DES的雪崩效应分析
Posted Tinoryj
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了DES的雪崩效应分析相关的知识,希望对你有一定的参考价值。
明文固定,密钥改变一个字节
假定明文为11111111(00000001 00000001 00000001 00000001 00000001 00000001 00000001 00000001);
密钥为12345678(00000001 00000010 00000011 00000100 00000101 00000110 00000111 00001000)。
密钥变动为10345678(00000001 00000000 00000011 00000100 00000101 00000110 00000111 00001000)仅变动一位。
进行分析:
使用原密钥12345678加密后的最终结果为:
D 6 9 0 F 1 E E 3 4 B C 5 5 4 5
使用变动后密钥10345678加密后的最终结果为:
4 7 B 3 6 1 5 5 A 5 B 3 1 5 2 A
每一轮数出的加密结果详见附录A,通过统计分析,得到每一轮的加密结果差异bit位数如下表所示:
| 加密轮数 | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 |
|---|---|---|---|---|---|---|---|---|
| 密文相差bit数 | 4 | 18 | 29 | 29 | 30 | 28 | 28 | 28 |
| 加密轮数 | 9 | 10 | 11 | 12 | 13 | 14 | 15 | 16 |
|---|---|---|---|---|---|---|---|---|
| 密文相差bit数 | 29 | 30 | 27 | 31 | 32 | 29 | 28 | 28 |
密钥固定,明文改变一个字节
假定密钥为11111111(00000001 00000001 00000001 00000001 00000001 00000001 00000001 00000001);
明文为12345678(00000001 00000010 00000011 00000100 00000101 00000110 00000111 00001000)。
明文变动为10345678(00000001 00000000 00000011 00000100 00000101 00000110 00000111 00001000)仅变动一位。
进行分析:
将原明文12345678加密后的最终结果为:
9 9 F B 3 C A 8 1 4 2 E 8 3 2 1
将变动后的明文10345678加密后的最终结果为:
2 7 8 B F B E 1 9 F 8 D 7 2 3 6
每一轮数出的加密结果详见附录A,通过统计分析,得到每一轮的加密结果差异bit位数如下表所示:
通过统计分析,可以得到
| 加密轮数 | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 |
|---|---|---|---|---|---|---|---|---|
| 密文相差bit数 | 1 | 4 | 15 | 31 | 33 | 33 | 37 | 34 |
| 加密轮数 | 9 | 10 | 11 | 12 | 13 | 14 | 15 | 16 |
|---|---|---|---|---|---|---|---|---|
| 密文相差bit数 | 32 | 37 | 37 | 33 | 28 | 30 | 36 | 34 |
由此可以看出,DES加密具有雪崩效应。
设计Feistel结构密码
Feistel密码结构设计思路:
- 令\\(F\\)为轮函数;
- 令\\(K_1,K_2,\\cdots,K_i,\\cdots,K_n\\)分别为第\\(1,2,\\cdots,i,\\cdots,n\\)轮的子密钥。
- 在每一轮中,将明文信息均分为两块\\((L_0,R_0)\\);
- 加密过程:\\(L_i = R_{i-1}; R_i = L_{i-1} \\oplus F(R_{i-1},K_i)\\)
- 解密过程:\\(R_{i-1} = L_i; L_{i-1} = R_i\\oplus F(R_{i-1},K_i) = R_i\\oplus F(L_i,K_i)\\)
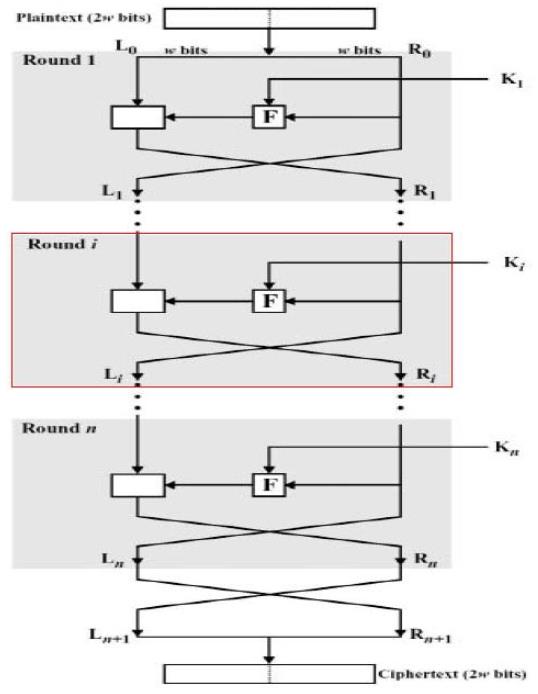 

与DES不同的设计
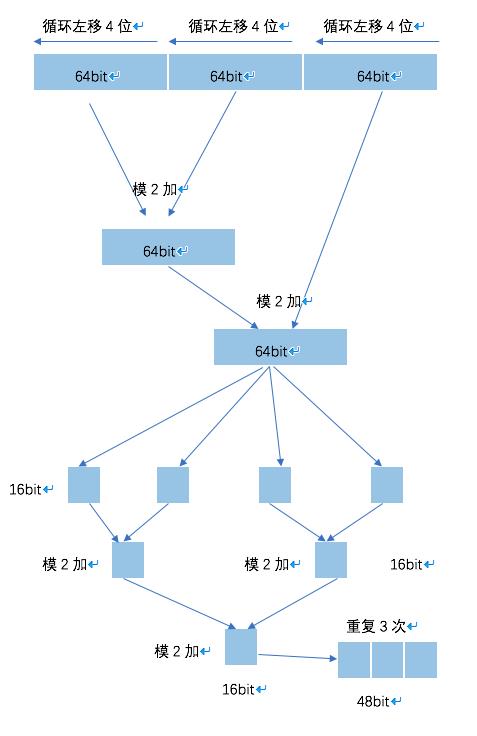
密钥设计
密钥总长度为192bit,设置时字符均为标准ASCII字符。密钥前128位和后64位组合,实现CM方式加密。
轮密钥生成
取出密钥前128bit,分为左64bit和右64bit,每一轮加密过程中,左右64bit循环左移4位。将移位后的左右半密钥做模2加运算。同时,在每轮中,密钥的后64bit循环左移4位。将两部分做模2加运算。最终得到64bit密钥。对于得到的64bit密钥,将其分为四段,每段16bit,做模2加运算后得到16bit密钥,扩展三倍,得到每轮所需要的轮密钥。
过程如下图所示

程序测试:
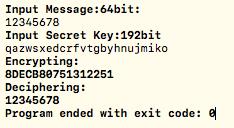 

相关代码详见附录B
附录A
原密钥加密各轮产生的密文bit
1 1 1 1 1 1 1 1 0 0 0 0 0 0 0 0 1 1 1 1 1 1 1 1 0 0 0 0 0 0 0 0 1 1 1 0 0 1 0 0 1 1 1 0 1 1 1 1 1 1 0 1 1 0 0 0 0 0 1 0 0 0 1 1
1 1 1 0 0 1 0 0 1 1 1 0 1 1 1 1 1 1 0 1 1 0 0 0 0 0 1 0 0 0 1 1 0 1 0 1 0 0 0 1 0 0 1 0 1 0 1 0 0 0 1 1 1 1 1 0 0 0 0 1 0 1 0 1
0 1 0 1 0 0 0 1 0 0 1 0 1 0 1 0 0 0 1 1 1 1 1 0 0 0 0 1 0 1 0 1 1 0 0 1 1 0 1 1 1 1 0 0 1 0 0 0 0 0 0 1 1 1 0 0 0 0 0 1 0 0 0 1
1 0 0 1 1 0 1 1 1 1 0 0 1 0 0 0 0 0 0 1 1 1 0 0 0 0 0 1 0 0 0 1 0 1 1 0 0 1 1 0 0 1 1 0 1 0 0 0 0 0 1 0 0 0 0 1 1 1 1 0 1 1 1 1
0 1 1 0 0 1 1 0 0 1 1 0 1 0 0 0 0 0 1 0 0 0 0 1 1 1 1 0 1 1 1 1 0 0 1 0 1 1 0 1 0 1 0 0 1 1 0 0 1 0 0 1 0 0 1 1 0 0 1 1 0 0 1 1
0 0 1 0 1 1 0 1 0 1 0 0 1 1 0 0 1 0 0 1 0 0 1 1 0 0 1 1 0 0 1 1 1 0 1 0 1 1 0 1 0 0 1 0 0 1 1 0 1 1 1 1 1 1 1 1 1 1 0 0 1 1 1 1
1 0 1 0 1 1 0 1 0 0 1 0 0 1 1 0 1 1 1 1 1 1 1 1 1 1 0 0 1 1 1 1 0 1 1 1 0 1 1 0 1 1 1 0 0 1 1 0 1 1 0 0 0 0 0 1 1 0 1 0 1 0 1 1
0 1 1 1 0 1 1 0 1 1 1 0 0 1 1 0 1 1 0 0 0 0 0 1 1 0 1 0 1 0 1 1 0 0 1 1 1 0 1 1 1 1 0 1 0 0 0 1 0 1 0 1 0 0 0 0 1 1 0 0 0 1 0 0
0 0 1 1 1 0 1 1 1 1 0 1 0 0 0 1 0 1 0 1 0 0 0 0 1 1 0 0 0 1 0 0 1 0 0 0 0 1 1 1 1 1 0 1 0 1 1 0 0 1 0 1 1 1 0 0 1 1 1 1 1 1 0 1
1 0 0 0 0 1 1 1 1 1 0 1 0 1 1 0 0 1 0 1 1 1 0 0 1 1 1 1 1 1 0 1 1 0 1 1 1 1 0 0 0 1 1 0 0 0 0 1 0 0 0 1 0 1 0 0 0 1 0 1 0 1 0 1
1 0 1 1 1 1 0 0 0 1 1 0 0 0 0 1 0 0 0 1 0 1 0 0 0 1 0 1 0 1 0 1 1 1 1 1 1 0 1 1 1 1 1 0 1 0 0 1 0 1 1 1 0 0 1 0 1 1 1 0 0 0 0 1
1 1 1 1 1 0 1 1 1 1 1 0 1 0 0 1 0 1 1 1 0 0 1 0 1 1 1 0 0 0 0 1 0 1 1 1 1 1 0 0 0 1 0 0 0 0 1 1 1 0 0 0 0 1 0 1 0 0 0 1 1 0 0 0
0 1 1 1 1 1 0 0 0 1 0 0 0 0 1 1 1 0 0 0 0 1 0 1 0 0 0 1 1 0 0 0 0 0 0 0 0 1 1 1 0 0 0 1 0 0 1 0 1 1 0 0 1 1 0 0 1 0 0 0 1 0 1 0
0 0 0 0 0 1 1 1 0 0 0 1 0 0 1 0 1 1 0 0 1 1 0 0 1 0 0 0 1 0 1 0 1 0 0 1 1 1 0 1 0 1 1 0 1 0 0 1 0 0 1 1 1 1 1 1 1 1 1 1 1 0 0 1
1 0 0 1 1 1 0 1 0 1 1 0 1 0 0 1 0 0 1 1 1 1 1 1 1 1 1 1 1 0 0 1 0 0 1 1 1 1 0 0 0 0 1 0 1 1 1 1 0 0 0 0 1 0 0 1 0 0 1 0 1 0 0 0
0 0 1 1 1 1 0 0 0 0 1 0 1 1 1 1 0 0 0 0 1 0 0 1 0 0 1 0 1 0 0 0 0 1 1 1 0 1 1 1 1 1 0 0 1 1 0 1 1 1 0 0 0 1 0 0 1 1 1 1 1 0 0 1
改变密钥后各轮得到的密文bit
1 1 1 1 1 1 1 1 0 0 0 0 0 0 0 0 1 1 1 1 1 1 1 1 0 0 0 0 0 0 0 0 1 1 1 0 0 1 0 0 0 1 1 0 1 1 1 1 0 1 0 1 1 0 1 0 0 0 1 0 0 0 0 1
1 1 1 0 0 1 0 0 0 1 1 0 1 1 1 1 0 1 0 1 1 0 1 0 0 0 1 0 0 0 0 1 0 0 0 1 0 0 0 0 0 1 0 0 1 0 0 1 0 1 1 0 0 1 1 0 1 0 1 0 1 0 0 1
0 0 0 1 0 0 0 0 0 1 0 0 1 0 0 1 0 1 1 0 0 1 1 0 1 0 1 0 1 0 0 1 0 1 0 1 1 0 1 0 0 0 0 0 0 0 1 0 1 0 0 0 1 1 1 0 0 1 1 0 1 0 1 1
0 1 0 1 1 0 1 0 0 0 0 0 0 0 1 0 1 0 0 0 1 1 1 0 0 1 1 0 1 0 1 1 0 1 0 1 1 0 1 1 0 1 0 0 0 0 0 1 0 0 1 1 0 1 1 1 0 1 1 0 0 0 1 1
0 1 0 1 1 0 1 1 0 1 0 0 0 0 0 1 0 0 1 1 0 1 1 1 0 1 1 0 0 0 1 1 1 0 1 1 1 0 0 0 0 1 1 1 1 1 0 1 0 1 1 0 0 0 0 0 0 0 1 0 0 1 0 1
1 0 1 1 1 0 0 0 0 1 1 1 1 1 0 1 0 1 1 0 0 0 0 0 0 0 1 0 0 1 0 1 0 1 1 1 1 0 1 1 0 0 0 0 1 1 1 0 1 0 0 1 1 1 1 1 1 1 1 1 1 1 0 1
0 1 1 1 1 0 1 1 0 0 0 0 1 1 1 0 1 0 0 1 1 1 1 1 1 1 1 1 1 1 0 1 0 0 0 0 1 0 1 1 1 0 0 0 1 1 1 0 0 0 1 0 0 0 0 0 0 1 0 0 1 0 1 1
0 0 0 0 1 0 1 1 1 0 0 0 1 1 1 0 0 0 1 0 0 0 0 0 0 1 0 0 1 0 1 1 1 0 1 0 1 1 0 0 0 1 0 0 0 0 0 1 0 1 0 1 0 0 1 1 1 1 1 1 0 0 0 0
1 0 1 0 1 1 0 0 0 1 0 0 0 0 0 1 0 1 0 1 0 0 1 1 1 1 1 1 0 0 0 0 0 1 1 1 1 1 0 0 1 1 1 1 1 1 1 1 1 1 1 1 0 1 1 0 0 1 1 0 0 1 0 1
0 1 1 1 1 1 0 0 1 1 1 1 1 1 1 1 1 1 1 1 0 1 1 0 0 1 1 0 0 1 0 1 0 0 1 1 0 1 1 1 0 1 1 1 0 1 0 0 1 1 1 1 0 1 0 0 0 1 1 1 1 0 0 1
0 0 1 1 0 1 1 1 0 1 1 1 0 1 0 0 1 1 1 1 0 1 0 0 0 1 1 1 1 0 0 1 0 1 1 0 1 0 1 0 0 1 0 0 1 0 1 1 1 0 0 1 0 1 0 0 0 1 1 0 1 1 0 1
0 1 1 0 1 0 1 0 0 1 0 0 1 0 1 1 1 0 0 1 0 1 0 0 0 1 1 0 1 1 0 1 1 1 1 1 0 0 1 0 1 0 1 1 0 1 0 1 0 1 0 0 0 1 0 0 0 1 1 1 0 0 0 1
1 1 1 1 0 0 1 0 1 0 1 1 0 1 0 1 0 1 0 0 0 1 0 0 0 1 1 1 0 0 0 1 0 0 1 0 1 0 1 0 0 1 0 1 1 0 1 1 1 0 1 1 0 1 1 0 1 0 1 0 0 0 1 1
0 0 1 0 1 0 1 0 0 1 0 1 1 0 1 1 1 0 1 1 0 1 1 0 1 0 1 0 0 0 1 1 1 0 1 1 0 1 0 0 0 0 0 1 0 0 0 1 0 0 0 0 1 0 1 1 0 1 1 0 0 0 0 0
1 0 1 1 0 1 0 0 0 0 0 1 0 0 0 1 0 0 0 0 1 0 1 1 0 1 1 0 0 0 0 0 1 0 1 1 0 1 1 0 0 0 1 1 0 0 1 0 1 0 1 0 0 0 1 1 1 0 0 0 0 0 0 0
1 0 1 1 0 1 1 0 0 0 1 1 0 0 1 0 1 0 1 0 0 0 1 1 1 0 0 0 0 0 0 0 0 1 1 0 1 0 1 0 0 0 0 0 1 1 0 1 0 1 1 1 1 1 1 1 0 1 0 1 1 0 0 1
原明文加密各轮产生的密文bit
0 1 0 1 0 1 0 1 0 1 1 1 1 0 0 0 1 1 1 1 1 1 1 1 0 0 0 0 0 0 0 0 1 1 0 0 1 0 1 0 1 0 1 0 0 1 1 0 0 0 0 0 1 0 0 0 0 0 0 1 0 0 1 1
1 1 0 0 1 0 1 0 1 0 1 0 0 1 1 0 0 0 0 0 1 0 0 0 0 0 0 1 0 0 1 1 1 0 0 1 0 1 0 0 0 1 1 1 0 1 1 0 0 0 0 0 0 0 1 0 1 1 1 0 1 0 1 1
1 0 0 1 0 1 0 0 0 1 1 1 0 1 1 0 0 0 0 0 0 0 1 0 1 1 1 0 1 0 1 1 1 0 1 1 0 0 0 1 0 0 0 1 0 0 1 1 1 1 1 0 1 1 1 0 0 0 0 1 0 1 0 0
1 0 1 1 0 0 0 1 0 0 0 1 0 0 1 1 1 1 1 0 1 1 1 0 0 0 0 1 0 1 0 0 0 0 0 1 0 0 1 1 1 0 1 1 0 1 0 1 1 1 0 0 1 1 1 0 0 0 1 0 0 0 1 1
0 0 0 1 0 0 1 1 1 0 1 1 0 1 0 1 1 1 0 0 1 1 1 0 0 0 1 0 0 0 1 1 0 1 0 1 0 1 1 0 0 1 0 0 1 1 0 1 1 1 0 1 0 0 1 0 1 1 0 0 0 0 1 0
0 1 0 1 0 1 1 0 0 1 0 0 1 1 0 1 1 1 0 1 0 0 1 0 1 1 0 0 0 0 1 0 1 0 1 0 1 0 1 1 1 0 1 0 1 0 1 1 1 1 0 0 1 0 1 1 0 1 1 0 0 1 0 0
1 0 1 0 1 0 1 1 1 0 1 0 1 0 1 1 1 1 0 0 1 0 1 1 0 1 1 0 0 1 0 0 0 1 1 0 1 1 0 0 0 0 0 1 0 1 0 1 1 1 1 0 0 0 1 0 0 0 0 0 0 0 1 1
0 1 1 0 1 1 0 0 0 0 0 1 0 1 0 1 1 1 1 0 0 0 1 0 0 0 0 0 0 0 1 1 1 1 0 0 0 1 1 0 1 0 1 1 0 1 1 1 0 1 1 1 1 1 0 0 0 0 1 1 0 0 0 1
1 1 0 0 0 1 1 0 1 0 1 1 0 1 1 1 0 1 1 1 1 1 0 0 0 0 1 1 0 0 0 1 0 0 0 0 1 0 1 1 0 1 1 1 1 1 1 0 0 1 1 1 1 1 1 0 0 0 1 1 0 1 1 0
0 0 0 0 1 0 1 1 0 1 1 1 1 1 1 0 0 1 1 1 1 1 1 0 0 0 1 1 0 1 1 0 0 1 1 1 1 1 0 1 0 1 1 0 0 0 0 0 0 0 1 0 1 0 1 1 1 1 0 0 0 0 0 1
0 1 1 1 1 1 0 1 0 1 1 0 0 0 0 0 0 0 1 0 1 0 1 1 1 1 0 0 0 0 0 1 0 1 1 1 1 0 0 0 1 0 1 0 1 1 0 0 1 1 0 0 1 1 1 0 0 0 1 0 1 0 0 0
0 1 1 1 1 0 0 0 1 0 1 0 1 1 0 0 1 1 0 0 1 1 1 0 0 0 1 0 1 0 0 0 1 1 0 0 0 1 1 1 0 1 1 1 1 0 0 1 1 1 1 1 1 0 1 1 0 1 1 0 0 0 0 1
1 1 0 0 0 1 1 1 0 1 1 1 1 0 0 1 1 1 1 1 1 0 1 1 0 1 1 0 0 0 0 1 0 1 1 0 0 1 0 1 0 0 0 1 1 0 0 0 0 1 1 1 1 1 0 1 1 1 0 1 1 0 1 0
0 1 1 0 0 1 0 1 0 0 0 1 1 0 0 0 0 1 1 1 1 1 0 1 1 1 0 1 1 0 1 0 0 0 0 0 1 0 1 1 1 1 0 1 1 0 0 1 0 0 0 0 0 0 0 0 0 1 0 1 1 0 0 1
0 0 0 0 1 0 1 1 1 1 0 1 1 0 0 1 0 0 0 0 0 0 0 0 0 1 0 1 1 0 0 1 1 0 1 0 1 1 1 0 0 1 0 0 1 0 1 1 0 1 1 0 0 0 1 0 0 0 1 0 1 1 1 1
1 0 1 0 1 1 1 0 0 1 0 0 1 0 1 1 0 1 1 0 0 0 1 0 0 0 1 0 1 1 1 1 0 0 0 1 0 1 1 1 0 0 0 0 0 0 1 0 1 1 0 0 0 0 1 1 0 0 1 1 0 1 0 0
改变明文后各轮得到的密文bit
0 1 0 1 0 1 0 1 0 1 1 1 1 0 0 0 1 1 1 1 1 1 1 1 0 0 0 0 0 0 0 0 1 1 0 0 1 0 0 0 1 0 1 0 0 1 1 0 0 0 0 0 1 0 0 0 0 0 0 1 0 0 1 1
1 1 0 0 1 0 0 0 1 0 1 0 0 1 1 0 0 0 0 0 1 0 0 0 0 0 0 1 0 0 1 1 1 1 0 1 0 1 0 0 0 1 1 1 1 1 1 0 0 0 0 0 0 0 1 0 1 1 1 1 1 0 1 1
1 1 0 1 0 1 0 0 0 1 1 1 1 1 1 0 0 0 0 0 0 0 1 0 1 1 1 1 1 0 1 1 1 0 1 1 0 0 0 1 0 1 0 0 0 0 0 1 1 1 1 0 0 0 0 1 0 1 1 1 0 0 1 1
1 0 1 1 0 0 0 1 0 1 0 0 0 0 0 1 1 1 1 0 0 0 0 1 0 1 1 1 0 0 1 1 1 1 1 0 1 1 0 0 1 0 1 0 1 1 1 1 1 1 0 1 1 0 0 1 1 1 1 1 0 0 0 1
1 1 1 0 1 1 0 0 1 0 1 0 1 1 1 1 1 1 0 1 1 0 0 1 1 1 1 1 0 0 0 1 0 0 0 1 0 0 1 1 0 0 1 0 0 1 0 0 0 1 1 0 1 0 0 0 0 1 0 0 0 0 0 0
0 0 0 1 0 0 1 1 0 0 1 0 0 1 0 0 0 1 1 0 1 0 0 0 0 1 0 0 0 0 0 0 0 0 1 1 0 1 1 0 0 0 0 1 0 1 1 0 1 1 0 1 0 1 0 0 0 0 0 0 0 1 0 1
0 0 1 1 0 1 1 0 0 0 0 1 0 1 1 0 1 1 0 1 0 1 0 0 0 0 0 0 0 1 0 1 1 0 1 0 1 0 0 1 0 0 1 1 1 0 1 0 0 1 0 1 1 0 1 1 0 1 1 0 1 0 1 0
1 0 1 0 1 0 0 1 0 0 1 1 1 0 1 0 0 1 0 1 1 0 1 1 0 1 1 0 1 0 1 0 0 1 0 1 1 1 1 1 1 0 1 0 0 0 1 1 0 0 1 1 1 1 1 1 1 1 0 0 1 1 0 0
0 1 0 1 1 1 1 1 1 0 1 0 0 0 1 1 0 0 1 1 1 1 1 1 1 1 0 0 1 1 0 0 1 1 1 0 0 0 0 0 0 1 0 0 0 1 1 0 0 1 0 0 0 0 1 1 0 1 0 1 0 1 1 0
1 1 1 0 0 0 0 0 0 1 0 0 0 1 1 0 0 1 0 0 0 0 1 1 0 1 0 1 0 1 1 0 1 0 0 0 0 1 1 0 1 1 1 1 0 0 1 1 1 0 0 1 1 1 1 0 0 0 0 1 1 1 0 1
1 0 0 0 0 1 1 0 1 1 1 1 0 0 1 1 1 0 0 1 1 1 1 0 0 0 0 1 1 1 0 1 0 1 0 0 0 0 0 0 0 1 1 1 0 0 1 1 1 0 1 1 1 1 1 0 0 0 1 1 1 0 1 1
0 1 0 0 0 0 0 0 0 1 1 1 0 0 1 1 1 0 1 1 1 1 1 0 0 0 1 1 1 0 1 1 1 1 0 1 0 0 0 1 1 1 0 0 1 1 0 1 0 1 1 1 0 0 0 1 1 0 0 0 1 1 1 0
1 1 0 1 0 0 0 1 1 1 0 0 1 1 0 1 0 1 1 1 0 0 0 1 1 0 0 0 1 1 1 0 0 1 0 0 1 1 0 1 0 1 1 0 1 0 0 0 0 1 0 1 1 1 1 1 1 0 0 0 1 0 0 1
0 1 0 0 1 1 0 1 0 1 1 0 1 0 0 0 0 1 0 1 1 1 1 1 1 0 0 0 1 0 0 1 1 0 0 0 0 1 0 1 1 0 1 0 0 0 1 1 0 1 1 0 1 1 1 1 0 1 0 0 1 1 1 0
1 0 0 0 0 1 0 1 1 0 1 0 0 0 1 1 0 1 1 0 1 1 1 1 0 1 0 0 1 1 1 0 1 1 0 0 1 1 0 1 0 0 1 1 1 1 1 0 1 1 0 1 0 1 1 1 0 0 1 1 0 1 1 0
1 1 0 0 1 1 0 1 0 0 1 1 1 1 1 0 1 1 0 1 0 1 1 1 0 0 1 1 0 1 1 0 1 1 0 1 0 1 0 0 0 1 0 0 1 1 0 0 0 0 1 1 1 1 1 1 1 0 1 1 0 0 0 1
附录B
#ifndef _TABLES_H_
#define _TABLES_H_
const char IP_Table[64]={
58,50,42,34,26,18,10, 2,60,52,44,36,28,20,12, 4,
62,54,46,38,30,22,14, 6,64,56,48,40,32,24,16, 8,
57,49,41,33,25,17, 9, 1,59,51,43,35,27,19,11, 3,
61,53,45,37,29,21,13, 5,63,55,47,39,31,23,15, 7
};
const char IPR_Table[64]={
40, 8,48,16,56,24,64,32,39, 7,47,15,55,23,63,31,
38, 6,46,14,54,22,62,30,37, 5,45,13,53,21,61,29,
36, 4,44,12,52,20,60,28,35, 3,43,11,51,19,59,27,
34, 2,42,10,50,18,58,26,33, 1,41, 9,49,17,57,25
};
static char E_Table[48]={
32, 1, 2, 3, 4, 5, 4, 5, 6, 7, 8, 9,
8, 9,10,11,12,13,12,13,14,15,16,17,
16,17,18,19,20,21,20,21,22,23,24,25,
24,25,26,27,28,29,28,29,30,31,32, 1
};
static char S_Box[8][4][16]={
//S1
14, 4,13, 1, 2,15,11, 8, 3,10, 6,12, 5, 9, 0, 7,
0,15, 7, 4,14, 2,13, 1,10, 6,12,11, 9, 5, 3, 8,
4, 1,14, 8,13, 6, 2,11,15,12, 9, 7, 3,10, 5, 0,
15,12, 8, 2, 4, 9, 1, 7, 5,11, 3,14,10, 0, 6,13,
//S2
15, 1, 8,14, 6,11, 3, 4, 9, 7, 2,13,12, 0, 5,10,
3,13, 4, 7,15, 2, 8,14,12, 0, 1,10, 6, 9,11, 5,
0,14, 7,11,10, 4,13, 1, 5, 8,12, 6, 9, 3, 2,15,
13, 8,10, 1, 3,15, 4, 2,11, 6, 7,12, 0, 5,14, 9,
//S3
10, 0, 9,14, 6, 3,15, 5, 1,13,12, 7,11, 4, 2, 8,
13, 7, 0, 9, 3, 4, 6,10, 2, 8, 5,14,12,11,15, 1,
13, 6, 4, 9, 8,15, 3, 0,11, 1, 2,12, 5,10,14, 7,
1,10,13, 0, 6, 9, 8, 7, 4,15,14, 3,11, 5, 2,12,
//S4
7,13,14, 3, 0, 6, 9,10, 1, 2, 8, 5,11,12, 4,15,
13, 8,11, 5, 6,15, 0, 3, 4, 7, 2,12, 1,10,14, 9,
10, 6, 9, 0,12,11, 7,13,15, 1, 3,14, 5, 2, 8, 4,
3,15, 0, 6,10, 1,13, 8, 9, 4, 5,11,12, 7, 2,14,
//S5
2,12, 4, 1, 7,10,11, 6, 8, 5, 3,15,13, 0,14, 9,
14,11, 2,12, 4, 7,13, 1, 5, 0,15,10, 3, 9, 8, 6,
4, 2, 1,11,10,13, 7, 8,15, 9,12, 5, 6, 3, 0,14,
11, 8,12, 7, 1,14, 2,13, 6,15, 0, 9,10, 4, 5, 3,
//S6
12, 1,10,15, 9, 2, 6, 8, 0,13, 3, 4,14, 7, 5,11,
10,15, 4, 2, 7,12, 0, 5, 6, 1,13,14, 0,11, 3, 8,
9,14,15, 5, 2, 8,12, 3, 7, 0, 4,10, 1,13,11, 6,
4, 3, 2,12, 9, 5,15,10,11,14, 1, 7, 6, 0, 8,13,
//S7
4,11, 2,14,15, 0, 8,13, 3,12, 9, 7, 5,10, 6, 1,
13, 0,11, 7, 4, 0, 1,10,14, 3, 5,12, 2,15, 8, 6,
1, 4,11,13,12, 3, 7,14,10,15, 6, 8, 0, 5, 9, 2,
6,11,13, 8, 1, 4,10, 7, 9, 5, 0,15,14, 2, 3,12,
//S8
13, 2, 8, 4, 6,15,11, 1,10, 9, 3,14, 5, 0,12, 7,
1,15,13, 8,10, 3, 7, 4,12, 5, 6,11, 0,14, 9, 2,
7,11, 4, 1, 9,12,14, 2, 0, 6,10,13,15, 3, 5, 8,
2, 1,14, 7, 4,10, 8,13,15,12, 9, 0, 3, 5, 6,11
};
static char P_Table[32]={
16, 7,20,21,29,12,28,17, 1,15,23,26, 5,18,31,10,
2, 8,24,14,32,27, 3, 9,19,13,30, 6,22,11, 4,25
};
static bool SubKey[16][48]={0};
#endif
//
// main.cpp
// DES
//
// Created by tinoryj on 2017/3/26.
// Copyright © 2017年 tinoryj. All rights reserved.
//
#include <stdlib.h>
#include <stdio.h>
#include "tables.h"
#include <iostream>
using namespace std;
void BitsCopy(bool *DatOut,bool *DatIn,int Len); // 数组复制
void ByteToBit(bool *DatOut,char *DatIn,int Num); // 字节到位
void BitToByte(char *DatOut,bool *DatIn,int Num); // 位到字节
void BitToHex(char *DatOut,bool *DatIn,int Num); // 二进制到十六进制 64位 to 4*16字符
void HexToBit(bool *DatOut,char *DatIn,int Num); // 十六进制到二进制
void TablePermute(bool *DatOut,bool *DatIn,const char *Table,int Num); // 位表置换函数
void LoopMove(bool *DatIn,int Len,int Num); // 循环左移 Len长度 Num移动位数
void Xor(bool *DatA,bool *DatB,int Num); // 异或函数
void S_Change(bool DatOut[32],bool DatIn[48]); // S盒变换
void F_Change(bool DatIn[32],bool DatKi[48]); // F函数
void SetKey(char KeyIn[24]); // 设置密钥
void PlayDes(char MesOut[8],char MesIn[8]); // 执行DES加密
void KickDes(char MesOut[8],char MesIn[8]); // 执行DES解密
int main(){
char MesHex[16]; // 16个字符数组用于存放 64位16进制的密文
char MyKey[25]; // 初始密钥 8字节*8
char MyMessage[8]; // 初始明文
cout<<"Input Message:64bit:"<<endl;
cin>>MyMessage; // 明文
cout<<"Input Secret Key:192bit"<<endl;
cin>>MyKey; // 密钥
int len = 0;
while(MyKey[len]!=\'\\0\')
len++;
while(len!=24){
cout<<"Input Correct Secret Key!"<<endl;
cin>>MyKey;
len = 0;
while(MyKey[len]!=\'\\0\')
len++;
}
SetKey(MyKey); // 设置密钥 得到子密钥Ki
PlayDes(MesHex,MyMessage); // 执行DES加密
cout<<"Encrypting:"<<endl; // 信息已加密
for(int i = 0; i < 16; i++)
cout<<MesHex[i];
cout<<endl;
KickDes(MyMessage,MesHex); // 解密输出到MyMessage
cout<<"Deciphering:"<<endl;
for(int i = 0; i < 8; i++)
cout<<MyMessage[i];
cout<<endl;
}
//位移动
void BitsCopy(bool *DatOut,bool *DatIn,int Len){
for(int i = 0; i < Len; i++)
DatOut[i] = DatIn[i];
}
//字节转换成位
void ByteToBit(bool *DatOut,char *DatIn,int Num){
for(int i = 0; i < Num; i++)
DatOut[i] = (DatIn[i / 8] >> (i % 8)) & 0x01;
}
//位转换成字节
void BitToByte(char *DatOut,bool *DatIn,int Num){
for(int i = 0; i < (Num / 8); i++)
DatOut[i] = 0;
for(int i = 0; i < Num; i++)
DatOut[i / 8] |= DatIn[i] << (i % 8);
}
//二进制密文转换为十六进制
void BitToHex(char *DatOut,bool *DatIn,int Num){
for(int i = 0; i < Num / 4; i++)
DatOut[i] = 0;
for(int i = 0; i < Num / 4; i++){
DatOut[i] = DatIn[i * 4] + (DatIn[i * 4 + 1] << 1) + (DatIn[i * 4 + 2] << 2) + (DatIn[i * 4 + 3] << 3);
if((DatOut[i] % 16) > 9)
DatOut[i] = DatOut[i] % 16 + \'7\'; // 余数大于9时处理 10-15 to A-F
else
DatOut[i] = DatOut[i] % 16 + \'0\';
}
}
//十六进制字符转二进制
void HexToBit(bool *DatOut,char *DatIn,int Num){
for(int i = 0; i < Num; i++){
if((DatIn[i / 4]) > \'9\') // 大于9
DatOut[i] = ((DatIn[i / 4] - \'7\') >> (i % 4)) & 0x01;
else
DatOut[i] = ((DatIn[i / 4] - \'0\') >> (i % 4)) & 0x01;
}
}
//表置换函数
void TablePermute(bool *DatOut,bool *DatIn,const char *Table,int Num){
static bool Temp[256]={0};
for(int i = 0; i < Num; i++) // Num为置换的长度
Temp[i] = DatIn[Table[i] - 1]; // 原来的数据按对应的表上的位置排列
BitsCopy(DatOut,Temp,Num); // 把缓存Temp的值输出
}
// 子密钥的移位
void LoopMove(bool *DatIn,int Len,int Num){
static bool Temp[256]={0};
BitsCopy(Temp,DatIn,Num); // 将数据最左边的Num位(被移出去的)存入Temp
BitsCopy(DatIn,DatIn+Num,Len-Num); // 将数据左边开始的第Num移入原来的空间
BitsCopy(DatIn+Len-Num,Temp,Num); // 将缓存中移出去的数据加到最右边
}
// 按位异或
void Xor(bool *DatA,bool *DatB,int Num){
for(int i = 0; i < Num; i++)
DatA[i] = DatA[i] ^ DatB[i];
}
// S盒
void S_Change(bool DatOut[32],bool DatIn[48]){
for(int i = 0,Y = 0,X = 0; i < 8; i++,DatIn += 6,DatOut += 4){ // 每执行一次,输入数据偏移6位,输出数据偏移4位
Y = (DatIn[0] << 1) + DatIn[5]; //af代表第几行
X = (DatIn[1] << 3) + (DatIn[2] << 2) + (DatIn[3] << 1) + DatIn[4]; // bcde代表第几列
ByteToBit(DatOut,&S_Box[i][Y][X],4); // 把找到的点数据换为二进制
}
}
// F函数
void F_Change(bool DatIn[32],bool DatKi[48]){
bool MiR[48] = {0}; // 输入32位通过E选位变为48位
TablePermute(MiR,DatIn,E_Table,48);
Xor(MiR,DatKi,48); // 和子密钥异或
S_Change(DatIn,MiR); // S盒变换
TablePermute(DatIn,DatIn,P_Table,32); // P置换后输出
}
void SetKey(char KeyIn[8]){ // 设置密钥 获取子密钥Ki
static bool KeyBit[192]={0}; // 密钥二进制存储空间
static bool *KiL =&KeyBit[0],*KiR =&KeyBit[64],*KiB =&KeyBit[128];
ByteToBit(KeyBit,KeyIn,192); // 把密钥转为二进制存入KeyBit
for(int i = 0; i < 16; i++){
LoopMove(KiL,64,4);
LoopMove(KiR,64,4);
LoopMove(KiB,64,4);
bool temp[64] = {0};
for(int j = 0; j < 64; j++){
temp[j] = KeyBit[i] ^ KeyBit[i + 64];
temp[j] = temp[j] ^ KeyBit[i + 128];
}
bool tep[48] = {0};
for(int j = 0; j < 16; j++){
tep[j] = (temp[j]^temp[j+16])^(temp[j+32]^temp[j+48]);
tep[j+16] = tep[j];
tep[j+32] = tep[j];
}
for(int j = 0; j < 16; j++)
SubKey[i][j] = tep[j];
}
}
// 执行DES加密
void PlayDes(char MesOut[8],char MesIn[8]){
static bool MesBit[64]={0}; // 明文二进制存储空间 64位
static bool Temp[32]={0};
static bool *MiL=&MesBit[0],*MiR=&MesBit[32]; // 前32位 后32位
ByteToBit(MesBit,MesIn,64); // 把明文换成二进制存入MesBit
TablePermute(MesBit,MesBit,IP_Table,64); // IP置换
for(int i = 0; i < 16; i++){
BitsCopy(Temp,MiR,32); // 临时存储
F_Change(MiR,SubKey[i]); // F函数变换
Xor(MiR,MiL,32); // 得到Ri
BitsCopy(MiL,Temp,32); // 得到Li
}
TablePermute(MesBit,MesBit,IPR_Table,64);
BitToHex(MesOut,MesBit,64);
}
// 执行DES解密
void KickDes(char MesOut[8],char MesIn[8]){
static bool MesBit[64]={0}; // 密文二进制存储空间 64位
static bool Temp[32]={0};
static bool *MiL=&MesBit[0],*MiR=&MesBit[32]; // 前32位 后32位
HexToBit(MesBit,MesIn,64); // 把密文换成二进制存入MesBit
TablePermute(MesBit,MesBit,IP_Table,64); // IP置换
for(int i = 15; i >= 0; i--){
BitsCopy(Temp,MiL,32);
F_Change(MiL,SubKey[i]);
Xor(MiL,MiR,32);
BitsCopy(MiR,Temp,32);
}
TablePermute(MesBit,MesBit,IPR_Table,64);
BitToByte(MesOut,MesBit,64);
}
以上是关于DES的雪崩效应分析的主要内容,如果未能解决你的问题,请参考以下文章