Linux如何创建私有CA和申请证书
Posted
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了Linux如何创建私有CA和申请证书相关的知识,希望对你有一定的参考价值。
openssl的配置文件:/etc/pki/tls/openssl.cnf
三种策略:匹配、支持和可选。匹配:指要求申请填写的信息跟CA设置信息必须一致;支持:指必须填写这项申请信息;可选:指可有可无。
实验环境:需要两台主机,我这里用主机A(Centos6:ip为172.17.250.83)创建CA并给其他主机提供CA服务;主机B(Centos7:ip为172.17.253.204)为httpd服务器,用来申请证书。
1、首先看一下配置文件的部分内容,其中以下内容在创建CA时是必须要写的:
dir = /etc/pki/CA # Where everything is kept certs = $dir/certs # Where the issued certs are kept crl_dir = $dir/crl # Where the issued crl are kept database = $dir/index.txt # database index file. #unique_subject = no # Set to ‘no‘ to allow creation of # several ctificates with same subject. new_certs_dir = $dir/newcerts # default place for new certs. certificate = $dir/cacert.pem # The CA certificate serial = $dir/serial # The current serial number crlnumber = $dir/crlnumber # the current crl number # must be commented out to leave a V1 CRL crl = $dir/crl.pem # The current CRL private_key = $dir/private/cakey.pem # The private key
2、根据配置文件的需要创建必须的文件。
[[email protected] ~]#touch /etc/pki/CA/index.txt #生成证书索引数据库的文件 [[email protected] ~]#echo 01 > /etc/pki/CA/serial #指定第一个颁发证书的序列号 [[email protected] ~]#tree /etc/pki/CA/ /etc/pki/CA/ ├── certs ├── crl ├── index.txt ├── newcerts ├── private └── serial 4 directories, 2 files
注意:创建的这两个文件,包括接下的实验里创建的文件名一定要与配置文件中的文件名一样。
3、在主机A(Centos6)上创建CA服务,并自签证书
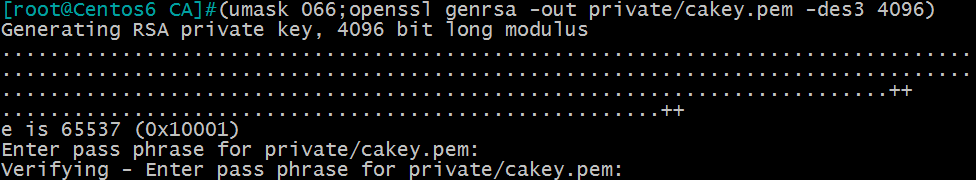
(1)生成私钥
[[email protected] ~]#(umask 066;openssl genrsa -out private/cakey.pem -des3 4096) #-des3是对文件进行加密
注意:用小括号说明是在子shell中执行括号内的命令,不会影响父shell的设置;将umask设置为066是为了防止其他人有权限查看和修改生成的私钥;在4096前还可以给私钥加上加密算法,比如des3、 rsa等,本例子用了des3加密。
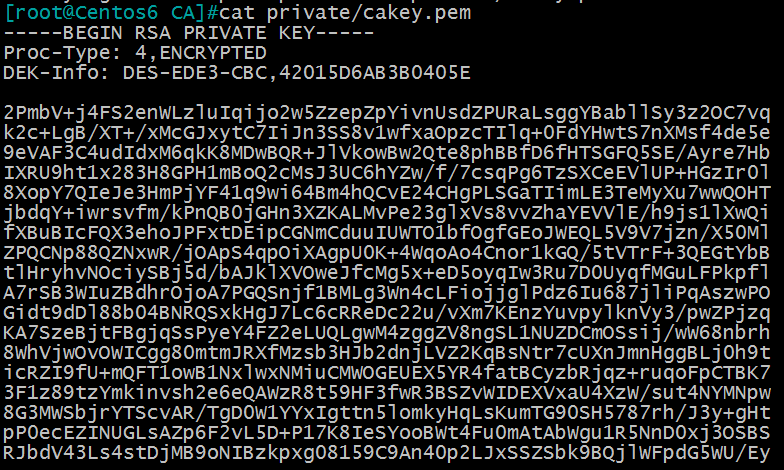
可以看一下加密过后的部分文本:
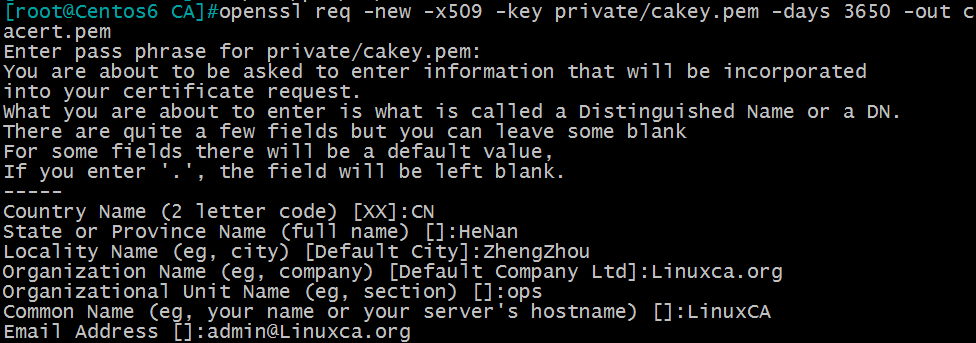
(2)生成自签证书
[[email protected] ~]#openssl req -new -x509 -key private/cakey.pem -days 3650 -out cacert.pem
其中:-new: 生成新证书签署请求
-x509: 专用于CA生成自签证书
-key: 生成请求时用到的私钥文件
-days n:证书的有效期限
-out /PATH/TO/SOMECERTFILE: 证书的保存路径
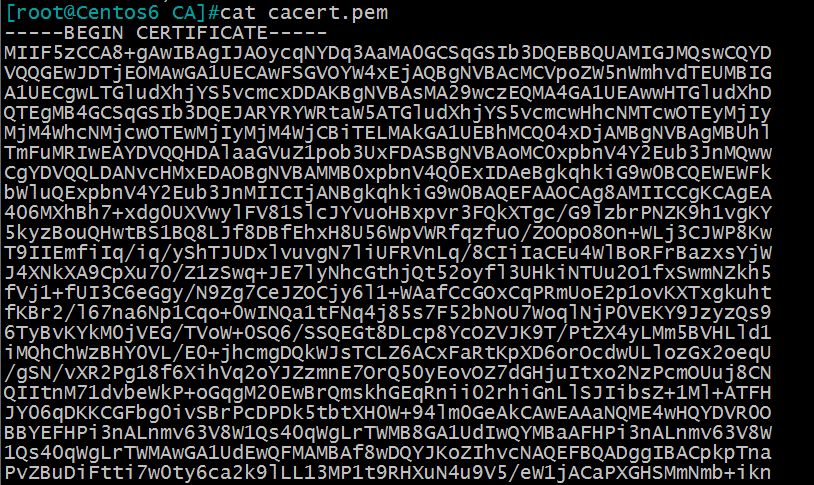
查看一下证书的部分加密文本:
(3)把cacert.pem文件传输到windows上,由于在windows上不能识别.pem为后缀的文本,所以这里我们要把该文本改成以.cer为后缀的文本,修改后的文件图标为 。
。
在windows上打开证书看一下。
4、在需要使用证书的主机B(Centos7)上生成证书请求
(1)给httpd服务生成私钥
[[email protected] ~]#(umask 066;openssl genrsa -out /etc/pki/tls/private/test.key -des3 4096) Generating RSA private key, 4096 bit long modulus ..........................................................++ ...........................................................................................................................................................................................................................++ e is 65537 (0x10001) Enter pass phrase for /etc/pki/tls/private/test.key: Verifying - Enter pass phrase for /etc/pki/tls/private/test.key:
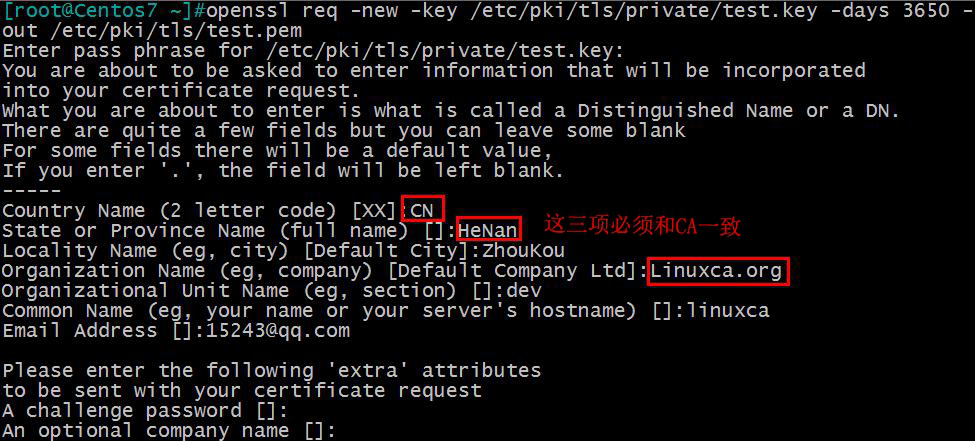
(2)生成证书申请文件
[[email protected] ~]#openssl req -new -key /etc/pki/tls/private/test.key -days 3650 -out /etc/pki/tls/test.pem
(3)将证书请求文件传输给CA
[[email protected] ~]#scp /etc/pki/tls/test.pem @172.17.250.83:/etc/pki/tls/ The authenticity of host ‘172.17.250.83 (172.17.250.83)‘ can‘t be established. RSA key fingerprint is 09:52:06:53:a1:13:99:f3:b9:5c:5f:0a:c4:b6:1c:ed. Are you sure you want to continue connecting (yes/no)? yes Warning: Permanently added ‘172.17.250.83‘ (RSA) to the list of known hosts. [email protected]‘s password: test.pem 100% 1736 1.7KB/s 00:00
5、在主机A(Centos6)上签署证书,并颁发给证书申请者(主机B)
(1)签署证书
[[email protected] ~]#openssl ca -in /etc/pki/tls/test.pem -out /etc/pki/CA/certs/test.crt -days 3650 Using configuration from /etc/pki/tls/openssl.cnf Enter pass phrase for /etc/pki/CA/private/cakey.pem: Check that the request matches the signature Signature ok Certificate Details: Serial Number: 1 (0x1) Validity Not Before: Sep 12 23:04:23 2017 GMT Not After : Sep 10 23:04:23 2027 GMT Subject: countryName = CN stateOrProvinceName = HeNan organizationName = Linuxca.org organizationalUnitName = dev commonName = linuxca emailAddress = [email protected] X509v3 extensions: X509v3 Basic Constraints: CA:FALSE Netscape Comment: OpenSSL Generated Certificate X509v3 Subject Key Identifier: 97:B6:0A:0A:70:C6:FB:29:BB:B9:4A:26:98:3E:73:8B:20:F4:37:5E X509v3 Authority Key Identifier: keyid:73:E2:DE:70:0B:9E:6B:FA:DD:5F:16:D5:0B:38:D2:A5:A0:2E:B4:D6 Certificate is to be certified until Sep 10 23:04:23 2027 GMT (3650 days) Sign the certificate? [y/n]:y 1 out of 1 certificate requests certified, commit? [y/n]y Write out database with 1 new entries Data Base Updated
(2)把证书颁发给主机B(Centos7)
[[email protected] CA]#scp certs/test.crt @172.17.253.204:/etc/pki/CA/ The authenticity of host ‘172.17.253.204 (172.17.253.204)‘ can‘t be established. RSA key fingerprint is 91:d3:76:ba:60:12:0d:13:9b:93:6a:39:71:18:fe:65. Are you sure you want to continue connecting (yes/no)? yes Warning: Permanently added ‘172.17.253.204‘ (RSA) to the list of known hosts. [email protected]‘s password: test.crt 100% 7311 7.1KB/s 00:00
(3)在主机B(Centos7)上查看证书中的信息,
openssl x509 -in /PATH/FROM/CERT_FILE
-text|issuer|subject|serial|dates
opensslca -status SERIAL查看指定编号的证书状态
[[email protected] CA]#openssl x509 -in test.crt -text
至此,CA的创建和申请、颁发就完成了。
以上是关于Linux如何创建私有CA和申请证书的主要内容,如果未能解决你的问题,请参考以下文章