zabbix 实现 iptables 监控
Posted 运维工匠实战(如果发现有错误请大家把正确的方法发送给我,方便
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了zabbix 实现 iptables 监控相关的知识,希望对你有一定的参考价值。
安装iptstate
# yum install iptstate
配置zabbix key
iptables.conf
# cat /etc/zabbix/zabbix_agentd.d/iptables.conf UserParameter=iptstate[*],/etc/zabbix/monitor_scripts/iptables.sh $1
配置监控脚本:
# cat /etc/zabbix/monitor_scripts/iptables.sh #!/bin/bash #iptables 监控脚本 #2016/11-18 function tcp { sudo iptstate --single | grep tcp | wc -l } function tcp-syn { sudo iptstate --single | grep SYN | wc -l } function tcp-timewait { sudo iptstate --single | grep TIME_WAIT | wc -l } function tcp-established { sudo iptstate --single | grep ESTABLISHED | wc -l } function tcp-close { sudo iptstate --single | grep CLOSE | wc -l } function udp { sudo iptstate --single | grep udp | wc -l } function icmp { sudo iptstate --single | grep icmp | wc -l } function all { sudo iptstate --single | wc -l } # Run the requested function $1
查看脚本的权限:
# ll total 8 -rwxr-xr-x 1 root root 622 Apr 24 18:44 iptables.sh
添加sudo执行权限:
sed -i "s/^Defaults requiretty/#Defaults requiretty/g" /etc/sudoers echo “zabbix ALL=NOPASSWD: /usr/sbin/iptstate” /etc/sudoers
模板配置:
# cat Template-iptables.xml <?xml version="1.0" encoding="UTF-8"?> <zabbix_export> <version>2.0</version> <date>2016-11-18T09:27:03Z</date> <groups> <group> <name>Template-Security</name> </group> </groups> <templates> <template> <template>Template-iptables</template> <name>Template-iptables</name> <description/> <groups> <group> <name>Template-Security</name> </group> </groups> <applications> <application> <name>Iptstates</name> </application> </applications> <items> <item> <name>total all</name> <type>0</type> <snmp_community/> <multiplier>0</multiplier> <snmp_oid/> <key>iptstate[all]</key> <delay>60</delay> <history>90</history> <trends>365</trends> <status>0</status> <value_type>3</value_type> <allowed_hosts/> <units/> <delta>0</delta> <snmpv3_contextname/> <snmpv3_securityname/> <snmpv3_securitylevel>0</snmpv3_securitylevel> <snmpv3_authprotocol>0</snmpv3_authprotocol> <snmpv3_authpassphrase/> <snmpv3_privprotocol>0</snmpv3_privprotocol> <snmpv3_privpassphrase/> <formula>1</formula> <delay_flex/> <params/> <ipmi_sensor/> <data_type>0</data_type> <authtype>0</authtype> <username/> <password/> <publickey/> <privatekey/> <port/> <description/> <inventory_link>0</inventory_link> <applications> <application> <name>Iptstates</name> </application> </applications> <valuemap/> <logtimefmt/> </item> <item> <name>total icmp</name> <type>0</type> <snmp_community/> <multiplier>0</multiplier> <snmp_oid/> <key>iptstate[icmp]</key> <delay>60</delay> <history>90</history> <trends>365</trends> <status>0</status> <value_type>3</value_type> <allowed_hosts/> <units/> <delta>0</delta> <snmpv3_contextname/> <snmpv3_securityname/> <snmpv3_securitylevel>0</snmpv3_securitylevel> <snmpv3_authprotocol>0</snmpv3_authprotocol> <snmpv3_authpassphrase/> <snmpv3_privprotocol>0</snmpv3_privprotocol> <snmpv3_privpassphrase/> <formula>1</formula> <delay_flex/> <params/> <ipmi_sensor/> <data_type>0</data_type> <authtype>0</authtype> <username/> <password/> <publickey/> <privatekey/> <port/> <description/> <inventory_link>0</inventory_link> <applications> <application> <name>Iptstates</name> </application> </applications> <valuemap/> <logtimefmt/> </item> <item> <name>tcp close</name> <type>0</type> <snmp_community/> <multiplier>0</multiplier> <snmp_oid/> <key>iptstate[tcp-close]</key> <delay>60</delay> <history>90</history> <trends>365</trends> <status>0</status> <value_type>3</value_type> <allowed_hosts/> <units/> <delta>0</delta> <snmpv3_contextname/> <snmpv3_securityname/> <snmpv3_securitylevel>0</snmpv3_securitylevel> <snmpv3_authprotocol>0</snmpv3_authprotocol> <snmpv3_authpassphrase/> <snmpv3_privprotocol>0</snmpv3_privprotocol> <snmpv3_privpassphrase/> <formula>1</formula> <delay_flex/> <params/> <ipmi_sensor/> <data_type>0</data_type> <authtype>0</authtype> <username/> <password/> <publickey/> <privatekey/> <port/> <description/> <inventory_link>0</inventory_link> <applications> <application> <name>Iptstates</name> </application> </applications> <valuemap/> <logtimefmt/> </item> <item> <name>tcp established</name> <type>0</type> <snmp_community/> <multiplier>0</multiplier> <snmp_oid/> <key>iptstate[tcp-established]</key> <delay>60</delay> <history>90</history> <trends>365</trends> <status>0</status> <value_type>3</value_type> <allowed_hosts/> <units/> <delta>0</delta> <snmpv3_contextname/> <snmpv3_securityname/> <snmpv3_securitylevel>0</snmpv3_securitylevel> <snmpv3_authprotocol>0</snmpv3_authprotocol> <snmpv3_authpassphrase/> <snmpv3_privprotocol>0</snmpv3_privprotocol> <snmpv3_privpassphrase/> <formula>1</formula> <delay_flex/> <params/> <ipmi_sensor/> <data_type>0</data_type> <authtype>0</authtype> <username/> <password/> <publickey/> <privatekey/> <port/> <description/> <inventory_link>0</inventory_link> <applications> <application> <name>Iptstates</name> </application> </applications> <valuemap/> <logtimefmt/> </item> <item> <name>tcp syn</name> <type>0</type> <snmp_community/> <multiplier>0</multiplier> <snmp_oid/> <key>iptstate[tcp-syn]</key> <delay>60</delay> <history>90</history> <trends>365</trends> <status>0</status> <value_type>3</value_type> <allowed_hosts/> <units/> <delta>0</delta> <snmpv3_contextname/> <snmpv3_securityname/> <snmpv3_securitylevel>0</snmpv3_securitylevel> <snmpv3_authprotocol>0</snmpv3_authprotocol> <snmpv3_authpassphrase/> <snmpv3_privprotocol>0</snmpv3_privprotocol> <snmpv3_privpassphrase/> <formula>1</formula> <delay_flex/> <params/> <ipmi_sensor/> <data_type>0</data_type> <authtype>0</authtype> <username/> <password/> <publickey/> <privatekey/> <port/> <description/> <inventory_link>0</inventory_link> <applications> <application> <name>Iptstates</name> </application> </applications> <valuemap/> <logtimefmt/> </item> <item> <name>tcp timewait</name> <type>0</type> <snmp_community/> <multiplier>0</multiplier> <snmp_oid/> <key>iptstate[tcp-timewait]</key> <delay>60</delay> <history>90</history> <trends>365</trends> <status>0</status> <value_type>3</value_type> <allowed_hosts/> <units/> <delta>0</delta> <snmpv3_contextname/> <snmpv3_securityname/> <snmpv3_securitylevel>0</snmpv3_securitylevel> <snmpv3_authprotocol>0</snmpv3_authprotocol> <snmpv3_authpassphrase/> <snmpv3_privprotocol>0</snmpv3_privprotocol> <snmpv3_privpassphrase/> <formula>1</formula> <delay_flex/> <params/> <ipmi_sensor/> <data_type>0</data_type> <authtype>0</authtype> <username/> <password/> <publickey/> <privatekey/> <port/> <description/> <inventory_link>0</inventory_link> <applications> <application> <name>Iptstates</name> </application> </applications> <valuemap/> <logtimefmt/> </item> <item> <name>total tcp</name> <type>0</type> <snmp_community/> <multiplier>0</multiplier> <snmp_oid/> <key>iptstate[tcp]</key> <delay>60</delay> <history>90</history> <trends>365</trends> <status>0</status> <value_type>3</value_type> <allowed_hosts/> <units/> <delta>0</delta> <snmpv3_contextname/> <snmpv3_securityname/> <snmpv3_securitylevel>0</snmpv3_securitylevel> <snmpv3_authprotocol>0</snmpv3_authprotocol> <snmpv3_authpassphrase/> <snmpv3_privprotocol>0</snmpv3_privprotocol> <snmpv3_privpassphrase/> <formula>1</formula> <delay_flex/> <params/> <ipmi_sensor/> <data_type>0</data_type> <authtype>0</authtype> <username/> <password/> <publickey/> <privatekey/> <port/> <description/> <inventory_link>0</inventory_link> <applications> <application> <name>Iptstates</name> </application> </applications> <valuemap/> <logtimefmt/> </item> <item> <name>total udp</name> <type>0</type> <snmp_community/> <multiplier>0</multiplier> <snmp_oid/> <key>iptstate[udp]</key> <delay>60</delay> <history>90</history> <trends>365</trends> <status>0</status> <value_type>3</value_type> <allowed_hosts/> <units/> <delta>0</delta> <snmpv3_contextname/> <snmpv3_securityname/> <snmpv3_securitylevel>0</snmpv3_securitylevel> <snmpv3_authprotocol>0</snmpv3_authprotocol> <snmpv3_authpassphrase/> <snmpv3_privprotocol>0</snmpv3_privprotocol> <snmpv3_privpassphrase/> <formula>1</formula> <delay_flex/> <params/> <ipmi_sensor/> <data_type>0</data_type> <authtype>0</authtype> <username/> <password/> <publickey/> <privatekey/> <port/> <description/> <inventory_link>0</inventory_link> <applications> <application> <name>Iptstates</name> </application> </applications> <valuemap/> <logtimefmt/> </item> </items> <discovery_rules/> <macros/> <templates/> <screens/> </template> </templates> <triggers> <trigger> <expression>{Template-iptables:iptstate[all].last()}<3</expression> <name>iptables not running</name> <url/> <status>0</status> <priority>2</priority> <description>iptstates条目小于3认为关闭或者异常状态</description> <type>0</type> <dependencies/> </trigger> </triggers> <graphs> <graph> <name>iptstate</name> <width>900</width> <height>200</height> <yaxismin>0.0000</yaxismin> <yaxismax>100.0000</yaxismax> <show_work_period>1</show_work_period> <show_triggers>1</show_triggers> <type>0</type> <show_legend>1</show_legend> <show_3d>0</show_3d> <percent_left>0.0000</percent_left> <percent_right>0.0000</percent_right> <ymin_type_1>0</ymin_type_1> <ymax_type_1>0</ymax_type_1> <ymin_item_1>0</ymin_item_1> <ymax_item_1>0</ymax_item_1> <graph_items> <graph_item> <sortorder>0</sortorder> <drawtype>0</drawtype> <color>00C800</color> <yaxisside>0</yaxisside> <calc_fnc>2</calc_fnc> <type>0</type> <item> <host>Template-iptables</host> <key>iptstate[tcp-close]</key> </item> </graph_item> <graph_item> <sortorder>1</sortorder> <drawtype>0</drawtype> <color>C80000</color> <yaxisside>0</yaxisside> <calc_fnc>2</calc_fnc> <type>0</type> <item> <host>Template-iptables</host> <key>iptstate[tcp-established]</key> </item> </graph_item> <graph_item> <sortorder>2</sortorder> <drawtype>0</drawtype> <color>0000C8</color> <yaxisside>0</yaxisside> <calc_fnc>2</calc_fnc> <type>0</type> <item> <host>Template-iptables</host> <key>iptstate[tcp-syn]</key> </item> </graph_item> <graph_item> <sortorder>3</sortorder> <drawtype>0</drawtype> <color>C800C8</color> <yaxisside>0</yaxisside> <calc_fnc>2</calc_fnc> <type>0</type> <item> <host>Template-iptables</host> <key>iptstate[tcp-timewait]</key> </item> </graph_item> <graph_item> <sortorder>4</sortorder> <drawtype>0</drawtype> <color>00C8C8</color> <yaxisside>0</yaxisside> <calc_fnc>2</calc_fnc> <type>0</type> <item> <host>Template-iptables</host> <key>iptstate[all]</key> </item> </graph_item> <graph_item> <sortorder>5</sortorder> <drawtype>0</drawtype> <color>C8C800</color> <yaxisside>0</yaxisside> <calc_fnc>2</calc_fnc> <type>0</type> <item> <host>Template-iptables</host> <key>iptstate[icmp]</key> </item> </graph_item> <graph_item> <sortorder>6</sortorder> <drawtype>0</drawtype> <color>C8C8C8</color> <yaxisside>0</yaxisside> <calc_fnc>2</calc_fnc> <type>0</type> <item> <host>Template-iptables</host> <key>iptstate[tcp]</key> </item> </graph_item> <graph_item> <sortorder>7</sortorder> <drawtype>0</drawtype> <color>009600</color> <yaxisside>0</yaxisside> <calc_fnc>2</calc_fnc> <type>0</type> <item> <host>Template-iptables</host> <key>iptstate[udp]</key> </item> </graph_item> </graph_items> </graph> </graphs> </zabbix_export>
导入模板:
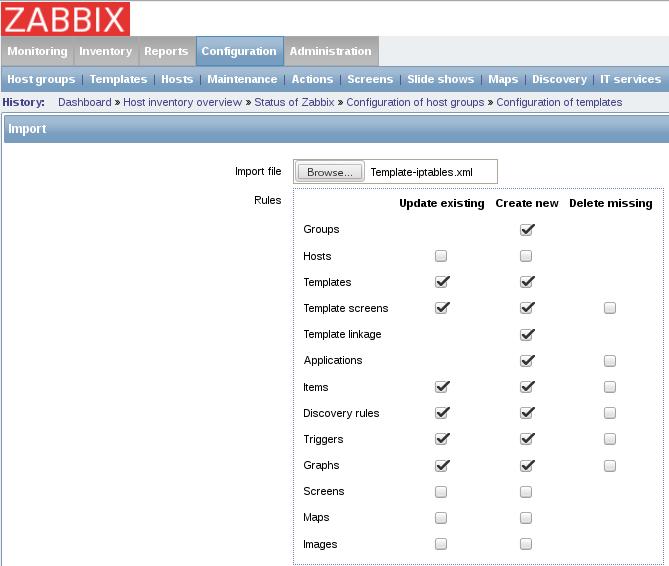
重启zabbix-agent:
# /etc/init.d/zabbix-agent restart
Shutting down Zabbix agent: [ OK ]
Starting Zabbix agent: [ OK ]
增加模板本上档host

以上是关于zabbix 实现 iptables 监控的主要内容,如果未能解决你的问题,请参考以下文章