CTFHub--Misc部分wp
Posted pipictf
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了CTFHub--Misc部分wp相关的知识,希望对你有一定的参考价值。
一叶障目
just a rar
鸡你太美
你猜我是个啥
藏藏藏
认真你就输了
签个到
difficult programming language
一叶障目
放到winhex中调一下高度
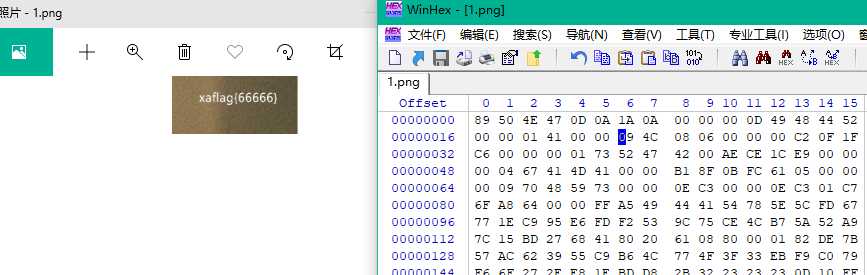
答案: xaflag{66666}
just a rar
下载下来题目,解压压缩包,4位数密码爆破
密码:2016
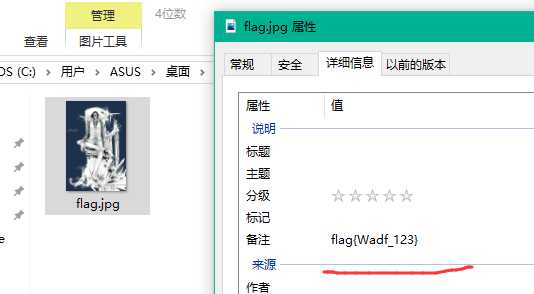
flag{Wadf_123}
鸡你太美
第2个打篮球的gif,副本打不开,通过winhex打开后,发现缺少gif开头
添加4个0字节符,输入gif开头格式:47 49 46 38
保存打开
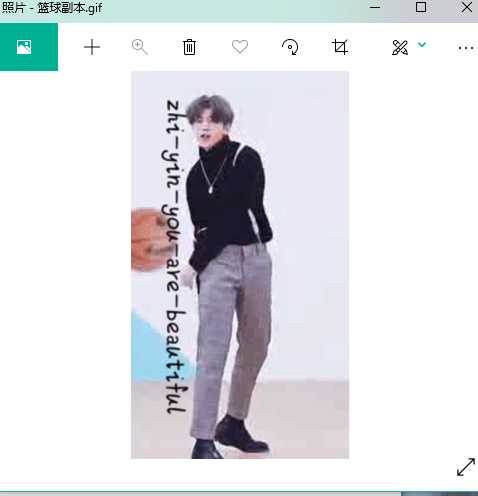
flag如图
你猜我是个啥
正常打开出现错误,尝试用winhex打开
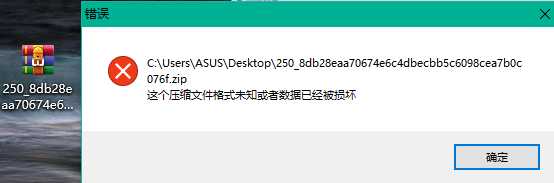
发现文件底部就有flag
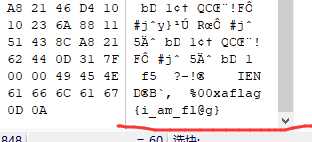
提交即可
藏藏藏
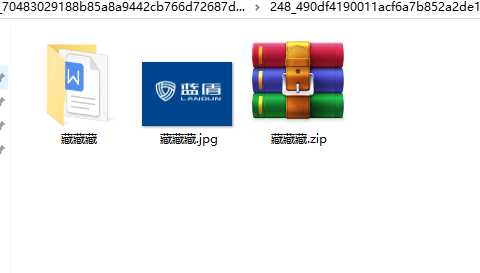
解压改后缀就ok了,这一类题多是这种套路
打开word,扫码即可

认真你就输了
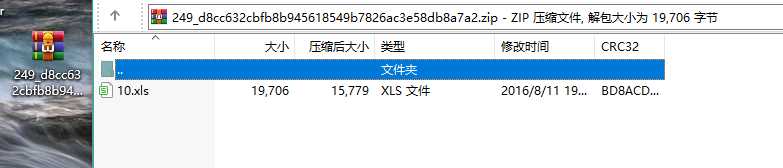
解压发现是个.xls文件,打开后,提示flag就在该表格下,找了一小会儿,也没发现什么
我尝试下了用txt打开,看到里面好多独立的文件,改后缀zip,解压
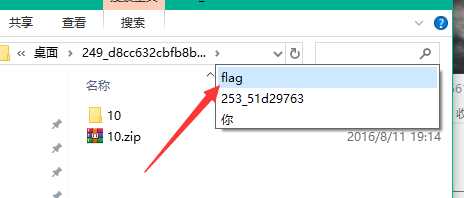
直接搜索flag,秒出答案
flag{M9eVfi2Pcs#}
签个到
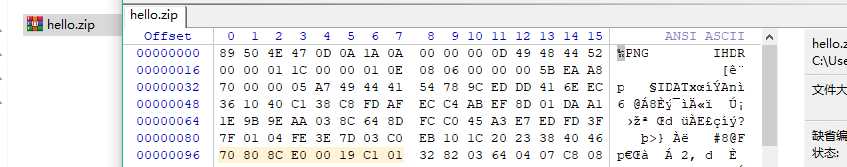
一直解压完事了,到这里,改后缀名为.png 二维码扫描即可

xaflag{i_am_a_tupian}
difficult programming language
题给了一个usb流量包,用tshark命令,将Leftover Capture Date域中的usb协议数据提取出来
tshark -r difficult_programming_language.pcap -T fields -e usb.capdata > usbdata.txt
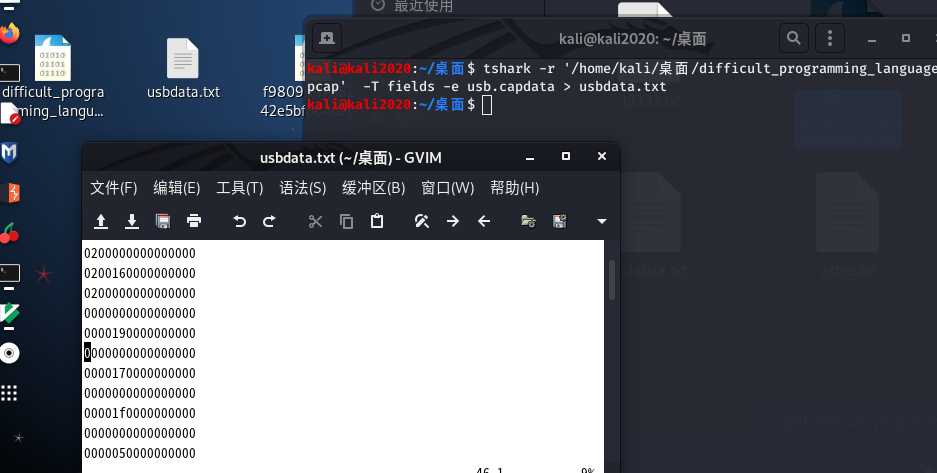
说实话,这个题有点难,复现失败了,不知道是怎么通过usb协议文档可以查找到值和键位的关系
下面贴上MiGo出题人师傅的wp https://www.dazhuanlan.com/2020/01/30/5e326194b93d1
借着把后面的wp补充完整一下
提取出数据后我们通过usb协议文档可以查找到值和键位的关系,编写脚本后得到结果
D’`;M?!mZ4j8hgSvt2bN);^]+7jiE3Ve0A@Q=|;)sxwYXtsl2pongOe+LKa’e^]a`_X|V[Tx;:VONSRQJn1MFKJCBfFE>&<`@9!=<5Y9y7654-,P0/o-,%I)ih&%$#z@xw|{ts9wvXWm3~
联系题目 difficult programming language ,可以搜索到这是一段malbolge语言的代码,找一个在线编译网站跑一下即可得到flag.
hctf{m4lb0lGe}
附上MiGo师傅的脚本
#!/usr/bin/env python import sys import os normalkeys = { 0x04:"a", 0x05:"b", 0x06:"c", 0x07:"d", 0x08:"e", 0x09:"f", 0x0A:"g", 0x0B:"h", 0x0C:"i", 0x0D:"j", 0x0E:"k", 0x0F:"l", 0x10:"m", 0x11:"n",0x12:"o", 0x13:"p", 0x14:"q", 0x15:"r", 0x16:"s", 0x17:"t", 0x18:"u",0x19:"v", 0x1A:"w", 0x1B:"x", 0x1C:"y", 0x1D:"z",0x1E:"1", 0x1F:"2", 0x20:"3", 0x21:"4", 0x22:"5", 0x23:"6", 0x24:"7", 0x25:"8", 0x26:"9", 0x27:"0", 0x28:"n", 0x2a:"[DEL]", 0X2B:" ", 0x2C:" ", 0x2D:"-", 0x2E:"=", 0x2F:"[", 0x30:"]", 0x31:"", 0x32:"`", 0x33:";", 0x34:"‘",0x35:"`", 0x36:",", 0x37:"." , 0x38:"/"} shiftkeys = { 0x04:"A", 0x05:"B", 0x06:"C", 0x07:"D", 0x08:"E", 0x09:"F", 0x0A:"G", 0x0B:"H", 0x0C:"I", 0x0D:"J", 0x0E:"K", 0x0F:"L", 0x10:"M", 0x11:"N",0x12:"O", 0x13:"P", 0x14:"Q", 0x15:"R", 0x16:"S", 0x17:"T", 0x18:"U",0x19:"V", 0x1A:"W", 0x1B:"X", 0x1C:"Y", 0x1D:"Z", 0x1E:"!", 0x1F:"@", 0x20:"#", 0x21:"$", 0x22:"%", 0x23:"^", 0x24:"&", 0x25:"*", 0x26:"(", 0x27:")", 0x28:"n", 0x2a:"[DEL]", 0X2B:" ", 0x2C:" ", 0x2D:"_", 0x2E:"+", 0x2F:"{", 0x30:"}", 0x31:"|", 0x32:"~", 0x33:":", 0x34:""",0x35:"~", 0x36:"<", 0x37:">", 0x38:"?" } nums = [] shift_press = [] keys = open(‘usbdata.txt‘) for line in keys: shift_press.append(line[1]) nums.append(int(line[6:8],16)) keys.close() output = "" m = 0 for n in nums: if n == 0 : m += 1 continue if n in shiftkeys: if shift_press[m] == ‘2‘ : #shift is pressed output += shiftkeys[n] m += 1 elif shift_press[m] == ‘0‘ : output += normalkeys[n] m += 1 print ‘output :n‘ + output
菜鸟的路,还很长,干就完了,
以上是关于CTFHub--Misc部分wp的主要内容,如果未能解决你的问题,请参考以下文章
markdown WordPress片段:使用WP CLI检查数据库
php Wordpress functions.php片段使用Yoast的插件将Google Analytics跟踪添加到wp_nav_menu