攻防世界 reverse 新手练习区
Posted DirWangK
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了攻防世界 reverse 新手练习区相关的知识,希望对你有一定的参考价值。
1.re1 DUTCTF
IDA shift+F12 查看字符串
DUTCTF{We1c0met0DUTCTF}
2.game ZSCTF
zsctf{T9is_tOpic_1s_v5ry_int7resting_b6t_others_are_n0t}
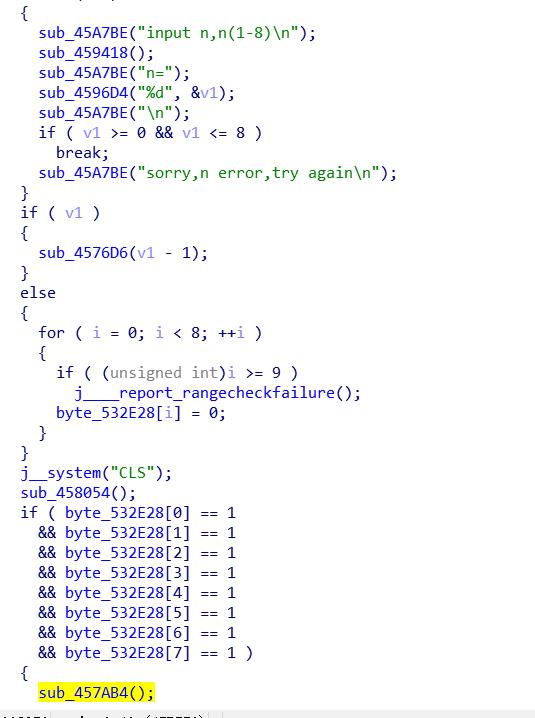
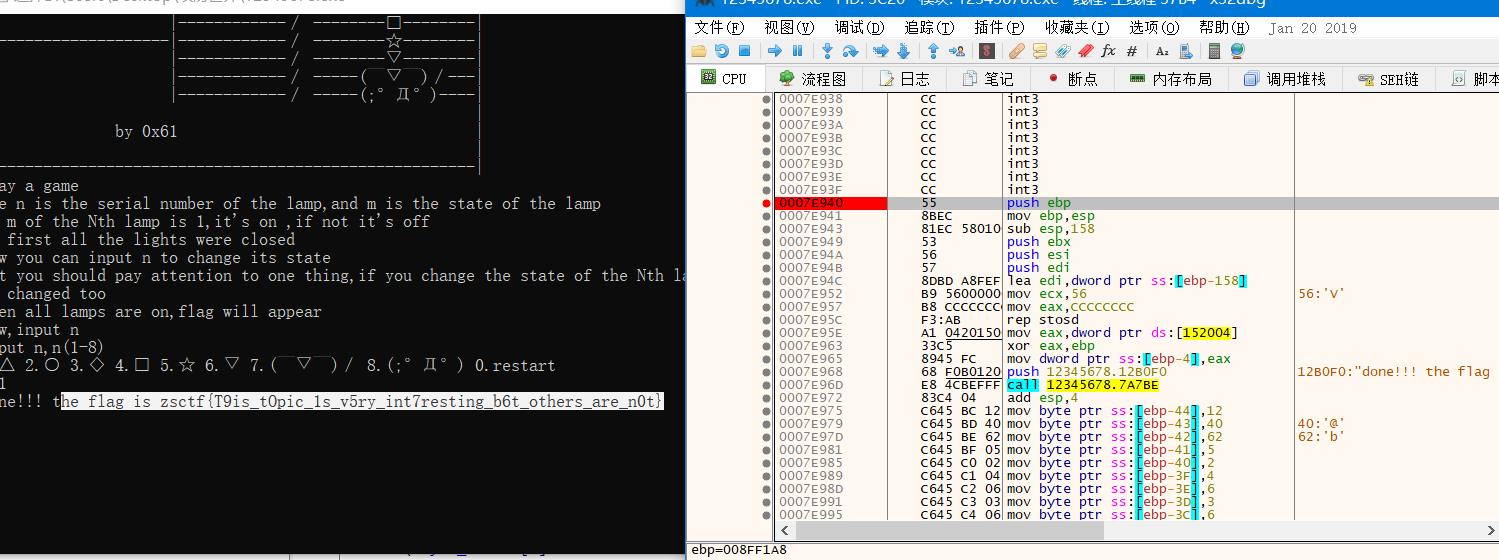
3.Hello, CTF Pediy CTF 2018
CrackMeJustForFun
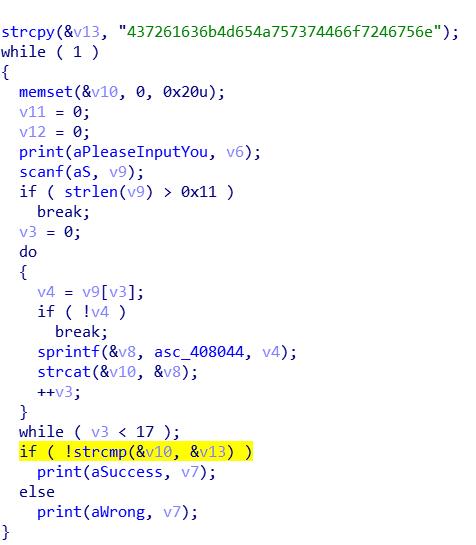
将16进制字符串转ascii字符串得到flag
4.open-source HackYou CTF
参数 51966 25 h4cky0u
flag为:
c0ffee
5.open-source 9447 CTF 2014
IDA查看字符串
9447{This_is_a_flag}
6.simple-unpack
脱壳搜索字符串
flag{Upx_1s_n0t_a_d3liv3r_c0mp4ny}
7.logmein RC3 CTF 2016
1 v8=":\\"AL_RT^L*.?+6/46" 2 v7 = \'ebmarah\'[::-1] 3 s=\'\' 4 for i in range(len(v8)): 5 s+=chr(ord(v7[i%7])^ord(v8[i])) 6 7 print(s)
RC3-2016-XORISGUD
8. no-strings-attached 9447 CTF 2014

1 x=[58, 20, 0, 0, 54, 20, 0, 0, 55, 20, 2 0, 0, 59, 20, 0, 0, 128, 20, 0, 0, 3 122, 20, 0, 0, 113, 20, 0, 0, 120, 20, 4 0, 0, 99, 20, 0, 0, 102, 20, 0, 0, 5 115, 20, 0, 0, 103, 20, 0, 0, 98, 20, 6 0, 0, 101, 20, 0, 0, 115, 20, 0, 0, 7 96, 20, 0, 0, 107, 20, 0, 0, 113, 20, 8 0, 0, 120, 20, 0, 0, 106, 20, 0, 0, 9 115, 20, 0, 0, 112, 20, 0, 0, 100, 20, 10 0, 0, 120, 20, 0, 0, 110, 20, 0, 0, 11 112, 20, 0, 0, 112, 20, 0, 0, 100, 20, 12 0, 0, 112, 20, 0, 0, 100, 20, 0, 0, 13 110, 20, 0, 0, 123, 20, 0, 0, 118, 20, 14 0, 0, 120, 20, 0, 0, 106, 20, 0, 0, 15 115, 20, 0, 0, 123, 20, 0, 0, 128, 20, 16 0, 0, 0, 0, 0, 0] 17 y=[] 18 for t in x: 19 if t!=20 and t!=0: 20 y.append(t) 21 i=0 22 while i<len(y): 23 for j in range(1,6): 24 y[i]-=j 25 y[i]=chr(y[i]) 26 i+=1 27 if i==len(y): 28 break 29 print(\'\'.join(y))
9447{you_are_an_international_mystery}
9.python-trade NJUPT CTF 2017
使用EasyPythonDecompiler.exe
1 import base64 2 3 buf = base64.b64decode(\'XlNkVmtUI1MgXWBZXCFeKY+AaXNt\') 4 flag = \'\' 5 for i in buf: 6 i -= 16 7 i ^= 32 8 flag += chr(i) 9 print(flag)
nctf{d3c0mpil1n9_PyC}
10.getit SharifCTF 2016
主要逻辑:

1 int __cdecl main(int argc, const char **argv, const char **envp) 2 { 3 char v3; // al 4 __int64 v5; // [rsp+0h] [rbp-40h] 5 int i; // [rsp+4h] [rbp-3Ch] 6 FILE *stream; // [rsp+8h] [rbp-38h] 7 char filename[8]; // [rsp+10h] [rbp-30h] 8 unsigned __int64 v9; // [rsp+28h] [rbp-18h] 9 10 v9 = __readfsqword(0x28u); 11 LODWORD(v5) = 0; 12 while ( (signed int)v5 < strlen(s) ) // s=c61b68366edeb7bdce3c6820314b7498 13 { 14 if ( v5 & 1 ) 15 v3 = 1; 16 else 17 v3 = -1; 18 t[(signed int)v5 + 10] = s[(signed int)v5] + v3; 19 LODWORD(v5) = v5 + 1; 20 } 21 strcpy(filename, "/tmp/flag.txt"); 22 stream = fopen(filename, "w"); 23 fprintf(stream, "%s\\n", u, v5); 24 for ( i = 0; i < strlen(t); ++i ) 25 { 26 fseek(stream, p[i], 0); 27 fputc(t[p[i]], stream); 28 fseek(stream, 0LL, 0); 29 fprintf(stream, "%s\\n", u); 30 } 31 fclose(stream); 32 remove(filename); 33 return 0; 34 }
解题脚本:

1 s=\'c61b68366edeb7bdce3c6820314b7498\' 2 t=list(\'SharifCTF{????????????????????????????????}\') 3 v5 = 0; 4 while v5 < len(s): #c61b68366edeb7bdce3c6820314b7498 5 6 if (v5 & 1): 7 v3 = 1; 8 else: 9 v3 = -1; 10 11 t[v5 + 10] = chr(ord(s[v5])+ v3) ; 12 v5= v5 + 1; 13 14 print(\'\'.join(t))
SharifCTF{b70c59275fcfa8aebf2d5911223c6589}
以上是关于攻防世界 reverse 新手练习区的主要内容,如果未能解决你的问题,请参考以下文章
