drf-jwt手动签发与校验
Posted xiongying4
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了drf-jwt手动签发与校验相关的知识,希望对你有一定的参考价值。
# 前提:给一个局部禁用了所有 认证与权限 的视图类发送用户信息得到token,其实就是登录接口 # 1)rest_framework_jwt.views.ObtainJSONWebToken 的 父类 JSONWebTokenAPIView 的 post 方法 # 接受有username、password的post请求 # 2)post方法将请求数据交给 rest_framework_jwt.serializer.JSONWebTokenSerializer 处理 # 完成数据的校验,会走序列化类的 全局钩子校验规则,校验得到登录用户并签发token存储在序列化对象中
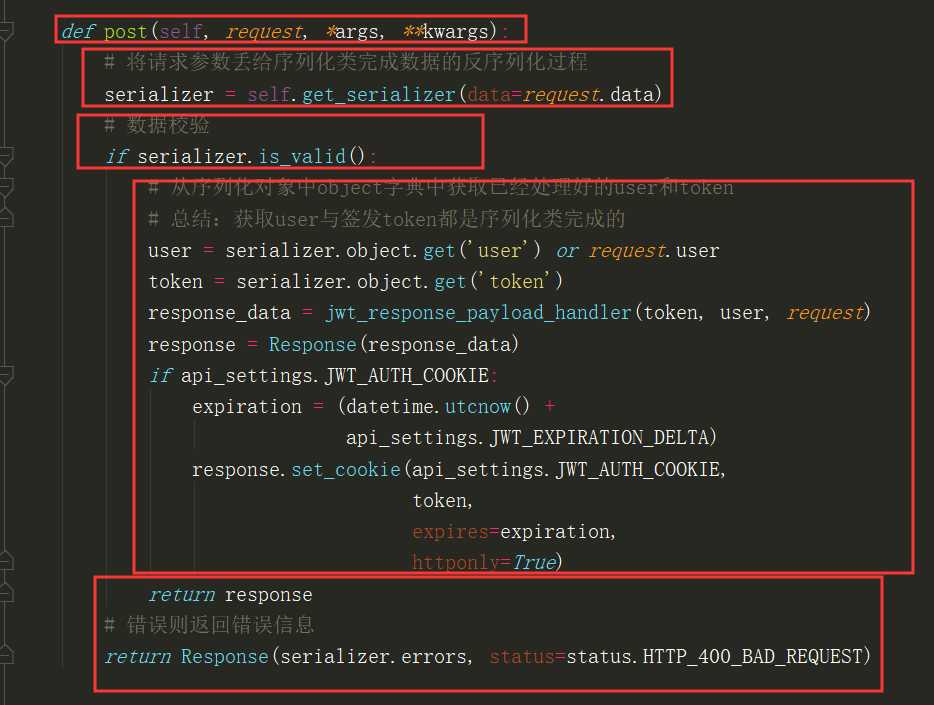
def validate(self, attrs): # 账号密码字典 credentials = { self.username_field: attrs.get(self.username_field), ‘password‘: attrs.get(‘password‘) } if all(credentials.values()): # 签发token第1步:用账号密码得到user对象 user = authenticate(**credentials) if user: if not user.is_active: msg = _(‘User account is disabled.‘) raise serializers.ValidationError(msg) # 签发token第2步:通过user得到payload,payload包含着用户信息与过期时间 payload = jwt_payload_handler(user) # 在视图类中,可以通过 序列化对象.object.get(‘user‘或者‘token‘) 拿到user和token return { # 签发token第3步:通过payload签发出token ‘token‘: jwt_encode_handler(payload), ‘user‘: user } else: msg = _(‘Unable to log in with provided credentials.‘) raise serializers.ValidationError(msg) else: msg = _(‘Must include "{username_field}" and "password".‘) msg = msg.format(username_field=self.username_field) raise serializers.ValidationError(msg)
# 1)通过username、password得到user对象 # 2)通过user对象生成payload:jwt_payload_handler(user) => payload # from rest_framework_jwt.serializers import jwt_payload_handler # 3)通过payload签发token:jwt_encode_handler(payload) => token # from rest_framework_jwt.serializers import jwt_encode_handler
# 前提:访问一个配置了jwt认证规则的视图类,就需要提交认证字符串token,在认证类中完成token的校验 # 1)rest_framework_jwt.authentication.JSONWebTokenAuthentication 的 父类 BaseJSONWebTokenAuthentication 的 authenticate 方法 # 请求头拿认证信息jwt-token => 通过反爬小规则确定有用的token => payload => user
def authenticate(self, request): """ Returns a two-tuple of `User` and token if a valid signature has been supplied using JWT-based authentication. Otherwise returns `None`. """ # 带有反爬小规则的获取token:前台必须按 "jwt token字符串" 方式提交 # 校验user第1步:从请求头 HTTP_AUTHORIZATION 中拿token,并提取 jwt_value = self.get_jwt_value(request) # 游客 if jwt_value is None: return None # 校验 try: # 校验user第2步:token => payload payload = jwt_decode_handler(jwt_value) except jwt.ExpiredSignature: msg = _(‘Signature has expired.‘) raise exceptions.AuthenticationFailed(msg) except jwt.DecodeError: msg = _(‘Error decoding signature.‘) raise exceptions.AuthenticationFailed(msg) except jwt.InvalidTokenError: raise exceptions.AuthenticationFailed() # 校验user第3步:token => payload user = self.authenticate_credentials(payload) return (user, jwt_value)

# 1)从请求头中获取token # 2)根据token解析出payload:jwt_decode_handler(token) => payloay # from rest_framework_jwt.authentication import jwt_decode_handler # 3)根据payload解析出user:self.authenticate_credentials(payload) => user # 继承drf-jwt的BaseJSONWebTokenAuthentication,拿到父级的authenticate_credentials方法
from django.db import models from django.contrib.auth.models import AbstractUser class User(AbstractUser): mobile = models.CharField(max_length=11, unique=True) class Meta: db_table = ‘api_user‘ verbose_name = ‘用户表‘ verbose_name_plural = verbose_name def __str__(self): return self.username
from rest_framework import serializers from . import models import re # 拿到前台token的两个函数: user => payload => token from rest_framework_jwt.serializers import jwt_payload_handler from rest_framework_jwt.serializers import jwt_encode_handler # 1) 前台提交多种登录信息都采用一个key,所以后台可以自定义反序列化字段进行对应 # 2) 序列化类要处理序列化与反序列化,要在fields中设置model绑定的Model类所有使用到的字段 # 3) 区分序列化字段与反序列化字段 read_only | write_only # 4) 在自定义校验规则中(局部钩子、全局钩子)校验数据是否合法、确定登录的用户、根据用户签发token # 5) 将登录的用户与签发的token保存在序列化类对象中 class UserModelSerializer(serializers.ModelSerializer): # 自定义反序列字段:一定要设置write_only,只参与反序列化,不会与model类字段映射 usr = serializers.CharField(write_only=True) pwd = serializers.CharField(write_only=True) class Meta: model = models.User fields = [‘usr‘, ‘pwd‘, ‘username‘, ‘mobile‘, ‘email‘] # 系统校验规则 extra_kwargs = { ‘username‘: { ‘read_only‘: True }, ‘mobile‘: { ‘read_only‘: True }, ‘email‘: { ‘read_only‘: True }, } def validate(self, attrs): usr = attrs.get(‘usr‘) pwd = attrs.get(‘pwd‘) # 多方式登录:各分支处理得到该方式下对应的用户 if re.match(r‘.+@.+‘, usr): user_query = models.User.objects.filter(email=usr) elif re.match(r‘1[3-9][0-9]{9}‘, usr): user_query = models.User.objects.filter(mobile=usr) else: user_query = models.User.objects.filter(username=usr) user_obj = user_query.first() # 签发:得到登录用户,签发token并存储在实例化对象中 if user_obj and user_obj.check_password(pwd): # 签发token,将token存放到 实例化类对象的token 名字中 payload = jwt_payload_handler(user_obj) token = jwt_encode_handler(payload) # 将当前用户与签发的token都保存在序列化对象中 self.user = user_obj self.token = token return attrs raise serializers.ValidationError({‘data‘: ‘数据有误‘})
#实现多方式登陆签发token:账号、手机号、邮箱等登陆 # 1) 禁用认证与权限组件 # 2) 拿到前台登录信息,交给序列化类 # 3) 序列化类校验得到登录用户与token存放在序列化对象中 # 4) 取出登录用户与token返回给前台 import re from . import serializers, models from utils.response import APIResponse from rest_framework_jwt.serializers import jwt_payload_handler from rest_framework_jwt.serializers import jwt_encode_handler class LoginAPIView(APIView): # 1) 禁用认证与权限组件 authentication_classes = [] permission_classes = [] def post(self, request, *args, **kwargs): # 2) 拿到前台登录信息,交给序列化类,规则:账号用usr传,密码用pwd传 user_ser = serializers.UserModelSerializer(data=request.data) # 3) 序列化类校验得到登录用户与token存放在序列化对象中 user_ser.is_valid(raise_exception=True) # 4) 取出登录用户与token返回给前台 return APIResponse(token=user_ser.token, results=serializers.UserModelSerializer(user_ser.user).data) # "一根筋" 思考方式:所有逻辑都在视图类中处理 def my_post(self, request, *args, **kwargs): usr = request.data.get(‘usr‘) pwd = request.data.get(‘pwd‘) if re.match(r‘.+@.+‘, usr): user_query = models.User.objects.filter(email=usr) elif re.match(r‘1[3-9][0-9]{9}‘, usr): user_query = models.User.objects.filter(mobile=usr) else: user_query = models.User.objects.filter(username=usr) user_obj = user_query.first() if user_obj and user_obj.check_password(pwd): payload = jwt_payload_handler(user_obj) token = jwt_encode_handler(payload) return APIResponse(results={‘username‘: user_obj.username}, token=token) return APIResponse(data_msg=‘不可控错误‘)
import jwt from rest_framework_jwt.authentication import BaseJSONWebTokenAuthentication from rest_framework_jwt.authentication import jwt_decode_handler from rest_framework.exceptions import AuthenticationFailed class JWTAuthentication(BaseJSONWebTokenAuthentication): def authenticate(self, request): jwt_token = request.META.get(‘HTTP_AUTHORIZATION‘) # 自定义校验规则:auth token jwt token = self.parse_jwt_token(jwt_token) if token is None: return None try: # token => payload payload = jwt_decode_handler(token) except jwt.ExpiredSignature: raise AuthenticationFailed(‘token已过期‘) except: raise AuthenticationFailed(‘非法用户‘) # payload => user user = self.authenticate_credentials(payload) return (user, token) # 自定义校验规则:auth token jwt,auth为前盐,jwt为后盐 def parse_jwt_token(self, jwt_token): tokens = jwt_token.split() if len(tokens) != 3 or tokens[0].lower() != ‘auth‘ or tokens[2].lower() != ‘jwt‘: return None return tokens[1]
from rest_framework.views import APIView from utils.response import APIResponse # 必须登录后才能访问 - 通过了认证权限组件 from rest_framework.permissions import IsAuthenticated # 自定义jwt校验规则 from .authentications import JWTAuthentication class UserDetail(APIView): authentication_classes = [JWTAuthentication] permission_classes = [IsAuthenticated] def get(self, request, *args, **kwargs): return APIResponse(results={‘username‘: request.user.username})
以上是关于drf-jwt手动签发与校验的主要内容,如果未能解决你的问题,请参考以下文章
DRF框架——drf-jwt手动签发与校验过滤组件筛选组件排序组件分页组件
drf_jwt手动签发与校验-drf小组件:过滤-筛选-排序-分页