pipeline将会fail
def qg = waitForQualityGate()
if (qg.status != 'OK')
error "未通过Sonarqube的代码质量阈检查,请及时修改!failure: $qg.status"
bearychatSend message:"Jenkins发布项目 $env.JOB_NAME 第$env.BUILD_NUMBER,代码静态检测结果:未通过:$qg.status",webhook: "$bearychat_url"
stage('MVN')
steps
sh "$params.mvnArgs"
#2.第二种方法(直接编写pipeline不用定义sonar-project.properties文件,所需参数通过-D指定):
def createVersion()
return new Date().format('yyyyMMddHHmmss')
pipeline
agent any
environment
_version = createVersion()
parameters
gitParameter branchFilter: 'origin/(.*)', defaultValue: 'master', name: 'BRANCH', type: 'PT_BRANCH'
string defaultValue: 'mvn clean package', description: '打包命令', name: 'mvnArgs', trim: false
tools
maven 'MAVEN'
jdk 'JDK'
nodejs 'NODEJS'
stages
stage('pull')
steps
cleanWs()
checkout([$class: 'GitSCM', branches: [[name: "$params.BRANCH"]], doGenerateSubmoduleConfigurations: false, extensions: [], submoduleCfg: [], userRemoteConfigs: [[credentialsId: '07-4a15-b78d-708e01d07', url: "ssh://git仓库地址"]]])
stage('SonarQubeanalysis')
steps
script
scannerHome = tool 'sonarscanner'
withSonarQubeEnv('sonarqube')
sh "$scannerHome/bin/sonar-scanner -Dsonar.projectKey=devops-iov-base -Dsonar.projectVersion=$_version -Dsonar.projectName=devops-iov-base -Dsonar.java.binaries=. -Dsonar.sources=."
stage("Quality Gate")
steps
timeout(time: 1, unit: 'HOURS')
sleep (10)
waitForQualityGate abortPipeline: true
stage('MVN')
steps
sh "$params.mvnArgs"
stage('docker-build')
steps
script
env.COMMIT= sh(returnStdout: true, script: 'git rev-parse --short HEAD').trim()
sh """
#!/bin/bash
echo $COMMIT
echo $_version
docker login test.com --username 123456 --password eyJhbGciOiJSUzI1NiIsImtpZCI6IlZVRFM6
docker build --build-arg test -t test.com/test/test:$params.BRANCH-$COMMIT-$_version .
docker push test.com/test/test:$params.BRANCH-$COMMIT-$_version
docker rmi test.com/test/test:$params.BRANCH-$COMMIT-$_version
"""
stage('docker-deploy')
steps
script
env.COMMIT= sh(returnStdout: true, script: 'git rev-parse --short HEAD').trim()
sh """
#!/bin/bash
echo $COMMIT
echo $_version
cp /data/jenkins/deploy/devops/service-deploy.sh .
cp /data/jenkins/deploy/devops/test.yml .
sed -i 's/:5.0_beta/:'$params.BRANCH-$COMMIT-$_version'/' test.yml
sed -i "/sleep 2/i docker pull test.com/test/test:$params.BRANCH-$COMMIT-$_version" service-deploy.sh
scp -P 22 service-deploy.sh root@172.17.1:/data/ota-deploy/scripts
scp -P 22 test.yml root@172.17:/data/ota-deploy/scripts
ssh -p 22 -tt root@172.17 << remotessh
cd /data/ota-deploy/scripts
sh service-deploy.sh iov-base
exit
remotessh
"""
构建成功后会在sonar的web的界面生成项目,也可在Jenkins上查看
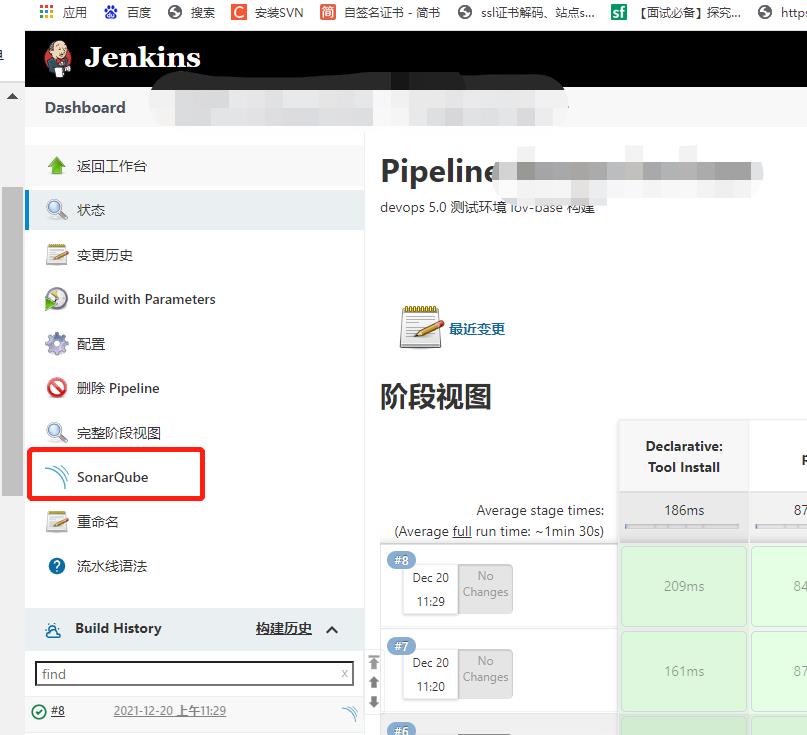
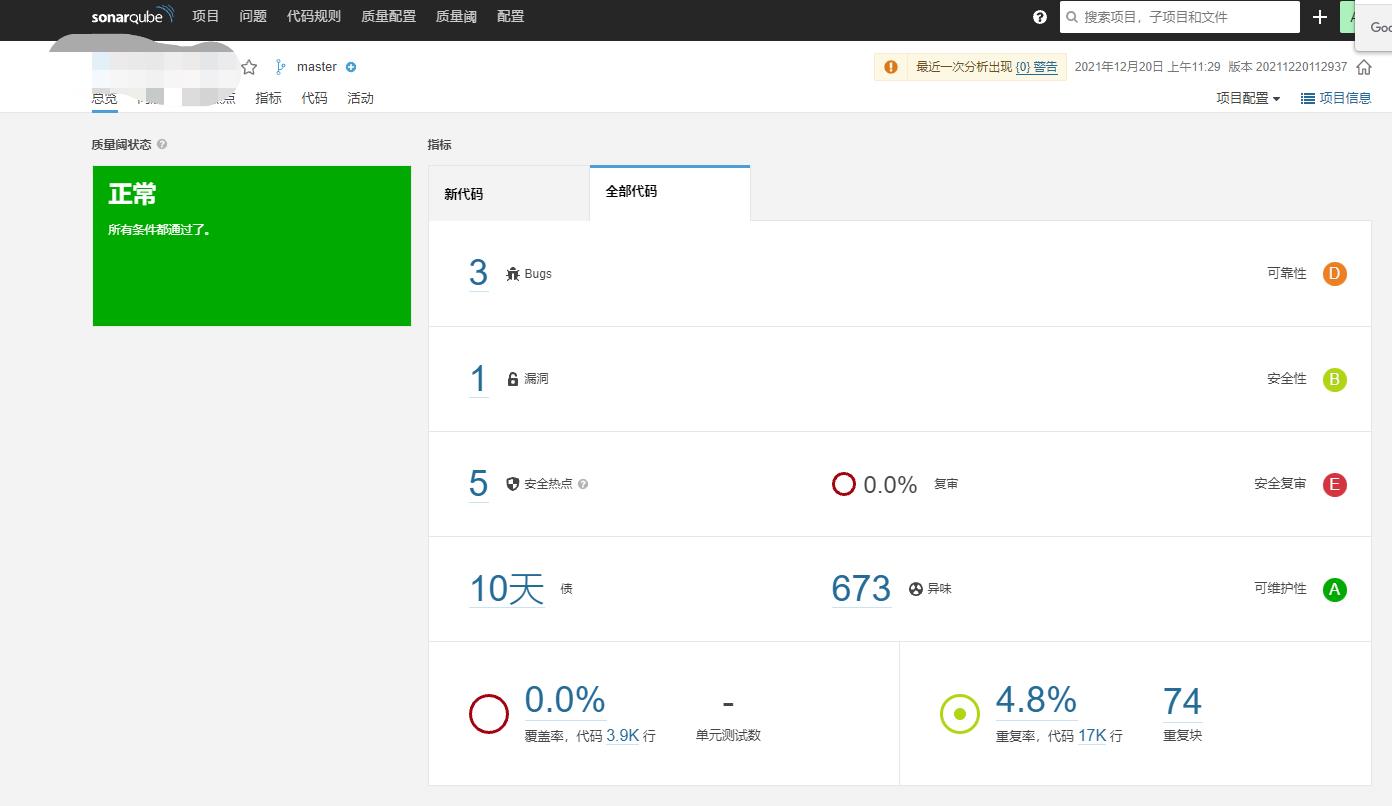
以上是关于devops===》Jenkins(pipeline)+gitlab+sonar代码扫描漏洞扫描的主要内容,如果未能解决你的问题,请参考以下文章
devops===》Jenkins(pipeline)+gitlab+sonar代码扫描漏洞扫描
devops===》Jenkins(pipeline)+gitlab+sonar代码扫描漏洞扫描
[云原生专题-62]:Kubesphere云治理-DevOps-持续集成与pipeline自动上云工具Jenkins