基础过滤工具
Posted liujunjun
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了基础过滤工具相关的知识,希望对你有一定的参考价值。

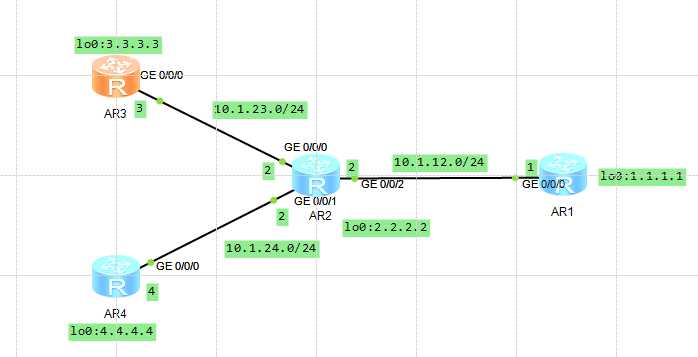
在所有的路由器上运行OSPF协议,通告相应网段到0区域,
配置
AR3 ospf 1 router-id 3.3.3.3 area 0.0.0.0 network 3.3.3.3 0.0.0.0 network 10.1.23.0 0.0.0.255 # AR2配置 ospf 1 router-id 2.2.2.2 area 0.0.0.0 network 2.2.2.0 0.0.0.255 network 10.1.12.0 0.0.0.255 network 10.1.23.0 0.0.0.255 network 10.1.24.0 0.0.0.255 AR1配置 ospf 1 router-id 1.1.1.1 area 0.0.0.0 network 1.1.1.1 0.0.0.0 network 10.1.12.0 0.0.0.255 AR4配置 ospf 1 router-id 4.4.4.4 area 0.0.0.0 network 4.4.4.4 0.0.0.0 network 10.1.24.0 0.0.0.255
在路由器AR4上配置telnet相关配置,配置密码为huawei
[AR1]user-interface vty 0 4 [AR1-ui-vty0-4]authentication-mode password Please configure the login password (maximum length 16):huawei
<AR3>telnet 1.1.1.1 Press CTRL_] to quit telnet mode Trying 1.1.1.1 ... Connected to 1.1.1.1 ... Login authentication Password:
这时发现只要路由可达的设备,并拥有密码,都可以访问R4路由器
AR1上创建ACL 200只允许2.2.2.2访问AR1,其余都禁止
acl number 2000 rule 5 permit source 2.2.2.2 0 rule 10 deny
user-interface vty 0 4 acl 2000 inbound 引用ACL 2000
此时就只有R2可以登录R1,其他路由器均无法登录R1
[AR1]dis acl 2000 Basic ACL 2000, 2 rules Acl‘s step is 5 rule 5 permit source 2.2.2.2 0 (1 matches) rule 10 deny (15 matches)
增加R3,让R3也可以登录R1
[AR1-acl-basic-2000]dis th [V200R003C00] # acl number 2000 rule 5 permit source 2.2.2.2 0 rule 6 permit source 3.3.3.3 0 rule 10 deny
<AR3>telnet -a 3.3.3.3 1.1.1.1 Press CTRL_] to quit telnet mode Trying 1.1.1.1 ... Connected to 1.1.1.1 ... Login authentication Password:
高级ACL
[AR1]dis acl 3000 Advanced ACL 3000, 1 rule Acl‘s step is 5 rule 5 permit tcp source 2.2.2.2 0 destination 1.1.1.1 0 (1 matches)
user-interface vty 0 4 acl 3000 inbound
配置前缀列表
[AR1-ospf-1]dis acl 2000 Basic ACL 2000, 2 rules Acl‘s step is 5 rule 5 deny source 10.1.23.0 0.0.0.255 (1 matches) rule 10 permit (8 matches) spf 1 router-id 1.1.1.1 filter-policy 2000 import
以上是关于基础过滤工具的主要内容,如果未能解决你的问题,请参考以下文章