tibco server keystore使用多域名证书
Posted 白马酒凉
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了tibco server keystore使用多域名证书相关的知识,希望对你有一定的参考价值。
Create a Subject Alternative Name certificate with Active Directory Certificate Services
https://knowledge.zomers.eu/misc/Pages/Create-a-Subject-Alternative-Name-certificate-with-Active-Directory-Certificate-Services.aspx
1.mmc.msc
File->Add/Remove Snap-in
select Certificates and click on the Add > button
choose Computer accountand click on Next
In the next screen, leave Local computer selected and click Finish
2.Certification->Personal->Cerfification
All Tasks->Request New Certificate
leave Active Directory Enrollment Policy selected and click Next
check the box in front of Web Server and click on the More information is required link under it
In the Certificate Properties popup under Type, select Common name,DNS , input Values and add them
Switch to the General tab and enter a name that you find identifyable for the certificate that you\'re creating
go to the Private Key tab and expand the Key options section. Under it, check Make private key exportable
On the Certification Authority tab, make sure the right certification authority is selected which you want to sign your certificate request
Click OK to close the Certificate Properties window and click Enroll in the Certificate Enrollment window to file the request
Install a Root Certification Authority
https://technet.microsoft.com/en-us/library/cc731183(v=ws.11).aspx
1.nltest /dsgetdc:alex.com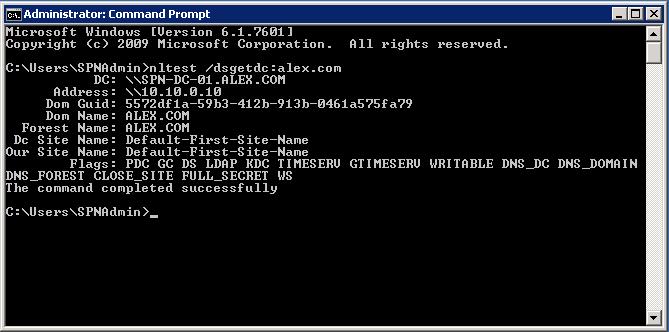
2.Certification Authority(certsrv)
openssl 生成私钥、申请文件,证书导入jks说明
http://www.cnblogs.com/liaier/p/4137383.html
openssl pkcs12 -export -in server.pem -inkey serverkey.key -out server.pfx -CAfile chain.pem
由于keytool没有直接导入private key的命令,又没有办法生成SAN证书请求,所以只能通过openssl生成CSR,然后再将签过的证书跟私钥生成PFX,再利用keytool将PFX转成JKS来使用。server端的keystore需要有private key的证书,client端的keystore不需要有private key的证书就可以使用,两者都不需要CA的证书。
1.创建私钥
openssl genrsa -out c:/server/server-key.pem 1024
2.创建证书请求 (subject alternative name (SAN) certificates):
openssl req -new -config CONF\\san.conf -out server-req.csr -key server-key.pem
san.conf
[req] distinguished_name = req_distinguished_name req_extensions = v3_req [ req_distinguished_name ] countryName_default = CN stateOrProvinceName_default = Test localityName_default = Test organizationName_default = Test commonName = Test (eg, YOUR name) commonName_max = 64 [ v3_req ] # Extensions to add to a certificate request basicConstraints = CA:FALSE keyUsage = nonRepudiation, digitalSignature, keyEncipherment subjectAltName = @alt_names [alt_names] DNS.1 = IPaddress1 DNS.2 = IPaddress2
3.CA收到证书申请后签发证书
openssl x509 -req -in c:/server/server-req.csr -out c:/server/server-cert.pem -signkey c:/server/server-key.pem -CA c:/ca/ca-cert.pem -CAkey c:/ca/ca-key.pem -CAcreateserial -days 3650
4.收到证书server-cert.pem(-----BEGIN CERTIFICATE-----),已有ca-cert.pem(-----BEGIN CERTIFICATE-----),server-key.pem(-----BEGIN RSA PRIVATE KEY-----)
利用这三者生成PFX文件
openssl pkcs12 -export -in server-cert.pem -inkey server-key.key -out server.pfx -CAfile ca-cert.pem
5.利用keytool将PFX转成JKS
keytool -importkeystore -srckeystore D:\\Temp\\server.pfx -srcstoretype pkcs12 -destkeystore D:\\Temp\\server.jks -deststoretype JKS -storepass testpwd2
6.查看JKS里面key alias为1
keytool -list -v -keystore D:\\Temp\\server.jks -storepass testpwd2
以上是关于tibco server keystore使用多域名证书的主要内容,如果未能解决你的问题,请参考以下文章
Windows Server 2008在MMC中申请多域名证书
Thawte SSL Web Server 多域型SSL证书
nginx+tomcat实现单ip,多域名,多项目配置,session有效