软件公司开发网络环境搭建
Posted
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了软件公司开发网络环境搭建相关的知识,希望对你有一定的参考价值。
一、一路光纤多个公网IP设置
公司192.168.1.0/24子网用于服务器集群,192.168.0.0/24子网用于办公子网,两个子网物理上不在一块。
公司开业时,申请了电信40Mbps专线光纤,5个IP地址,网关:*.168.112.9 255.255.255.248,地址块:*.168.112.10-14,电信公司送了一个光猫,一个路由器,5个公网IP是绑定在一起的,现在需要把公网IP设置在路由器,方便以后服务器向外发布信息,方法有二:
1、从电信送的路由器上拉多条网线到H3C-MSR930路由器上,比如插入H3C-MSR930路由器的G0、G1、G2口,每个端口设置一个公网IP,然后再设置路由策略,就可以使用多个公网IP了,但是这个方法麻烦。
2、因H3C-MSR930路由器是千兆路由器,且只有5个端口,资源非常宝贵,所以决定从电信送的路由器上只拉一条网线插入H3C-MSR930的G0口,用子接口的方式,把公网都设置在这个G0口上,这样路由器设置也省事啊,设置如下:
interface Vlan-interface1
ip address 192.168.0.1 255.255.255.0
dhcp server apply ip-pool vlan1
#
interface
Vlan-interface2
ip address 192.168.1.1 255.255.255.0
#
interface GigabitEthernet0/0
port link-mode route
nat
outbound 2000
ip address
*.168.112.10 255.255.255.248
ip address *.168.112.11 255.255.255.248
sub
ip address *.168.112.12 255.255.255.248 sub
ip address *.168.112.13 255.255.255.248 sub
ip address *.168.112.14 255.255.255.248 sub
ddns apply policy 9xiang.picp.net
dns server 202.96.209.133
dns
server 202.96.209.5
#
interface GigabitEthernet0/1
port link-mode bridge
port access vlan 2
#
interface
GigabitEthernet0/2
port link-mode bridge
port access vlan 2
#
interface GigabitEthernet0/3
port link-mode bridge
port access vlan 2
#
interface GigabitEthernet0/4
port link-mode bridge
port link-type trunk
port trunk permit
vlan all
#
ip route-static 0.0.0.0
0.0.0.0 GigabitEthernet0/0 *.168.112.9
(注:真实地址用*号隐藏下,原因大家晓得,主要是红色字设置)
二、内网服务器映射到公网上访问
软件企业做软件产品,要发布到外网上测试、使用,只需要在出口上做下nat转换就行了,如下在路由器的出口上配置nat。
#
interface GigabitEthernet0/0
port link-mode route
nat
outbound 2000
nat server protocol tcp
global *.168.112.11 8088 inside 192.168.1.1 8088
nat server protocol tcp
global *.168.112.11 8888 inside 192.168.1.170 8181
nat server protocol
tcp global *.168.112.10 8888 inside 192.168.1.168 8080
nat server
protocol tcp global *.168.112.11 8181 inside 192.168.0.56 8181
nat
server protocol tcp global *.168.112.11 18080 inside 192.168.0.36 8080
nat server protocol tcp global *.168.112.11 www inside 192.168.1.197
8080
ip address *.168.112.10 255.255.255.248
ip address
*.168.112.11 255.255.255.248 sub
ip address *.168.112.12 255.255.255.248 sub
ip address *.168.112.13 255.255.255.248 sub
ip address *.168.112.14 255.255.255.248 sub
ddns apply policy 9xiang.picp.net
dns server 202.96.209.133
dns
server 202.96.209.5
#
三、内网通过公网地址访问内部服务器
现在内网服务器发布到外网后,外网是可以正常访问公司的服务器了,但问题是发布到外网后,比如使用浏览器在公司以外网络上访问http://*.168.112.11:8888是可以正常访问的,但公司内网192.168.0.0/24办公网段中访问这个http://*.168.112.11:8888就不能访问了。问题出在路由器上,原来,比如IP是192.168.0.50的电脑发出了访问http://*.168.112.11:8888指令,在TCP协议中指定的目标地址是*.168.112.11:8888,源地址是192.168.0.50,H3C-MSR930路由器在nat地址表里一匹配,发现*.168.112.11:8888对应的IP是192.168.1.170:8181,就把这个请求转给了192.168.1.170:8181服务器,192.168.1.170:8181服务器响应请求,给源地址192.168.0.50给出所要的回应,这时的回应信息打包成目标地址是192.168.0.50,源地址是192.168.1.170:8181发给了目标主机192.168.0.50,但192.168.0.50收到这个回应包后,解开一看,源地址是192.168.1.170:8181发的包,TM我是向*.168.112.11:8888发出的请求,192.168.1.170:8181是哪个二货啊,于是路由器果断把这个包当垃圾丢掉,苦了192.168.0.50上的浏览器,还在苦巴巴的等回应,等了半天没回应,只好显示前途一片黑暗,什么都没有,这就是在内网通过公网地址访问内部服务器的常见故障,解决方法是在内网的VLAN1上再建一个nat转换表,让响应服务器192.168.1.170:8181发给了目标主机192.168.0.50信息在路由器中重新封闭成目标地址是192.168.0.50,源地址是*.168.112.11:8888,就不会被IP是192.168.0.50的电脑给丢掉包了,如下设置:
#
interface Vlan-interface1
ip address 192.168.0.1
255.255.255.0
dhcp server apply ip-pool vlan1
nat server protocol tcp global *.168.112.11 8888 inside
192.168.1.170 8181
nat server protocol tcp global *.168.112.11 8181
inside 192.168.0.56 8181
nat server protocol tcp global *.168.112.11
9090 inside 192.168.1.197 8080
nat server protocol tcp global
*.168.112.10 8888 inside 192.168.1.168 8080
nat server protocol tcp
global *.168.112.11 18080 inside 192.168.0.36 8080
nat server
protocol tcp global *.168.112.11 www inside 192.168.1.197 8080
#
interface Vlan-interface2
ip address 192.168.1.1
255.255.255.0
#
interface GigabitEthernet0/0
port
link-mode route
nat outbound 2000
nat server protocol tcp global
*.168.112.11 8088 inside 192.168.1.1 8088
nat server protocol tcp global
*.168.112.11 8888 inside 192.168.1.170 8181
nat server protocol tcp
global *.168.112.10 8888 inside 192.168.1.168 8080
nat server protocol
tcp global *.168.112.11 8181 inside 192.168.0.56 8181
nat server
protocol tcp global *.168.112.11 18080 inside 192.168.0.36 8080
nat
server protocol tcp global *.168.112.11 www inside 192.168.1.197 8080
ip
address *.168.112.10 255.255.255.248
ip address *.168.112.11
255.255.255.248 sub
ddns apply policy 9xiang.picp.net
dns server
202.96.209.133
dns server 202.96.209.5
#
interface GigabitEthernet0/1
port link-mode bridge
port
access vlan 2
#
interface GigabitEthernet0/2
port
link-mode bridge
port access vlan 2
#
interface
GigabitEthernet0/3
port link-mode bridge
port access vlan 2
#
interface GigabitEthernet0/4
port link-mode bridge
port link-type trunk
port trunk permit vlan all
#
ip
route-static 0.0.0.0 0.0.0.0 GigabitEthernet0/0 *.168.112.9
四、VPN到公司在家办公
有很多资源都在公司的服务器上及NAS上,在家时要访问公司内部的资源,最好就是建立一个L2TP VPN,这样在家中一拔后,就和在公司一样,所有资源地址都不变的被直接打开,要实现这个功能,需要在路由器和电脑上都配置下,首先,路由器端:
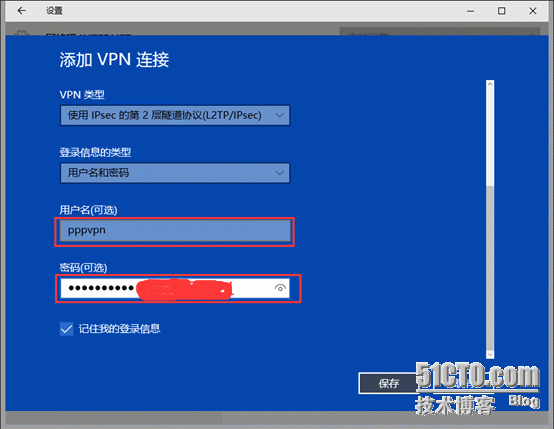
1、建立用来L2TP VPN登陆的用户pppvpn,密码:[email protected]#$
#
local-user admin
password cipher
$c$3$3l/gDC59tw4jJL61545454LbSKBLUvhuT5Wq3
authorization-attribute level
3
service-type telnet
service-type web
local-user pppvpn
password cipher
[email protected]#$
service-type ppp
#
2、为登陆的VPN用户分配IP地址的地址池pool 1。
#
domain system
access-limit disable
state active
idle-cut disable
self-service-url disable
ip pool 1 192.168.2.10 192.168.2.20
#
3、建立VPN封闭方式及虚接口,接入的VPN网关是192.168.2.1
#
l2tp-group 1
undo tunnel
authentication
allow l2tp virtual-template 0
#
interface Aux0
async mode flow
link-protocol ppp
#
interface Cellular0/0
async mode protocol
link-protocol ppp
tcp mss 1024
#
interface Virtual-Template0
ppp
authentication-mode chap domain system
remote address pool 1
ip address 192.168.2.1 255.255.255.0
#
4、电脑端设置(win10)
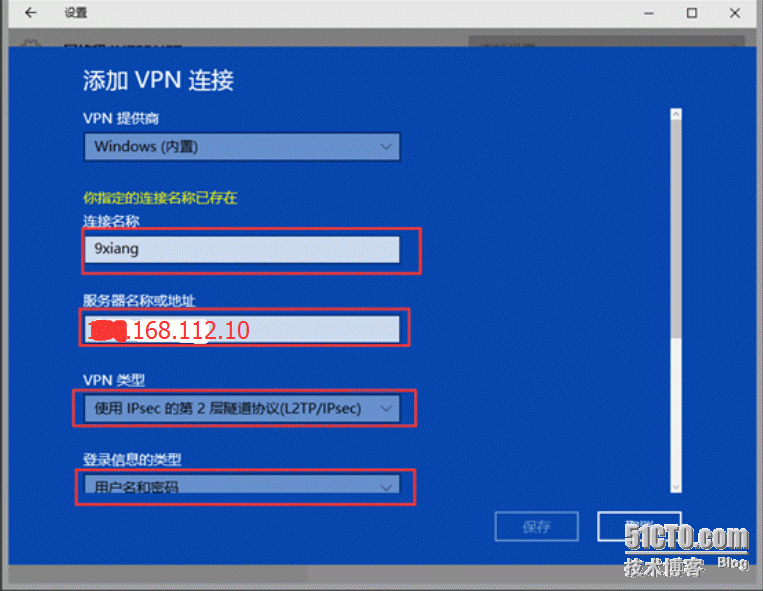
4.1增加VPN(打开网络连接或网络设置)
连接名称可以自己瞎写,服务器IP地址填入为:*.168.112.10
向下翻动如下:
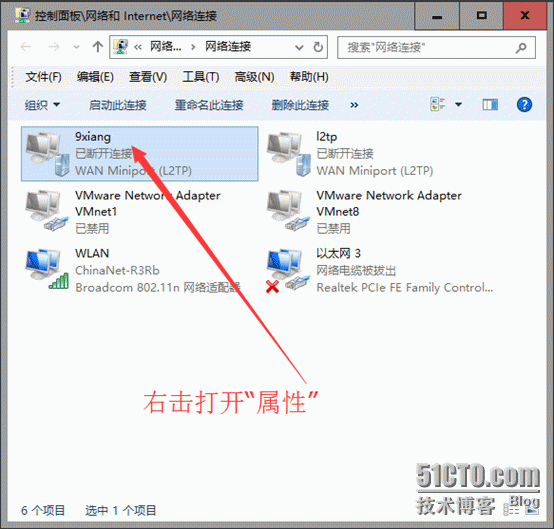
4.2、打开“更改适配器选项”或者打开网络连接
如下修改设置并确定.
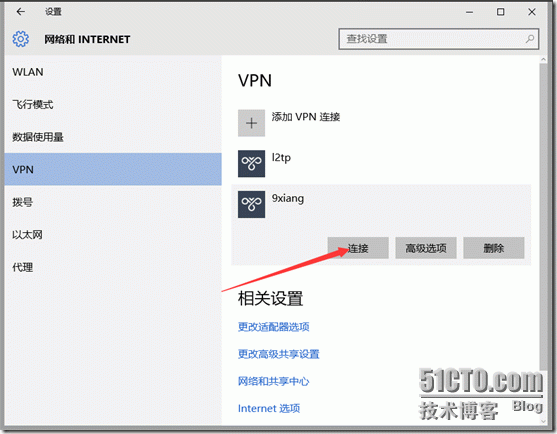
4.3、VPN连接
本文出自 “坚强的技术交流blog” 博客,请务必保留此出处http://newthink.blog.51cto.com/872263/1775483
以上是关于软件公司开发网络环境搭建的主要内容,如果未能解决你的问题,请参考以下文章

![image_thumb[2].png 技术分享](http://s5.51cto.com/wyfs02/M01/80/5F/wKioL1c-17-yLpY8AAEC5QG9_aY925.png)
![image[7].png 技术分享](http://s5.51cto.com/wyfs02/M00/80/5F/wKioL1c-19qCZpqWAACRRJPv_Zs534.png)