交换机 show port-channel traffic显示结果解析 如Rx-Ucst Tx-Ucst Rx-Mcst Tx-Mcst Rx-Bcst 分别表示什么?
Posted
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了交换机 show port-channel traffic显示结果解析 如Rx-Ucst Tx-Ucst Rx-Mcst Tx-Mcst Rx-Bcst 分别表示什么?相关的知识,希望对你有一定的参考价值。
参考技术A Rx:下行(接收)流量;Tx:上行(发送)流量;
Ucst:单播数据包;
Mcst:组播数据包;
Bcst:广播数据包。本回答被提问者采纳
企业网cisco交换机dhcp snooping和IP source guard禁止手动配置IP
网络拓扑结构: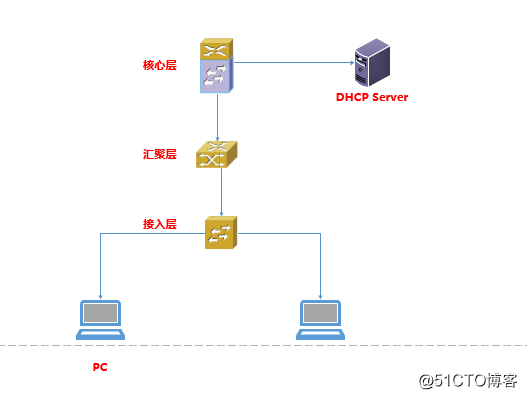
场景介绍:
核心层: 各个vlan接口网关均在核心层
汇聚层: 两台堆叠,port-channel 上联到核心层,port-channel 下联到接入层,不运行动态路由
接入层: 两端口port-channel,分别链接至两台汇聚交换机
目的:
通过dhcp snooping 防止内部企业网私自接入dhcp server;
通过启用IP source guard防止内部用户私自手动配置ip地址。
接入层dhcp snooping 配置:
2F-NEW-ACC-SW-1(config)#ip dhcp snooping
2F-NEW-ACC-SW-1(config)# ip dhcp snooping vlan 24
2F-NEW-ACC-SW-1(config)# ip dhcp snooping vlan 25
2F-NEW-ACC-SW-1(config)#interface GigabitEthernet1/0/47
2F-NEW-ACC-SW-1(config-if)#ip dhcp snooping trust
2F-NEW-ACC-SW-1(config)#interface GigabitEthernet1/0/48
2F-NEW-ACC-SW-1(config-if)#ip dhcp snooping trust
2F-NEW-ACC-SW-1(config)#interface Po1
2F-NEW-ACC-SW-1(config-if)#ip dhcp snooping trust
核心层需要如下配置:(否则客户端获取不到IP地址)
6S-CORE-SW-1(config)#interface vlan 24
6S-CORE-SW-1(config)# ip dhcp relay information trusted
6S-CORE-SW-1(config)#interface vlan 25
6S-CORE-SW-1(config)# ip dhcp relay information trusted
看一下效果:
2F-NEW-ACC-SW-1#sh ip dhcp snooping
Switch DHCP snooping is enabled
Switch DHCP gleaning is disabled
DHCP snooping is configured on following VLANs:
24-25
DHCP snooping is operational on following VLANs:
24-25
DHCP snooping is configured on the following L3 Interfaces:
Insertion of option 82 is enabled
circuit-id default format: vlan-mod-port
remote-id: 50f7.22c7.8d00 (MAC)
Option 82 on untrusted port is not allowed
Verification of hwaddr field is enabled
Verification of giaddr field is enabled
DHCP snooping trust/rate is configured on the following Interfaces:
Interface Trusted Allow option Rate limit (pps)
----------------------- ------- ------------ ----------------
GigabitEthernet1/0/47 yes yes unlimited
Custom circuit-ids:
GigabitEthernet1/0/48 yes yes unlimited
Custom circuit-ids:
Port-channel1 yes yes unlimited
Interface Trusted Allow option Rate limit (pps)
----------------------- ------- ------------ ----------------
Custom circuit-ids:
2F-NEW-ACC-SW-1#sh ip dhcp snooping binding
MacAddress IpAddress Lease(sec) Type VLAN Interface
------------------ --------------- ---------- ------------- ---- ---------- ----------
2C:60:0C:73:EA:FC 172.16.24.17 688869 dhcp-snooping 24 GigabitEt hernet1/0/17
00:0B:82:86:10:35 172.16.24.136 609318 dhcp-snooping 24 GigabitEt hernet1/0/20
A8:1E:84:A6:74:7E 172.16.25.12 690293 dhcp-snooping 25 GigabitEt hernet1/0/30
1C:39:47:E4:7D:1D 172.16.25.11 688206 dhcp-snooping 25 GigabitEt hernet1/0/28
A4:4C:C8:10:63:EE 172.16.24.150 688220 dhcp-snooping 24 GigabitEt hernet1/0/7
1C:39:47:E3:5C:C3 172.16.25.14 690459 dhcp-snooping 25 GigabitEt hernet1/0/29
D4:81:D7:FF:04:08 172.16.24.33 684055 dhcp-snooping 24 GigabitEt hernet1/0/15
A8:60:B6:2E:C7:A9 172.16.25.127 690215 dhcp-snooping 25 GigabitEt hernet1/0/44
A8:60:B6:38:2F:A9 172.16.25.132 689510 dhcp-snooping 25 GigabitEt hernet1/0/43
F0:76:1C:E2:64:4C 172.16.25.10 689447 dhcp-snooping 25 GigabitEt hernet1/0/34
--More--
IP Source Guard 配置:
Ip Souce Guard 需要借助于dhcp snooping,因此配置ip source guard 之前,必须先启用 dhcp snooping.
Ip Source Guard配置很简单,只需在对应的接口下启用即可:
2F-NEW-ACC-SW-1(config)#interface gigabitEthernet 1/0/1
2F-NEW-ACC-SW-1(config-if)#switchport port-security
2F-NEW-ACC-SW-1(config-if)#ip verify source port-security
看一下效果:
2F-NEW-ACC-SW-1#sh ip ver source
Interface Filter-type Filter-mode IP-address Mac-address Vlan
--------- ----------- ----------- --------------- ----------------- ----
Gi1/0/1 ip-mac inactive-no-snooping-vlan
Gi1/0/2 ip-mac active deny-all deny-all 24
Gi1/0/3 ip-mac inactive-no-snooping-vlan
Gi1/0/4 ip-mac active deny-all deny-all 24
Gi1/0/5 ip-mac active deny-all deny-all 24
Gi1/0/6 ip-mac active deny-all deny-all 24
Gi1/0/7 ip-mac active 172.16.24.150 A4:4C:C8:10:63:EE 24
Gi1/0/8 ip-mac inactive-no-snooping-vlan
Gi1/0/9 ip-mac active deny-all deny-all 24
Gi1/0/10 ip-mac inactive-no-snooping-vlan
Gi1/0/11 ip-mac active deny-all deny-all 24
Gi1/0/12 ip-mac active deny-all deny-all 24
Gi1/0/13 ip-mac active deny-all deny-all 24
Gi1/0/14 ip-mac inactive-no-snooping-vlan
Gi1/0/15 ip-mac active 172.16.24.33 D4:81:D7:FF:04:08 24
Gi1/0/16 ip-mac inactive-no-snooping-vlan
Gi1/0/17 ip-mac active 172.16.24.17 2C:60:0C:73:EA:FC 24
Gi1/0/18 ip-mac inactive-no-snooping-vlan
Gi1/0/19 ip-mac inactive-no-snooping-vlan
Gi1/0/20 ip-mac active 172.16.24.136 00:0B:82:86:10:35 24
Filter mode: 全部为Active 状态
IP 地址一栏中, 显示正常IP的既可以正常上网,deny-all 的可能是手动配置的IP地址 .
以上是关于交换机 show port-channel traffic显示结果解析 如Rx-Ucst Tx-Ucst Rx-Mcst Tx-Mcst Rx-Bcst 分别表示什么?的主要内容,如果未能解决你的问题,请参考以下文章
思科交换机 interface port-channel 5 命令有啥用??
企业网cisco交换机dhcp snooping和IP source guard禁止手动配置IP
channel-group,port-channel,etherchannel 小结