BUUCTF GWCTF-xxor-WP
Posted 水番正文
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了BUUCTF GWCTF-xxor-WP相关的知识,希望对你有一定的参考价值。
打开程序无壳直接丢进ida64
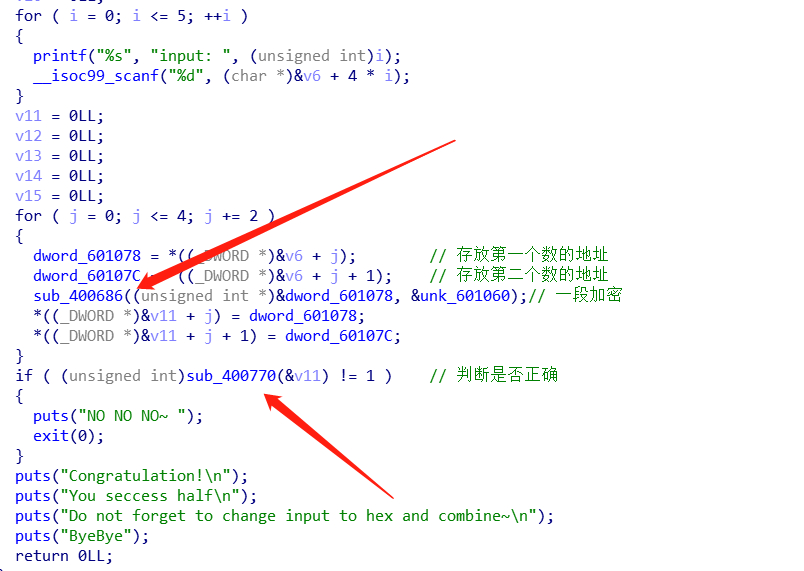
关键地方就两个,观看一下程序就可以了解大概流程
数据在400770

用z3或手解获得6个数
得到数组后确认无其他乱七八糟的移位
就可以看看加密了
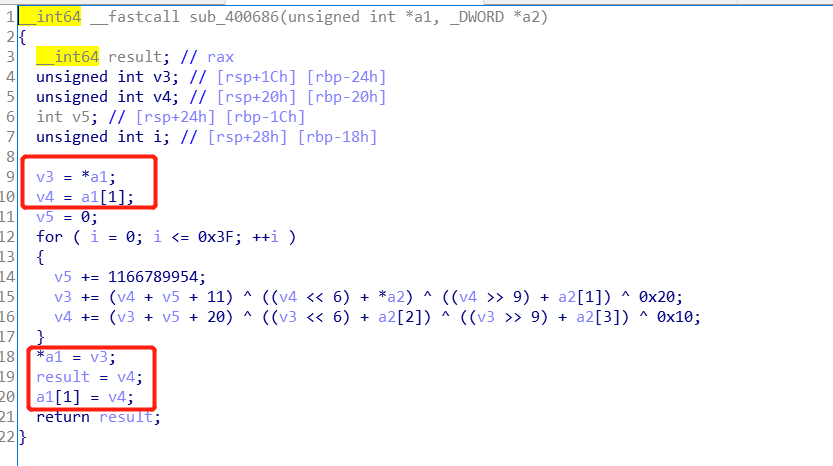
就是丢进来的两个数加密后再赋值
就是逆这段异或了
有个a2数组注意,4字节所以
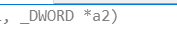
这样才是正确看法
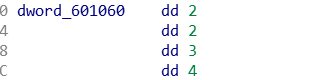
循环64次,所有数都是加,所以逆就是减
大概流程就是
1.v5等于最后一次的数开始
2.v4放上面 v3放下面
注意一个点这里的数都是无符号数
上exp!
#include <stdio.h>
int main(void)
{
int a1[6];
a1[0] = 0xDF48EF7E;
a1[1] = 0x20CAACF4;
a1[5] = 0x84F30420;
//a1[0] = 3746099070;
//a1[1] = 550153460;
//a1[5] = 2230518816;
int n1,n2; //无符号数和符号数结果不一样!??
n1 = 0x42D731A8 + 0xFA6CB703; //a[2]+a[3]
//a1[2] - a1[4] = 0x42D731A8
//a1[3] + a1[4] = 0xFA6CB703
//a1[2] - a1[3] = 0x84A236FF
n2 = n1 + 0x84A236FF; //2a[2]
a1[2] = n2/2;
a1[3] = a1[2] - 0x84A236FF;
a1[4] = a1[2] - 0x42D731A8;
//a1[4] = 2652626477;
//a1[2] = 3774025685;
//a1[3] = 1548802262;
int i,j;
int a2[] = {2,2,3,4};
int v5 = 0;
unsigned int v3,v4; //注意要和题中一样
for(j = 4;j >= 0;j -= 2)
{
v3 = a1[j];
v4 = a1[j+1];
for (i = 63; i >= 0; i-- )
{
v5 = 0x458BCD42*(i+1);
v4 -= (v3 + v5 + 20) ^ ((v3 << 6) + a2[2]) ^ ((v3 >> 9) + a2[3]) ^ 0x10;
v3 -= (v4 + v5 + 11) ^ ((v4 << 6) + a2[0]) ^ ((v4 >> 9) + a2[1]) ^ 0x20;
}
a1[j] = v3;
a1[j+1] = v4;
}
for(i=0;i<=5;i++)
printf("%x ",a1[i]);
printf("\\n");
for(i = 0;i<=5;i++)
{
printf("%c%c%c",*((char*)&a1[i]) , *((char*)&a1[i]+1) , *((char*)&a1[i]+2));
}
printf("\\n");
for(i = 0;i<=5;i++)
{
printf("%c%c%c",*((char*)&a1[i]+2) , *((char*)&a1[i]+1) , *((char*)&a1[i]));
}
}以上是关于BUUCTF GWCTF-xxor-WP的主要内容,如果未能解决你的问题,请参考以下文章