Centos7+Apache实现HTTPS
Posted
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了Centos7+Apache实现HTTPS相关的知识,希望对你有一定的参考价值。
参考技术A 一、安装apache,已安装略过。未安装的看这篇文章 centOS7-安装apache+php 。二、安装Apache支持SSL/TLS
yum install mod_ssl openssl
三、编辑SSL配置文件
vi /etc/httpd/conf.d/ssl.conf
四、创建CA证书、CA证书签名
linux架构学习第二十六天之web服务搭建(apache)以及https的实现
内容:
1、httpd版本以及安装
2、httpd的配置文件详解
3、httpd的用户身份验证实现
4、httpd的虚拟主机的实现
5、https的通信过程以及实现演示
1、httpd版本以及安装
centos默认的httpd版本是2.2,而centos默认的httpd版本是2.4,这里演示的是centos6的httpd-2.2版本
安装的方式有两种,一个是rpm包安装,一个是编译安装,编译安装相关的配置文件需要手动设置,这里演示的是rpm包安装
httpd2.2和2.4的区别:
2.2的MPM是非DSO机制,不支持LoadModule进行切换;
2.2和2.4的基于IP的访问控制机制命令格式有所不同
虚拟主机配置格式有点不同:
基于ServerName的虚拟主机,要使用专用指令NameVirtualHost;
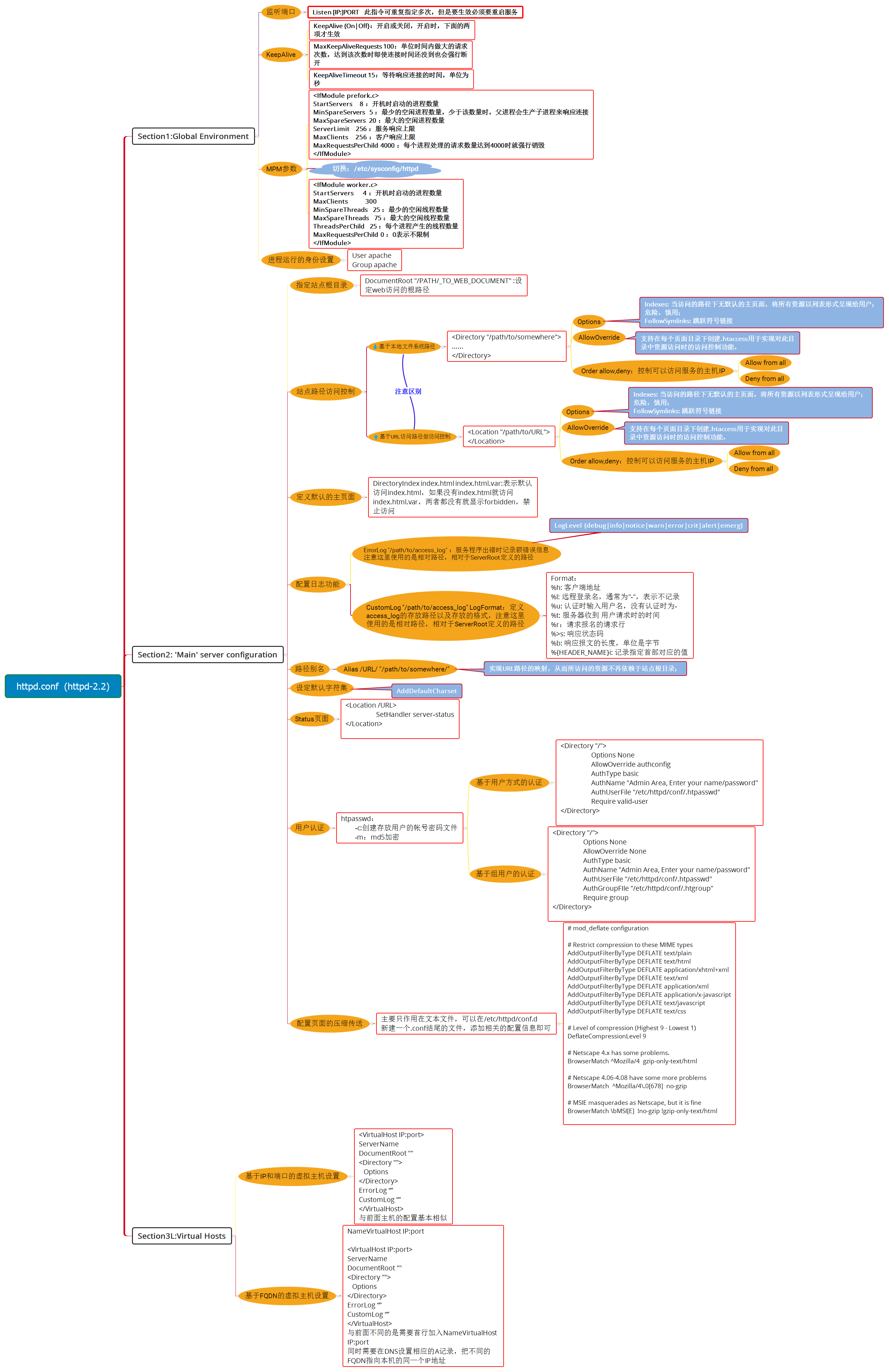
2、httpd的配置文件详解
[07:18 [email protected]~]# rpm -ql httpd /etc/httpd /etc/httpd/conf /etc/httpd/conf.d /etc/httpd/conf.d/README /etc/httpd/conf.d/welcome.conf /etc/httpd/conf/httpd.conf /etc/httpd/conf/magic /etc/httpd/logs /etc/httpd/modules /etc/httpd/run /usr/lib64/httpd /usr/sbin/httpd /usr/sbin/httpd.event /usr/sbin/httpd.worker /var/log/httpd /var/run/httpd /var/www/html
httpd的主要配置文件有几类:
应用程序的文件:/usr/sbin/httpd
配置文件:/etc/httpd/conf.d/*.conf和/etc/httpd/conf/httpd.conf
日志文件:/var/log/httpd
web资源主目录:/var/www/html
这里对/etc/httpd/conf/httpd.conf文件进行详细的说明,因为绝大部分的web服务设置都是在该配置文件进行完成的。
注意:配置文件里的对本地文件系统文件的引用一般要加上""双引号进行引用。
主配置文件位置: /etc/httpd/conf/httpd.conf
httpd -t 可测试配置文件的语法是否有误
配置文件大概分为3个部分,可以通过grep命令来大致查看:
[[email protected] conf]# grep "Section" httpd.conf ### Section 1: Global Environment ### Section 2: ‘Main‘ server configuration ### Section 3: Virtual Hosts
另外,Main server和Virtual Hosts配置同时只能有一个生效
可以在/etc/httpd/conf.d/目录下定义以.conf结尾的文件来定义属性,也可以直接修改httpd.conf文件
httpd.conf配置文件的内容格式基本都是
directive-name directive-value
比如
MaxKeepAliveRequests 100
下面基于httpd2.2的配置做了个思维导图说明:
3、httpd的用户身份验证实现
有时访问默写资源时,需要验证用户的身份信息,这就需要进行身份的质询认证,这里的身份验证是利用http协议自身提供的功能,并不是利用其他表单等工具实现
身份信息存储位置(帐号密码),可以另定义:
文件:/etc/httpd/conf/.htpasswd
认证类型(auth):
basic: 基本认证,帐号和密码明文发送;
digest:摘要认证,hash编程之后发送;
这里实验采用basic认证方式
实现步骤概述:
(1)编辑httpd.conf配置文件,对需要认证的URL资源进行设定身份认证
(2)使用htpasswd命令生成相应的帐号密码
htpasswd [options] FILE_PATH USERNAME [PASSWORD]
-c:首次创建文件时才需要此选项,否则会重置覆盖原文件
-m:密码进行md5加密
-D:删除用户
(3)访问资源进行验证
就是这么简单,下面来验证:用户访问/admin/index.html时需要进行身份验证
[19:47 [email protected]~]# tree /var/www/html/ /var/www/html/ ├── admin │ └── index.html ├── index.html └── test.html 1 directory, 3 files
编辑httpd.conf配置文件(在空白处添加以下内容),对需要认证的URL资源进行设定身份认证:
<Directory "/var/www/html/admin"> options none #options指令 allowoverride authconfig # authname "please input your ID/PASSWD" #登录提示语 authtype basic #认证方式 authuserfile "/etc/httpd/conf/.htpasswd" #指定用户密码的存放路径 authgroupfile "/etc/httpd/conf/.htgroup" #指定组用户的存放路径 require valid-user #指定哪里用户客户登录,valid-user表示文件路径存放的都可以访问,后面也可以逐个添加用户,只需要写上用户名即可 require group admins #指定那个组的用户可以登录 </Directory>
修改配置后,使用httpd -t进行配置文件的语法检测(强烈推荐,这是一个基本的良好习惯):
[20:02 [email protected]/var/www/html]# httpd -t Syntax OK
使用htpasswd添加相关的用户以及组:
[20:12 [email protected]/var/www/html]# htpasswd -c -m /etc/httpd/conf/.htpasswd hill New password: Re-type new password: Adding password for user hill [20:12 [email protected]/var/www/html]#htpasswd -m /etc/httpd/conf/.htpasswd jason New password: Re-type new password: Adding password for user jason [20:13 [email protected]/var/www/html]#htpasswd -m /etc/httpd/conf/.htpasswd nancy New password: Re-type new password: Adding password for user nancy [20:13 [email protected]/var/www/html]#cat /etc/httpd/conf/.htgroup admin: hill nancy [20:13 [email protected]/var/www/html]# cat /etc/httpd/conf/.htpasswd hill:$apr1$Y66c0zU3$oK9237JoHPrbcc9JIYPjD0 jason:$apr1$lfmcM6jh$b2n50Np7dgST8qIBT/RL00 nancy:$apr1$ye576Up7$LvHzYot8mVl/EkO85HJI4.
重载服务进行访问验证:
略
4、httpd的虚拟主机的实现
传统的是一个物理主机提供一个web服务站点,使用了虚拟主机设置后,可以实现在一个物理主机进行多个web站点的设置
注意,一般中心主机和虚拟主机不同时使用,所以使用虚拟主机时,需要把中心主机注释掉,注释DocumentRoot即可
虚拟主机的分类:
基于不同的IP实现不同的虚拟主机
变化IP
基于不同的port实现不同的虚拟主机
变化port
基于不同的FQDN实现不同的虚拟主机
变化ServerName的值
基于不同的IP实现不同的虚拟主机:
创建不同的站点:
[20:46 [email protected]/var/www/html]# mkdir /var/www/html/{www1,www2} [20:46 [email protected]/var/www/html]#touch /var/www/html/{www1,www2}/index.html [20:46 [email protected]/var/www/html]#echo "www1" > /var/www/html/www1/index.html [20:46 [email protected]/var/www/html]# echo "www2" > /var/www/html/www1/index.html [20:47 [email protected]/var/www/html]# tree . ├── admin │ └── index.html ├── index.html ├── test.html ├── www1 │ └── index.html └── www2 └── index.html 3 directories, 5 files
编辑配置文件,添加虚拟主机:
<virtualhost 172.18.16.139:80> #不同IP的同一端口 documentroot "/var/www/html/www1" #设置根目录路径 servername "www1.nihao.com" #设置站点FQDN </virtualhost> <virtualhost 172.18.16.138:80> #不同IP的同一端口 documentroot "/var/www/html/www2" #设置根目录路径 servername "www2.nihao.com" #设置站点FQDN </virtualhost>
临时设置本机IP进行实验:
[21:02 [email protected]/var/www/html]# ifconfig eth0:1 172.18.16.140/24 [21:03 [email protected]/var/www/html]# ifconfig eth0:2 172.18.16.141/24 [21:03 [email protected]/var/www/html]# ip addr show 1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00 inet 127.0.0.1/8 scope host lo inet6 ::1/128 scope host valid_lft forever preferred_lft forever 2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000 link/ether 00:0c:29:f4:30:a5 brd ff:ff:ff:ff:ff:ff inet 172.18.16.139/24 brd 172.18.16.255 scope global eth0 inet 172.18.16.140/24 brd 172.18.16.255 scope global secondary eth0:1 inet 172.18.16.141/24 brd 172.18.16.255 scope global secondary eth0:2 inet6 fe80::20c:29ff:fef4:30a5/64 scope link valid_lft forever preferred_lft forever
重置httpd服务后,验证成功:
[13:09 [email protected]~]# curl 172.18.16.140 www1 [13:09 [email protected]~]# curl 172.18.16.141 www2
基于不同的port实现不同的虚拟主机:
编辑配置文件,添加虚拟主机:
listen 8080 <virtualhost 172.18.16.140:80> documentroot "/var/www/html/www1" servername "www1.nihao.com" </virtualhost> <virtualhost 172.18.16.140:8080> documentroot "/var/www/html/www2" servername "www2.nihao.com" </virtualhost>
重置httpd服务后,验证成功:
[13:39 [email protected]~]# curl 172.18.16.140 www1 [13:39 [email protected]~]# curl 172.18.16.140:8080 www2
基于不同的FQDN实现不同的虚拟主机:
编辑配置文件,添加虚拟主机(与前面不同的是,要在首行加入:namevirtualhost IP:prot):
namevirtualhost 172.18.16.140:80 #在httpd-2.2的版本中,如果是基于FQDN的虚拟主机,要加上此行 <virtualhost 172.18.16.140:80> documentroot "/var/www/html/www1" servername "www1.nihao.com" </virtualhost> <virtualhost 172.18.16.140:80> documentroot "/var/www/html/www2" servername "www2.nihao.com" </virtualhost>
修改测试机器的hosts文件,能解析FQDN
[13:42 [email protected]~]# cat !$ cat /etc/hosts 127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4 ::1 localhost localhost.localdomain localhost6 localhost6.localdomain6 127.0.0.1 centos6.8 172.18.16.140 www1.nihao.com 172.18.16.140 www2.nihao.com
重置httpd服务后,验证成功:
[13:45 [email protected]~]# curl www1.nihao.com www1 [13:46 [email protected]~]# curl www2.nihao.com www2
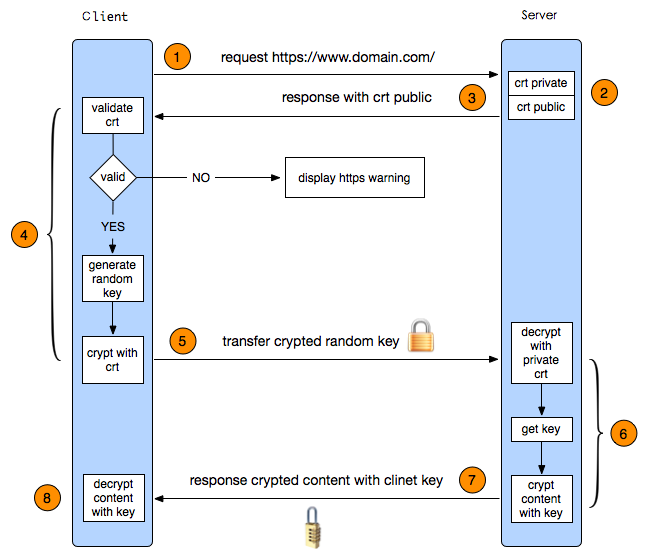
5、https的实现
在前面安全章已经学习,https是基于ssl的安全加密通信,https的默认端口是443
https的通信过程:
https的实现步骤:
(1)CA服务器签发证书
(2)把签发的证书发回到web服务器
(3)web服务端配置httpd支持使用lls,安装mod_ssl模块支持ssl协议
(4)设置mod_ssl的相关配置文件,如指定web根目录、https的端口指定等等
(4)客户端安装CA证书进行访问测试
下面来按步骤进行演示:
(1)
搭建私有根CA服务器:
[16:32 [email protected]/etc/pki/CA]# tree . ├── certs ├── crl ├── index.txt ├── newcerts ├── private └── serial 4 directories, 2 files [16:32 [email protected]/etc/pki/CA]# (umask 066;openssl genrsa -out private/cakey.pem) Generating RSA private key, 1024 bit long modulus ......................................++++++ .......++++++ e is 65537 (0x10001) [16:33 [email protected]/etc/pki/CA]#openssl req -new -x509 -key private/cakey.pem -out /etc/pki/CA/cacert.pem -days 365 You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter ‘.‘, the field will be left blank. ----- Country Name (2 letter code) [XX]:CN State or Province Name (full name) []:BEIJING Locality Name (eg, city) [Default City]:BEIJING Organization Name (eg, company) [Default Company Ltd]:nihao Organizational Unit Name (eg, section) []:nihao.com Common Name (eg, your name or your server‘s hostname) []:ca.nihao.com Email Address []:[email protected] [16:35 [email protected]/etc/pki/CA]# tree . ├── cacert.pem ├── certs ├── crl ├── index.txt ├── newcerts ├── private │?? └── cakey.pem └── serial 4 directories, 4 files
web服务器生成证书的申请文件:
[00:31 [email protected]~]# mkdir -p /etc/httpd/ssl/private [00:31 [email protected]~]#(umask 066;openssl genrsa -out /etc/httpd/ssl/private/httpd.key 2048) Generating RSA private key, 2048 bit long modulus ..........................................................................+++ ........................................................+++ e is 65537 (0x10001) [00:32 [email protected]~]#openssl req -new -key /etc/httpd/ssl/private/httpd.key -out /etc/httpd/ssl/httpd.csr You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter ‘.‘, the field will be left blank. ----- Country Name (2 letter code) [XX]:CN State or Province Name (full name) []:BEIJING Locality Name (eg, city) [Default City]:BEIJING Organization Name (eg, company) [Default Company Ltd]:nihao Organizational Unit Name (eg, section) []:www.nihao.com Common Name (eg, your name or your server‘s hostname) []:www.nihao.com Email Address []:[email protected] Please enter the following ‘extra‘ attributes to be sent with your certificate request A challenge password []: An optional company name []: [00:34 [email protected]~]# scp /etc/httpd/ssl/httpd.csr 192.168.31.29:/etc/pki/CA/certs/ ssh: connect to host 192.168.31.29 port 22: No route to host lost connection
把申请证书文件上传到根CA服务器以便签署:
[00:35 [email protected]~]# scp /etc/httpd/ssl/httpd.csr 192.168.31.49:/etc/pki/CA/certs/ The authenticity of host ‘192.168.31.49 (192.168.31.49)‘ can‘t be established. RSA key fingerprint is d1:42:7c:63:7d:e2:7f:70:b5:b3:ea:4d:6e:bc:97:af. Are you sure you want to continue connecting (yes/no)? yes Warning: Permanently added ‘192.168.31.49‘ (RSA) to the list of known hosts. [email protected]‘s password: httpd.csr 100% 1062 1.0KB/s 00:00
(2)对申请证书进行签署,并把签署的证书发送回web服务器:
[16:44 [email protected]/etc/pki/CA]# openssl ca -in certs/httpd.csr -out httpd.key Using configuration from /etc/pki/tls/openssl.cnf Check that the request matches the signature Signature ok Certificate Details: Serial Number: 1 (0x1) Validity Not Before: Sep 29 08:44:15 2016 GMT Not After : Sep 29 08:44:15 2017 GMT Subject: countryName = CN stateOrProvinceName = BEIJING organizationName = nihao organizationalUnitName = www.nihao.com commonName = www.nihao.com emailAddress = [email protected] X509v3 extensions: X509v3 Basic Constraints: CA:FALSE Netscape Comment: OpenSSL Generated Certificate X509v3 Subject Key Identifier: A8:83:56:22:E3:F1:EE:B6:6D:59:A1:E1:59:87:E0:01:DA:06:11:33 X509v3 Authority Key Identifier: keyid:CD:0B:CD:B6:10:FE:3D:8E:A9:CB:DF:B4:DC:AD:6F:C6:F2:4E:EE:13 Certificate is to be certified until Sep 29 08:44:15 2017 GMT (365 days) Sign the certificate? [y/n]:y 1 out of 1 certificate requests certified, commit? [y/n]y Write out database with 1 new entries Data Base Updated [16:44 [email protected]/etc/pki/CA]# ll certs/ total 4 -rw-r--r--. 1 root root 1062 Sep 29 16:41 httpd.csr -rw-r--r--. 1 root root 0 Sep 29 16:43 httpd.key [16:45 [email protected]/etc/pki/CA]# scp certs/httpd.key 192.168.31.212:/etc/httpd/ssl/ The authenticity of host ‘192.168.31.212 (192.168.31.212)‘ can‘t be established. RSA key fingerprint is 37:57:be:b6:cb:a7:e4:2a:77:a1:98:ed:63:5e:30:73. Are you sure you want to continue connecting (yes/no)? yes Warning: Permanently added ‘192.168.31.212‘ (RSA) to the list of known hosts. [email protected]‘s password: httpd.key 100% 0 0.0KB/s 00:00
(3)web服务端配置httpd支持使用lls,安装mod_ssl模块支持ssl协议
[00:40 [email protected]~]# rpm -q mod_ssl package mod_ssl is not installed [00:41 [email protected]~]# yum install -y mod_ssl Loaded plugins: fastestmirror, refresh-packagekit, security Setting up Install Process Loading mirror speeds from cached hostfile * base: mirrors.sina.cn * extras: mirrors.yun-idc.com * updates: mirrors.yun-idc.com base | 3.7 kB 00:00 extras | 3.4 kB 00:00 updates | 3.4 kB 00:00 updates/primary_db | 2.1 MB 00:01 Resolving Dependencies --> Running transaction check ---> Package mod_ssl.x86_64 1:2.2.15-54.el6.centos will be installed --> Finished Dependency Resolution Dependencies Resolved ========================================================================================================================= Package Arch Version Repository Size ========================================================================================================================= Installing: mod_ssl x86_64 1:2.2.15-54.el6.centos updates 97 k Transaction Summary ========================================================================================================================= Install 1 Package(s) Total download size: 97 k Installed size: 187 k Downloading Packages: mod_ssl-2.2.15-54.el6.centos.x86_64.rpm | 97 kB 00:00 Running rpm_check_debug Running Transaction Test Transaction Test Succeeded Running Transaction Installing : 1:mod_ssl-2.2.15-54.el6.centos.x86_64 1/1 Verifying : 1:mod_ssl-2.2.15-54.el6.centos.x86_64 1/1 Installed: mod_ssl.x86_64 1:2.2.15-54.el6.centos Complete! [00:42 [email protected]~]#rpm -qy mod_ssl mod_ssl-2.2.15-54.el6.centos.x86_64
(4)设置mod_ssl的相关配置文件:/etc/httpd/conf.d/ssl.conf
[00:42 [email protected]~]# rpm -ql mod_ssl /etc/httpd/conf.d/ssl.conf /usr/lib64/httpd/modules/mod_ssl.so /var/cache/mod_ssl /var/cache/mod_ssl/scache.dir /var/cache/mod_ssl/scache.pag /var/cache/mod_ssl/scache.sem
需要修改的配置文件的地方,其他的默认就可以:
ServerName:改成自己的web站点名称
SSLCertificateFile:指定web的签署证书路径
SSLCertificateKeyFile:指定web的证书私钥路径
[00:50 [email protected]~]# grep "^[^#]" /etc/httpd/conf.d/ssl.conf LoadModule ssl_module modules/mod_ssl.so Listen 443 SSLPassPhraseDialog builtin SSLSessionCache shmcb:/var/cache/mod_ssl/scache(512000) SSLSessionCacheTimeout 300 SSLMutex default SSLRandomSeed startup file:/dev/urandom 256 SSLRandomSeed connect builtin SSLCryptoDevice builtin <VirtualHost _default_:443> ServerName www.nihao.com ErrorLog logs/ssl_error_log TransferLog logs/ssl_access_log LogLevel warn SSLEngine on SSLProtocol all -SSLv2 SSLCipherSuite DEFAULT:!EXP:!SSLv2:!DES:!IDEA:!SEED:+3DES SSLCertificateFile /etc/http/ssl/httpd.crt SSLCertificateKeyFile /etc/httpd/ssl/private/httpd.key <Files ~ "\.(cgi|shtml|phtml|php3?)$"> SSLOptions +StdEnvVars </Files> <Directory "/var/www/cgi-bin"> SSLOptions +StdEnvVars </Directory> SetEnvIf User-Agent ".*MSIE.*" nokeepalive ssl-unclean-shutdown downgrade-1.0 force-response-1.0 CustomLog logs/ssl_request_log "%t %h %{SSL_PROTOCOL}x %{SSL_CIPHER}x \"%r\" %b" </VirtualHost>
修改后httpd -t检查语法没有问题,重载服务后,发现已经开始监听443端口,也就是https已经开始工作
[01:09 [email protected]/etc/httpd/ssl]# httpd -t Syntax OK [01:09 [email protected]/etc/httpd/ssl]# service httpd reload Reloading httpd: [01:09 [email protected]/etc/httpd/ssl]# netstat -tan Active Internet connections (servers and established) Proto Recv-Q Send-Q Local Address Foreign Address State tcp 0 0 192.168.31.212:53 0.0.0.0:* LISTEN tcp 0 0 127.0.0.1:53 0.0.0.0:* LISTEN tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN tcp 0 0 127.0.0.1:631 0.0.0.0:* LISTEN tcp 0 0 127.0.0.1:25 0.0.0.0:* LISTEN tcp 0 0 127.0.0.1:953 0.0.0.0:* LISTEN tcp 0 0 192.168.31.212:48896 192.168.31.49:22 TIME_WAIT tcp 0 0 192.168.31.212:22 192.168.31.19:63115 ESTABLISHED tcp 0 0 :::80 :::* LISTEN tcp 0 0 ::1:53 :::* LISTEN tcp 0 0 :::22 :::* LISTEN tcp 0 0 ::1:631 :::* LISTEN tcp 0 0 ::1:25 :::* LISTEN tcp 0 0 ::1:953 :::* LISTEN tcp 0 0 :::443 :::* LISTEN
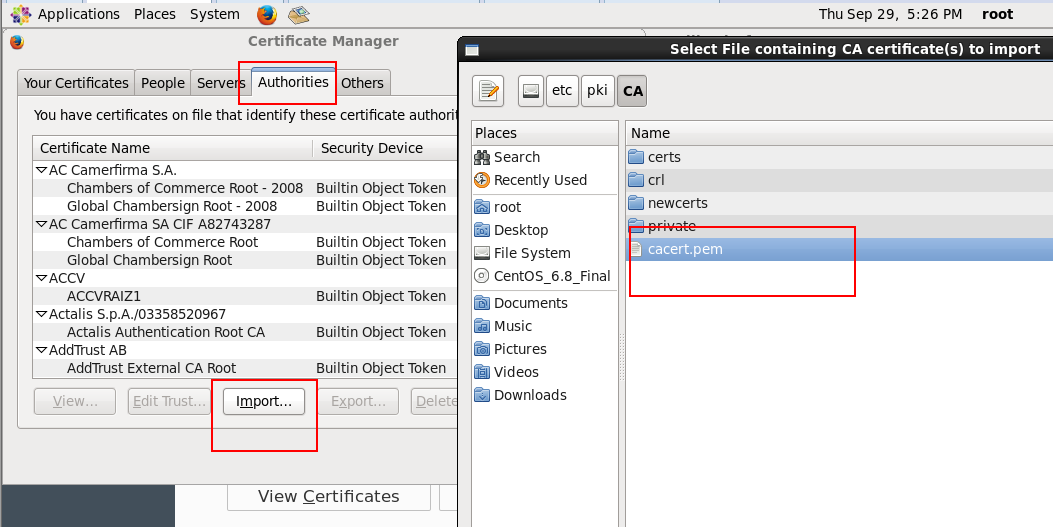
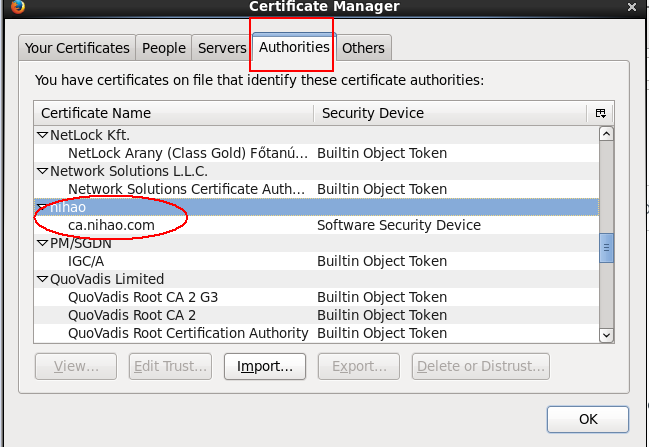
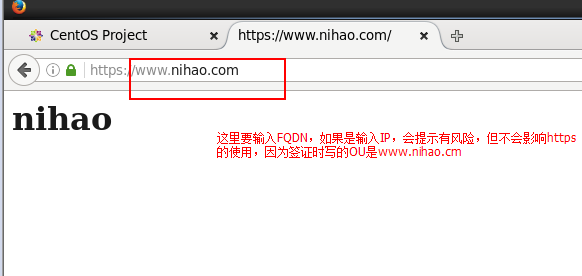
(4)客户端浏览器到处证书,测试正常!
本文出自 “6638225” 博客,转载请与作者联系!
以上是关于Centos7+Apache实现HTTPS的主要内容,如果未能解决你的问题,请参考以下文章
Centos7+Lvs+keeplived实现Apache高可用的负载均衡
Centos7+Nginx+Keepalived实现Apache服务的高可用&负载均衡
centos7搭建SVN+Apache+IF.svnadmin实现web管理SVN