RHEL 6.5----LDAP实现集中化认证
Posted zd520pyx1314
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了RHEL 6.5----LDAP实现集中化认证相关的知识,希望对你有一定的参考价值。
| 主机名 | IP | 安装软件 |
| master | 192.168.30.130 | openldap openldap-devel openldap-servers nfs migrationtools |
| slave | 192.168.30.131 | openldap-clients autofs nss-pam-ldapd authconfig-gtk |
配置思路:
- 建立域:修改源文件的方式
- 重启服务
- 创建用户
- 使用迁移工具,将passwd和group文件转化为ldif文件,将域的信息添加到basedn
- 将用户信息添加到basedn
- 客户端加域,关闭缓存服务nscd,开启nslcd服务,启动客户端验证
在master上安装
[[email protected] ~]# yum install -y openldap*
在slave上安装
[[email protected] ~]# yum install -y openldap-clients authconfig-gtk
在master上配置
[[email protected] ~]# cd /etc/openldap/slapd.d/cn\\=config [[email protected] cn=config]# ls cn=schema olcDatabase={0}config.ldif olcDatabase={1}monitor.ldif cn=schema.ldif olcDatabase={-1}frontend.ldif olcDatabase={2}bdb.ldif [[email protected] cn=config]# vim olcDatabase\\=\\{1\\}monitor.ldif [[email protected] cn=config]# cp olcDatabase\\=\\{1\\}monitor.ldif{,.back} [[email protected] cn=config]# vim olcDatabase\\=\\{1\\}monitor.ldif dn: olcDatabase={1}monitor objectClass: olcDatabaseConfig olcDatabase: {1}monitor olcAccess: {0}to * by dn.base="gidNumber=0+uidNumber=0,cn=peercred,cn=externa l,cn=auth" read by dn.base="cn=Manager,dc=SiShen,dc=cn" read by * none .......... #其他选项不要动 #生成根密码 [[email protected] cn=config]# slappasswd New password: Re-enter new password: {SSHA}rtDbc7rinDkNgJXb9LZvMZ4g+A4XmGOu [[email protected] cn=config]# vim olcDatabase\\=\\{2\\}bdb.ldif dn: olcDatabase={2}bdb objectClass: olcDatabaseConfig objectClass: olcBdbConfig olcDatabase: {2}bdb olcSuffix: dc=SiShen,dc=cn olcAddContentAcl: FALSE olcLastMod: TRUE olcMaxDerefDepth: 15 olcReadOnly: FALSE olcRootDN: cn=Manager,dc=SiShen,dc=cn olcRootPW: {SSHA}rtDbc7rinDkNgJXb9LZvMZ4g+A4XmGOu #添加此行 ................. [[email protected] cn=config]# slaptest -u config file testing succeeded 出现这个提示证明配置没有问题
重启服务
[[email protected] ~]# /etc/init.d/slapd restart Stopping slapd: [FAILED] Starting slapd: [ OK ] 查看配置信息 [[email protected] ~]# ldapsearch -x -b "dc=SiShen,dc=cn" # extended LDIF # # LDAPv3 # base <dc=SiShen,dc=cn> with scope subtree # filter: (objectclass=*) # requesting: ALL # # search result search: 2 result: 32 No such object # numResponses: 1
使用迁移工具
[[email protected] ~]# yum install -y migrationtools [[email protected] ~]# vim /usr/share/migrationtools/migrate_common.ph +71 #注意+号前面有空格 ............. # Default DNS domain $DEFAULT_MAIL_DOMAIN = "SiShen.cn"; # Default base $DEFAULT_BASE = "dc=SiShen,dc=cn"; ........... [[email protected] ~]# /usr/share/migrationtools/migrate_base.pl > /tmp/base.ldif #生成base.ldif文件 [[email protected] ~]# ldapadd -x -W -D "cn=Manager,dc=SiShen,dc=cn" -f /tmp/base.ldif #-x简单的认证方式, -W 使用命令行输入密码 -D bindDN,入域 Enter LDAP Password: adding new entry "dc=SiShen,dc=cn" adding new entry "ou=Hosts,dc=SiShen,dc=cn" adding new entry "ou=Rpc,dc=SiShen,dc=cn" adding new entry "ou=Services,dc=SiShen,dc=cn" adding new entry "nisMapName=netgroup.byuser,dc=SiShen,dc=cn" adding new entry "ou=Mounts,dc=SiShen,dc=cn" adding new entry "ou=Networks,dc=SiShen,dc=cn" adding new entry "ou=People,dc=SiShen,dc=cn" adding new entry "ou=Group,dc=SiShen,dc=cn" adding new entry "ou=Netgroup,dc=SiShen,dc=cn" adding new entry "ou=Protocols,dc=SiShen,dc=cn" adding new entry "ou=Aliases,dc=SiShen,dc=cn" adding new entry "nisMapName=netgroup.byhost,dc=SiShen,dc=cn" 也可以 [[email protected] ~]# ldapadd -x -w123456 -D "cn=Manager,dc=SiShen,dc=cn" -f /tmp/base.ldif # -w不适用命令行,直接制定密码
添加测试用户
[[email protected] ~]# mkdir /ldaphome #创建ldap账户主目录
[[email protected] ~]# for i in {1..5}
> do > useradd -u 100$i -d /ldaphome/ldapuser$i ldapuser$i > echo ldapuser$i:123456 | chpasswd > done
[[email protected] ~]# tail -5 /etc/passwd ldapuser1:x:2001:2001::/ldaphome/ldapuser1:/bin/bash ldapuser2:x:2002:2002::/ldaphome/ldapuser2:/bin/bash ldapuser3:x:2003:2003::/ldaphome/ldapuser3:/bin/bash ldapuser4:x:2004:2004::/ldaphome/ldapuser4:/bin/bash ldapuser5:x:2005:2005::/ldaphome/ldapuser5:/bin/bash
查看是否添加成功
[[email protected] ~]# grep ldapuser /etc/passwd ldapuser1:x:2001:2001::/ldaphome/ldapuser1:/bin/bash ldapuser2:x:2002:2002::/ldaphome/ldapuser2:/bin/bash ldapuser3:x:2003:2003::/ldaphome/ldapuser3:/bin/bash ldapuser4:x:2004:2004::/ldaphome/ldapuser4:/bin/bash ldapuser5:x:2005:2005::/ldaphome/ldapuser5:/bin/bash [[email protected] ~]# grep ldapuser /etc/group ldapuser1:x:2001: ldapuser2:x:2002: ldapuser3:x:2003: ldapuser4:x:2004: ldapuser5:x:2005:
将测试用户加入域
[[email protected] ~]# /usr/share/migrationtools/migrate_passwd.pl /tmp/passwd /tmp/passwd.ldif //使用迁移工具将passwd文件转化为passwd.ldif文件 [[email protected] ~]# /usr/share/migrationtools/migrate_group.pl /tmp/group /tmp/group.ldif [[email protected] ~]# ldapadd -x -w123456 -D "cn=Manager,dc=SiShen,dc=cn" -f /tmp/passwd.ldif adding new entry "uid=ldapuser1,ou=People,dc=SiShen,dc=cn" adding new entry "uid=ldapuser2,ou=People,dc=SiShen,dc=cn" adding new entry "uid=ldapuser3,ou=People,dc=SiShen,dc=cn" adding new entry "uid=ldapuser4,ou=People,dc=SiShen,dc=cn" adding new entry "uid=ldapuser5,ou=People,dc=SiShen,dc=cn" [[email protected] ~]# ldapadd -x -w123456 -D "cn=Manager,dc=SiShen,dc=cn" -f /tmp/group.ldif adding new entry "cn=ldapuser1,ou=Group,dc=SiShen,dc=cn" adding new entry "cn=ldapuser2,ou=Group,dc=SiShen,dc=cn" adding new entry "cn=ldapuser3,ou=Group,dc=SiShen,dc=cn" adding new entry "cn=ldapuser4,ou=Group,dc=SiShen,dc=cn" adding new entry "cn=ldapuser5,ou=Group,dc=SiShen,dc=cn"
查看入域是否成功
[[email protected] ~]# ldapsearch -x -w123456 -D "cn=Manager,dc=SiShen,dc=cn" -b "dc=SiShen,dc=cn" # extended LDIF # # LDAPv3 # base <dc=SiShen,dc=cn> with scope subtree # filter: (objectclass=*) # requesting: ALL # # SiShen.cn dn: dc=SiShen,dc=cn dc: SiShen objectClass: top objectClass: domain # Hosts, SiShen.cn dn: ou=Hosts,dc=SiShen,dc=cn ou: Hosts objectClass: top objectClass: organizationalUnit # Rpc, SiShen.cn dn: ou=Rpc,dc=SiShen,dc=cn ou: Rpc objectClass: top objectClass: organizationalUnit # Services, SiShen.cn dn: ou=Services,dc=SiShen,dc=cn ou: Services objectClass: top objectClass: organizationalUnit # netgroup.byuser, SiShen.cn dn: nisMapName=netgroup.byuser,dc=SiShen,dc=cn nisMapName: netgroup.byuser objectClass: top objectClass: nisMap # Mounts, SiShen.cn dn: ou=Mounts,dc=SiShen,dc=cn ou: Mounts objectClass: top objectClass: organizationalUnit # Networks, SiShen.cn dn: ou=Networks,dc=SiShen,dc=cn ou: Networks objectClass: top objectClass: organizationalUnit # People, SiShen.cn dn: ou=People,dc=SiShen,dc=cn ou: People objectClass: top objectClass: organizationalUnit # Group, SiShen.cn dn: ou=Group,dc=SiShen,dc=cn ou: Group objectClass: top objectClass: organizationalUnit # Netgroup, SiShen.cn dn: ou=Netgroup,dc=SiShen,dc=cn ou: Netgroup objectClass: top objectClass: organizationalUnit # Protocols, SiShen.cn dn: ou=Protocols,dc=SiShen,dc=cn ou: Protocols objectClass: top objectClass: organizationalUnit # Aliases, SiShen.cn dn: ou=Aliases,dc=SiShen,dc=cn ou: Aliases objectClass: top objectClass: organizationalUnit # netgroup.byhost, SiShen.cn dn: nisMapName=netgroup.byhost,dc=SiShen,dc=cn nisMapName: netgroup.byhost objectClass: top objectClass: nisMap # ldapuser1, People, SiShen.cn dn: uid=ldapuser1,ou=People,dc=SiShen,dc=cn uid: ldapuser1 cn: ldapuser1 objectClass: account objectClass: posixAccount objectClass: top objectClass: shadowAccount userPassword:: e2NyeXB0fSQ2JGZFVHNOL0tNOEluL3pLMiQxWm5vVmVrMFdxeDNhcUZPbG5DUUR EdmpnL2RteFFhbEtYT21VNW9SdzJWN3J2LzZCRHM0Y1pDdWk5RmxpbHRIY0YvYzBzdkJ1T0cwTlQx ZlNkaWQ3MA== shadowLastChange: 17678 shadowMin: 0 shadowMax: 99999 shadowWarning: 7 loginShell: /bin/bash uidNumber: 2001 gidNumber: 2001 homeDirectory: /ldaphome/ldapuser1 # ldapuser2, People, SiShen.cn dn: uid=ldapuser2,ou=People,dc=SiShen,dc=cn uid: ldapuser2 cn: ldapuser2 objectClass: account objectClass: posixAccount objectClass: top objectClass: shadowAccount userPassword:: e2NyeXB0fSQ2JHA3YkdnL09HQWk2L05qJEYuMVZUTldKa21YUHRIWG44dnl5VG5 EOTJWWlBhclp5T0ZiYzRDaTlDalcwQzBjaXFUNUlycjBodHdLSHFNNFNmcEFoeEw2TXdwMXpjYWxJ VlV4aWMu shadowLastChange: 17678 shadowMin: 0 shadowMax: 99999 shadowWarning: 7 loginShell: /bin/bash uidNumber: 2002 gidNumber: 2002 homeDirectory: /ldaphome/ldapuser2 # ldapuser3, People, SiShen.cn dn: uid=ldapuser3,ou=People,dc=SiShen,dc=cn uid: ldapuser3 cn: ldapuser3 objectClass: account objectClass: posixAccount objectClass: top objectClass: shadowAccount userPassword:: e2NyeXB0fSQ2JFQwdThPNUN0dzR2VkRNUyQ0d3BkTkliQXU0OHg1NzlZV2tSY09 HbDRjWU5vNEtWLi8wd2JWdTd1emlWaEpuZER1Ljl4OE1YLmRob3RERkp2b0FxV0tSY2tML2NGOFpL cXlKMjg1MQ== shadowLastChange: 17678 shadowMin: 0 shadowMax: 99999 shadowWarning: 7 loginShell: /bin/bash uidNumber: 2003 gidNumber: 2003 homeDirectory: /ldaphome/ldapuser3 # ldapuser4, People, SiShen.cn dn: uid=ldapuser4,ou=People,dc=SiShen,dc=cn uid: ldapuser4 cn: ldapuser4 objectClass: account objectClass: posixAccount objectClass: top objectClass: shadowAccount userPassword:: e2NyeXB0fSQ2JHM0SmhaSXVNcW4vQiQ5anVVeC50bi5OLkNMVFJhS21oLjhoTFF NUTRrWVBWRThDVmVyWVZwVVFUaE5NR0JGeGd3cjQ4VmdOdVpBN00zUm5idHo2VlViSVplTy9qNGYz eXBvLg== shadowLastChange: 17678 shadowMin: 0 shadowMax: 99999 shadowWarning: 7 loginShell: /bin/bash uidNumber: 2004 gidNumber: 2004 homeDirectory: /ldaphome/ldapuser4 # ldapuser5, People, SiShen.cn dn: uid=ldapuser5,ou=People,dc=SiShen,dc=cn uid: ldapuser5 cn: ldapuser5 objectClass: account objectClass: posixAccount objectClass: top objectClass: shadowAccount userPassword:: e2NyeXB0fSQ2JDdEUk1FL3hHQ2NlL2ZlUEIkOWZsdmpmUmJCRzJUMXpNTHZOZ0p iWW8veDZNeHlCcEszMEtaVS9UQkd3bTVqZFdNUEI1a0Q3ZXdudmQ1QmRZUmJnQlgwTndYTGI2RnJU SW0vaHJEWDE= shadowLastChange: 17678 shadowMin: 0 shadowMax: 99999 shadowWarning: 7 loginShell: /bin/bash uidNumber: 2005 gidNumber: 2005 homeDirectory: /ldaphome/ldapuser5 # ldapuser1, Group, SiShen.cn dn: cn=ldapuser1,ou=Group,dc=SiShen,dc=cn objectClass: posixGroup objectClass: top cn: ldapuser1 userPassword:: e2NyeXB0fXg= gidNumber: 2001 # ldapuser2, Group, SiShen.cn dn: cn=ldapuser2,ou=Group,dc=SiShen,dc=cn objectClass: posixGroup objectClass: top cn: ldapuser2 userPassword:: e2NyeXB0fXg= gidNumber: 2002 # ldapuser3, Group, SiShen.cn dn: cn=ldapuser3,ou=Group,dc=SiShen,dc=cn objectClass: posixGroup objectClass: top cn: ldapuser3 userPassword:: e2NyeXB0fXg= gidNumber: 2003 # ldapuser4, Group, SiShen.cn dn: cn=ldapuser4,ou=Group,dc=SiShen,dc=cn objectClass: posixGroup objectClass: top cn: ldapuser4 userPassword:: e2NyeXB0fXg= gidNumber: 2004 # ldapuser5, Group, SiShen.cn dn: cn=ldapuser5,ou=Group,dc=SiShen,dc=cn objectClass: posixGroup objectClass: top cn: ldapuser5 userPassword:: e2NyeXB0fXg= gidNumber: 2005 # search result search: 2 result: 0 Success # numResponses: 24 # numEntries: 23
在客户端slave上


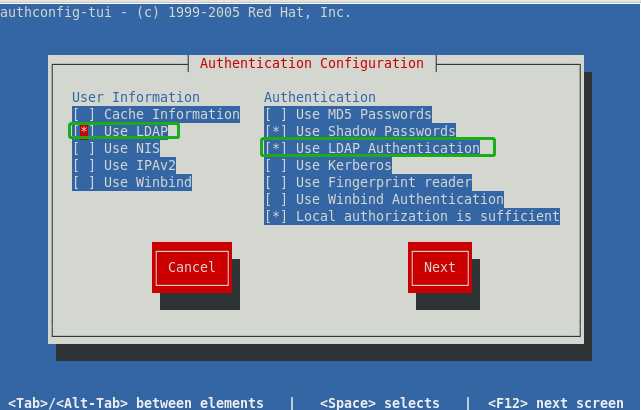
如果没有安装图形化界面,则可以使用以下方法,其结果是一样的。
next
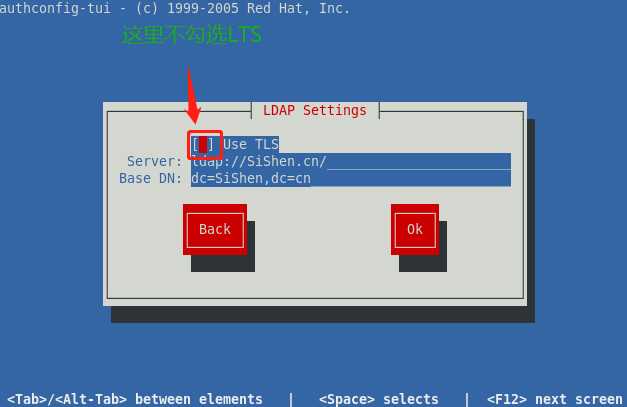


可以看出在执行了authconfig-tui后,客户端会停止sssd服务,并启动nslcd服务;此外nscd服务也会被停掉
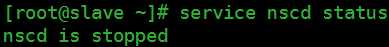
修改authconfig文件
[[email protected] ~]# vim /etc/sysconfig/authconfig ................ 9 FORCELEGACY=yes #第九行将FORCELEGACY的原值no修改为yes .............
看是否可以拿到用户
[[email protected] ~]# getent passwd | grep ldapuser ldapuser1:x:2001:2001:ldapuser1:/ldaphome/ldapuser1:/bin/bash ldapuser2:x:2002:2002:ldapuser2:/ldaphome/ldapuser2:/bin/bash ldapuser3:x:2003:2003:ldapuser3:/ldaphome/ldapuser3:/bin/bash ldapuser4:x:2004:2004:ldapuser4:/ldaphome/ldapuser4:/bin/bash ldapuser5:x:2005:2005:ldapuser5:/ldaphome/ldapuser5:/bin/bash
测试登录
[[email protected] ~]# su - ldapuser1 su: warning: cannot change directory to /ldaphome/ldapuser1: No such file or directory -bash-4.1$ ls ls: cannot open directory .: Permission denied -bash-4.1$ hostname slave -bash-4.1$ su - ldapuser2 Password: su: warning: cannot change directory to /ldaphome/ldapuser2: No such file or directory -bash-4.1$ whoami ldapuser2
可以登录但是没有家目录,家目录的漫游在本实验结束时再配置,现在使用第二种方法修改配置文件,上面的方法是在源文件的基础上修改的,接下来新建文件,测试。
第二种修改方法
建立配置文件,并修改
[[email protected] ~]# cd /etc/openldap/ [[email protected] openldap]# ls certs ldap.conf schema slapd.d #注意slapd.d目录存在时,ldap.conf是不生效的,所以,移除slapd.d目录 #可以查看下slapd.d目录下都有什么内容 [[email protected] openldap]# tree slapd.d/ slapd.d/ ├── cn=config │ ├── cn=schema │ │ ├── cn={0}corba.ldif │ │ ├── cn={10}ppolicy.ldif │ │ ├── cn={11}collective.ldif │ │ ├── cn={1}core.ldif │ │ ├── cn={2}cosine.ldif │ │ ├── cn={3}duaconf.ldif │ │ ├── cn={4}dyngroup.ldif │ │ ├── cn={5}inetorgperson.ldif │ │ ├── cn={6}java.ldif │ │ ├── cn={7}misc.ldif │ │ ├── cn={8}nis.ldif │ │ └── cn={9}openldap.ldif │ ├── cn=schema.ldif │ ├── olcDatabase={0}config.ldif │ ├── olcDatabase={-1}frontend.ldif │ ├── olcDatabase={1}monitor.ldif │ └── olcDatabase={2}bdb.ldif └── cn=config.ldif 2 directories, 18 files #因为当前目录下ldap.conf文件没有什么有效的内容,所以,需要进行以下操作 [[email protected] openldap]# cat /usr/share/openldap-servers/slapd.conf.obsolete > /etc/openldap/ldap.conf [[email protected] openldap]# vim ldap.conf [[email protected] openldap]# cp /usr/share/openldap-servers/slapd.conf.obsolete /etc/openldap/slapd.conf 新建slapd.conf文件 [[email protected] openldap]# pwd /etc/openldap [[email protected] openldap]# ls certs ldap.conf schema slapd.conf
修改slapd.conf文件
#生成密码文件 [[email protected] ~]# slappasswd New password: Re-enter new password: {SSHA}rq7wj1IR4MHPPeLtnWPtZbtb1nt5dLKa [[email protected] ~]# vim /etc/openldap/slapd.conf ........ suffix "dc=SiShen,dc=cn" checkpoint 1024 15 rootdn "cn=Manager,dc=SiShen,dc=cn" ...... #测试配置文件 [[email protected] ~]# slaptest -u config file testing succeeded
创建数据库文件
[[email protected] ~]# cp /usr/share/openldap-servers/DB_CONFIG.example /etc/openldap/DB_CONFIG
重启salpd服务并搜索域测试
[[email protected] ~]# service slapd restart Stopping slapd: [FAILED] Starting slapd: [ OK ] [[email protected] ~]# ldapsearch -x -b "dc=SiShen,dc=cn" # extended LDIF # # LDAPv3 # base <dc=SiShen,dc=cn> with scope subtree # filter: (objectclass=*) # requesting: ALL # # search result search: 2 result: 32 No such object # numResponses: 1
创建测试用户
[[email protected] ~]# mkdir /ldaphome [[email protected] ~]# for i in {1..3} > do > useradd -u 100$i -d /ldaphome/ldapuser$i ldapuser$i > echo ldapuser$i:123456 | chpasswd > done [[email protected] ~]# grep ldapuser /etc/passwd ldapuser1:x:1001:1001::/ldaphome/ldapuser1:/bin/bash ldapuser2:x:1002:1002::/ldaphome/ldapuser2:/bin/bash ldapuser3:x:1003:1003::/ldaphome/ldapuser3:/bin/bash [[email protected] ~]# grep ldapuser /etc/group ldapuser1:x:1001: ldapuser2:x:1002: ldapuser3:x:1003:
安装迁移工具migrationtools
[[email protected] ~]# yum install -y migrationtools [[email protected] ~]# vim /usr/share/migrationtools/migrate_common.ph +71 ........ # Default DNS domain $DEFAULT_MAIL_DOMAIN = "SiShen.cn"; # Default base $DEFAULT_BASE = "dc=SiShen,dc=cn"; ..... #生成base.ldif文件 [[email protected] ~]# /usr/share/migrationtools/migrate_base.pl > /tmp/base.ldif [[email protected] ~]# cat /tmp/base.ldif dn: dc=SiShen,dc=cn dc: SiShen objectClass: top objectClass: domain dn: ou=Hosts,dc=SiShen,dc=cn ou: Hosts objectClass: top objectClass: organizationalUnit dn: ou=Rpc,dc=SiShen,dc=cn ou: Rpc objectClass: top objectClass: organizationalUnit dn: ou=Services,dc=SiShen,dc=cn ou: Services objectClass: top objectClass: organizationalUnit dn: nisMapName=netgroup.byuser,dc=SiShen,dc=cn nismapname: netgroup.byuser objectClass: top objectClass: nisMap dn: ou=Mounts,dc=SiShen,dc=cn ou: Mounts objectClass: top objectClass: organizationalUnit dn: ou=Networks,dc=SiShen,dc=cn ou: Networks objectClass: top objectClass: organizationalUnit dn: ou=People,dc=SiShen,dc=cn ou: People objectClass: top objectClass: organizationalUnit dn: ou=Group,dc=SiShen,dc=cn ou: Group objectClass: top objectClass: organizationalUnit dn: ou=Netgroup,dc=SiShen,dc=cn ou: Netgroup objectClass: top objectClass: organizationalUnit dn: ou=Protocols,dc=SiShen,dc=cn ou: Protocols objectClass: top objectClass: organizationalUnit dn: ou=Aliases,dc=SiShen,dc=cn ou: Aliases objectClass: top objectClass: organizationalUnit dn: nisMapName=netgroup.byhost,dc=SiShen,dc=cn nismapname: netgroup.byhost objectClass: top objectClass: nisMap 将测试用户加入域 [[email protected] ~]# ldapadd -x -w123456 -D "cn=Manager,dc=SiShen,dc=cn" -f /tmp/base.ldif adding new entry "dc=SiShen,dc=cn" adding new entry "ou=Hosts,dc=SiShen,dc=cn" adding new entry "ou=Rpc,dc=SiShen,dc=cn" adding new entry "ou=Services,dc=SiShen,dc=cn" adding new entry "nisMapName=netgroup.byuser,dc=SiShen,dc=cn" adding new entry "ou=Mounts,dc=SiShen,dc=cn" adding new entry "ou=Networks,dc=SiShen,dc=cn" adding new entry "ou=People,dc=SiShen,dc=cn" adding new entry "ou=Group,dc=SiShen,dc=cn" adding new entry "ou=Netgroup,dc=SiShen,dc=cn" adding new entry "ou=Protocols,dc=SiShen,dc=cn" adding new entry "ou=Aliases,dc=SiShen,dc=cn" adding new entry "nisMapName=netgroup.byhost,dc=SiShen,dc=cn" #生成passwd.ldif文件和group.ldif文件 [[email protected] ~]# grep ldapuser /etc/passwd > /tmp/passwd [[email protected] ~]# grep ldapuser /etc/group > /tmp/group [[email protected] ~]# cat /tmp/passwd ldapuser1:x:1001:1001::/ldaphome/ldapuser1:/bin/bash ldapuser2:x:1002:1002::/ldaphome/ldapuser2:/bin/bash ldapuser3:x:1003:1003::/ldaphome/ldapuser3:/bin/bash #将测试用户账户密码和组文件转化为ldif文件 [[email protected] ~]# /usr/share/migrationtools/migrate_passwd.pl /tmp/passwd /tmp/passwd.ldif [[email protected] ~]# /usr/share/migrationtools/migrate_group.pl /tmp/group /tmp/group.ldif #将ldif文件中的内容添加到basedn中去 [[email protected] ~]# ldapadd -x -w123456 -D "cn=Manager,dc=SiShen,dc=cn" -f /tmp/passwd.ldif adding new entry "uid=ldapuser1,ou=People,dc=SiShen,dc=cn" adding new entry "uid=ldapuser2,ou=People,dc=SiShen,dc=cn" adding new entry "uid=ldapuser3,ou=People,dc=SiShen,dc=cn" [[email protected] ~]# ldapadd -x -w123456 -D "cn=Manager,dc=SiShen,dc=cn" -f /tmp/group.ldif adding new entry "cn=ldapuser1,ou=Group,dc=SiShen,dc=cn" adding new entry "cn=ldapuser2,ou=Group,dc=SiShen,dc=cn" adding new entry "cn=ldapuser3,ou=Group,dc=SiShen,dc=cn"
重启slapd服务搜索域,查看添加内容是否存在
[[email protected] ~]# service slapd restart Stopping slapd: [ OK ] Starting slapd: [ OK ]
查看内容
[[email protected] ~]# ldapsearch -x -b "dc=SiShen,dc=cn" # extended LDIF # # LDAPv3 # base <dc=SiShen,dc=cn> with scope subtree # filter: (objectclass=*) # requesting: ALL # # SiShen.cn dn: dc=SiShen,dc=cn dc: SiShen objectClass: top objectClass: domain # Hosts, SiShen.cn dn: ou=Hosts,dc=SiShen,dc=cn ou: Hosts objectClass: top objectClass: organizationalUnit # Rpc, SiShen.cn dn: ou=Rpc,dc=SiShen,dc=cn ou: Rpc objectClass: top objectClass: organizationalUnit # Services, SiShen.cn dn: ou=Services,dc=SiShen,dc=cn ou: Services objectClass: top objectClass: organizationalUnit # netgroup.byuser, SiShen.cn dn: nisMapName=netgroup.byuser,dc=SiShen,dc=cn nisMapName: netgroup.byuser objectClass: top objectClass: nisMap # Mounts, SiShen.cn dn: ou=Mounts,dc=SiShen,dc=cn ou: Mounts objectClass: top objectClass: organizationalUnit # Networks, SiShen.cn dn: ou=Networks,dc=SiShen,dc=cn ou: Networks objectClass: top objectClass: organizationalUnit # People, SiShen.cn dn: ou=People,dc=SiShen,dc=cn ou: People objectClass: top objectClass: organizationalUnit # Group, SiShen.cn dn: ou=Group,dc=SiShen,dc=cn ou: Group objectClass: top objectClass: organizationalUnit # Netgroup, SiShen.cn dn: ou=Netgroup,dc=SiShen,dc=cn ou: Netgroup objectClass: top objectClass: organizationalUnit # Protocols, SiShen.cn dn: ou=Protocols,dc=SiShen,dc=cn ou: Protocols objectClass: top objectClass: organizationalUnit # Aliases, SiShen.cn dn: ou=Aliases,dc=SiShen,dc=cn ou: Aliases objectClass: top objectClass: organizationalUnit # netgroup.byhost, SiShen.cn dn: nisMapName=netgroup.byhost,dc=SiShen,dc=cn nisMapName: netgroup.byhost objectClass: top objectClass: nisMap # ldapuser1, People, SiShen.cn dn: uid=ldapuser1,ou=People,dc=SiShen,dc=cn uid: ldapuser1 cn: ldapuser1 objectClass: account objectClass: posixAccount objectClass: top objectClass: shadowAccount userPassword:: e2NyeXB0fSQ2JHlld1F1L2tpUHdlL3N2d2skb21TWlpuamwxeTRvM3VMU2dzL0p zMzl2ZGp5Ni8zRVl5QTVsZDA4SVFQNWUxeE1QLkYwalhxMTIuUkdPSHpRSGo2UEd1ampJUmlDUW8z NW1LRmFUby4= shadowLastChange: 17678 shadowMin: 0 shadowMax: 99999 shadowWarning: 7 loginShell: /bin/bash uidNumber: 1001 gidNumber: 1001 homeDirectory: /ldaphome/ldapuser1 # ldapuser2, People, SiShen.cn dn: uid=ldapuser2,ou=People,dc=SiShen,dc=cn uid: ldapuser2 cn: ldapuser2 objectClass: account objectClass: posixAccount objectClass: top objectClass: shadowAccount userPassword:: e2NyeXB0fSQ2JG52M0w3eGhEMHE3VSQ0dkVaT1JSNmxsT0Y0cFBDNFlJZUV2eXF BUlhGUmw4MnQwMU1GbDFKay55RTlhVjZScWF0eDZ5LkZXZlJLU1hiV2x0ek1xQjVJM2ptS2ozcWZr L2ExLg== shadowLastChange: 17678 shadowMin: 0 shadowMax: 99999 shadowWarning: 7 loginShell: /bin/bash uidNumber: 1002 gidNumber: 1002 homeDirectory: /ldaphome/ldapuser2 # ldapuser3, People, SiShen.cn dn: uid=ldapuser3,ou=People,dc=SiShen,dc=cn uid: ldapuser3 cn: ldapuser3 objectClass: account objectClass: posixAccount objectClass: top objectClass: shadowAccount userPassword:: e2NyeXB0fSQ2JHhZdk5YL0didzdXLzdHJDZHNzY4MFJSZ3VmWFdiYWl4ZHgyNC5 qYy9GU3A1Ujlma3piZGhzODRva09WWlUzNnk0cURVc0VQbXd1bDlCSkpZQ2tCcy9oYXp3cmZFUjJs b0tnWGQw shadowLastChange: 17678 shadowMin: 0 shadowMax: 99999 shadowWarning: 7 loginShell: /bin/bash uidNumber: 1003 gidNumber: 1003 homeDirectory: /ldaphome/ldapuser3 # ldapuser1, Group, SiShen.cn dn: cn=ldapuser1,ou=Group,dc=SiShen,dc=cn objectClass: posixGroup objectClass: top cn: ldapuser1 userPassword:: e2NyeXB0fXg= gidNumber: 1001 # ldapuser2, Group, SiShen.cn dn: cn=ldapuser2,ou=Group,dc=SiShen,dc=cn objectClass: posixGroup objectClass: top cn: ldapuser2 userPassword:: e2NyeXB0fXg= gidNumber: 1002 # ldapuser3, Group, SiShen.cn dn: cn=ldapuser3,ou=Group,dc=SiShen,dc=cn objectClass: posixGroup objectClass: top cn: ldapuser3 userPassword:: e2NyeXB0fXg= gidNumber: 1003 # search result search: 2 result: 0 Success # numResponses: 20 # numEntries: 19 出现这些内容表示添加成功
在客户端测试
首先修改下hosts文件
[[email protected] ~]# vim /etc/hosts 192.168.30.130 master SiShen.cn #添加ldap-serverIP地址与SiShen.cn的映射 #注意如果这里没有添加ldap-server的IP地址到SiShen.cn的映射,会报不能发现ldap-server
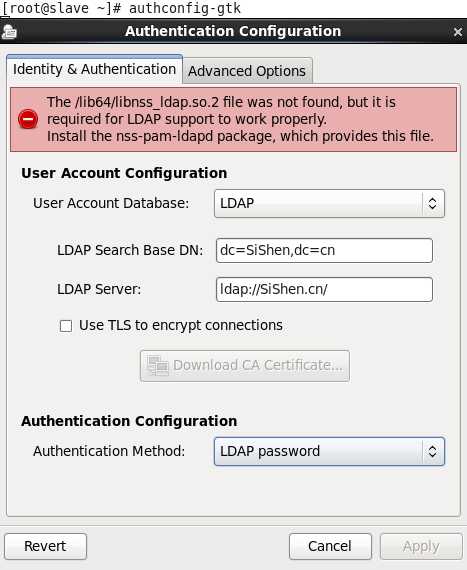
安装必要软件包 [[email protected] ~]# yum install -y authconfig-gtk nss-pam-ldapd openldap-clients 修改authconfig配置 [[email protected] ~]# vim /etc/sysconfig/authconfig FORCELEGACY=yes #这里原值是no,改为yes
配置ldap认证
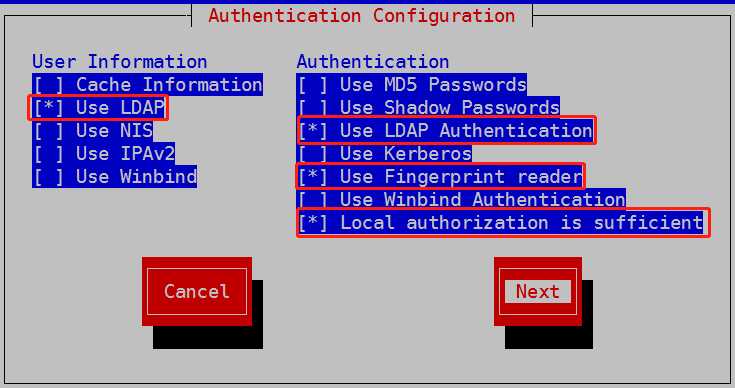
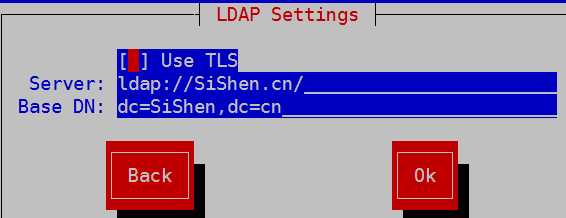
执行过这个操作之后,出现以下信息

测试是否获可以获取用户
[[email protected] ~]# getent passwd | grep ldapuser ldapuser1:x:1001:1001:ldapuser1:/ldaphome/ldapuser1:/bin/bash ldapuser2:x:1002:1002:ldapuser2:/ldaphome/ldapuser2:/bin/bash ldapuser3:x:1003:1003:ldapuser3:/ldaphome/ldapuser3:/bin/bash
注意,如果这里没有获取成功,可能原因在客户端的/etc/hosts文件里查看,是否有类似的对应关系,
或者直接在如下位置些ldap-server的ip地址ldap://ldap-server-IP/
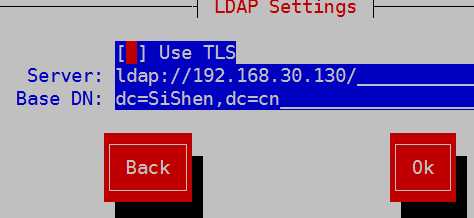
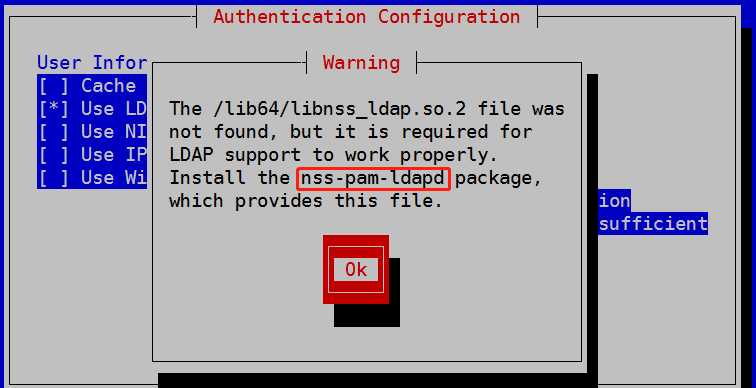
提示这个错误,安装下nss-pam-ldapd即可
测试ldapuser用户是否可以登录
[[email protected] ~]# su - ldapuser1 su: warning: cannot change directory to /ldaphome/ldapuser1: No such file or directory -bash-4.1$ su - ldapuser2 Password: su: warning: cannot change directory to /ldaphome/ldapuser2: No such file or directory -bash-4.1$ whoami ldapuser2
上面虽然可以成功登陆,但是没有家目录,接下来实现家目录漫游
首先在ldap服务端安装并启动nfs
[[email protected] ~]# yum install -y nfs-utils #配置nfs共享目录 [[email protected] ~]# vim /etc/exports /ldaphome/ *(rw) [[email protected] ~]# service nfs restart Shutting down NFS daemon: [ OK ] Shutting down NFS mountd: [ OK ] Shutting down NFS quotas: [ OK ] Shutting down RPC idmapd: [ OK ] Starting NFS services: [ OK ] Starting NFS quotas: [ OK ] Starting NFS mountd: [ OK ] Starting NFS daemon: [ OK ] Starting RPC idmapd: [ OK ] [[email protected] ~]# showmount -e Export list for master: /ldaphome *
在客户端
#安装autofs [[email protected] ~]# yum install -y autofs #配置autofs [[email protected] ~]# vim /etc/auto.master /ldaphome /etc/auto.ldap #添加此行内容 [[email protected] ~]# vim /etc/auto.ldap #此文件为新建文件 * master:/ldaphome/& #添加此行内容 [[email protected] ~]# service autofs restart Stopping automount: [ OK ] Starting automount: [ OK ] [[email protected] ~]# chkconfig autofs on
在客户端测试
[[email protected] ~]# su - ldapuser1 [[email protected] ~]$ whoami #注意看与之前登录之后的区别,有家目录了 ldapuser1 [[email protected] ~]$ su - ldapuser2 Password: [[email protected] ~]$ whoami ldapuser2 [[email protected] ~]$ ls [[email protected] ~]$ touch ldapuser2.txt [[email protected] ~]$ exit logout [[email protected] ~]$ touch ldapuser1.txt [[email protected] ~]$ exit logout
在服务端查看
[[email protected] ~]# ls /ldaphome/ldapuser1/ ldapuser1.txt [[email protected] ~]# ls /ldaphome/ldapuser2/ ldapuser2.txt
OK,到此结束~
以上是关于RHEL 6.5----LDAP实现集中化认证的主要内容,如果未能解决你的问题,请参考以下文章