Etcd集群搭建(证书通信)
Posted 张小爽
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了Etcd集群搭建(证书通信)相关的知识,希望对你有一定的参考价值。
1 安装生成证书工具
1.0环境配置
|
Nodes |
主机ip |
角色 |
|
Etcd1 |
192.168.253.*** |
Master |
|
Etcd2 |
192.168.253.*** |
Node |
|
Etcd3 |
192.168.253.*** |
Node |
1.1 安装三个工具分别是cfssl、cdssl-json、cfssl-certinfo
wget https://pkg.cfssl.org/R1.2/cfssl_ _linux-amd64
wget https:// pkg.cfssl.org/R1.2/cfssljson__ linux- amd64
wget https://pkg.cfssl.org/R1.2/cfssl-certinfo_ _linux-amd64
mv cfssI_ _linux- amd64 /usr/local/bin/cfssI
mv cfssljson_ _linux-amd64 /usr/local/bin/cfssl-json
mv cfssl-certinfo_ linux-amd64 /usr/bin/cfssI-certinfo
chmod +x cfssl cfssl-json cfssl-certinfo
2部署签发证书环境
2.1签发ca证书
[root@etcd1 ~]# mkdir /opt/certs
[root@etcd1 ~]# vim /opt/certs/ca-csr.json
{
"CN": "kubernetes-ca",
"hosts": [
],
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"ST": "beijing",
"L": "beijing",
"O": "od",
"OU": "ops"
}
],
"ca": {
"expiry": "175200h"
}
}
(1)参数分析
CN: Common Name,浏览器使用该字段验证网站是否合法,一般写的是域名。非常重要。浏览器使用该字段验证网站是否合法
C: Country, 国家
ST: State,州,省
L: Locality,地区,城市
O: Organization Name,组织名称,公司名称
OU: Organization Unit Name,组织单位名称,公司部门
2.2 生成ca证书
[root@etcd1 certs]# cfssl gencert -initca ca-csr.json | cfssl-json -bare ca
[root@host-1 certs]# ll
total 16
-rw-r--r-- 1 root root 332 Nov 14 22:04 ca-csr.json
-rw------- 1 root root 1675 Nov 14 22:11 ca-key.pem
-rw-r--r-- 1 root root 1001 Nov 14 22:11 ca.csr
-rw-r--r-- 1 root root 1354 Nov 14 22:11 ca.pem
3签发证书ca证书配置
3.1创建ca证书配置文件
[root@etcd1 ~]# cd /opt/certs/
[root@etcd1 certs]# vim ca-config.json
{
"signing": {
"default": {
"expiry": "175200h"
},
"profiles": {
"server": {
"expiry": "175200h",
"usages": [
"signing",
"key encipherment",
"server auth"
]
},
"client": {
"expiry": "175200h",
"usages": [
"signing",
"key encipherment",
"client auth"
]
},
"peer": {
"expiry": "175200h",
"usages": [
"signing",
"key encipherment",
"server auth",
"client auth"
]
}
}
}
}
3.2签发etcd证书
[root@etcd1 certs]# vim etcd-peer-csr.json
{
"CN": "k8s-etcd",
"hosts": [
"192.168.253.100",
"192.168.253.101",
"192.168.253.102"
],
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"ST": "beijing",
"L": "beijing",
"O": "od",
"OU": "ops"
}
]
}
3.3生成etcd证书
[root@etcd1 certs]# cfssl gencert -ca=ca.pem -ca-key=ca-key.pem -config=ca-config.json -profile=peer etcd-peer-csr.json | cfssl-json -bareetcd-peer
[root@etcd1 certs]# ll etcd*
-rw-r--r-- 1 root root 363 Nov 15 16:44 etcd-peer-csr.json
-rw------- 1 root root 1675 Nov 15 16:46 etcd-peer-key.pem
-rw-r--r-- 1 root root 1062 Nov 15 16:46 etcd-peer.csr
-rw-r--r-- 1 root root 1432 Nov 15 16:46 etcd-peer.pem
4部署etcd
4.1创建用户
[root@etcd1 ~]# mkdir /opt/src
[root@etcd1 ~]# cd /opt/src
[root@etcd1 src]# useradd -s /sbin/nologin -M etcd
4.2安装etcd
[root@etcd1src]#wget https://github.com/etcd-io/etcd/releases/download/v3.3.6/etcd-v3.3.6-linux-amd64.tar.gz
[root@etcd1 src]# tar zxf etcd-v3.3.6-linux-amd64.tar.gz -C /opt
[root@etcd1 src]# cd /opt/
[root@etcd1 opt]# mv etcd-v3.3.6-linux-amd64/ etcd-v3.3.6
[root@etcd1 opt]# ln -s /opt/etcd-v3.3.6/ /opt/etcd
4.3拷贝证书
scp -r certs root@etcd2:/opt/
scp -r certs root@etcd3:/opt/
4.4创建etcd启动脚本
[root@etcd1 etcd]# vi etcd-server-startup.sh
#!/bin/bash
./etcd --name etcd1 \\
--data-dir /data/etcd/etcd-server/ \\
--listen-peer-urls https://192.168.253.100:2380 \\
--listen-client-urls https://192.168.253.100:2379,http://127.0.0.1:2379 \\
--quota-backend-bytes 8000000000 \\
--initial-advertise-peer-urls https://192.168.253.100:2380 \\
--advertise-client-urls https://192.168.253.100:2379,http://127.0.0.1:2379 \\
--initial-cluster etcd1=https://192.168.253.100:2380,etcd2=https://192.168.253.101:2380,etcd3=https://192.168.253.102:2380 \\
--ca-file ../certs/ca.pem \\
--cert-file ../certs/etcd-peer.pem \\
--key-file ../certs/etcd-peer-key.pem \\
--client-cert-auth \\
--trusted-ca-file ../certs/ca.pem \\
--peer-ca-file ../certs/ca.pem \\
--peer-cert-file ../certs/etcd-peer.pem \\
--peer-key-file ../certs/etcd-peer-key.pem \\
--peer-client-cert-auth \\
--peer-trusted-ca-file ../certs/ca.pem \\
--log-output stdout
4.5授权及创建日志目录
[root@etcd1 etcd]# chmod +x etcd-server-startup.sh
[root@etcd1 etcd]# chown -R etcd.etcd /opt/etcd-v3.3.6/
[root@etcd1 etcd]# chown -R etcd.etcd /data/etcd /data/logs/etcd-server/
(参考)
chown etcd. /data/etcd/ /data/logs/etcd-server/
chown -R etcd. /data/*
ll /data/*
4.6启动etcd
[root@etcd1 etcd]# pwd
/opt/etcd
[root@etcd1 etcd]# nohup ./etcd-server-startup.sh &
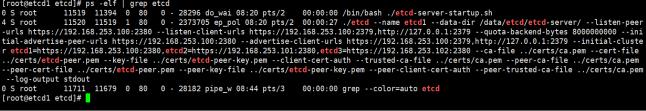
4.7查看状态
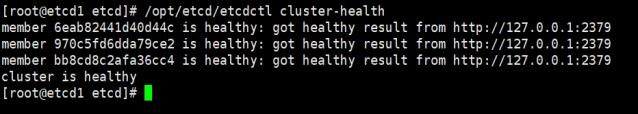
/opt/etcd/etcdctl cluster-health
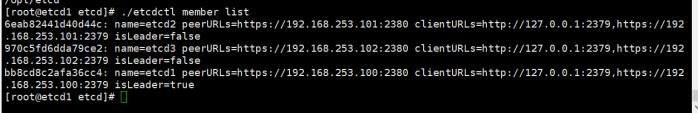
./etcdctl member list
欢迎进群讨论:QQ群294668383(有意向可以添加)
以上是关于Etcd集群搭建(证书通信)的主要内容,如果未能解决你的问题,请参考以下文章
Kubernetes学习一:Kubernetes集群搭建之etcd安装部署
K8S------Kubernetes单Master集群二进制搭建
K8S------Kubernetes单Master集群二进制搭建