kubernetes学习14—Dashboard搭建和认证
Posted lonelyxmas
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了kubernetes学习14—Dashboard搭建和认证相关的知识,希望对你有一定的参考价值。
原文:kubernetes学习14—Dashboard搭建和认证本文收录在容器技术学习系列文章总目录
一、介绍
Kubernetes Dashboard是Kubernetes集群的基于Web的通用UI。它允许用户管理在群集中运行的应用程序并对其进行故障排除,以及管理群集本身。
二、搭建dashboard
1、编写yaml文件
借鉴GitHub,修改了image的下载地址和pod的一些配置
[[email protected] ~]# vim dashboard.yaml
# Filename: dashboard.yaml
# Revision: 1.0
# Date: 2018/10/18
# Author: along
# Description: Build kubernetes dashboard
# ------------------- Dashboard Secret ------------------- #
apiVersion: v1
kind: Secret
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard-certs
namespace: kube-system
type: Opaque
---
# ------------------- Dashboard Service Account ------------------- #
apiVersion: v1
kind: ServiceAccount
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kube-system
---
# ------------------- Dashboard Role & Role Binding ------------------- #
kind: Role
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: kubernetes-dashboard-minimal
namespace: kube-system
rules:
# Allow Dashboard to create ‘kubernetes-dashboard-key-holder‘ secret.
- apiGroups: [""]
resources: ["secrets"]
verbs: ["create"]
# Allow Dashboard to create ‘kubernetes-dashboard-settings‘ config map.
- apiGroups: [""]
resources: ["configmaps"]
verbs: ["create"]
# Allow Dashboard to get, update and delete Dashboard exclusive secrets.
- apiGroups: [""]
resources: ["secrets"]
resourceNames: ["kubernetes-dashboard-key-holder", "kubernetes-dashboard-certs"]
verbs: ["get", "update", "delete"]
# Allow Dashboard to get and update ‘kubernetes-dashboard-settings‘ config map.
- apiGroups: [""]
resources: ["configmaps"]
resourceNames: ["kubernetes-dashboard-settings"]
verbs: ["get", "update"]
# Allow Dashboard to get metrics from heapster.
- apiGroups: [""]
resources: ["services"]
resourceNames: ["heapster"]
verbs: ["proxy"]
- apiGroups: [""]
resources: ["services/proxy"]
resourceNames: ["heapster", "http:heapster:", "https:heapster:"]
verbs: ["get"]
---
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
name: kubernetes-dashboard-minimal
namespace: kube-system
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: kubernetes-dashboard-minimal
subjects:
- kind: ServiceAccount
name: kubernetes-dashboard
namespace: kube-system
---
# ------------------- Dashboard Deployment ------------------- #
kind: Deployment
apiVersion: apps/v1beta2
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kube-system
spec:
replicas: 1
revisionHistoryLimit: 10
selector:
matchLabels:
k8s-app: kubernetes-dashboard
template:
metadata:
labels:
k8s-app: kubernetes-dashboard
spec:
containers:
- name: kubernetes-dashboard
image: mirrorgooglecontainers/kubernetes-dashboard-amd64:v1.10.0
ports:
- containerPort: 8443
protocol: TCP
args:
- --auto-generate-certificates
# Uncomment the following line to manually specify Kubernetes API server Host
# If not specified, Dashboard will attempt to auto discover the API server and connect
# to it. Uncomment only if the default does not work.
# - --apiserver-host=http://my-address:port
volumeMounts:
- name: kubernetes-dashboard-certs
mountPath: /certs
# Create on-disk volume to store exec logs
- mountPath: /tmp
name: tmp-volume
livenessProbe:
httpGet:
scheme: HTTPS
path: /
port: 8443
initialDelaySeconds: 30
timeoutSeconds: 30
volumes:
- name: kubernetes-dashboard-certs
secret:
secretName: kubernetes-dashboard-certs
- name: tmp-volume
emptyDir: {}
serviceAccountName: kubernetes-dashboard
# Comment the following tolerations if Dashboard must not be deployed on master
tolerations:
- key: node-role.kubernetes.io/master
effect: NoSchedule
---
# ------------------- Dashboard Service ------------------- #
kind: Service
apiVersion: v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kube-system
spec:
type: NodePort
ports:
- port: 443
targetPort: 8443
nodePort: 30000
selector:
k8s-app: kubernetes-dashboard
2、apply yaml文件,搭建dashboard
[[email protected] ~]# kubectl apply -f dashboard.yaml
secret/kubernetes-dashboard-certs created
serviceaccount/kubernetes-dashboard created
role.rbac.authorization.k8s.io/kubernetes-dashboard-minimal created
rolebinding.rbac.authorization.k8s.io/kubernetes-dashboard-minimal created
deployment.apps/kubernetes-dashboard created
service/kubernetes-dashboard created
3、查看验证
(1)pod已经创建成功
[[email protected] ~]# kubectl get pods -n kube-system |grep dashboard
kubernetes-dashboard-68bf55748d-4zzph 1/1 Running 0 2m
(2)service也已经创建成功,并且有映射端口,此时已经可以登录了,但是无法登录,因为没有认证
[[email protected] ~]# kubectl get svc -n kube-system
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
kubernetes-dashboard NodePort 10.97.55.246 <none> 443:30000/TCP 2m
三、dashboard与kubernetes集群的认证,方案一:令牌认证
(1)有两种认证方法:
口令
kubeconfig
(2)并且在认证的时候,还可以管理限制dashboard用户的权限;为了让大家进一步理解:
在方案一:口令认证时,dashboard用户的权限设为对所有名称空间都有admin的权限;
在方案二:kubeconfig认证时,dashboard用户的权限设为只对default名称空间有admin权限;
1、授权,对所有名称空间都有admin的权限
(1)创建serviceaccount
[[email protected] ~]# kubectl create serviceaccount dashboard-serviceaccount -n kube-system
serviceaccount/dashboard-serviceaccount created
(2)创建clusterrolebinding
使用clusterrolebinding绑定cluster-admin的clusterrole和dashboard-serviceaccount的serviceaccount,这样dashboard-serviceaccount的serviceaccount就在所有名称空间有了kubernetes的admin权限
[[email protected] ~]# kubectl create clusterrolebinding dashboard-cluster-admin --clusterrole=cluster-admin --serviceaccount=kube-system:dashboard-serviceaccount
clusterrolebinding.rbac.authorization.k8s.io/dashboard-cluster-admin created
2、获取令牌
(1)在secret中查找dashboard-serviceaccount
[[email protected] ~]# kubectl get secret -n kube-system |grep dashboard-serviceaccount-token
dashboard-serviceaccount-token-nz7xd kubernetes.io/service-account-token 3 4m
(2)查看dashboard-serviceaccount中的口令
[[email protected] ~]# kubectl describe secret dashboard-serviceaccount-token-nz7xd -n kube-system
Name: dashboard-serviceaccount-token-nz7xd Namespace: kube-system Labels: <none> Annotations: kubernetes.io/service-account.name=dashboard-serviceaccount kubernetes.io/service-account.uid=2af6061f-d1f0-11e8-8059-005056277243 Type: kubernetes.io/service-account-token Data ==== ca.crt: 1025 bytes namespace: 11 bytes token: eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJkYXNoYm9hcmQtc2VydmljZWFjY291bnQtdG9rZW4tbno3eGQiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiZGFzaGJvYXJkLXNlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiMmFmNjA2MWYtZDFmMC0xMWU4LTgwNTktMDA1MDU2Mjc3MjQzIiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50Omt1YmUtc3lzdGVtOmRhc2hib2FyZC1zZXJ2aWNlYWNjb3VudCJ9.BAJVarqum57S_KepqOgcS1IimNEmDilhu4tIiWQKxaz0o5TKyXBZ5YqN3ZS5tJNQbLvDS6LuRRXdvH-MeKQnUpg08OhYDg1u9XE3Oygr7YF5Ad7yBw4czpPPN6iIJZ5qQJ8laOfPRb8qYVbR0R4MONin08lhzrkLBkRLwhAVJ_6zXXB9vaJLU9asTyA4YmDAZZi06zkYeeO8Rhqr2-Yeu4Ya7miLYVRv_ioqDlkqGEf6ILUriPjeJHohIEbgdslRXTnxgwkt2Uwsv3QRFKF2CisSBSW7P-9muuCrzSb2xQVop7WbAUyROdUuqQFmSON2UC0643e_iEW5DBaAAGQxbw
3、网页通过令牌登录
(1)使用https协议打开https://192.168.130.103:30000(任意节点的IP都可以)
输入dashboard-serviceaccount的口令
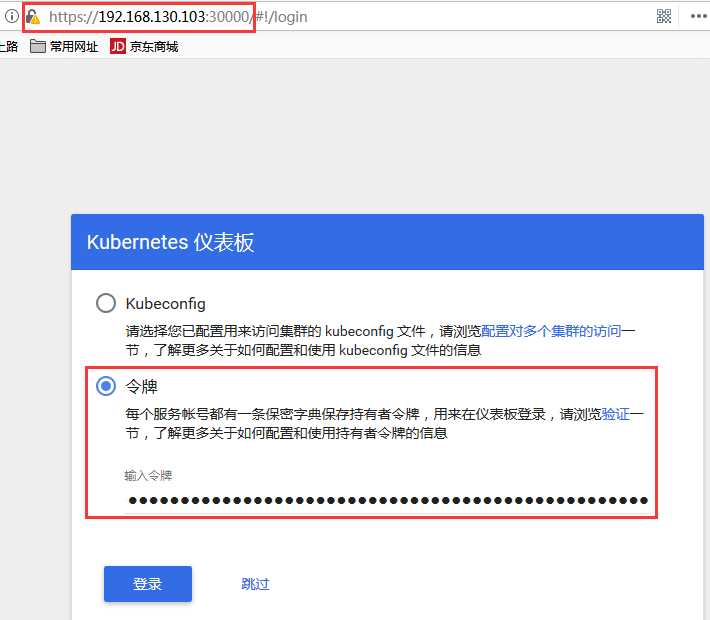
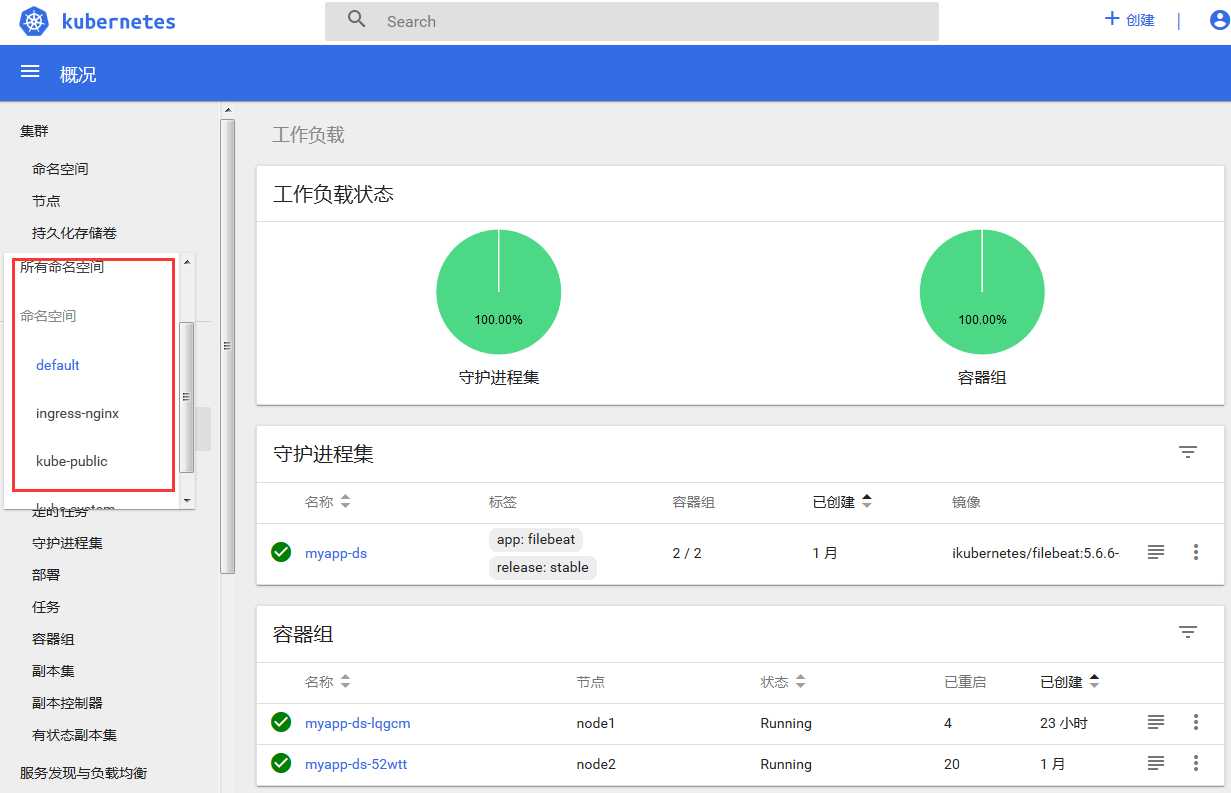
(2)打开成功,并且对所有名称空间都有admin权限
四、dashboard与kubernetes集群的认证,方案二:configing认证
1、授权,只对default名称空间有admin的权限
(1)创建serviceaccount
[[email protected] ~]# kubectl create serviceaccount def-ns-dashboard-sa -n default
serviceaccount/def-ns-dashboard-sa created
(2)创建rolebinding
使用rolebinding绑定cluster-admin的clusterrole和def-ns-dashboard的serviceaccount,这样def-ns-dashboard的serviceaccount就只有default这一个名称空间的admin权限
[[email protected] ~]# kubectl create rolebinding def-ns-dashboard-rb --clusterrole=cluster-admin --serviceaccount=default:def-ns-dashboard-sa
rolebinding.rbac.authorization.k8s.io/def-ns-dashboard-rb created
2、获取令牌
(1)在secret中查找def-ns-dashboard-sa
[[email protected] ~]# kubectl get secret
NAME TYPE DATA AGE
def-ns-dashboard-sa-token-b8plm kubernetes.io/service-account-token 3 1m
(2)查看def-ns-dashboard-sa中的口令
[[email protected] ~]# kubectl describe secret def-ns-dashboard-sa-token-b8plm
Name: def-ns-dashboard-sa-token-b8plm Namespace: default Labels: <none> Annotations: kubernetes.io/service-account.name=def-ns-dashboard-sa kubernetes.io/service-account.uid=8b040303-d287-11e8-be88-005056277243 Type: kubernetes.io/service-account-token Data ==== ca.crt: 1025 bytes namespace: 7 bytes token: eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJkZWZhdWx0Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6ImRlZi1ucy1kYXNoYm9hcmQtc2EtdG9rZW4tYjhwbG0iLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiZGVmLW5zLWRhc2hib2FyZC1zYSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6IjhiMDQwMzAzLWQyODctMTFlOC1iZTg4LTAwNTA1NjI3NzI0MyIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDpkZWZhdWx0OmRlZi1ucy1kYXNoYm9hcmQtc2EifQ.VqAgyqN8_F4mjawWtZ5TzvFioKA50u4MUL_4ypBxWrr-XU8TciM8EX1OcGm9vAjUW_m5QZangS7VW3rVYPcqKMqaYKE8vN-l9wTC5CzTnxPHMghTx8sTTkPWnqHt7C7v8cVRNfeRAWygWMp1B8Chx5pAK2l9t095uZy_w59qFQdoAKeAcxiH5K6kz9sx8VwEXVr9nRH8bFqvtr3yXCdYo2e2qSQXOpNddlyrEOYXrIUlamNyImgcbfkNLV0Qkt5sdfSLSJdaB2opLWD8pST88m73r6KG2c_aMmyZ7mTCUeNd1BwCOnLSto4V2xPXCtHA6ELvB5afh9irpCj4e5VgPw
3、定义一个kubeconfig认证文件
(1)在一个新的kubeconfig文件下,创建一个集群dashboard
[[email protected] ~]# kubectl config set-cluster dashboard --certificate-authority=/etc/kubernetes/pki/ca.crt --server="https://192.168.130.103:6443" --embed-certs=true --kubeconfig=/root/def-ns-dashboard.conf
Cluster "dashboard" set.
/root/def-ns-dashboard.conf 文件已经生成
[[email protected] ~]# ll /root/def-ns-dashboard.conf
-rw------- 1 root root 1568 Oct 18 13:36 /root/def-ns-dashboard.conf
(2)使用def-ns-dashboard-sa的serviceaccount,创建一个用户def-ns-dashboard-user
[[email protected] ~]# kubectl config set-credentials def-ns-dashboard-user --kubeconfig=/root/def-ns-dashboard.conf --token=eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJkZWZhdWx0Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6ImRlZi1ucy1kYXNoYm9hcmQtc2EtdG9rZW4tYjhwbG0iLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiZGVmLW5zLWRhc2hib2FyZC1zYSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6IjhiMDQwMzAzLWQyODctMTFlOC1iZTg4LTAwNTA1NjI3NzI0MyIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDpkZWZhdWx0OmRlZi1ucy1kYXNoYm9hcmQtc2EifQ.VqAgyqN8_F4mjawWtZ5TzvFioKA50u4MUL_4ypBxWrr-XU8TciM8EX1OcGm9vAjUW_m5QZangS7VW3rVYPcqKMqaYKE8vN-l9wTC5CzTnxPHMghTx8sTTkPWnqHt7C7v8cVRNfeRAWygWMp1B8Chx5pAK2l9t095uZy_w59qFQdoAKeAcxiH5K6kz9sx8VwEXVr9nRH8bFqvtr3yXCdYo2e2qSQXOpNddlyrEOYXrIUlamNyImgcbfkNLV0Qkt5sdfSLSJdaB2opLWD8pST88m73r6KG2c_aMmyZ7mTCUeNd1BwCOnLSto4V2xPXCtHA6ELvB5afh9irpCj4e5VgPw
User "def-ns-dashboard-user" set.
(3)在这个kubeconfig文件下,创建一个上下文关系[email protected]
[[email protected] ~]# kubectl config set-context [email protected] --cluster=dashboard --user=def-ns-dashboard-user --kubeconfig=/root/def-ns-dashboard.conf
Context "[email protected]" created.
(4)在这个kubeconfig文件下,使用[email protected]这个上下文关系
[[email protected] ~]# kubectl config use-context [email protected] --kubeconfig=/root/def-ns-dashboard.conf
Switched to context "[email protected]".
(5)通过view查看验证
[[email protected] ~]# kubectl config view --kubeconfig=/root/def-ns-dashboard.conf
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: REDACTED
server: https://192.168.130.103:6443
name: dashboard
contexts:
- context:
cluster: dashboard
user: def-ns-dashboard-user
name: [email protected]
current-context: [email protected]
kind: Config
preferences: {}
users:
- name: def-ns-dashboard-user
user:
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJkZWZhdWx0Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6ImRlZi1ucy1kYXNoYm9hcmQtc2EtdG9rZW4tYjhwbG0iLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiZGVmLW5zLWRhc2hib2FyZC1zYSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6IjhiMDQwMzAzLWQyODctMTFlOC1iZTg4LTAwNTA1NjI3NzI0MyIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDpkZWZhdWx0OmRlZi1ucy1kYXNoYm9hcmQtc2EifQ.VqAgyqN8_F4mjawWtZ5TzvFioKA50u4MUL_4ypBxWrr-XU8TciM8EX1OcGm9vAjUW_m5QZangS7VW3rVYPcqKMqaYKE8vN-l9wTC5CzTnxPHMghTx8sTTkPWnqHt7C7v8cVRNfeRAWygWMp1B8Chx5pAK2l9t095uZy_w59qFQdoAKeAcxiH5K6kz9sx8VwEXVr9nRH8bFqvtr3yXCdYo2e2qSQXOpNddlyrEOYXrIUlamNyImgcbfkNLV0Qkt5sdfSLSJdaB2opLWD8pST88m73r6KG2c_aMmyZ7mTCUeNd1BwCOnLSto4V2xPXCtHA6ELvB5afh9irpCj4e5VgPw
4、网页通过kubeconfig登录
(1)将/root/def-ns-dashboard.conf 文件上传到windows机器上,把/root/def-ns-dashboard.conf这个kubeconfig文件导入到登录时的页面,就可以成功登录
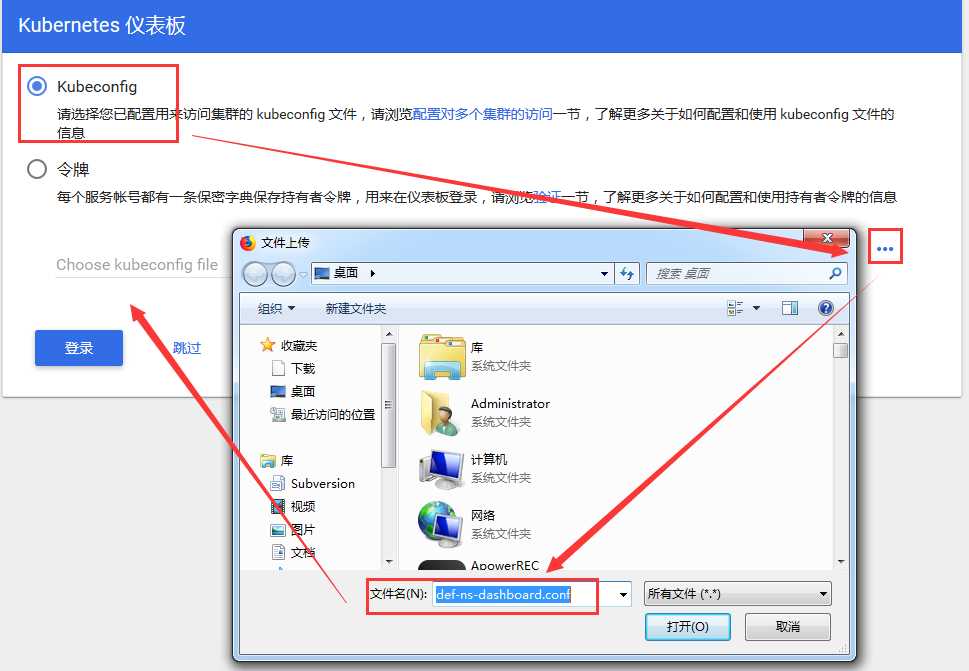
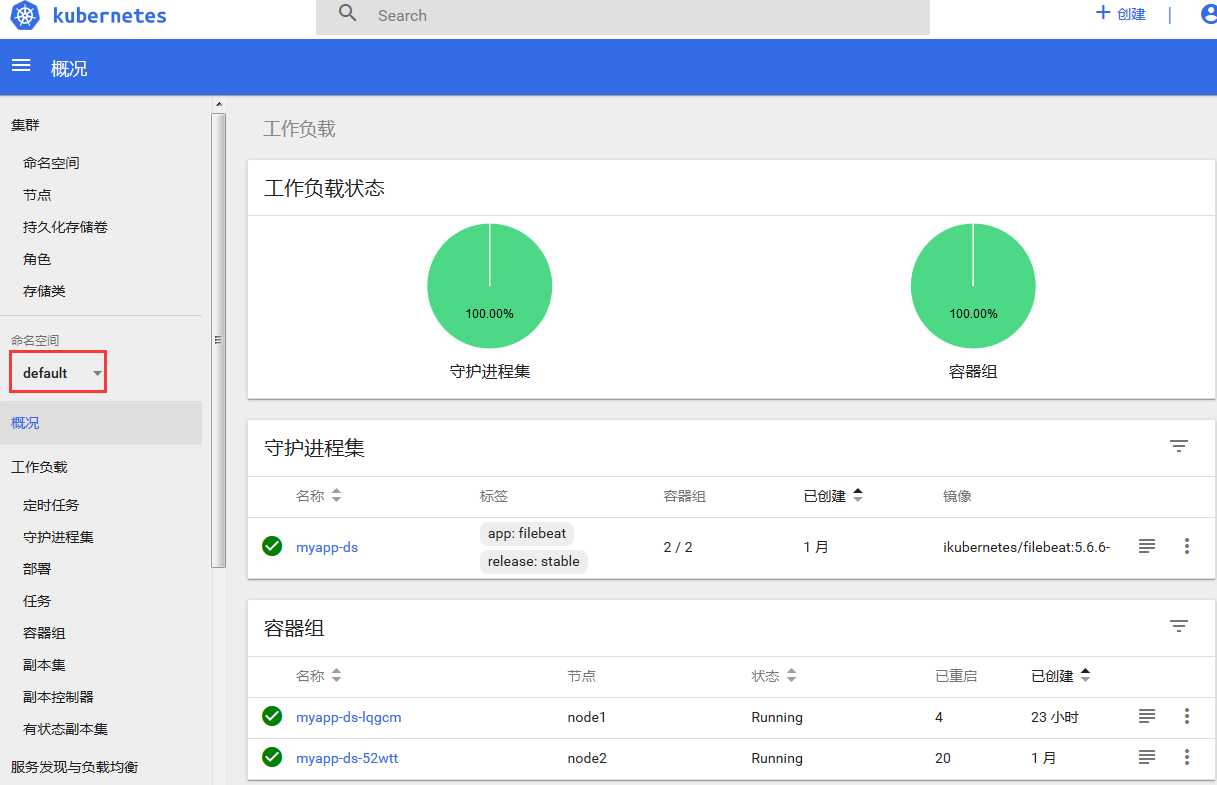
(2)登录成功,但是只有default这个名称空间的admin权限
至此,我们已经成功搭建了dashboard;并且完成了对K8S集群的认证;
我们可以通过dashboard创建和管理Pod、service、存储卷... ... 这里就不再演示了。
以上是关于kubernetes学习14—Dashboard搭建和认证的主要内容,如果未能解决你的问题,请参考以下文章
KUBERNETES02_集群安装逻辑前置环境搭建一主两从部署dashboard访问页面
KUBERNETES02_集群安装逻辑前置环境搭建一主两从部署dashboard访问页面
KUBERNETES02_集群安装逻辑前置环境搭建一主两从部署dashboard访问页面