160个CrackMe 002 Afkayas.1
Posted
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了160个CrackMe 002 Afkayas.1相关的知识,希望对你有一定的参考价值。
首先,同样的操作,PEID查壳: 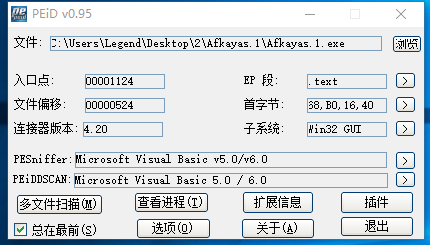
VB的程序,没有壳,OK,注意一下VB中的函数就可以了,这里推荐一个微博,总结了在逆向中常用到的VB的函数
VB程序逆向反汇编常见的函数
试着自己运行: 
OD运行起来,右键,查找,查找所有参考文本字符串,找到错误字符串的位置
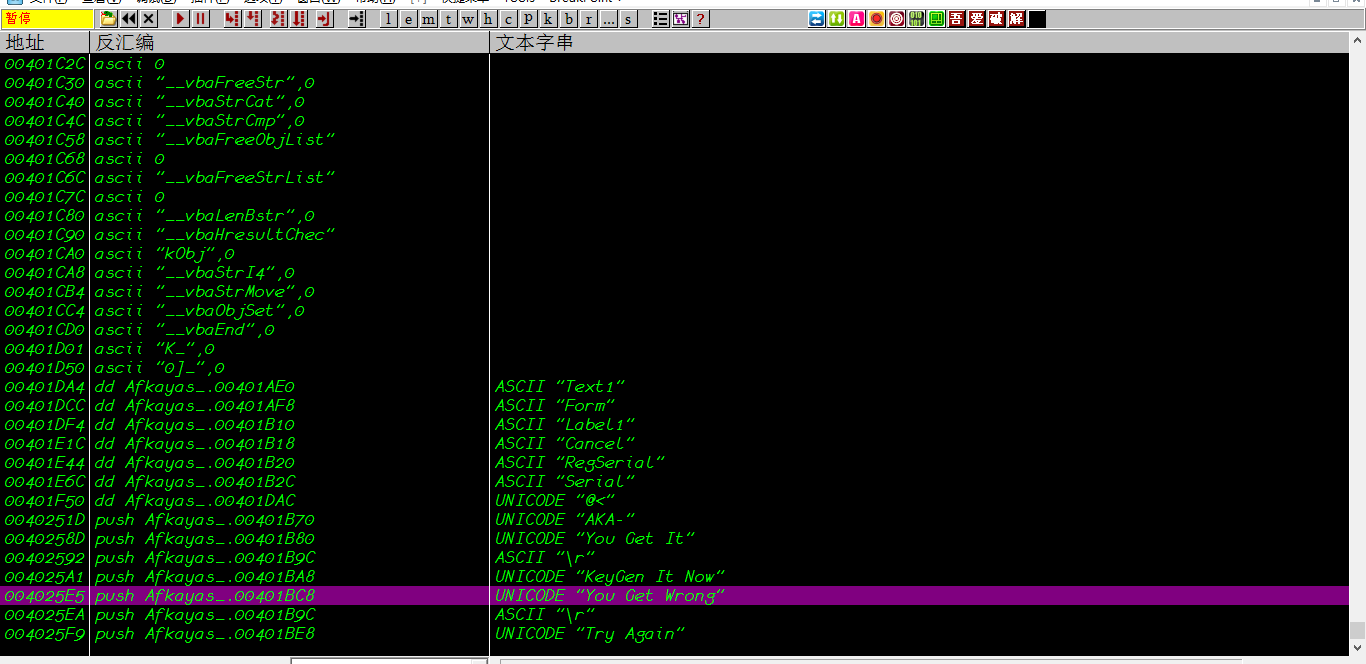
看到我们的错误字符串了,You Get Wrong,并且在上面还发现了应该是正确的字符串,两个字符串相距不远,嗯嗯,这个题目应该不难(至少跳转会少些..)
双击字符串进入位置,发现了跳转指令 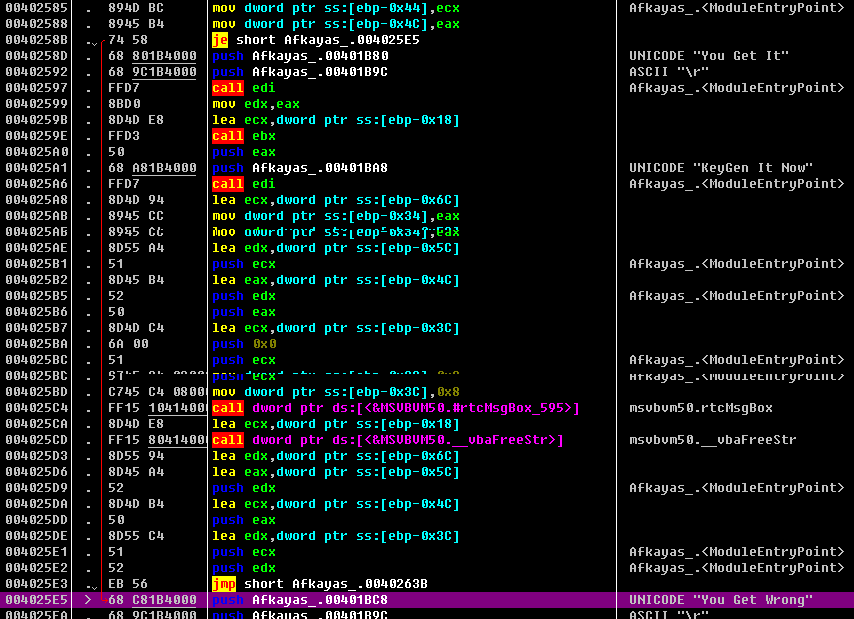
在跳转的位置F2下断,重新运行程序,输入我们瞎扯的字符串上去: 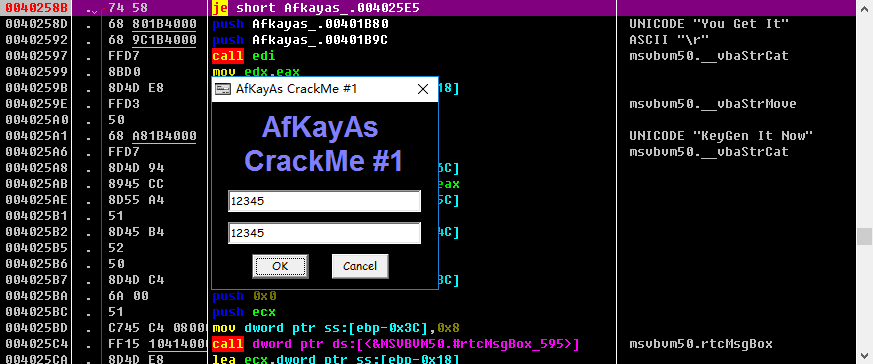
好,停住,向上分析代码,找到及其关键的函数_vbastrcmp()字符串比较函数 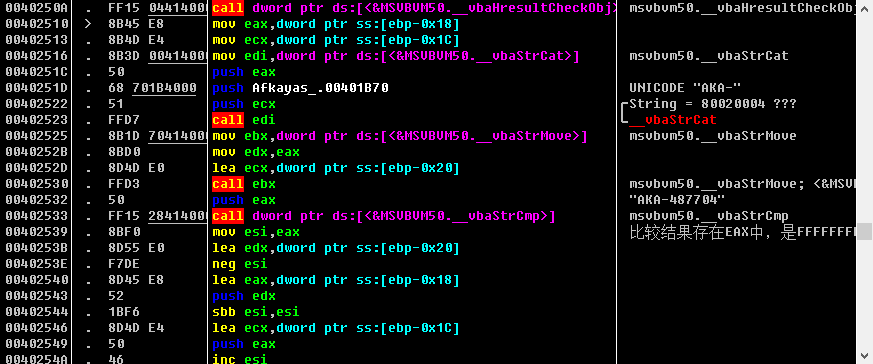
这样的话说明在这时的序列号已经生成了,所以对输入的name和生成的name比较,序列号生成代码就在这片汇编代码中
于是我丧心病狂的找到了这个函数的头部,F2下断: 
重新运行起来,F9到断点的位置,F8一步一步地调试,遇到重要的不认识的VB函数,就去博客上查,知道它是做什么用的就可以,具体分析的过程就不说了,耐心,很简单,分析源码:
00402409 > \8B95 50FFFFFF mov edx,dword ptr ss:[ebp-0xB0] 0040240F . 8B45 E4 mov eax,dword ptr ss:[ebp-0x1C] ; 输入的name:12345 00402412 . 50 push eax ; /String = 0000000A ??? 00402413 . 8B1A mov ebx,dword ptr ds:[edx] ; | 00402415 . FF15 E4404000 call dword ptr ds:[<&MSVBVM50.__vbaLenBstr>] ; \__vbaLenBstr 获得一个字符串的长度 0040241B . 8BF8 mov edi,eax ; 函数的返回值放在EAX寄存器中,本例为5 0040241D . 8B4D E8 mov ecx,dword ptr ss:[ebp-0x18] 00402420 . 69FF FB7C0100 imul edi,edi,0x17CFB ; edi为name的长度乘以0x17CFB 00402426 . 51 push ecx ; /String="1" 取出name的首字符 00402427 . 0F80 91020000 jo Afkayas_.004026BE ; | 0040242D . FF15 F8404000 call dword ptr ds:[<&MSVBVM50.#rtcAnsiValueBstr_516>>; \rtcAnsiValueBstr 计算name首字符的Ascii值 00402433 . 0FBFD0 movsx edx,ax ; 最终edi的值为name的长度乘以0x17cfb在加上第一个字符的ASCII码值 00402436 . 03FA add edi,edx 00402438 . 0F80 80020000 jo Afkayas_.004026BE 0040243E . 57 push edi ; msvbvm50.__vbaStrCat 0040243F . FF15 E0404000 call dword ptr ds:[<&MSVBVM50.__vbaStrI4>] ; msvbm50._vbaStrI4 edi中值16进制转成10进制 00402445 . 8BD0 mov edx,eax ; 得到正确serila的数字部分 00402447 . 8D4D E0 lea ecx,dword ptr ss:[ebp-0x20] 0040244A . FF15 70414000 call dword ptr ds:[<&MSVBVM50.__vbaStrMove>] ; msvbvm50.__vbaStrMove 00402450 . 8BBD 50FFFFFF mov edi,dword ptr ss:[ebp-0xB0] 00402456 . 50 push eax 00402457 . 57 push edi ; msvbvm50.__vbaStrCat 00402458 . FF93 A4000000 call dword ptr ds:[ebx+0xA4] 0040245E . 85C0 test eax,eax 00402460 . 7D 12 jge short Afkayas_.00402474 00402462 . 68 A4000000 push 0xA4 00402467 . 68 5C1B4000 push Afkayas_.00401B5C 0040246C . 57 push edi ; msvbvm50.__vbaStrCat 0040246D . 50 push eax 0040246E . FF15 04414000 call dword ptr ds:[<&MSVBVM50.__vbaHresultCheckObj>] ; msvbvm50.__vbaHresultCheckObj 00402474 > 8D45 E0 lea eax,dword ptr ss:[ebp-0x20] 00402477 . 8D4D E4 lea ecx,dword ptr ss:[ebp-0x1C] 0040247A . 50 push eax 0040247B . 8D55 E8 lea edx,dword ptr ss:[ebp-0x18] 0040247E . 51 push ecx 0040247F . 52 push edx 00402480 . 6A 03 push 0x3 00402482 . FF15 5C414000 call dword ptr ds:[<&MSVBVM50.__vbaFreeStrList>] ; msvbvm50.__vbaFreeStrList 00402488 . 83C4 10 add esp,0x10 0040248B . 8D45 D4 lea eax,dword ptr ss:[ebp-0x2C] 0040248E . 8D4D D8 lea ecx,dword ptr ss:[ebp-0x28] 00402491 . 8D55 DC lea edx,dword ptr ss:[ebp-0x24] 00402494 . 50 push eax 00402495 . 51 push ecx 00402496 . 52 push edx 00402497 . 6A 03 push 0x3 00402499 . FF15 F4404000 call dword ptr ds:[<&MSVBVM50.__vbaFreeObjList>] ; msvbvm50.__vbaFreeObjList 0040249F . 8B06 mov eax,dword ptr ds:[esi] 004024A1 . 83C4 10 add esp,0x10 004024A4 . 56 push esi 004024A5 . FF90 04030000 call dword ptr ds:[eax+0x304] 004024AB . 8B1D 0C414000 mov ebx,dword ptr ds:[<&MSVBVM50.__vbaObjSet>] ; msvbvm50.__vbaObjSet 004024B1 . 50 push eax 004024B2 . 8D45 DC lea eax,dword ptr ss:[ebp-0x24] 004024B5 . 50 push eax 004024B6 . FFD3 call ebx ; msvbvm50.__vbaStrMove; <&MSVBVM50.__vbaObjSet> 004024B8 . 8BF8 mov edi,eax 004024BA . 8D55 E8 lea edx,dword ptr ss:[ebp-0x18] 004024BD . 52 push edx 004024BE . 57 push edi ; msvbvm50.__vbaStrCat 004024BF . 8B0F mov ecx,dword ptr ds:[edi] 004024C1 . FF91 A0000000 call dword ptr ds:[ecx+0xA0] 004024C7 . 85C0 test eax,eax 004024C9 . 7D 12 jge short Afkayas_.004024DD 004024CB . 68 A0000000 push 0xA0 004024D0 . 68 5C1B4000 push Afkayas_.00401B5C 004024D5 . 57 push edi ; msvbvm50.__vbaStrCat 004024D6 . 50 push eax 004024D7 . FF15 04414000 call dword ptr ds:[<&MSVBVM50.__vbaHresultCheckObj>] ; msvbvm50.__vbaHresultCheckObj 004024DD > 56 push esi 004024DE . FF95 40FFFFFF call dword ptr ss:[ebp-0xC0] ; msvbvm50.741CC368 004024E4 . 50 push eax 004024E5 . 8D45 D8 lea eax,dword ptr ss:[ebp-0x28] 004024E8 . 50 push eax 004024E9 . FFD3 call ebx ; msvbvm50.__vbaStrMove 004024EB . 8BF0 mov esi,eax 004024ED . 8D55 E4 lea edx,dword ptr ss:[ebp-0x1C] 004024F0 . 52 push edx 004024F1 . 56 push esi 004024F2 . 8B0E mov ecx,dword ptr ds:[esi] 004024F4 . FF91 A0000000 call dword ptr ds:[ecx+0xA0] 004024FA . 85C0 test eax,eax 004024FC . 7D 12 jge short Afkayas_.00402510 004024FE . 68 A0000000 push 0xA0 00402503 . 68 5C1B4000 push Afkayas_.00401B5C 00402508 . 56 push esi 00402509 . 50 push eax 0040250A . FF15 04414000 call dword ptr ds:[<&MSVBVM50.__vbaHresultCheckObj>] ; msvbvm50.__vbaHresultCheckObj 00402510 > 8B45 E8 mov eax,dword ptr ss:[ebp-0x18] 00402513 . 8B4D E4 mov ecx,dword ptr ss:[ebp-0x1C] 00402516 . 8B3D 00414000 mov edi,dword ptr ds:[<&MSVBVM50.__vbaStrCat>] ; msvbvm50.__vbaStrCat 0040251C . 50 push eax 0040251D . 68 701B4000 push Afkayas_.00401B70 ; UNICODE "AKA-" 00402522 . 51 push ecx ; /String = 80020004 ??? 00402523 . FFD7 call edi ; \__vbaStrCat 00402525 . 8B1D 70414000 mov ebx,dword ptr ds:[<&MSVBVM50.__vbaStrMove>] ; msvbvm50.__vbaStrMove 0040252B . 8BD0 mov edx,eax 0040252D . 8D4D E0 lea ecx,dword ptr ss:[ebp-0x20] 00402530 . FFD3 call ebx ; msvbvm50.__vbaStrMove; <&MSVBVM50.__vbaStrMove> 00402532 . 50 push eax ; "AKA-487704" 00402533 . FF15 28414000 call dword ptr ds:[<&MSVBVM50.__vbaStrCmp>] ; msvbvm50.__vbaStrCmp 00402539 . 8BF0 mov esi,eax ; 比较结果存在EAX中,是FFFFFFFF,说明失败了其中在这个位置的函数_VbaStrI4()
0040243E . 57 push edi 0040243F . FF15 E0404000 call dword ptr ds:[<&MSVBVM50.__vbaStrI4>] ; msvbm50._vbaStrI4 edi中值16进制转成10进制 00402445 . 8BD0 mov edx,eax ; 得到正确serila的数字部分 00402447 . 8D4D E0 lea ecx,dword ptr ss:[ebp-0x20]
它的作用我简单查了一下,没有找到(当然我努力找肯定能找到),但是
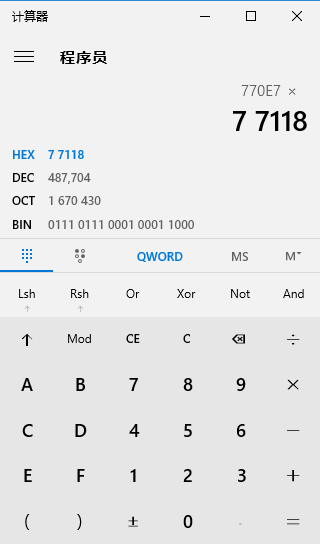
和第一题一样的套路...16进制转10进制字符串
将本例的结果试验一下:
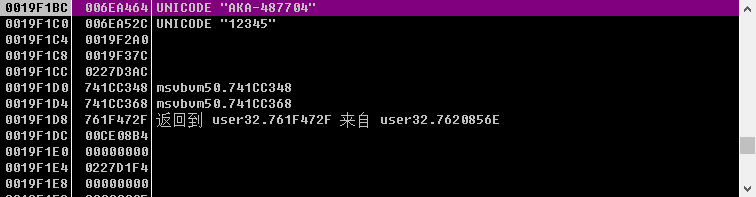
成功!
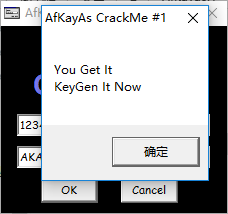
算法分析:
最终生成的serial是
AKA-((name的长度)*0x17CFB+第一个字符的ASCII码值)转成10进制字符串)
OK,写注册机,我要用python
str1=raw_input(‘input your name:‘) length=str1.__len__() c=ord(str1[0]) serial=length*97531+c print ‘serial:‘ print ‘AKA-‘+str(serial)
最后还有的几个JO命令的地方是判断是否溢出的,溢出就直接ERROR。这个我心算了一下...,应该很难溢出,就不考虑了..
这题目还可以用VB的反汇编工具,例如:VB Decompiler
直接看VB源码:
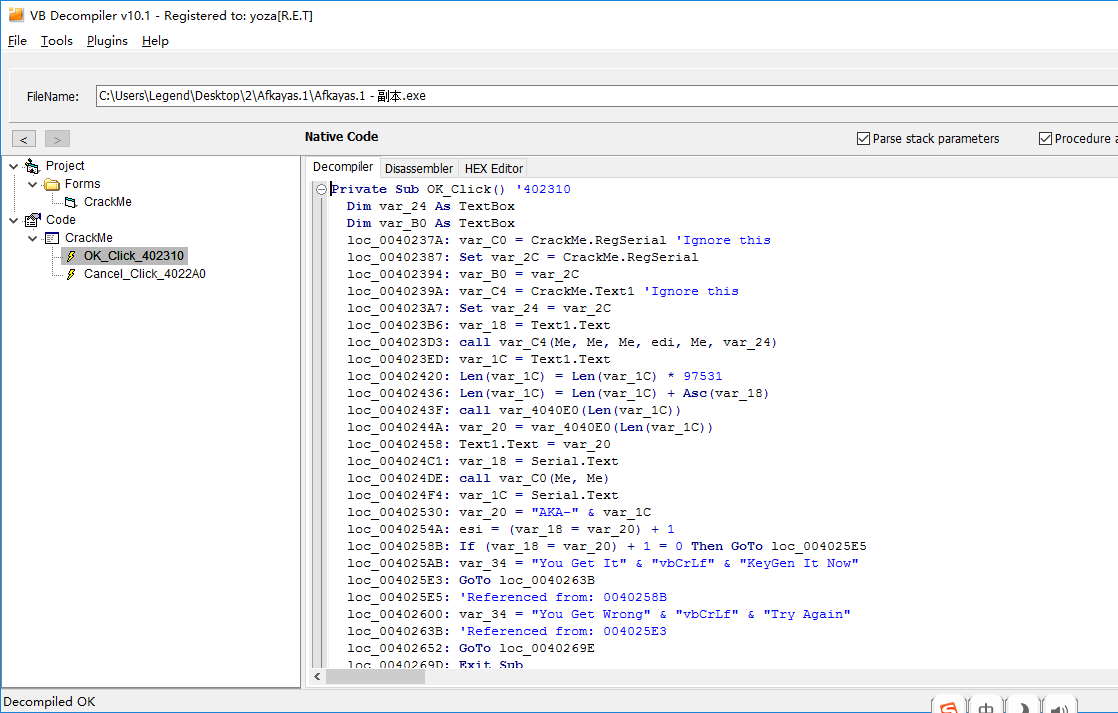
这个是不是很简单
源码:
Private Sub OK_Click() ‘402310 Dim var_24 As TextBox Dim var_B0 As TextBox loc_0040237A: var_C0 = CrackMe.RegSerial ‘Ignore this loc_00402387: Set var_2C = CrackMe.RegSerial loc_00402394: var_B0 = var_2C loc_0040239A: var_C4 = CrackMe.Text1 ‘Ignore this loc_004023A7: Set var_24 = var_2C loc_004023B6: var_18 = Text1.Text loc_004023D3: call var_C4(Me, Me, Me, edi, Me, var_24) loc_004023ED: var_1C = Text1.Text loc_00402420: Len(var_1C) = Len(var_1C) * 97531 loc_00402436: Len(var_1C) = Len(var_1C) + Asc(var_18) loc_0040243F: call var_4040E0(Len(var_1C)) loc_0040244A: var_20 = var_4040E0(Len(var_1C)) loc_00402458: Text1.Text = var_20 loc_004024C1: var_18 = Serial.Text loc_004024DE: call var_C0(Me, Me) loc_004024F4: var_1C = Serial.Text loc_00402530: var_20 = "AKA-" & var_1C loc_0040254A: esi = (var_18 = var_20) + 1 loc_0040258B: If (var_18 = var_20) + 1 = 0 Then GoTo loc_004025E5 loc_004025AB: var_34 = "You Get It" & "vbCrLf" & "KeyGen It Now" loc_004025E3: GoTo loc_0040263B loc_004025E5: ‘Referenced from: 0040258B loc_00402600: var_34 = "You Get Wrong" & "vbCrLf" & "Try Again" loc_0040263B: ‘Referenced from: 004025E3 loc_00402652: GoTo loc_0040269E loc_0040269D: Exit Sub loc_0040269E: ‘Referenced from: 00402652 loc_0040269E: Exit Sub End Sub 相比汇编,这个很容易看懂了,不过借助工具终究是外力,总有工具是有限制的,唯一能改变这点的就是自己NB,谁都骗不过你喽(我还是新手,勿喷).
以上是关于160个CrackMe 002 Afkayas.1的主要内容,如果未能解决你的问题,请参考以下文章