信息收集:使用dnsrecon进行子域名爆破
Posted Zeker62
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了信息收集:使用dnsrecon进行子域名爆破相关的知识,希望对你有一定的参考价值。
dnsrecon
- kali工具
- 可以进行域名爆破
步骤
- 创建字典:vim dns.dic ,写入字典
- 输入dnsrecon -d badu.com -D /tmp/1901/dic/dns.dic -t brt
- 其中,字典一定要是绝对路径
- -d表示domain,-D表示路径名 -t表示爆破方法type
Type of enumeration to perform. std: SOA, NS, A, AAAA, MX and SRV. rvl: Reverse lookup of a given CIDR or IP range. brt: Brute force domains and hosts using a given dictionary. srv: SRV records. axfr: Test all NS servers for a zone transfer. bing: Perform Bing search for subdomains and hosts. yand: Perform Yandex search for subdomains and hosts. crt: Perform crt.sh search for subdomains and hosts. snoop:
Perform cache snooping against all NS servers for a given domain, testing all with file containing the domains, file given with -D option. tld: Remove the TLD of given domain and test against all TLDs registered in IANA. zonewalk: Perform a DNSSEC zone walk using NSEC records.
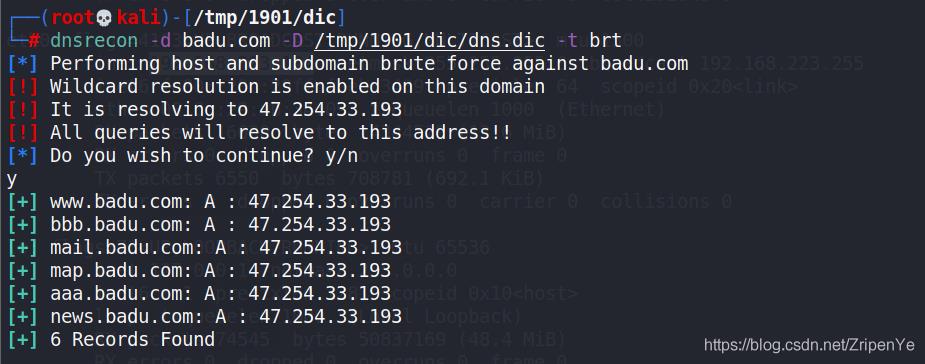
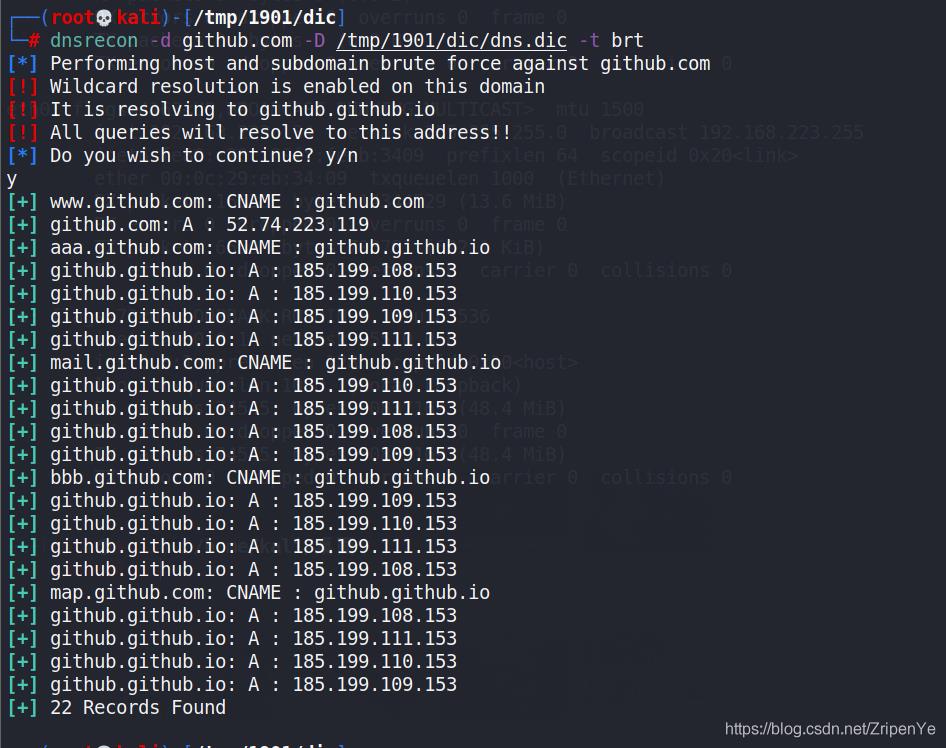
以上是关于信息收集:使用dnsrecon进行子域名爆破的主要内容,如果未能解决你的问题,请参考以下文章