思科下一代模拟器EVE-NG做一个ASAIPsecIKEv2点对点互联实验
Posted gsls200808
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了思科下一代模拟器EVE-NG做一个ASAIPsecIKEv2点对点互联实验相关的知识,希望对你有一定的参考价值。
接上一篇实验,实验的内网只做了单个网段的配置,协议是ike v1的,这边和上一篇不同的是
协议使用v2,并且局域网内网支持多网段。
依旧是网络拓扑图
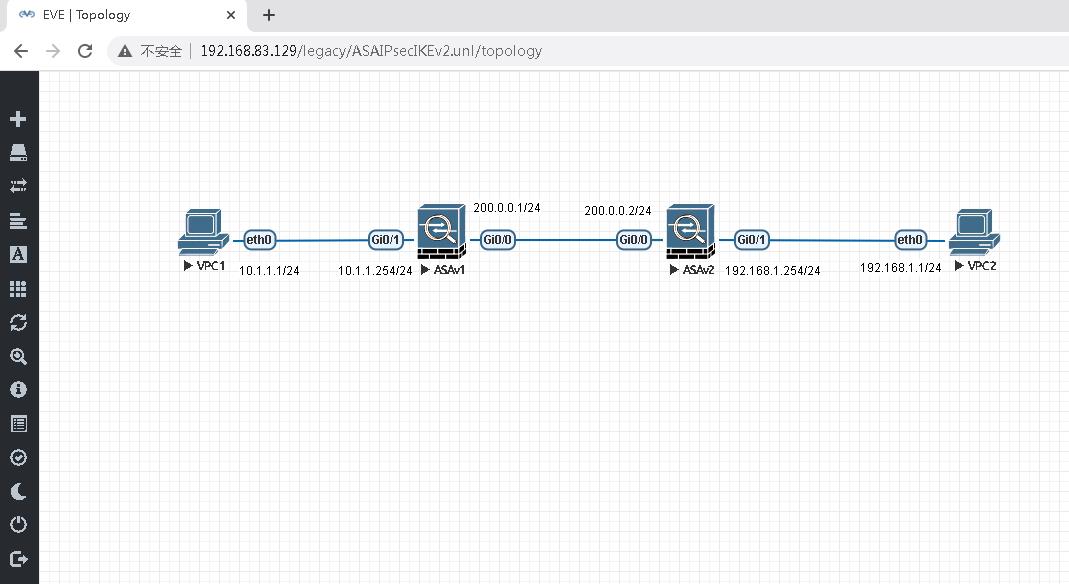
实现目标,VPC1和VPC2相互ping通
1.防火墙1 asa1配置
#主机名,网卡ip配置
hostname asa1
interface GigabitEthernet0/0
nameif outside
security-level 0
ip address 200.0.0.1 255.255.255.0
no shutdown
interface GigabitEthernet0/1
nameif inside
security-level 100
ip address 10.1.1.254 255.255.255.0
no shutdown
#路由配置 设置静态路由,下一跳地址为200.0.0.2
route outside 0 0 200.0.0.2
//以下是定义object,方便后面调用
object network Inside_network
subnet 10.1.0.0 255.255.0.0
object-group network SH_Internal //定义远端子网网段
network-object 192.168.1.0 255.255.255.0
network-object 192.168.2.0 255.255.255.0
object-group network SY_Internal //定义本端子网网段
network-object 10.1.1.0 255.255.255.0
network-object 10.1.2.0 255.255.255.0
access-list 110 extended permit ip any any
access-list IPSEC_IKEV2_V extended permit ip object-group SY_Internal object-group SH_Internal //定义感兴趣流
nat (inside,outside) source static SY_Internal SY_Internal destination static SH_Internal SH_Internal //将数据流和NAT分离
object network Inside_network
nat (inside,outside) dynamic interface //设置PAT
access-group 110 in interface outside
crypto ipsec ikev2 ipsec-proposal ESP_AES256_SHA //定义ipsec转换集
protocol esp encryption aes-256
protocol esp integrity md5
crypto map VMAP 10 match address IPSEC_IKEV2_V //定义crypto map,此处的“IPSEC_IKEV2_V”便是刚才创建的感兴趣流的ACL的名称
crypto map VMAP 10 set peer 200.0.0.2 //设置对端出口ip
crypto map VMAP 10 set ikev2 ipsec-proposal ESP_AES256_SHA //调用刚才创建的ipsec转换集
crypto map VMAP interface outside //将其运用到outside端
crypto ikev2 policy 10 //定义ikev2策略
encryption aes-256
integrity sha256 md5
group 2
prf sha256 md5
lifetime seconds 86400
crypto ikev2 enable outside //在outside端口启用ikev2,这个很重要,如果不启用,其余都是浮云
tunnel-group 200.0.0.2 type ipsec-l2l //定义组类型
tunnel-group 200.0.0.2 ipsec-attributes //定义组属性
ikev2 remote-authentication pre-shared-key cisco
ikev2 local-authentication pre-shared-key cisco
#允许ping配置
access-list OUTSIDE_IN_ACL permit icmp any any echo-reply
access-group OUTSIDE_IN_ACL in interface outside
#保存
wr
#重启
reload
2.防火墙2 asa2配置
hostname asa2
interface GigabitEthernet0/0
nameif outside
security-level 0
ip address 200.0.0.2 255.255.255.0
no shutdown
interface GigabitEthernet0/1
nameif inside
security-level 100
ip address 192.168.1.254 255.255.255.0
no shutdown
#路由配置 设置静态路由,下一跳地址为200.0.0.1
route outside 0 0 200.0.0.1
//以下是定义object,方便后面调用
object network Inside_network
subnet 192.168.0.0 255.255.0.0
object-group network SY_Internal //定义远端子网网段
network-object 10.1.1.0 255.255.255.0
network-object 10.1.2.0 255.255.255.0
object-group network SH_Internal //定义本端子网网段
network-object 192.168.1.0 255.255.255.0
network-object 192.168.2.0 255.255.255.0
access-list 110 extended permit ip any any
access-list IPSEC_IKEV2_V extended permit ip object-group SH_Internal object-group SY_Internal //定义感兴趣流
nat (inside,outside) source static SH_Internal SH_Internal destination static SY_Internal SY_Internal //将数据流和NAT分离
object network Inside_network
nat (inside,outside) dynamic interface //设置PAT
access-group 110 in interface outside
crypto ipsec ikev2 ipsec-proposal ESP_AES256_SHA //定义ipsec转换集
protocol esp encryption aes-256
protocol esp integrity md5
crypto map VMAP 10 match address IPSEC_IKEV2_V //定义crypto map,此处的“IPSEC_IKEV2_V”便是刚才创建的感兴趣流的ACL的名称
crypto map VMAP 10 set peer 200.0.0.1 //设置对端出口ip
crypto map VMAP 10 set ikev2 ipsec-proposal ESP_AES256_SHA //调用刚才创建的ipsec转换集
crypto map VMAP interface outside //将其运用到outside端
crypto ikev2 policy 10 //定义ikev2策略
encryption aes-256
integrity sha256 md5
group 2
prf sha256 md5
lifetime seconds 86400
crypto ikev2 enable outside //在outside端口启用ikev2,这个很重要,如果不启用,其余都是浮云
tunnel-group 200.0.0.1 type ipsec-l2l //定义组类型
tunnel-group 200.0.0.1 ipsec-attributes //定义组属性 本段和对端的预共享密钥
ikev2 remote-authentication pre-shared-key cisco
ikev2 local-authentication pre-shared-key cisco
#允许ping配置
access-list OUTSIDE_IN_ACL permit icmp any any echo-reply
access-group OUTSIDE_IN_ACL in interface outside
#保存
wr
#重启
reload3.VPC1配置
ip 10.1.1.1/24 10.1.1.254
save4.VPC2配置
ip 192.168.1.1/24 192.168.1.254
save5.互ping测试
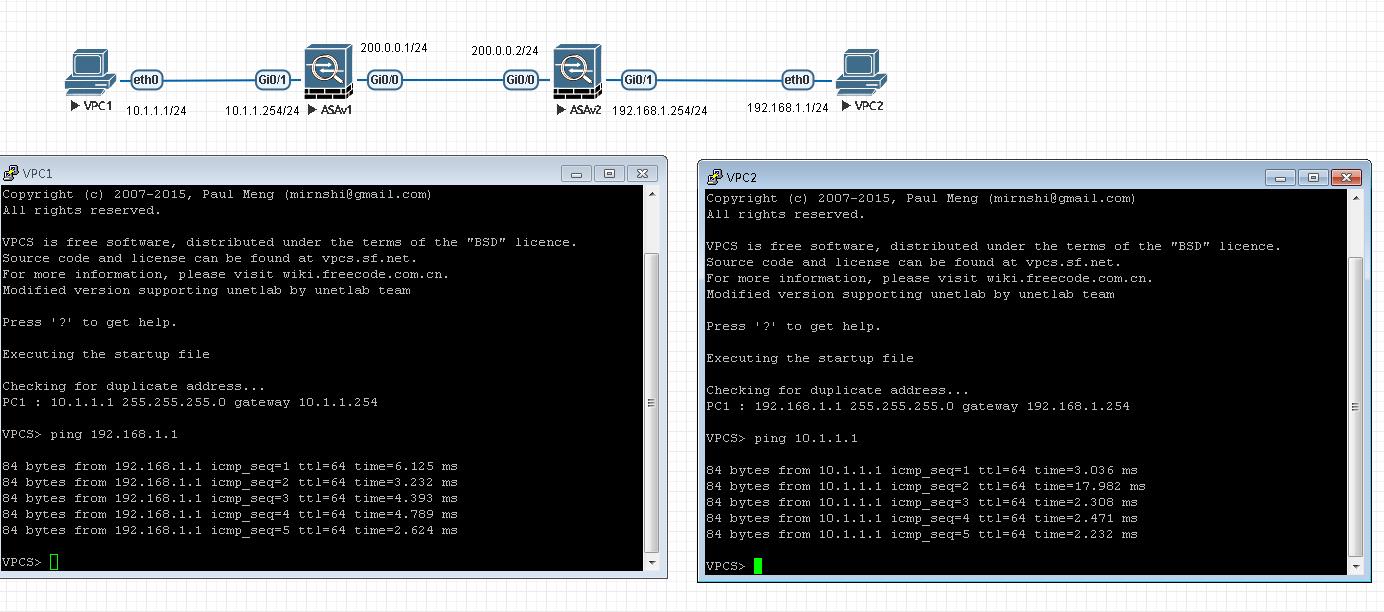
6.查看管理连接sa的状态
show crypto isakmp sa 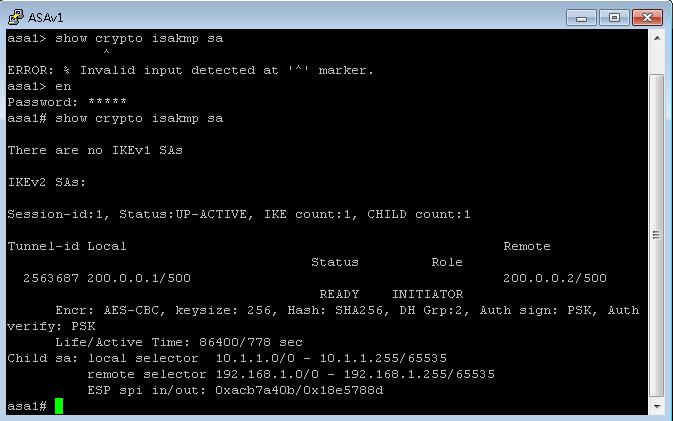
以上是关于思科下一代模拟器EVE-NG做一个ASAIPsecIKEv2点对点互联实验的主要内容,如果未能解决你的问题,请参考以下文章