linux命令:CA证书制作及httpd服务器证书签核实例
Posted
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了linux命令:CA证书制作及httpd服务器证书签核实例相关的知识,希望对你有一定的参考价值。
实例:
实现httpd服务器,CA证书服务器,客户端访问httpd网页站点证书有效登录,
证书的安装及发放。openssl证书搭配https服务器配置。
准备工作:需要准备2台服务器;
1、第一台服务器先安装好httpd服务,上一章提到了httpd服务器配置与安装。
这里就不详细解释如何安装httpd和配置httpd服务器IP:10.109.134.249
2、第二台服务器作为CA证书签核服务器,CA证书服务器IP地址:10.109.134.236
1、先确认httpd是否安装过ssl模块(10.109.134.249服务器)
[[email protected] ~]# httpd -M |grep ssl #查询httpd服务器是否装有ssl模块
Loaded Modules:
.........
proxy_ajp_module (shared)
python_module (shared)
ssl_module (shared) #该服务器已经装了ssl服务模块
Syntax OK
如果没有安装必须先安装httpd服务器的ssl服务模块:
[[email protected] ~]# yum install mod_ssl #安装ssl模块
Loaded plugins: rhnplugin, security
This system is not registered with RHN.
RHN support will be disabled.
Setting up Install Process
Package1:mod_ssl-2.2.3-31.el5.x86_64 already installed and latest version#表示已安装ssl模块
[[email protected] ~]# rpm -ql mod_ssl #查看mod_ssl模块安装了那些文件
/etc/httpd/conf.d/ssl.conf
/usr/lib64/httpd/modules/mod_ssl.so
/var/cache/mod_ssl
/var/cache/mod_ssl/scache.dir
/var/cache/mod_ssl/scache.pag
/var/cache/mod_ssl/scache.sem
2、登录第二台服务器做CA证书服务器(10.109.134.236服务器)并配置好:
[[email protected] ~]# cd /etc/pki
[[email protected] pki]# cd CA
[[email protected] CA]# pwd
/etc/pki/CA
[[email protected] CA]# (umask 077; openssl genrsa -out private/cakey.pem 2048) #生成私钥;umask077表示生产私钥权限为600,genrsa证书加密格式,-out保存路径及文件名 2048私钥长度
Generating RSA private key, 2048 bit long modulus
...............................................+++
.......+++
e is 65537 (0x10001)
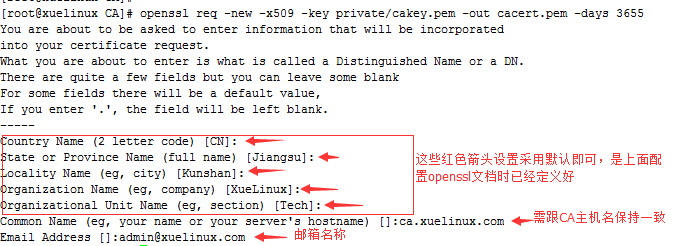
[[email protected] CA]#vim /etc/pki/tls/openssl.cnf #编辑openssl配置文件,红色部分是更改的地方
[ req_distinguished_name ]
countryName = Country Name (2 letter code)
countryName_default = CN #国家
countryName_min = 2
countryName_max = 2
stateOrProvinceName = State or Province Name (full name)
stateOrProvinceName_default = Jiangsu #省份
localityName = Locality Name (eg, city)
localityName_default = Kunshan #城市
0.organizationName = Organization Name (eg, company)
0.organizationName_default = XueLinux #组织
# we can do this but it is not needed normally :-)
#1.organizationName = Second Organization Name (eg, company)
#1.organizationName_default = World Wide Web Pty Ltd
organizationalUnitName = Organizational Unit Name (eg, section)
organizationalUnitName_default = Tech #部门
[[email protected] CA]# vim /etc/pki/tls/openssl.cnf #修改CA证书路径为绝对路径
[[email protected] CA]# openssl req -new -x509 -key private/cakey.pem -out cacert.pem -days 3655 #跟据cakey.pem私钥生成自签证书cacert.pem,其他默认格式,-days是证书有效期(天)
[[email protected] CA]# mkdir certs crl newcerts #创建3个证书相关的目录
[[email protected] CA]# touch index.txt
[[email protected] CA]# echo 01 > serial #下一个证书编号为01
[[email protected] CA]# ls #确保/etc/pki/CA目录下有以下文件及目录
cacert.pem certs crl index.txt newcerts private serial
3、重新登录到httpd服务器(10.109.134.249)端,进行相关私钥的设置:
[[email protected] ~]# cd /etc/httpd
[[email protected] httpd]# ls
conf conf.d logs modules run
[[email protected] httpd]# mkdir ssl #建立ssl目录
[[email protected] httpd]# cd ssl/
[[email protected] ssl]# (umask 077; openssl genrsa 1024 > httpd.key) #生成私钥文件
Generating RSA private key, 1024 bit long modulus
.............................++++++
..............................................++++++
e is 65537 (0x10001)
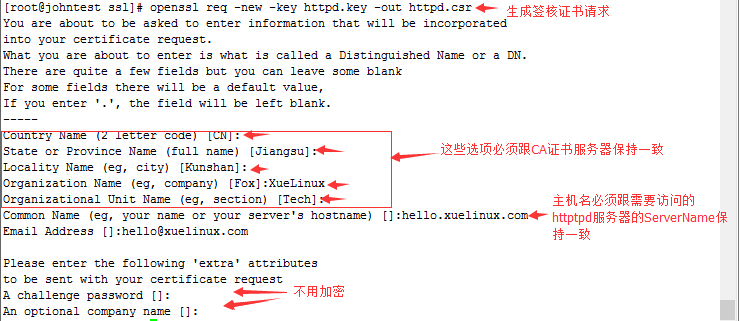
[[email protected] ssl]# openssl req -new -key httpd.key -out httpd.csr #生成证书签核请求
[[email protected] ssl]# ls
httpd.csr httpd.key
[[email protected] ssl]# scp httpd.crs 10.109.134.236:/tmp #把生成的证书签核请求文件复制
到CA证书服务器的/tmp目录下
[email protected]‘s password:
httpd.crs 100% 3892 3.8KB/s 00:00
4、登录CA证书服务器端(10.109.134.236),对生成的证书签核请求进行签核:
[[email protected] ~]# cd /tmp
[[email protected] tmp]# ls
httpd.csr lost+found
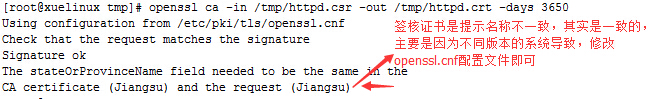
[[email protected] tmp]# openssl ca -in /tmp/httpd.csr -out /tmp/httpd.crt -days 3650 #签核证书申请,并生成证书文件httpd.crt,-days证书有效期,如提示以下错误,需修改配置文件
[[email protected] tmp]#cd /etc/pki/CA
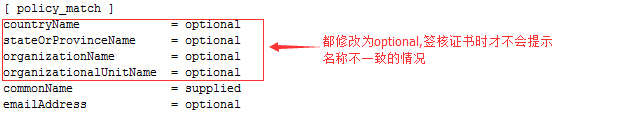
[[email protected] CA]# vim /etc/pki/tls/openssl.cnf #修改配置文件,具体如下图,
全部修改为optional:
[[email protected] CA]# openssl ca -in /tmp/httpd.csr -out /tmp/httpd.crt -days 3650
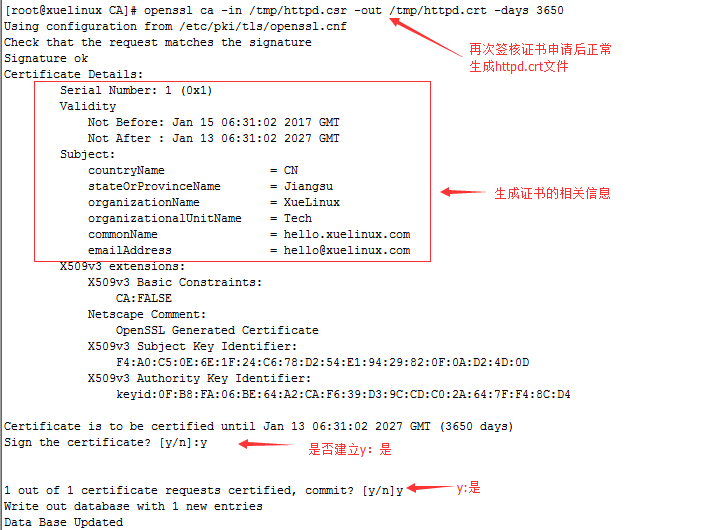 [[email protected] CA]# cat index.txt #查看签核证书记录文件,已经生成一条证书签核记录
[[email protected] CA]# cat index.txt #查看签核证书记录文件,已经生成一条证书签核记录
V270113063102Z01unknown/C=CN/ST=Jiangsu/O=XueLinux/OU=Tech/CN=hello.xuelinux.com/[email protected]
[[email protected] CA]# cat serial #查看证书版本号,下一个证书号为02
02
[[email protected] CA]# scp /tmp/httpd.crt 10.109.134.249:/etc/httpd/ssl/ #把签核好的证书文 件httpd.crt从CA服务器拷贝到httpd服务器/etc/httpd/ssl/目录下
The authenticity of host ‘10.109.134.249 (10.109.134.249)‘ can‘t be established.
RSA key fingerprint is 5c:ec:b4:96:87:ae:6a:f8:66:09:d9:7a:f8:39:21:ae.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added ‘10.109.134.249‘ (RSA) to the list of known hosts.
[email protected]‘s password:
httpd.crt 100% 3892 3.8KB/s 00:00 #拷贝完成
[[email protected] CA]# ls newcerts/ #查看是否有生成证书的记录01.pem生成的第一个证书记录
01.pem
[[email protected] CA]# cd /tmp
[[email protected] tmp]# ls
httpd.crt httpd.csr lost+found
[[email protected] tmp]# rm -rf httpd.c* #需把临时目录下的证书文件清除,以免被别人获取
[[email protected] tmp]# ls
lost+found
5、登录到httpd服务器端(10.109.134.249),对ssl配置文件进行修改:
[[email protected] ssl]# ls
httpd.crt httpd.csr httpd.key
[[email protected] ssl]# cd /etc/httpd/conf.d
[[email protected] conf.d]# ls
manual.conf php.conf python.conf squid.conf virtual.conf welcome.conf
perl.conf proxy_ajp.conf README ssl.conf webalizer.conf
[[email protected] conf.d]# cp ssl.conf ssl.conf.back #修改配置文件前先复制一份以免错误可以恢复
[[email protected] conf.d]# ls
manual.conf php.conf python.conf squid.conf ssl.conf.back webalizer.conf
perl.conf proxy_ajp.conf README ssl.conf virtual.conf welcome.conf
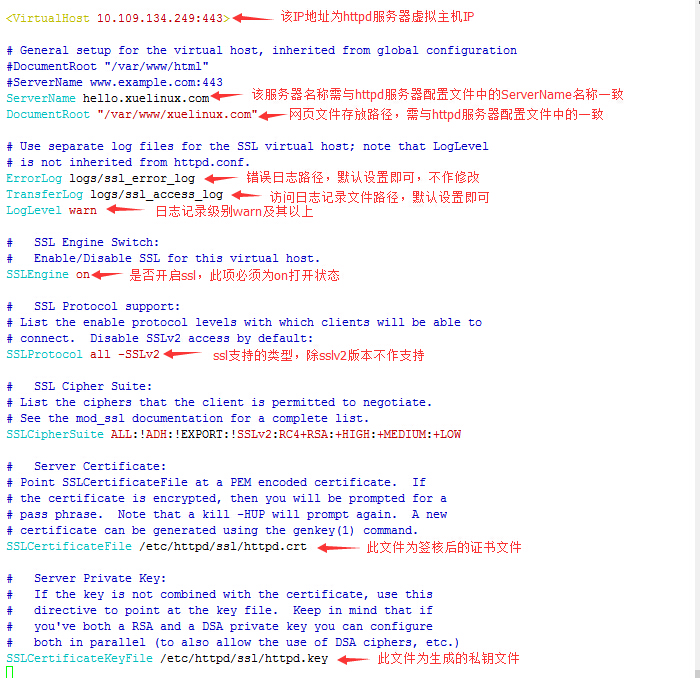
[[email protected] conf.d]# vim /etc/httpd/conf.d/ssl.conf #修改配置文件ssl.conf,
如下图位置需做修改:
 [[email protected] conf.d]# httpd -t #检查httpd配置文件是否有语法错误
[[email protected] conf.d]# httpd -t #检查httpd配置文件是否有语法错误
Syntax OK
[[email protected] conf.d]# service httpd restart #重启httpd服务
停止 httpd: [OK]
启动 httpd: [OK]
[[email protected] conf.d]# netstat -tlnp #查看主机是否监听了443端口
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 127.0.0.1:2208 0.0.0.0:* LISTEN 3575/hpiod ........
........
tcp 0 0 :::8080 :::* LISTEN 9470/httpd
tcp 0 0 :::80 :::* LISTEN 9470/httpd
tcp 0 0 :::22 :::* LISTEN 3617/sshd
tcp 0 0 :::443 :::* LISTEN 9470/httpd
至此httpd服务器端和CA证书服务器端配置完成。
以下为在客户端测试结果:
1、先修改客户端的C:\Windows\System32\drivers\etc\hosts文件,在最后面添加一行并保存退出:
10.109.134.249 hello.xuelinux.com
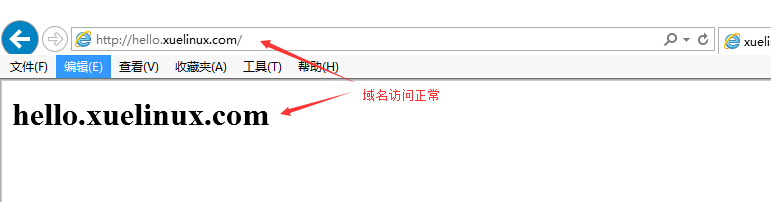
没有安装证书访问网页显示如下:
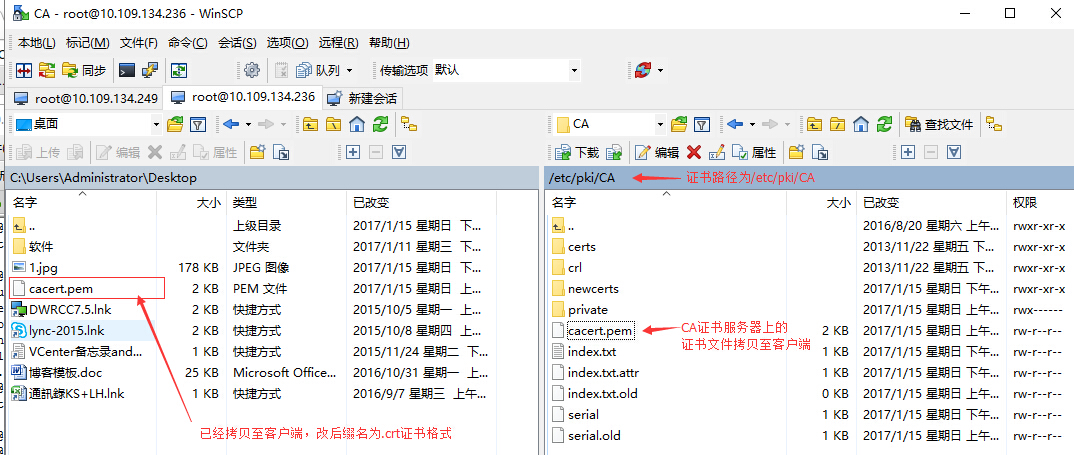
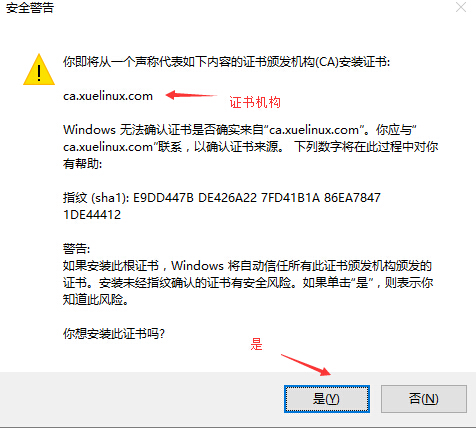
把CA证书服务器上生成的证书文件/etc/pki/CA/cacert.pem拷贝到客户端后,并改名后缀名为
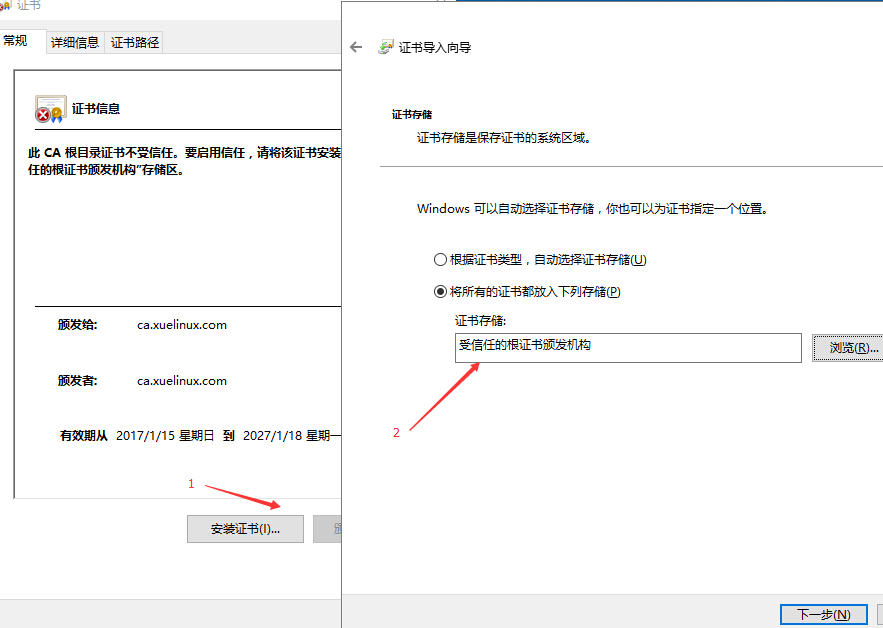
cacert.crt,然后点击安装安装证书至受信任机构中即可:
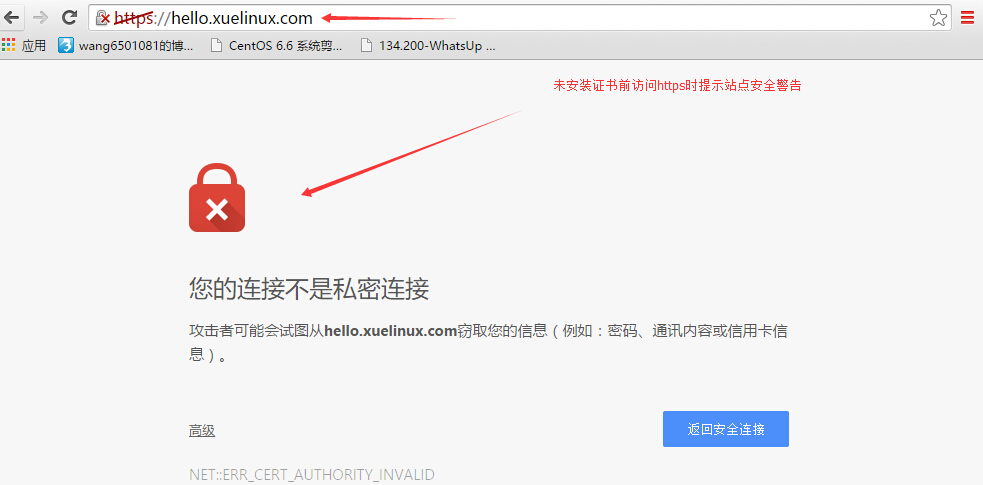
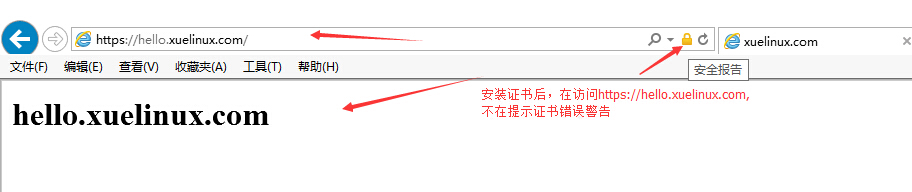
安装完证书后,再打开https://hello.xuelinux.com,如下图:
至此成功实现了通过CA证书服务器签核证书,并通过httpd服务器验证,客户端访问操作。
本文出自 “学linux历程” 博客,请务必保留此出处http://woyaoxuelinux.blog.51cto.com/5663865/1892091
以上是关于linux命令:CA证书制作及httpd服务器证书签核实例的主要内容,如果未能解决你的问题,请参考以下文章