linux ssh publickey登录
Posted Noway11
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了linux ssh publickey登录相关的知识,希望对你有一定的参考价值。
一、公钥认证的基本思想:
对信息的加密和解密采用不同的key,这对key分别称作private key和public key,其中,public key存放在目标服务器上,而private key为特定的客户机所持有。
当客户机向服务器发出建立安全连接的请求时,首先发送自己的public key,如果这个public key是被服务器所允许的,服务器就发送一个经过public key加密的随机数据给客户机,这个数据只能通过private key解密,客户机将解密后的信息发还给服务器,服务器验证正确后即确认客户机是可信任的,从而建立起一条安全的信息通道。
通过这种方式,客户机不需要向外发送自己的身份标志“private key”即可达到校验的目的,并且private key是不能通过public key反向推断出来的。这避免了网络窃听可能造成的密码泄露。客户机需要小心的保存自己的private key,以免被其他人窃取,一旦这样的事情发生,就需要各服务器更换受信的public key列表。
二、无密码登录实现方式(server1 publickey连接server2免密码登录)
1、用ssh-keygen创建公钥(server1)
[root@server1 ~]# ssh-keygen
Generating public/private rsa key pair.
Enter file in which to save the key(/root/.ssh/id_rsa):
Created directory \'/root/.ssh\'.
Enter passphrase (empty for no passphrase): (此处密码决定终端连接时使用的私钥密码)
Enter same passphrase again:
Your identification has been saved in/root/.ssh/id_rsa.
Your public key has been saved in/root/.ssh/id_rsa.pub.
The key fingerprint is:
7b:aa:08:a0:99:fc:d9:cc:d8:2e:4b:1a:c0:6b:da:e4root@Server1
The key\'s randomart image is:
+--[ RSA 2048]----+
| |
| |
| |
|. |
|o. S |
|++. . |
|+=o. . . |
|o+=oB. o |
|..E==*... |
+-----------------+
补充说明 ssh-keygen:生成秘钥,其中:
-t指定算法
-f 指定生成秘钥路径
-N 指定密码
2、查看生成证书:
[root@server1]$ ll /root/.ssh/
total 16
-rw------- 1 yida yida 1675 Mar 31 11:42 id_rsa
-rw-r--r-- 1 yida yida 399 Mar 31 11:42 id_rsa.pub
3、将server1 publickey复制到server2 authorized_keys,需要输入server2 root用户密码
[root@server1 .ssh]$ ssh-copy-id -i id_rsa.pub root@10.207.0.179
The authenticity of host \'10.207.0.179 (10.207.0.179)\' can\'t be established.
RSA key fingerprint is 94:5f:47:a8:ae:0b:b0:31:0f:ce:6b:86:08:51:98:a7.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added \'10.207.0.179\' (RSA) to the list of known hosts.
Address 10.207.0.179 maps to localhost, but this does not map back to the address - POSSIBLE BREAK-IN ATTEMPT!
Password:
Now try logging into the machine, with "ssh \'root@10.207.0.179\'", and check in:
.ssh/authorized_keys
to make sure we haven\'t added extra keys that you weren\'t expecting.
[yida@yw_d10075798 .ssh]$
4、server2 查看public key文件
[root@server2]$ ll
total 16
-rw------- 1 root root 408 Mar 30 15:43 authorized_keys
5、实现server1登录server2免密码登录
ssh-keygen -t rsa -f /root/test/root.pem -b 2048 -P "XXXXX"
三、SecureCRT客户端使用publickey登录linux
方法一:服务器端生成公钥私钥文件,保留公钥文件为authorized_keys,下载公钥私钥文件到客户端本地,提供给secureCRT连接使用。
1、用ssh-keygen创建公钥(server1)
[root@server1 ~]# ssh-keygen
Generating public/private rsa key pair.
Enter file in which to save the key(/root/.ssh/id_rsa):
Created directory \'/root/.ssh\'.
Enter passphrase (empty for no passphrase): (此处密码决定终端连接时使用的私钥密码)
Enter same passphrase again:
Your identification has been saved in/root/.ssh/id_rsa.
Your public key has been saved in/root/.ssh/id_rsa.pub.
The key fingerprint is:
7b:aa:08:a0:99:fc:d9:cc:d8:2e:4b:1a:c0:6b:da:e4root@Server1
The key\'s randomart image is:
+--[ RSA 2048]----+
| |
| |
| |
|. |
|o. S |
|++. . |
|+=o. . . |
|o+=oB. o |
|..E==*... |
+-----------------+
[root@server1]$ ll /root/.ssh/
total 16
-rw------- 1 yida yida 1675 Mar 31 11:42 id_rsa
-rw-r--r-- 1 yida yida 399 Mar 31 11:42 id_rsa.pub
2、发送公钥私钥到本地,修改公钥为授权证书文件
[root@.ssh~]#sz id_rsa id_rsa.pub
[root@.ssh~]#mv id_rsa.pub authorized_keys
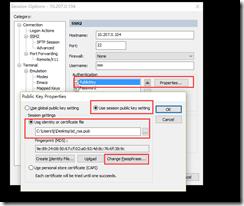
3、设置secureCRT连接
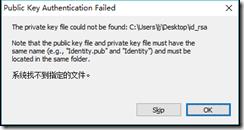
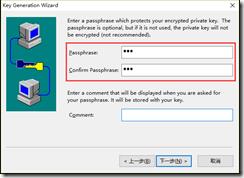
注意生成在server1生成证书时passphrase设置,同时一定要把公钥私钥文件放在本地同一目录下,否则会出现以下报错
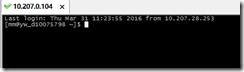
4、登陆成功
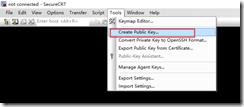
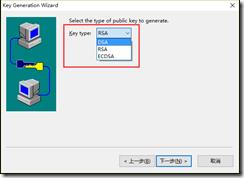
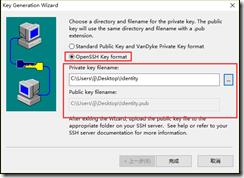
方法二:在secureCRT客户端生成通用openssh key format公钥私钥文件,并将公钥文件复制到server端authorized_keys文件。
以上是关于linux ssh publickey登录的主要内容,如果未能解决你的问题,请参考以下文章
Xshell配置密钥公钥(Public key)与私钥(Private Key)登录
Linux配置SSH公钥认证与Jenkins远程登录进行自动发布