玩玩nmap
Posted
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了玩玩nmap相关的知识,希望对你有一定的参考价值。
---恢复内容开始---
[[email protected] ~]# nmap -v Starting Nmap 7.12 ( https://nmap.org ) at 2016-04-04 15:34 CST Read data files from: /usr/bin/../share/nmap WARNING: No targets were specified, so 0 hosts scanned. Nmap done: 0 IP addresses (0 hosts up) scanned in 0.07 seconds Raw packets sent: 0 (0B) | Rcvd: 0 (0B)
nmap用于探查网络、执行安全扫描、网络核查并且在远程机器上找出开放端口。它可以扫描在线的主机、操作系统、包过滤器和远程主机上的开放端口。
nmap命令格式:
Usage: nmap [Scan Type(s)] [Options] {target specification}
1.使用主机名扫描:
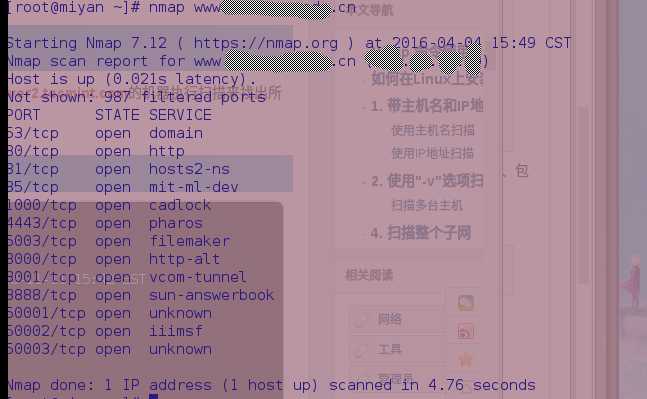
2.使用IP扫描
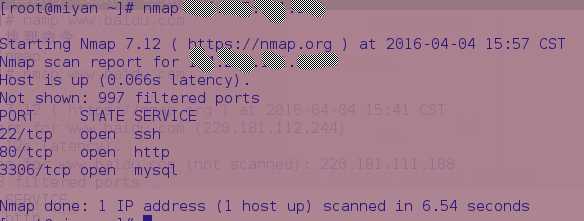
2.使用-v选项可以给出更详细信息
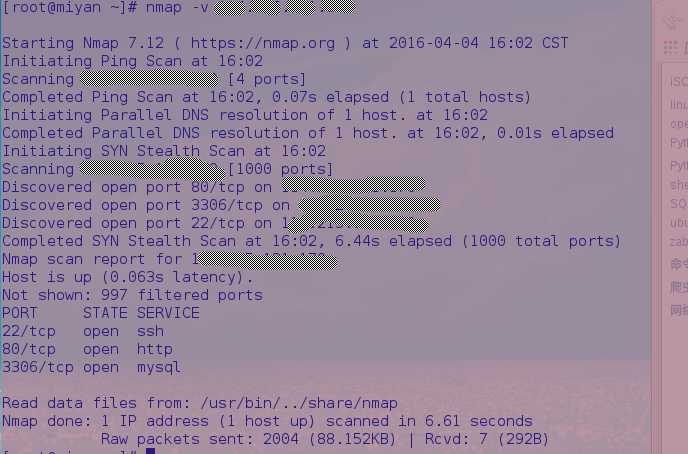
3.扫描多台主机。nmap后面写上多个IP地址或者主机名
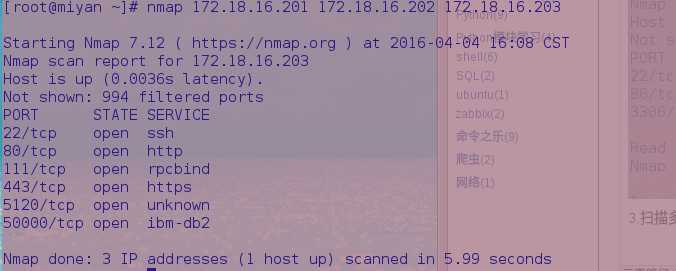
4.使用通配符来使nmap扫描整个子网或者IP段
[[email protected] ~]# nmap 172.18.16.*
耗时太久
5.使用IP地址的最后一段扫描多台主机
[[email protected] ~]# nmap 172.18.16.201,202,203 Starting Nmap 7.12 ( https://nmap.org ) at 2016-04-04 16:26 CST Nmap scan report for 172.18.16.203 Host is up (0.012s latency). Not shown: 994 filtered ports PORT STATE SERVICE 22/tcp open ssh 80/tcp open http 111/tcp open rpcbind 443/tcp open https 5120/tcp open unknown 50000/tcp open ibm-db2 Nmap done: 3 IP addresses (1 host up) scanned in 6.20 seconds
6.从文件中扫描主机列表
将主机名或者IP写到一个文件中,可以直接让nmap读取并执行扫描。
[[email protected] ~]# cat test.txt 172.18.16.201 172.18.16.202 172.18.16.203
执行扫描,使用-iL参数
[[email protected] ~]# nmap -iL test.txt Starting Nmap 7.12 ( https://nmap.org ) at 2016-04-04 16:43 CST Nmap scan report for 172.18.16.203 Host is up (0.015s latency). Not shown: 994 filtered ports PORT STATE SERVICE 22/tcp open ssh 80/tcp open http 111/tcp open rpcbind 443/tcp open https 5120/tcp open unknown 50000/tcp open ibm-db2 Nmap done: 3 IP addresses (1 host up) scanned in 6.08 seconds
7.扫描一个IP段

[[email protected] ~]# nmap 172.18.16.200-220 Starting Nmap 7.12 ( https://nmap.org ) at 2016-04-04 16:46 CST Nmap scan report for 172.18.16.203 Host is up (0.084s latency). Not shown: 994 filtered ports PORT STATE SERVICE 22/tcp open ssh 80/tcp open http 111/tcp open rpcbind 443/tcp open https 5120/tcp open unknown 50000/tcp open ibm-db2 Nmap scan report for 172.18.16.205 Host is up (0.074s latency). Not shown: 997 filtered ports PORT STATE SERVICE 80/tcp open http 3306/tcp open mysql 3389/tcp open ms-wbt-server Nmap scan report for 172.18.16.209 Host is up (0.041s latency). Not shown: 995 filtered ports PORT STATE SERVICE 135/tcp open msrpc 139/tcp open netbios-ssn 445/tcp open microsoft-ds 3389/tcp open ms-wbt-server 10000/tcp open snet-sensor-mgmt Nmap scan report for 172.18.16.214 Host is up (0.052s latency). Not shown: 993 filtered ports PORT STATE SERVICE 135/tcp open msrpc 139/tcp open netbios-ssn 445/tcp open microsoft-ds 2869/tcp open icslap 3389/tcp open ms-wbt-server 5357/tcp open wsdapi 10243/tcp open unknown Nmap scan report for 172.18.16.218 Host is up (0.0043s latency). All 1000 scanned ports on 172.18.16.218 are filtered Nmap done: 21 IP addresses (5 hosts up) scanned in 31.94 seconds
8.排除部分主机

[[email protected] ~]# nmap 172.18.16.200-210 --exclude 172.18.16.205 Starting Nmap 7.12 ( https://nmap.org ) at 2016-04-04 17:12 CST Nmap scan report for 172.18.16.203 Host is up (0.025s latency). Not shown: 994 filtered ports PORT STATE SERVICE 22/tcp open ssh 80/tcp open http 111/tcp open rpcbind 443/tcp open https 5120/tcp open unknown 50000/tcp open ibm-db2 Nmap scan report for 172.18.16.209 Host is up (0.015s latency). Not shown: 995 filtered ports PORT STATE SERVICE 135/tcp open msrpc 139/tcp open netbios-ssn 445/tcp open microsoft-ds 3389/tcp open ms-wbt-server 10000/tcp open snet-sensor-mgmt Nmap done: 10 IP addresses (2 hosts up) scanned in 16.57 seconds
9.扫描系统信息

[[email protected] ~]# nmap -A 172.18.16.203 Starting Nmap 7.12 ( https://nmap.org ) at 2016-04-04 17:14 CST Nmap scan report for 172.18.16.203 Host is up (0.0024s latency). Not shown: 994 filtered ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 3.8.1p1 Debian 8.sarge.4 (protocol 2.0) | ssh-hostkey: |_ 1024 c7:ef:29:9a:6e:2e:f6:08:71:67:d6:cd:db:ef:b2:40 (RSA) 80/tcp open http GoAhead WebServer 111/tcp open rpcbind 2 (RPC #100000) | rpcinfo: | program version port/proto service | 100000 2 111/tcp rpcbind |_ 100000 2 111/udp rpcbind 443/tcp open ssl/http GoAhead WebServer | ssl-cert: Subject: commonName=AMI/organizationName=American Megatrends Inc./stateOrProvinceName=Georgia/countryName=US | Not valid before: 2006-03-08T22:01:07 |_Not valid after: 2006-04-07T22:01:07 5120/tcp open ipmi-usb IPMI USB redirection 50000/tcp open upnp SuperMicro IPMI UPnP Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port Device type: general purpose Running: Linux 2.6.X OS CPE: cpe:/o:linux:linux_kernel:2.6 OS details: Linux 2.6.15 - 2.6.26 (likely embedded) Network Distance: 2 hops Service Info: OS: Linux; Device: remote management; CPE: cpe:/o:linux:linux_kernel, cpe:/o:supermicro:intelligent_platform_management_firmware TRACEROUTE (using port 111/tcp) HOP RTT ADDRESS 1 4.04 ms 192.168.1.1 2 4.02 ms 172.18.16.203 OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 103.10 seconds
同样-O或者-osscan-guess同样可以实现

[[email protected] ~]# nmap -O 172.18.16.203 Starting Nmap 7.12 ( https://nmap.org ) at 2016-04-04 17:21 CST Nmap scan report for 172.18.16.203 Host is up (0.0030s latency). Not shown: 994 filtered ports PORT STATE SERVICE 22/tcp open ssh 80/tcp open http 111/tcp open rpcbind 443/tcp open https 5120/tcp open unknown 50000/tcp open ibm-db2 Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port Device type: general purpose Running: Linux 2.6.X OS CPE: cpe:/o:linux:linux_kernel:2.6 OS details: Linux 2.6.15 - 2.6.26 (likely embedded) Network Distance: 2 hops OS detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 6.22 seconds
10.扫描主机来检测防火墙
[[email protected] ~]# nmap -sA 172.18.16.203 Starting Nmap 7.12 ( https://nmap.org ) at 2016-04-04 17:22 CST Nmap scan report for 172.18.16.203 Host is up (0.0015s latency). All 1000 scanned ports on 172.18.16.203 are filtered Nmap done: 1 IP address (1 host up) scanned in 21.18 seconds
11.检测主机以检查防火墙是否正在工作

[[email protected] ~]# nmap -PN 172.18.16.203 Starting Nmap 7.12 ( https://nmap.org ) at 2016-04-04 17:24 CST Nmap scan report for 172.18.16.203 Host is up (0.0039s latency). Not shown: 994 filtered ports PORT STATE SERVICE 22/tcp open ssh 80/tcp open http 111/tcp open rpcbind 443/tcp open https 5120/tcp open unknown 50000/tcp open ibm-db2 Nmap done: 1 IP address (1 host up) scanned in 4.53 seconds
12.查找网络中的在线主机

[[email protected] ~]# nmap -sP 172.18.16.* Starting Nmap 7.12 ( https://nmap.org ) at 2016-04-04 17:25 CST Nmap scan report for 172.18.16.1 Host is up (0.0026s latency). Nmap scan report for 172.18.16.62 Host is up (0.0039s latency). Nmap scan report for 172.18.16.65 Host is up (0.0021s latency). Nmap scan report for 172.18.16.69 Host is up (0.0045s latency). Nmap scan report for 172.18.16.87 Host is up (0.0025s latency). Nmap scan report for 172.18.16.92 Host is up (0.0082s latency). Nmap scan report for 172.18.16.126 Host is up (0.0016s latency). Nmap scan report for 172.18.16.130 Host is up (0.0023s latency). Nmap scan report for 172.18.16.132 Host is up (0.0029s latency). Nmap scan report for 172.18.16.186 Host is up (0.0048s latency). Nmap scan report for 172.18.16.190 Host is up (0.027s latency). Nmap scan report for 172.18.16.203 Host is up (0.0043s latency). Nmap scan report for 172.18.16.205 Host is up (0.0090s latency). Nmap scan report for 172.18.16.209 Host is up (0.0064s latency). Nmap scan report for 172.18.16.214 Host is up (0.0060s latency). Nmap scan report for 172.18.16.218 Host is up (0.0086s latency). Nmap scan report for 172.18.16.231 Host is up (0.0025s latency). Nmap scan report for 172.18.16.235 Host is up (0.0067s latency). Nmap scan report for 172.18.16.237 Host is up (0.00079s latency). Nmap scan report for 172.18.16.239 Host is up (0.0029s latency). Nmap scan report for 172.18.16.248 Host is up (0.0071s latency). Nmap scan report for 172.18.16.254 Host is up (0.0035s latency). Nmap done: 256 IP addresses (22 hosts up) scanned in 3.40 seconds
13.执行快速扫描
使用-F参数,扫描仅在/usr/share/nmap/nmap-services中列出的端口

[[email protected] ~]# nmap -F 172.18.16.203 Starting Nmap 7.12 ( https://nmap.org ) at 2016-04-04 17:57 CST Nmap scan report for 172.18.16.203 Host is up (0.0041s latency). Not shown: 96 filtered ports PORT STATE SERVICE 22/tcp open ssh 80/tcp open http 111/tcp open rpcbind 443/tcp open https Nmap done: 1 IP address (1 host up) scanned in 1.94 seconds
14.连续扫描端口
[[email protected] ~]# nmap -r 172.18.16.203 Starting Nmap 7.12 ( https://nmap.org ) at 2016-04-04 18:01 CST Nmap scan report for 172.18.16.203 Host is up (0.0083s latency). Not shown: 994 filtered ports PORT STATE SERVICE 22/tcp open ssh 80/tcp open http 111/tcp open rpcbind 443/tcp open https 5120/tcp open unknown 50000/tcp open ibm-db2 Nmap done: 1 IP address (1 host up) scanned in 4.16 seconds
15.显示主机及路由
列出本机的主机接口与路由信息

[[email protected] ~]# nmap --iflist Starting Nmap 7.12 ( https://nmap.org ) at 2016-04-04 18:02 CST ************************INTERFACES************************ DEV (SHORT) IP/MASK TYPE UP MTU MAC enp3s0 (enp3s0) (none)/0 ethernet up 1500 F0:DE:F1:39:B9:9C virbr0-nic (virbr0-nic) (none)/0 ethernet down 1500 52:54:00:D1:81:64 wlp4s0b1 (wlp4s0b1) 192.168.1.8/24 ethernet up 1500 AC:81:12:2B:0E:AA wlp4s0b1 (wlp4s0b1) fe80::ae81:12ff:fe2b:eaa/64 ethernet up 1500 AC:81:12:2B:0E:AA docker0 (docker0) 172.17.0.1/16 ethernet up 1500 02:42:D1:E0:5D:AC virbr0 (virbr0) 192.168.124.1/24 ethernet up 1500 52:54:00:D1:81:64 lo (lo) 127.0.0.1/8 loopback up 65536 lo (lo) ::1/128 loopback up 65536 **************************ROUTES************************** DST/MASK DEV METRIC GATEWAY 192.168.124.0/24 virbr0 0 192.168.1.0/24 wlp4s0b1 600 172.17.0.0/16 docker0 0 0.0.0.0/0 wlp4s0b1 600 192.168.1.1 ::1/128 lo 0 fe80::ae81:12ff:fe2b:eaa/128 lo 0 fe80::/64 wlp4s0b1 256 ff00::/8 wlp4s0b1 256
16.扫描特定端口
[[email protected] ~]# nmap -p 80 172.18.16.203 Starting Nmap 7.12 ( https://nmap.org ) at 2016-04-04 18:04 CST Nmap scan report for 172.18.16.203 Host is up (0.0015s latency). PORT STATE SERVICE 80/tcp open http Nmap done: 1 IP address (1 host up) scanned in 0.09 seconds
扫描多个端口
[[email protected] ~]# nmap -p 80,135 172.18.16.203 Starting Nmap 7.12 ( https://nmap.org ) at 2016-04-04 18:11 CST Nmap scan report for 172.18.16.203 Host is up (0.0015s latency). PORT STATE SERVICE 80/tcp open http 135/tcp filtered msrpc Nmap done: 1 IP address (1 host up) scanned in 1.31 seconds
指定端口范围:
[[email protected] ~]# nmap -p 80-160 172.18.16.203 Starting Nmap 7.12 ( https://nmap.org ) at 2016-04-04 18:16 CST Nmap scan report for 172.18.16.203 Host is up (0.0022s latency). Not shown: 79 filtered ports PORT STATE SERVICE 80/tcp open http 111/tcp open rpcbind Nmap done: 1 IP address (1 host up) scanned in 1.81 seconds
17.扫描TCP端口
指定nmap扫描的端口类型和端口号
[[email protected] ~]# nmap -p T:80 172.18.16.203 Starting Nmap 7.12 ( https://nmap.org ) at 2016-04-04 18:08 CST Nmap scan report for 172.18.16.203 Host is up (0.0028s latency). PORT STATE SERVICE 80/tcp open http Nmap done: 1 IP address (1 host up) scanned in 0.11 seconds
18.扫描UDP端口
[[email protected] ~]# nmap -sU 53 172.18.16.203
19.找出远程主机服务版本号

[[email protected] ~]# nmap -sV 172.18.16.203 Starting Nmap 7.12 ( https://nmap.org ) at 2016-04-04 18:18 CST Nmap scan report for 172.18.16.203 Host is up (0.0048s latency). Not shown: 994 filtered ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 3.8.1p1 Debian 8.sarge.4 (protocol 2.0) 80/tcp open http GoAhead WebServer 111/tcp open rpcbind 2 (RPC #100000) 443/tcp open ssl/http GoAhead WebServer 5120/tcp open ipmi-usb IPMI USB redirection 50000/tcp open upnp SuperMicro IPMI UPnP Service Info: OS: Linux; Device: remote management; CPE: cpe:/o:linux:linux_kernel, cpe:/o:supermicro:intelligent_platform_management_firmware Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 48.88 seconds
20.使用TCP ACK(PA)和TCP Syn(PS)扫描主机
有时包过滤防火墙阻止了标准ICMPping请求,在这个情况下,使用TCP ACK和TCP Syn方法来扫描远程主机

[[email protected] ~]# nmap -PS 172.18.16.203 Starting Nmap 7.12 ( https://nmap.org ) at 2016-04-04 18:23 CST Nmap scan report for 172.18.16.203 Host is up (0.0073s latency). Not shown: 994 filtered ports PORT STATE SERVICE 22/tcp open ssh 80/tcp open http 111/tcp open rpcbind 443/tcp open https 5120/tcp open unknown 50000/tcp open ibm-db2 Nmap done: 1 IP address (1 host up) scanned in 4.68 seconds
[email protected] ~]# nmap -PA 172.18.16.203
TCP Syn(PS)扫描远程主机的特定端口
Starting Nmap 7.12 ( https://nmap.org ) at 2016-04-04 18:26 CST Nmap scan report for 172.18.16.203 Host is up (0.0014s latency). PORT STATE SERVICE 80/tcp open http Nmap done: 1 IP address (1 host up) scanned in 0.10 seconds
TCP Syn(PS)扫描最常用端口

[[email protected] ~]# nmap -sT 172.18.16.203 Starting Nmap 7.12 ( https://nmap.org ) at 2016-04-04 18:28 CST Nmap scan report for 172.18.16.203 Host is up (0.0025s latency). Not shown: 994 filtered ports PORT STATE SERVICE 22/tcp open ssh 80/tcp open http 111/tcp open rpcbind 443/tcp open https 5120/tcp open unknown 50000/tcp open ibm-db2 Nmap done: 1 IP address (1 host up) scanned in 4.29 seconds
21.执行隐秘扫描

[[email protected] ~]# nmap -sS 172.18.16.203 Starting Nmap 7.12 ( https://nmap.org ) at 2016-04-04 18:27 CST Nmap scan report for 172.18.16.203 Host is up (0.0062s latency). Not shown: 994 filtered ports PORT STATE SERVICE 22/tcp open ssh 80/tcp open http 111/tcp open rpcbind 443/tcp open https 5120/tcp open unknown 50000/tcp open ibm-db2 Nmap done: 1 IP address (1 host up) scanned in 4.88 seconds
22.tcp空扫描
[[email protected] ~]# nmap -sN 172.18.16.203 Starting Nmap 7.12 ( https://nmap.org ) at 2016-04-04 18:30 CST Nmap scan report for 172.18.16.203 Host is up (0.0013s latency). All 1000 scanned ports on 172.18.16.203 are open|filtered Nmap done: 1 IP address (1 host up) scanned in 21.15 seconds
原文地址:
https://linux.cn/article-2561-3.html
以上是关于玩玩nmap的主要内容,如果未能解决你的问题,请参考以下文章
