LDAP架构部署认证
Posted
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了LDAP架构部署认证相关的知识,希望对你有一定的参考价值。
LDAP架构部署
LDAP
LDAP是轻量目录访问协议,英文全称是Lightweight Directory Access Protocol,一般都简称为LDAP。它是基于X.500标准的,但是简单多了并且可以根据需要定制。与X.500不同,LDAP支持TCP/IP,这对访问Internet是必须的。LDAP的核心规范在RFC中都有定义,所有与LDAP相关的RFC都可以在LDAPman RFC网页中找到
ldap环境安装
1-1检查系统环境
[[email protected] xuqizhang]# cat/etc/redhat-release
CentOS release 6.5 (Final)
[[email protected] xuqizhang]## uname -r
2.6.32-431.el6.x86_64
[[email protected] xuqizhang]## uname -m
x86_64
配置yum源,保留rpm原有的包
[[email protected] xuqizhang]# sed -i‘s#keepcache=0#keepcache=1#g‘ /etc/yum.conf
[[email protected] xuqizhang]# grep keepcache/etc/yum.conf
keepcache=1
关闭selinux防火墙以及防火墙
[[email protected] xuqizhang]# setenforce 0
[[email protected] xuqizhang]# getenforce
Permissive
[[email protected] xuqizhang]#/etc/init.d/iptables stop
时间同步
[[email protected] xuqizhang]# /usr/sbin/ntpdatetime.windows.com
[[email protected] xuqizhang]# crontab -e
#time sync
*/5 * * * */usr/sbin/ntpdate time.windows.com>/dev/null 2>&1
设定ldap域名并配置host
[[email protected] xuqizhang]# echo"10.1.11.149 baobaotang.org" >>/etc/hosts
[[email protected] xuqizhang]# tail -1 /etc/hosts
10.1.11.149 baobaotang.org
[[email protected] xuqizhang]# pingbaobaotang.org
PING baobaotang.org (10.1.11.149) 56(84)bytes of data.
64 bytes from baobaotang.org (10.1.11.149):icmp_seq=1 ttl=64 time=7.37 ms
64 bytes from baobaotang.org (10.1.11.149):icmp_seq=2 ttl=64 time=0.031 ms
开始安装ldap master
openldap依赖的软件很多,我们一般功能性软件都用yum安装,定制的软件用源码安装
安装前:检查
[[email protected] xuqizhang]# rpm -qa openldap
openldap-2.4.40-12.el6.x86_64
[[email protected] xuqizhang]# rpm -qa |grepopenldap
openldap-2.4.40-12.el6.x86_64
openldap-devel-2.4.40-12.el6.x86_64
安装
[[email protected] xuqizhang]# yum -y installopenldap openldap-* -y
[[email protected] xuqizhang]# yum -y installnscd nss-pam-ldap nss-* pcre pcre-*
安装好检查一下,出现以下包就ok
[[email protected] xuqizhang]# rpm -qa |grepopenldap
openldap-clients-2.4.40-12.el6.x86_64
openldap-servers-2.4.40-12.el6.x86_64
openldap-servers-sql-2.4.40-12.el6.x86_64
openldap-2.4.40-12.el6.x86_64
openldap-devel-2.4.40-12.el6.x86_64
小提示:如果以上安装出现报错,建议依赖包分开yum安装
配置ldap master
[[email protected] xuqizhang]# cd /etc/openldap/
[[email protected] openldap]# ll
total 20
drwxr-xr-x. 2 root root 4096 Mar 9 16:47 certs
-rw-r----- 1 root ldap 121 May 11 2016 check_password.conf
-rw-r--r-- 1 root root 280 May 11 2016 ldap.conf
drwxr-xr-x 2 root root 4096 Mar 30 10:31 schema
drwx------ 3 ldap ldap 4096 Mar 30 10:31 slapd.d
centos5和centos6 ldap配置文件有变化,6的配置文件在slapd.d目录下,5的就是当前目录下的slapd.conf
[[email protected] openldap]# cp/usr/share/openldap-servers/slapd.conf.obsolete slapd.conf #拷贝模板在当前目录下
[[email protected]]# slappasswd -s admin #生成密码,管理员创建的密码
{SSHA}ZZ7RPi0ih/cr00LurQoTfse1826YbQGj
[[email protected] openldap]# slappasswd -s admin|sed -e "s#{SSHA}#rootpw\t{SSHA}#g" >>slapd.conf #这个文件追加到slapd.conf下
[[email protected] openldap]# tail -1 slapd.conf
rootpw {SSHA}XKdLuM/nmj43cQATC42z/CY8YTBClBHB
[[email protected] openldap]# cp slapd.confslapd.conf.ori
[[email protected] openldap]#vim slapd.conf
database bdb #默认就好,是指定使用的数据库
suffix "dc=baobaotang,dc=org" #修改自己的域名
#checkpoint 1024 15 #注释
rootdn "cn=admin,dc=baobaotang,dc=org" #管理员的rootdn,唯一标示
Ldap管理员:admin 密码:admin
ldap参数优化及日志、缓存参数
##日志参数,cat用法
[[email protected] openldap]# cat >>/etc/openldap/slapd.conf<<EOF
> #add start by xqz 2017/3/30
> loglevel 296 #日志级别
> cachesize 1000 #缓存记录数
> checkpoint 2048 10 #文件达到2048,每10分钟做一次回写
> #add end by xqz 2018/3/30
> EOF
权限控制
删除如下:
vim slapd.conf
98 database config #这是写法是2.4的写法,不用删除加新的写法,2.4的配置,兼容2.3
99 access to *
100 bydn.exact="gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn= auth" manage
101 by * none
102
103 # enable server status monitoring (cn=monitor)
104 database monitor
105 access to *
106 bydn.exact="gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn= auth" read
107 bydn.exact="cn=Manager,dc=my-domain,dc=com" read
108 by * none
添加如下内容 不加也可以~~~
96 access to *
97 by self write
98 by users read
99 by anonymous auth
1-2配置rssyslog记录ldap服务日志
[[email protected] openldap]# cp/etc/rsyslog.conf /etc/rsyslog.conf.ori.$(date +%F%T)
[[email protected] openldap]# echo ‘#recordldap.log by xqz 2017-03-30‘ >> /etc/rsyslog.conf
[[email protected] openldap]# echo ‘local4.* /var/log/ldap.log‘>> /etc/rsyslog.conf
[[email protected] openldap]# tail -1/etc/rsyslog.conf
local4.* /var/log/ldap.log
[[email protected] openldap]# /etc/init.d/rsyslogrestart
1-3 配置ldap数据库路径,提示:6.4以下的版本可能路径会发生变化
[[email protected] openldap]# ll/var/lib/ldap/ #数据库路径
total 0
[[email protected] openldap]# cp/usr/share/openldap-servers/DB_CONFIG.example /var/lib/ldap/DB_CONFIG
[[email protected] openldap]#ll /var/lib/ldap/ #数据库已经拷贝过来了
total 4
-rw-r--r-- 1 root root845 Mar 30 12:13 DB_CONFIG
授权访问,默认是root
[[email protected] openldap]# chown ldap:ldap/var/lib/ldap/DB_CONFIG
[[email protected] openldap]# chmod 700/var/lib/ldap/
[[email protected] openldap]# ls -l/var/lib/ldap/
total 4
-rw-r--r-- 1 ldap ldap 845 Mar 30 12:13DB_CONFIG
过滤查看一下数据库里面的文件
[[email protected] openldap]# grep -Ev"#|^$" /var/lib/ldap/DB_CONFIG
set_cachesize 0 268435456 1
set_lg_regionmax 262144
set_lg_bsize 2097152
[[email protected] openldap]# slaptest -u #执行这个命令证明数据库配置成功
config file testing succeeded
1-4 启动ldap-master服务
系统5.8启动方式是/etc/init.d/ldap start 6.4以上系统启动就变了,如下就是6.5的启动方式
[[email protected] openldap]# /etc/init.d/slapdstart
Starting slapd: [ OK ]
[[email protected] openldap]# lsof -i :389
COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME
slapd 24258 ldap 7u IPv4 115368 0t0 TCP *:ldap (LISTEN)
slapd 24258 ldap 8u IPv6 115369 0t0 TCP *:ldap (LISTEN)
[[email protected] openldap]# ps -ef|grep ldap
ldap 24258 1 0 12:32 ? 00:00:01 /usr/sbin/slapd -h ldap:/// ldapi:/// -u ldap
root 24274 23605 0 12:38 pts/1 00:00:00 grep ldap
开机自启动,也可以放在rc.local下
[[email protected] openldap]# chkconfig slapd on
[[email protected] openldap]# chkconfig --listslapd
slapd 0:off 1:off 2:on 3:on 4:on 5:on 6:off
查看启动日志
[[email protected] openldap]# tail/var/log/ldap.log #如果没有日志说明你的rsyslog服务器没配好
Mar 30 12:32:57 vm0021 slapd[24257]: @(#)$OpenLDAP: slapd 2.4.40
(May 10 2016 23:30:49)$#012#[email protected]:
/builddir/build/BUILD/openldap-2.4.40/openldap-2.4.40/build-servers/servers/slapd
命令的用法
[[email protected] openldap]# ldap #命令的用法
ldapadd ldapdelete ldapmodify ldappasswd ldapurl
ldapcompare ldapexop ldapmodrdn ldapsearch ldapwhoami
[[email protected] openldap]# ldapsearch -LLL -W-x -H ldap://baobaotang.org -D "cn=admin,dc=baobaotang,dc=org" -b"dc=baobaotang,dc=org" "(uid=*)"
Enter LDAP Password: #输入密码
ldap_bind: Invalid credentials (49) #有问题,版本导致的
解决方法:
[[email protected] openldap]# rm -rf/etc/openldap/slapd.d/* #删除默认2.4的配置文件
[[email protected] openldap]# slaptest -f/etc/openldap/slapd.conf -F /etc/openldap/slapd.d/ #重新生成slapd.d
58dca609 bdb_monitor_db_open: monitoringdisabled; configure monitor database to enable
config file testing succeeded
[[email protected] openldap]# /etc/init.d/slapdrestart
Stopping slapd: [ OK ]
Checking configuration files forslapd: [FAILED]
58dca645 ldif_read_file: Permission deniedfor "/etc/openldap/slapd.d/cn=config.ldif" #启动报错,权限问题
slaptest: bad configuration file!
[[email protected] openldap]# chown -R ldap.ldap/etc/openldap/slapd.d/ #给权限
[[email protected] openldap]# /etc/init.d/slapdrestart
Stopping slapd: [FAILED]
Starting slapd: [ OK ]
[[email protected] openldap]# ldapsearch -LLL -W-x -H ldap://baobaotang.org -D "cn=admin,dc=baobaotang,dc=org" -b"dc=baobaotang,dc=org" "(uid=*)"
Enter LDAP Password:
No such object (32) #重新查询,出现这个就证明好了
到此问题解决
1-5 为ldap master数据库添加数据的方法
根据系统用户及ldap自带的脚本初始化数据
添加测试用户test,配置用户登录环境
[[email protected] openldap]# groupadd -g 5000test
[[email protected] openldap]# useradd -u 5001 -g5000 test
创建根项,并使用openLDAP-servers自带脚本生成和导入pass/group配置
[[email protected] openldap]# grep test /etc/passwd> passwd.in
[[email protected] openldap]# grep test/etc/group > group.in
[[email protected] openldap]# yum installmigrationtools -y
[[email protected] openldap]#/usr/share/migrationtools/migrate_base.pl > base.ldif
[[email protected] openldap]# vi /usr/share/migrationtools/migrate_common.ph #修改71行和74行,修改结果如下
# Default DNS domain
$DEFAULT_MAIL_DOMAIN ="baobaotang.org";
# Default base
$DEFAULT_BASE ="dc=baobaotang,dc=org";
生成ldap数据,引用脚本导入数据
操作命令:
[[email protected] openldap]# export LC_ALL=C
[[email protected] openldap]#/usr/share/migrationtools/migrate_base.pl >base.ldif
[[email protected] openldap]#/usr/share/migrationtools/migrate_base.pl passwd.in passwd.ldif
dn: dc=baobaotang,dc=org
dc: baobaotang
objectClass: top
objectClass: domain
dn: ou=Hosts,dc=baobaotang,dc=org
ou: Hosts
objectClass: top
objectClass: organizationalUnit
dn: ou=Rpc,dc=baobaotang,dc=org
ou: Rpc
objectClass: top
objectClass: organizationalUnit
dn: ou=Services,dc=baobaotang,dc=org
ou: Services
objectClass: top
objectClass: organizationalUnit
dn:nisMapName=netgroup.byuser,dc=baobaotang,dc=org
nismapname: netgroup.byuser
objectClass: top
objectClass: nisMap
dn: ou=Mounts,dc=baobaotang,dc=org
ou: Mounts
objectClass: top
objectClass: organizationalUnit
dn: ou=Networks,dc=baobaotang,dc=org
ou: Networks
objectClass: top
objectClass: organizationalUnit
dn: ou=People,dc=baobaotang,dc=org
ou: People
objectClass: top
objectClass: organizationalUnit
dn: ou=Group,dc=baobaotang,dc=org
ou: Group
objectClass: top
objectClass: organizationalUnit
dn: ou=Netgroup,dc=baobaotang,dc=org
ou: Netgroup
objectClass: top
objectClass: organizationalUnit
dn: ou=Protocols,dc=baobaotang,dc=org
ou: Protocols
objectClass: top
objectClass: organizationalUnit
dn: ou=Aliases,dc=baobaotang,dc=org
ou: Aliases
objectClass: top
objectClass: organizationalUnit
dn:nisMapName=netgroup.byhost,dc=baobaotang,dc=org
nismapname: netgroup.byhost
objectClass: top
objectClass: nisMap
[[email protected] openldap]# ll group.inpasswd.*
-rw-r--r--. 1 root root 13 Mar 31 00:55group.in
-rw-r--r--. 1 root root 39 Mar 31 00:55passwd.in
[[email protected] openldap]#/usr/share/migrationtools/migrate_base.pl group.in group.ldif
dn: dc=baobaotang,dc=org
dc: baobaotang
objectClass: top
objectClass: domain
dn: ou=Hosts,dc=baobaotang,dc=org
ou: Hosts
objectClass: top
objectClass: organizationalUnit
dn: ou=Rpc,dc=baobaotang,dc=org
ou: Rpc
objectClass: top
objectClass: organizationalUnit
dn: ou=Services,dc=baobaotang,dc=org
ou: Services
objectClass: top
objectClass: organizationalUnit
dn:nisMapName=netgroup.byuser,dc=baobaotang,dc=org
nismapname: netgroup.byuser
objectClass: top
objectClass: nisMap
dn: ou=Mounts,dc=baobaotang,dc=org
ou: Mounts
objectClass: top
objectClass: organizationalUnit
dn: ou=Networks,dc=baobaotang,dc=org
ou: Networks
objectClass: top
objectClass: organizationalUnit
dn: ou=People,dc=baobaotang,dc=org
ou: People
objectClass: top
objectClass: organizationalUnit
dn: ou=Group,dc=baobaotang,dc=org
ou: Group
objectClass: top
objectClass: organizationalUnit
dn: ou=Netgroup,dc=baobaotang,dc=org
ou: Netgroup
objectClass: top
objectClass: organizationalUnit
dn: ou=Protocols,dc=baobaotang,dc=org
ou: Protocols
objectClass: top
objectClass: organizationalUnit
dn: ou=Aliases,dc=baobaotang,dc=org
ou: Aliases
objectClass: top
objectClass: organizationalUnit
dn:nisMapName=netgroup.byhost,dc=baobaotang,dc=org
nismapname: netgroup.byhost
objectClass: top
objectClass: nisMap
[[email protected] openldap]# ll -al *.ldif
-rw-r--r--. 1 root root 1284 Mar 31 01:09base.ldif
利用ldapadd 导入模板文件中的内容。
导入用户LDIF 文件至OpenLDAP 目录树中,生成用户
[[email protected] openldap]# ldapadd -w admin -x-H ldap://127.0.0.1 -D "cn=admin,dc=baobaotang,dc=org" -f base.ldif
adding new entry"dc=baobaotang,dc=org"
adding new entry "ou=Hosts,dc=baobaotang,dc=org"
adding new entry"ou=Rpc,dc=baobaotang,dc=org"
adding new entry"ou=Services,dc=baobaotang,dc=org"
adding new entry"nisMapName=netgroup.byuser,dc=baobaotang,dc=org"
adding new entry"ou=Mounts,dc=baobaotang,dc=org"
adding new entry "ou=Networks,dc=baobaotang,dc=org"
adding new entry"ou=People,dc=baobaotang,dc=org"
adding new entry"ou=Group,dc=baobaotang,dc=org"
adding new entry"ou=Netgroup,dc=baobaotang,dc=org"
adding new entry"ou=Protocols,dc=baobaotang,dc=org"
adding new entry"ou=Aliases,dc=baobaotang,dc=org"
adding new entry"nisMapName=netgroup.byhost,dc=baobaotang,dc=org"
[[email protected] openldap]# ldapadd -x -W -D"cn=Manager,dc=gdy,dc=com" -f group.ldif
group.ldif: No such file or directory
[[email protected] openldap]#
[[email protected] openldap]# tail -n 10/etc/group > group
[[email protected] openldap]# cat group
stapusr:x:156:
stapsys:x:157:
stapdev:x:158:
sshd:x:74:
tcpdump:x:72:
slocate:x:21:
smart:x:500:
ldap:x:55:
nscd:x:28:
test:x:5000:
[[email protected] openldap]# /usr/share/migrationtools/migrate_group.plgroup group.ldif
[[email protected] openldap]# head -n 20group.ldif
dn:cn=stapusr,ou=Group,dc=baobaotang,dc=org
objectClass: posixGroup
objectClass: top
cn: stapusr
userPassword: {crypt}x
gidNumber: 156
dn: cn=stapsys,ou=Group,dc=baobaotang,dc=org
objectClass: posixGroup
objectClass: top
cn: stapsys
userPassword: {crypt}x
gidNumber: 157
dn:cn=stapdev,ou=Group,dc=baobaotang,dc=org
objectClass: posixGroup
objectClass: top
cn: stapdev
userPassword: {crypt}x
gidNumber: 158
[[email protected] openldap]# ldapadd -x -W -D"cn=Manager,dc=gdy,dc=com" -f group.ldif
Enter LDAP Password:
ldap_bind: Invalid credentials (49)
[[email protected] openldap]# ldapadd -x -W -D"cn=admin,dc=baobaotang,dc=org" -f group.ldif
Enter LDAP Password:
adding new entry"cn=stapusr,ou=Group,dc=baobaotang,dc=org"
adding new entry"cn=stapsys,ou=Group,dc=baobaotang,dc=org"
adding new entry"cn=stapdev,ou=Group,dc=baobaotang,dc=org"
adding new entry"cn=sshd,ou=Group,dc=baobaotang,dc=org"
adding new entry"cn=tcpdump,ou=Group,dc=baobaotang,dc=org"
adding new entry"cn=slocate,ou=Group,dc=baobaotang,dc=org"
adding new entry"cn=smart,ou=Group,dc=baobaotang,dc=org"
adding new entry"cn=ldap,ou=Group,dc=baobaotang,dc=org"
adding new entry "cn=nscd,ou=Group,dc=baobaotang,dc=org"
adding new entry"cn=test,ou=Group,dc=baobaotang,dc=org"
[[email protected] openldap]# ldapadd -x -W -D"cn=admin,dc=baobaotang,dc=org" -f passwd.ldif
passwd.ldif: No such file or directory
[[email protected] openldap]# tail -n 10 /etc/passwd> passwd
[[email protected] openldap]#/usr/share/migrationtools/migrate_group.pl passwd passwd.ldif
[[email protected] openldap]# ldapadd -x -W -D"cn=admin,dc=baobaotang,dc=org" -f passwd.ldif
Enter LDAP Password:
adding new entry"cn=saslauth,ou=Group,dc=baobaotang,dc=org"
adding new entry"cn=postfix,ou=Group,dc=baobaotang,dc=org"
adding new entry"cn=pulse,ou=Group,dc=baobaotang,dc=org"
adding new entry"cn=sshd,ou=Group,dc=baobaotang,dc=org"
ldap_add: Already exists (68) #已存在,先不管
[[email protected] openldap]# ll -al *.ldif
-rw-r--r--. 1 root root 1284 Mar 31 01:09base.ldif
-rw-r--r--. 1 root root 1338 Mar 31 01:42group.ldif
-rw-r--r--. 1 root root 1475 Mar 31 01:48passwd.ldif
分别cat查看一下
[[email protected] openldap]# cat passwd.ldif
dn: cn=saslauth,ou=Group,dc=baobaotang,dc=org
objectClass: posixGroup
objectClass: top
cn: saslauth
userPassword: {crypt}x
gidNumber: 498
memberUid: 76
dn:cn=postfix,ou=Group,dc=baobaotang,dc=org
objectClass: posixGroup
objectClass: top
cn: postfix
userPassword: {crypt}x
gidNumber: 89
memberUid: 89
dn: cn=pulse,ou=Group,dc=baobaotang,dc=org
objectClass: posixGroup
objectClass: top
cn: pulse
userPassword: {crypt}x
gidNumber: 497
memberUid: 496
dn: cn=sshd,ou=Group,dc=baobaotang,dc=org
objectClass: posixGroup
objectClass: top
cn: sshd
userPassword: {crypt}x
gidNumber: 74
memberUid: 74
dn:cn=tcpdump,ou=Group,dc=baobaotang,dc=org
objectClass: posixGroup
objectClass: top
cn: tcpdump
userPassword: {crypt}x
gidNumber: 72
memberUid: 72
dn: cn=smart,ou=Group,dc=baobaotang,dc=org
objectClass: posixGroup
objectClass: top
cn: smart
userPassword: {crypt}x
gidNumber: 500
memberUid: 500
dn: cn=ldap,ou=Group,dc=baobaotang,dc=org
objectClass: posixGroup
objectClass: top
cn: ldap
userPassword: {crypt}x
gidNumber: 55
memberUid: 55
dn: cn=nscd,ou=Group,dc=baobaotang,dc=org
objectClass: posixGroup
objectClass: top
cn: nscd
userPassword: {crypt}x
gidNumber: 28
memberUid: 28
dn: cn=nslcd,ou=Group,dc=baobaotang,dc=org
objectClass: posixGroup
objectClass: top
cn: nslcd
userPassword: {crypt}x
gidNumber: 65
memberUid: 55
dn: cn=test,ou=Group,dc=baobaotang,dc=org
objectClass: posixGroup
objectClass: top
cn: test
userPassword: {crypt}x
gidNumber: 5001
memberUid: 5000
以上就是导入到ldap数据库的操作
备份ldap数据
[[email protected] openldap]# ldapsearch -LLL -wadmin -x -H ldap://baobaotang.org -D "cn=admin,dc=baobaotang,dc=org"-b "dc=baobaotang,dc=org" >bak-ldap.ldif
[[email protected] openldap]# cat bak-ldap.ldif
dn: dc=baobaotang,dc=org
dc: baobaotang
objectClass: top
objectClass: domain
dn: ou=Hosts,dc=baobaotang,dc=org
ou: Hosts
objectClass: top
objectClass: organizationalUnit
dn: ou=Rpc,dc=baobaotang,dc=org
ou: Rpc
objectClass: top
objectClass: organizationalUnit
dn: ou=Services,dc=baobaotang,dc=org
ou: Services
objectClass: top
objectClass: organizationalUnit
dn:nisMapName=netgroup.byuser,dc=baobaotang,dc=org
nisMapName: netgroup.byuser
objectClass: top
objectClass: nisMap
dn: ou=Mounts,dc=baobaotang,dc=org
ou: Mounts
objectClass: top
objectClass: organizationalUnit
dn: ou=Networks,dc=baobaotang,dc=org
ou: Networks
objectClass: top
objectClass: organizationalUnit
dn: ou=People,dc=baobaotang,dc=org
ou: People
objectClass: top
objectClass: organizationalUnit
dn: ou=Group,dc=baobaotang,dc=org
ou: Group
objectClass: top
objectClass: organizationalUnit
dn: ou=Netgroup,dc=baobaotang,dc=org
ou: Netgroup
objectClass: top
objectClass: organizationalUnit
dn: ou=Protocols,dc=baobaotang,dc=org
ou: Protocols
objectClass: top
objectClass: organizationalUnit
dn: ou=Aliases,dc=baobaotang,dc=org
ou: Aliases
objectClass: top
objectClass: organizationalUnit
dn:nisMapName=netgroup.byhost,dc=baobaotang,dc=org
nisMapName: netgroup.byhost
objectClass: top
objectClass: nisMap
dn:cn=stapusr,ou=Group,dc=baobaotang,dc=org
objectClass: posixGroup
objectClass: top
cn: stapusr
userPassword:: e2NyeXB0fXg=
gidNumber: 156
dn:cn=stapsys,ou=Group,dc=baobaotang,dc=org
objectClass: posixGroup
objectClass: top
cn: stapsys
userPassword:: e2NyeXB0fXg=
gidNumber: 157
dn: cn=stapdev,ou=Group,dc=baobaotang,dc=org
objectClass: posixGroup
objectClass: top
cn: stapdev
userPassword:: e2NyeXB0fXg=
gidNumber: 158
dn: cn=sshd,ou=Group,dc=baobaotang,dc=org
objectClass: posixGroup
objectClass: top
cn: sshd
userPassword:: e2NyeXB0fXg=
gidNumber: 74
dn: cn=tcpdump,ou=Group,dc=baobaotang,dc=org
objectClass: posixGroup
objectClass: top
cn: tcpdump
userPassword:: e2NyeXB0fXg=
gidNumber: 72
dn:cn=slocate,ou=Group,dc=baobaotang,dc=org
objectClass: posixGroup
objectClass: top
cn: slocate
userPassword:: e2NyeXB0fXg=
gidNumber: 21
dn: cn=smart,ou=Group,dc=baobaotang,dc=org
objectClass: posixGroup
objectClass: top
cn: smart
userPassword:: e2NyeXB0fXg=
gidNumber: 500
dn: cn=ldap,ou=Group,dc=baobaotang,dc=org
objectClass: posixGroup
objectClass: top
cn: ldap
userPassword:: e2NyeXB0fXg=
gidNumber: 55
dn: cn=nscd,ou=Group,dc=baobaotang,dc=org
objectClass: posixGroup
objectClass: top
cn: nscd
userPassword:: e2NyeXB0fXg=
gidNumber: 28
dn: cn=test,ou=Group,dc=baobaotang,dc=org
objectClass: posixGroup
objectClass: top
cn: test
userPassword:: e2NyeXB0fXg=
gidNumber: 5000
dn:cn=saslauth,ou=Group,dc=baobaotang,dc=org
objectClass: posixGroup
objectClass: top
cn: saslauth
userPassword:: e2NyeXB0fXg=
gidNumber: 498
memberUid: 76
dn: cn=postfix,ou=Group,dc=baobaotang,dc=org
objectClass: posixGroup
objectClass: top
cn: postfix
userPassword:: e2NyeXB0fXg=
gidNumber: 89
memberUid: 89
dn: cn=pulse,ou=Group,dc=baobaotang,dc=org
objectClass: posixGroup
objectClass: top
cn: pulse
userPassword:: e2NyeXB0fXg=
gidNumber: 497
memberUid: 496
ldap master配置web管理接口
ldap的客户端管理接口有很多,有b/s结构、web的、也有C/S结构的,我们以b/s为例讲解,ldap-account-manager-3.7.tar.gz讲解
这个软件需要安装lamp服务环境
[[email protected] openldap]# yum install httpdphp php-ldap php-gd -y
[[email protected] openldap]# rpm -qa httpd phpphp-ldap php-gd
php-gd-5.3.3-48.el6_8.x86_64
httpd-2.2.15-56.el6.centos.3.x86_64
php-ldap-5.3.3-48.el6_8.x86_64
php-5.3.3-48.el6_8.x86_64
https://www.ldap-account-manager.org/lamcms/ 官网下载ldap-account-manager-3.7.tar.gz
[[email protected] openldap]# cd /var/www/html/
wgethttp://prdownloads.sourceforge.net/lam/ldap-account-manager-3.7.tar.gz
[[email protected] html]# ll
总用量 8944
-rw-r--r--. 1 root root 9157357 3月 31 10:47 ldap-account-manager-3.7.tar.gz
[[email protected] html]# tar -xfldap-account-manager-3.7.tar.gz
[[email protected] html]# cdldap-account-manager-3.7
[[email protected] ldap-account-manager-3.7]# cdconfig
[[email protected] config]# cp config.cfg_sampleconfig.cfg_sample.bak
[[email protected] config]# cp lam.conf_samplelam.conf_sample.bak
[[email protected] config]# sed -i‘s#cn=Manager#cn=admin#g‘ lam.conf_sample
[[email protected] config]# sed -i‘s#dc=my-domain#dc=baobaotang#g‘ lam.conf_sample
[[email protected] config]# sed -i‘s#dc=com#dc=org#g‘ lam.conf_sample
[[email protected] config]# diff lam.conf_samplelam.conf_sample.bak
13c13
< admins: cn=admin,dc=baobaotang,dc=org
---
> admins: cn=Manager,dc=my-domain,dc=com
55c55
< types: suffix_user:ou=People,dc=baobaotang,dc=org
---
> types: suffix_user:ou=People,dc=my-domain,dc=com
59c59
< types: suffix_group:ou=group,dc=baobaotang,dc=org
---
> types: suffix_group:ou=group,dc=my-domain,dc=com
63c63
< types: suffix_host:ou=machines,dc=baobaotang,dc=org
---
> types: suffix_host:ou=machines,dc=my-domain,dc=com
67c67
< types: suffix_smbDomain:dc=baobaotang,dc=org
---
> types: suffix_smbDomain: dc=my-domain,dc=com
[[email protected] html]# mvldap-account-manager-3.7 ldap
[[email protected] config]# chown -Rapache.apache /var/www/html/ldap
[[email protected] config]# /etc/init.d/httpdrestart
正在启动 httpd:httpd: apr_sockaddr_info_get() failed for vm0021
httpd: Could not reliably determine theserver‘s fully qualified domain name, using 127.0.0.1 for ServerName
[确定]
[[email protected] config]# lsof -i :80
COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME
httpd 2567 root 4u IPv6 21230 0t0 TCP *:http (LISTEN)
httpd 2572 apache 4u IPv6 21230 0t0 TCP *:http (LISTEN)
httpd 2573 apache 4u IPv6 21230 0t0 TCP *:http (LISTEN)
httpd 2574 apache 4u IPv6 21230 0t0 TCP *:http (LISTEN)
httpd 2575 apache 4u IPv6 21230 0t0 TCP *:http (LISTEN)
httpd 2576 apache 4u IPv6 21230 0t0 TCP *:http (LISTEN)
httpd 2577 apache 4u IPv6 21230 0t0 TCP *:http (LISTEN)
httpd 2578 apache 4u IPv6 21230 0t0 TCP *:http (LISTEN)
httpd 2579 apache 4u IPv6 21230 0t0 TCP *:http (LISTEN)
登录客户端访问http://10.1.11.149/ldap/即可,具体用法自己研究~~~ 当然还有别的工具
配置网络服务通过ldap服务进行身份验证
安装配置svn服务(非Apachesvn)
启用svn服务器的SASL验证机制 [独立的验证机制]
检查一下
[[email protected] html]# rpm -qa|grep sasl
cyrus-sasl-lib-2.1.23-15.el6_6.2.x86_64
cyrus-sasl-2.1.23-15.el6_6.2.x86_64
cyrus-sasl-gssapi-2.1.23-15.el6_6.2.x86_64
cyrus-sasl-md5-2.1.23-15.el6_6.2.x86_64
cyrus-sasl-plain-2.1.23-15.el6_6.2.x86_64
cyrus-sasl-devel-2.1.23-15.el6_6.2.x86_64
yum安装相关的软件包,安装完成检查会有一推的包
[[email protected] html]# yum install *sasl* -y
[[email protected] openldap]# saslauthd -v #通过这个命令查看验证机制列表
saslauthd 2.1.23
authentication mechanisms: getpwentkerberos5 pam rimap shadow ldap
[[email protected] openldap]# grep -i mech/etc/sysconfig/saslauthd #-i是忽略大小写,MECH=pam是调整验证机制的
# Mechanism to use when checkingpasswords. Run "saslauthd -v"to get a list
# of which mechanism your installation wascompiled with the ablity to use.
MECH=pam
# Options sent to the saslauthd. If theMECH is other than "pam" uncomment the next line.
[[email protected] openldap]# sed -i‘s#MECH=pam#MECH=shadow#g‘ /etc/sysconfig/saslauthd #sed 替换为shadow
# Options sent to the saslauthd. If theMECH is other than "pam" uncomment the next line.
[[email protected] openldap]#/etc/init.d/saslauthd restart
Stopping saslauthd: [FAILED]
Starting saslauthd: [ OK ]
[[email protected] openldap]# ps -ef|grep sasl
root 29453 1 0 14:35 ? 00:00:00 /usr/sbin/saslauthd -m/var/run/saslauthd -a shadow
root 29454 29453 0 14:35 ? 00:00:00 /usr/sbin/saslauthd -m/var/run/saslauthd -a shadow
root 29455 29453 0 14:35 ? 00:00:00 /usr/sbin/saslauthd -m/var/run/saslauthd -a shadow
root 29456 29453 0 14:35 ? 00:00:00 /usr/sbin/saslauthd -m/var/run/saslauthd -a shadow
root 29458 29453 0 14:35 ? 00:00:00 /usr/sbin/saslauthd -m/var/run/saslauthd -a shadow
root 29460 28899 0 14:35 pts/1 00:00:00 grep sasl
命令测试saslauthd进程的认证功能
admin为linux系统用户,admin为用户的密码,执行后出现OK "Success,则表示认证功能已起作用
[[email protected] openldap]# testsaslauthd-uadmin -padmin #验证失败
0: NO "authentication failed"
[[email protected] openldap]# grep admin /etc/passwd #没有这个用户名
[[email protected] openldap]# id admin
id: admin: No such user
[[email protected] openldap]# useradd admin #创建一个本地系统用户
[[email protected] openldap]# passwd admin #给一个密码,这里密码不显示,我给的密码是admin
Changing password for user admin.
New password:
BAD PASSWORD: it is too short
BAD PASSWORD: is too simple
Retype new password:
passwd: all authentication tokens updatedsuccessfully.
再次验证,成功
[[email protected] openldap]# testsaslauthd-uadmin -padmin #
0: OK "Success."
通过ldap进行验证
man saslauthd配置文件,会看到这个文件是存在的,隐藏了,但是可以vi编辑这个文件
[[email protected] openldap]# ll/etc/saslauthd.conf
ls: cannot access /etc/saslauthd.conf: Nosuch file or directory
[[email protected] config]# sed -i‘s#MECH=shadow#MECH=ldap#g‘ /etc/sysconfig/saslauthd #改成ldap验证机制
[[email protected] config]# /etc/init.d/saslauthdrestart
Stopping saslauthd: [ OK ]
Starting saslauthd: [ OK ]
#再次验证,失败,接下来怎么办呢,vi编辑这个文件/etc/saslauthd.conf,默认是不存在的
[[email protected] config]# testsaslauthd -uadmin-padmin
0: NO "authentication failed"
这里按理说是成功的。。。。
[[email protected] openldap]#
[[email protected] config]# cat/etc/saslauthd.conf
ldap_servers:ldap://baobaotang.org/
ldap_bind_dn: cn=admin,dc=baobaotang,dc=org
ldap_bind_pw: admin
ldap_search_base: ou=People,dc=baobaotang,dc=org
ldap_filter: uid=%U
ldap_password_atter:userPassword
因为在这之前没有创建ldap用户,用user1测试时不成功的,因为用户不存在
下面我来创建ldap的用户,操作如下:
[[email protected] openldap]# vim adduser.sh
#!/bin/bash
# Add system user
for ldap in {1..5};do
if id user${ldap} &>/dev/null;then
echo "System account alreadyexists"
else
adduser user${ldap}
echo user${ldap} | passwd --stdinuser${ldap} &> /dev/null
echo "user${ldap} system addfinish"
fi
done
[[email protected] openldap]# chmod +x adduser.sh
[[email protected] openldap]# ./adduser.sh
[[email protected] openldap]# id user1
uid=5004(user1) gid=5004(user1)groups=5004(user1)
[[email protected] openldap]# testsaslauthd-uuser1 -puser1
0: NO "authentication failed"
[[email protected] openldap]# tail -n 5/etc/passwd > system
[[email protected] openldap]#/usr/share/migrationtools/migrate_passwd.pl system people.ldif
[[email protected] openldap]# ll
total 80
-rwxr-xr-x 1 root root 274 Mar 31 16:43adduser.sh
-rw-r--r-- 1 root root 2671 Mar 31 11:50 bak-ldap.ldif
-rw-r--r-- 1 root root 1284 Mar 31 11:46 base.ldif
drwxr-xr-x. 2 root root 4096 Mar 9 16:47 certs
-rw-r----- 1 root ldap 121 May 11 2016 check_password.conf
-rw-r--r-- 1 root root 132 Mar 31 11:47group
-rw-r--r-- 1 root root 13 Mar 30 15:58group.in
-rw-r--r-- 1 root root 1337 Mar 31 11:47 group.ldif
-rw-r--r-- 1 root root 280 May 11 2016 ldap.conf
-rw-r--r-- 1 root root 501 Mar 31 11:49passwd
-rw-r--r-- 1 root root 39 Mar 30 15:58passwd.in
-rw-r--r-- 1 root root 1478 Mar 31 11:49 passwd.ldif
-rw-r--r-- 1 root root 2150 Mar 31 16:47 people.ldif
drwxr-xr-x 2 root root 4096 Mar 30 10:31 schema
-rw-r--r-- 1 root root 4459 Mar 30 11:39 slapd.conf
-rw-r--r-- 1 root root 4681 Mar 30 11:05 slapd.conf.ori
drwx------ 3 ldap ldap 4096 Mar 30 14:30 slapd.d
-rw-r--r-- 1 root root 205 Mar 31 16:47system
[[email protected] openldap]# tail -n 10/etc/group > group
[[email protected] openldap]#/usr/share/migrationtools/migrate_group.pl group group.ldif
[[email protected] openldap]# head -n 5people.ldif
dn: uid=user1,ou=People,dc=baobaotang,dc=org
uid: user1
cn: user1
objectClass: account
objectClass: posixAccount
[[email protected] openldap]# cat people.ldif
dn:uid=user1,ou=People,dc=baobaotang,dc=org
uid: user1
cn: user1
objectClass: account
objectClass: posixAccount
objectClass: top
objectClass: shadowAccount
userPassword:{crypt}$6$oWFU.3BW$1HWbdkYosz9VL6i5wKiRM4I2vT6Hk9zMoyIsyrkSK/.xCKQyiWRxWRHJgBY5xAiXW82qYK94ykvbdHzWZV8hj.
shadowLastChange: 17256
shadowMin: 0
shadowMax: 99999
shadowWarning: 7
loginShell: /bin/bash
uidNumber: 5004
gidNumber: 5004
homeDirectory: /home/user1
dn:uid=user2,ou=People,dc=baobaotang,dc=org
uid: user2
cn: user2
objectClass: account
objectClass: posixAccount
objectClass: top
objectClass: shadowAccount
userPassword:{crypt}$6$zYODZFJV$8IOdKkUM2mIRFmaKbNd3Mnv38mRawqNylTSTFWru6fXgTPCNpdlNqn1ZI1cAMwYLLElnYKKdNgZWv2eOvMOFk/
shadowLastChange: 17256
shadowMin: 0
shadowMax: 99999
shadowWarning: 7
loginShell: /bin/bash
uidNumber: 5005
gidNumber: 5005
homeDirectory: /home/user2
dn: uid=user3,ou=People,dc=baobaotang,dc=org
uid: user3
cn: user3
objectClass: account
objectClass: posixAccount
objectClass: top
objectClass: shadowAccount
userPassword:{crypt}$6$kaE/FMPD$oxEh8BewkoeaOejAjmKxH7VtXY13aRTqHTzDaQ9/H8svHTgACVgX0G1/8X7ECgIKT7/LjHRXusqiNbflZEEmS1
shadowLastChange: 17256
shadowMin: 0
shadowMax: 99999
shadowWarning: 7
loginShell: /bin/bash
uidNumber: 5006
gidNumber: 5006
homeDirectory: /home/user3
dn:uid=user4,ou=People,dc=baobaotang,dc=org
uid: user4
cn: user4
objectClass: account
objectClass: posixAccount
objectClass: top
objectClass: shadowAccount
userPassword:{crypt}$6$lBvP7CR3$7pDlbuerW58mWILooQVy33yn39nr5gs4ED1VgCH3FUYXk0hhUeTG8kxeQHhdGEUzGN0978eEYiCl.A9T2sp1g1
shadowLastChange: 17256
shadowMin: 0
shadowMax: 99999
shadowWarning: 7
loginShell: /bin/bash
uidNumber: 5007
gidNumber: 5007
homeDirectory: /home/user4
dn:uid=user5,ou=People,dc=baobaotang,dc=org
uid: user5
cn: user5
objectClass: account
objectClass: posixAccount
objectClass: top
objectClass: shadowAccount
userPassword:{crypt}$6$pz5Ln4/i$o3X2PlZS243cDOvXvlwBPz1tl9rEKVxuri9JQFbyhvR6FFrhtIHCLrEIEZrr/oQG9lDq8IdVVqca8Xyli9DJQ.
shadowLastChange: 17256
shadowMin: 0
shadowMax: 99999
shadowWarning: 7
loginShell: /bin/bash
uidNumber: 5008
gidNumber: 5008
homeDirectory: /home/user5
[[email protected] openldap]# ldapadd -x -W -D"cn=admin,dc=baobaotang,dc=org" -f people.ldif
Enter LDAP Password:
adding new entry"uid=user1,ou=People,dc=baobaotang,dc=org"
adding new entry"uid=user2,ou=People,dc=baobaotang,dc=org"
adding new entry"uid=user3,ou=People,dc=baobaotang,dc=org"
adding new entry"uid=user4,ou=People,dc=baobaotang,dc=org"
adding new entry"uid=user5,ou=People,dc=baobaotang,dc=org"
[[email protected] openldap]# ldapadd -x -W -D"cn=admin,dc=baobaotang,dc=org" -f group.ldif
Enter LDAP Password:
adding new entry"cn=avahi,ou=Group,dc=baobaotang,dc=org"
ldap_add: Already exists (68)
[[email protected] openldap]# cat group.ldif
dn: cn=avahi,ou=Group,dc=baobaotang,dc=org
objectClass: posixGroup
objectClass: top
cn: avahi
userPassword: {crypt}x
gidNumber: 70
dn: cn=nscd,ou=Group,dc=baobaotang,dc=org
objectClass: posixGroup
objectClass: top
cn: nscd
userPassword: {crypt}x
gidNumber: 28
dn: cn=test,ou=Group,dc=baobaotang,dc=org
objectClass: posixGroup
objectClass: top
cn: test
userPassword: {crypt}x
gidNumber: 5000
dn: cn=admin,ou=Group,dc=baobaotang,dc=org
objectClass: posixGroup
objectClass: top
cn: admin
userPassword: {crypt}x
gidNumber: 5002
dn: cn=ltest,ou=Group,dc=baobaotang,dc=org
objectClass: posixGroup
objectClass: top
cn: ltest
userPassword: {crypt}x
gidNumber: 5003
dn: cn=user1,ou=Group,dc=baobaotang,dc=org
objectClass: posixGroup
objectClass: top
cn: user1
userPassword: {crypt}x
gidNumber: 5004
dn: cn=user2,ou=Group,dc=baobaotang,dc=org
objectClass: posixGroup
objectClass: top
cn: user2
userPassword: {crypt}x
gidNumber: 5005
dn: cn=user3,ou=Group,dc=baobaotang,dc=org
objectClass: posixGroup
objectClass: top
cn: user3
userPassword: {crypt}x
gidNumber: 5006
dn: cn=user4,ou=Group,dc=baobaotang,dc=org
objectClass: posixGroup
objectClass: top
cn: user4
userPassword: {crypt}x
gidNumber: 5007
dn: cn=user5,ou=Group,dc=baobaotang,dc=org
objectClass: posixGroup
objectClass: top
cn: user5
userPassword: {crypt}x
gidNumber: 5008
[[email protected] openldap]# testsaslauthd -uuser1-puser1
0: OK "Success."
[[email protected] openldap]# testsaslauthd-uuser2 -puser2
0: OK "Success."
###########成功了,这里有点小激动,不容易搞定的#####################
测试成功
[[email protected] openldap]# testsaslauthd-uuser1 -puser1 #这个用户是ldap用户
0: OK "Success."
小结
ldap要有对应的测试用户,要有ldap用户
更改文件里的配置
[[email protected] openldap]# grep -i mech/etc/sysconfig/saslauthd
# Mechanism to use when checkingpasswords. Run "saslauthd -v"to get a list
# of which mechanism your installation wascompiled with the ablity to use.
MECH=ldap
调整配置etc/saslauthd.conf,如果不可以,重启saslauthd服务
安装svn并测试
安装略过~~~~~
svn通过ldap认证
这是不成功的,提示权限认证有问题
[[email protected] openldap]# svn checkoutsvn://10.1.11.149 /tmp --username=user1 --password=user1
Authentication realm:<svn://10.1.11.149:3690> My First Repository
Username: user1
Password for ‘user1‘:
接下来操作给权限
[[email protected] conf]# ll /etc/sasl2/
total 4
-rw-r--r-- 1 root root 49 Nov 10 2015 smtpd.conf
[[email protected] conf]# vi/etc/sasl2/svn.conf #默认不存在,创建一个文件
[[email protected] conf]# cat /etc/sasl2/svn.conf
pwcheck_method: saslauthd
mech_list: PLAIN LOCIN
[[email protected] conf]# pwd
/svn/project/conf
[[email protected] conf]# sed -i ‘[email protected]# use-sasl [email protected] = [email protected]‘ svnserve.conf
[[email protected] conf]# grep use-saslsvnserve.conf
use-sasl = true #去掉这行注释
[[email protected] openldap]# cd/svn/project/conf/
[[email protected] conf]# pkill svnserve
[[email protected] conf]# lsof -i :3690
[[email protected] conf]# svnserve -d -r/svn/project/
[[email protected] conf]# lsof -i :3690
COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME
svnserve 30088 root 3u IPv4 157380 0t0 TCP *:svn (LISTEN)
[[email protected] conf]# diff svnserve.conf.baksvnserve.conf
12,13c12,13
< # anon-access = read
< # auth-access = write
---
> anon-access = none
> auth-access = write
20c20
< # password-db = passwd
---
> password-db = /svn/project/conf/passwd
27c27
< # authz-db = authz
---
> authz-db = /svn/project/conf/authz
32c32
< # realm = My First Repository
---
> realm = My First Repository
40c40
< # use-sasl = true
---
> use-sasl = true
[[email protected] openldap]# svn checkoutsvn://10.1.11.149 /tmp --username=user1 --password=user1
-----------------------------------------------------------------------
ATTENTION! Your password for authentication realm:
<svn://10.1.11.149:3690> My First Repository
can only be stored to diskunencrypted! You are advised toconfigure
your system so that Subversion can storepasswords encrypted, if
possible. See the documentation for details.
You can avoid future appearances of thiswarning by setting the value
of the ‘store-plaintext-passwords‘ optionto either ‘yes‘ or ‘no‘ in
‘/root/.subversion/servers‘.
-----------------------------------------------------------------------
Store password unencrypted (yes/no)? yes
svn: Authorization failed #提示授权失败,这是因为我之前的svn服务修改了好几处配置文件,接下来恢复原始配置试试
出现authorization failed异常,一般都是authz文件里,用户组或者用户权限没有配置好,只要设置[/]就可以,代表根目录下所有的资源,如果要限定资源,可以加上子目录即可
[[email protected] conf]# mv svnserve.conf.baksvnserve.conf
mv: overwrite `svnserve.conf‘? y
[[email protected] conf]# ll
total 12
-rwx------ 1 root root 1140 Mar 16 15:31authz
-rwx------ 1 root root 340 Mar 16 15:31 passwd
-rw-r--r-- 1 root root 2279 Dec 14 16:00svnserve.conf
[[email protected] conf]# cp svnserve.confsvnserve.conf.bak
[[email protected] conf]# sed -i ‘[email protected]# use-sasl [email protected] = [email protected]‘ svnserve.conf
[[email protected] conf]# diff svnserve.conf.baksvnserve.conf
40c40
< # use-sasl = true
---
> use-sasl = true
[[email protected] conf]# pkill svnserve
[[email protected] conf]# lsof -i :3690
[[email protected] conf]# svnserve -d -r/svn/project/
[[email protected] conf]# lsof -i :3690
COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME
svnserve 30131 root 3u IPv4 157592 0t0 TCP *:svn (LISTEN)
[[email protected] conf]# svn checkoutsvn://10.1.11.149 /tmp --username=user1 --password=user1
-----------------------------------------------------------------------
ATTENTION! Your password for authentication realm:
<svn://10.1.11.149:3690> 45e01b91-73e4-4b5e-bf37-88c21b61a46b
can only be stored to diskunencrypted! You are advised toconfigure
your system so that Subversion can storepasswords encrypted, if
possible. See the documentation for details.
You can avoid future appearances of thiswarning by setting the value
of the ‘store-plaintext-passwords‘ optionto either ‘yes‘ or ‘no‘ in
‘/root/.subversion/servers‘.
-----------------------------------------------------------------------
Store password unencrypted (yes/no)? yes
Checked out revision 6.
此时成功了
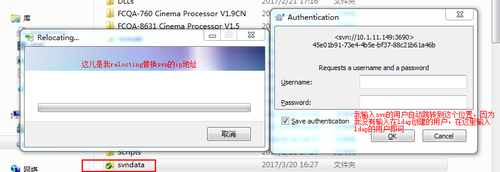
我们在windows下测试一下
以下就表示成功
如有不明白的请联系作者~~~
本文出自 “Arthur” 博客,请务必保留此出处http://sumous.blog.51cto.com/10483407/1945934
以上是关于LDAP架构部署认证的主要内容,如果未能解决你的问题,请参考以下文章