L2TP/IPSec一键安装脚本
Posted
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了L2TP/IPSec一键安装脚本相关的知识,希望对你有一定的参考价值。
感谢 秋水逸冰 的一键安装L2TP的脚本,确实很方便,留待备用!

本脚本适用环境:
系统支持:CentOS6+,Debian7+,Ubuntu12+
内存要求:≥128M
更新日期:2016 年 09 月 12 日
关于本脚本:
名词解释如下
L2TP(Layer 2 Tunneling Protocol)
IPSec(Internet Protocol Security)
IKEv2 (Internet Key Exchange v2)
能实现 IPsec 的目前总体上有 openswan,libreswan,strongswan 这3种。
libreswan 是基于 openswan 的 fork,所以现在各个发行版基本已经看不到 openswan 的身影了。
当然也有使用 strongswan 的。
之所以要更新 L2TP 一键安装脚本,是因为随着各个 Linux 发行版不断推陈出新,原有的脚本已经不适应现在的需求。
本脚本通过编译安装最新版 libreswan 来实现 IPSec(CentOS7 下则是全部 yum 安装),yum 或 apt-get 来安装 xl2tpd,再根据各个发行版的使用方法不同,部署防火墙规则。
写在前面:
基于 OpenVZ 虚拟化技术的 VPS 需要开启TUN/TAP才能正常使用,购买 VPS 时请先咨询服务商是否支持开启 TUN/TAP。
纠正:
OpenVZ 虚拟的 VPS 需要系统内核支持 IPSec 才行。也就是说,母服务器的内核如果不支持的话那就没办法,只能换 VPS。
因此,一般不建议在 OpenVZ 的 VPS 上安装本脚本。脚本如果检测到该 VPS 为 OpenVZ 架构,会出现警告提醒。
如何检测是否支持TUN模块?
执行命令:
cat /dev/net/tun
如果返回信息为:cat: /dev/net/tun: File descriptor in bad state 说明正常
如何检测是否支持ppp模块?
执行命令:
cat /dev/ppp
如果返回信息为:cat: /dev/ppp: No such device or address 说明正常
当然,脚本在安装时也会执行检查,如果不适用于安装,脚本会予以提示。
使用方法:
root 用户登录后,运行以下命令:
wget --no-check-certificate https://raw.githubusercontent.com/teddysun/across/master/l2tp.sh chmod +x l2tp.sh ./l2tp.sh
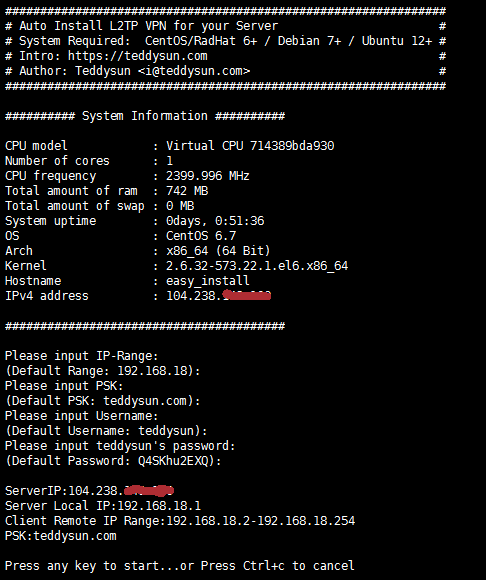
执行后,会有如下交互界面
Please input IP-Range:
(Default Range: 192.168.18):
输入本地IP段范围(本地电脑连接到VPS后给分配的一个本地IP地址),直接回车意味着输入默认值192.168.18
Please input PSK:
(Default PSK: teddysun.com):
PSK意为预共享密钥,即指定一个密钥将来在连接时需要用到,直接回车意味着输入默认值teddysun.com
Please input Username:
(Default Username: teddysun):
Username意为用户名,即第一个默认用户。直接回车意味着输入默认值teddysun
Please input teddysun’s password:
(Default Password: Q4SKhu2EXQ):
输入用户的密码,默认会随机生成一个10位包含大小写字母和数字的密码,当然你也可以指定密码。
ServerIP:your_server_main_IP
显示你的 VPS 的主 IP(如果是多 IP 的 VPS 也只显示一个)
Server Local IP:192.168.18.1
显示你的 VPS 的本地 IP(默认即可)
Client Remote IP Range:192.168.18.2-192.168.18.254
显示 IP 段范围
PSK:teddysun.com
显示 PSK
Press any key to start…or Press Ctrl+c to cancel
按下任意按键继续,如果想取消安装,请按Ctrl+c键
安装完成后,脚本会执行 ipsec verify 命令并提示如下:
If there are no [FAILED] above, then you can connect to your L2TP VPN Server with the default Username/Password is below: ServerIP:your_server_IP PSK:your PSK Username:your usename Password:your password If you want to modify user settings, please use command(s): l2tp -a (Add a user) l2tp -d (Delete a user) l2tp -l (List all users) l2tp -m (Modify a user password) Welcome to visit https://teddysun.com/448.html Enjoy it!
如果你要想对用户进行操作,可以使用如下命令:
l2tp -a 新增用户
l2tp -d 删除用户
l2tp -m 修改现有的用户的密码
l2tp -l 列出所有用户名和密码
l2tp -h 列出帮助信息
其他事项:
1、脚本在安装完成后,已自动启动进程,并加入了开机自启动。
2、脚本会改写 iptables 或 firewalld 的规则。
3、脚本安装时,会即时将安装日志写到 /root/l2tp.log 文件里,如果你安装失败,可以通过此文件来寻找错误信息。
使用命令:
ipsec status (查看 IPSec 运行状态)
ipsec verify (查看 IPSec 检查结果)
/etc/init.d/ipsec start|stop|restart|status (CentOS6 下使用)
/etc/init.d/xl2tpd start|stop|restart (CentOS6 下使用)
systemctl start|stop|restart|status ipsec (CentOS7 下使用)
systemctl start|stop|restart xl2tpd (CentOS7 下使用)
service ipsec start|stop|restart|status (Debian/Ubuntu 下使用)
service xl2tpd start|stop|restart (Debian/Ubuntu 下使用)
评论节选(有改动),供参考
评论节选1(感谢@wawnnzxd 评论于 2016-11-10)
安卓6.0系统无法成功连接l2tp,查了谷歌之后发现好像是安卓是sha256加密
我是这么做的,目前正常连接一小时,没有断线,mac ios android
需要在 /etc/ipsec.conf 的 conn L2TP-PSK-noNAT 下加入
sha2-truncbug=yes
然后重启 IPSec 和 xl2tpd 服务,重新连接就可以了。
可以解决安卓 6.0 的 vpn 无法连接问题。
评论节选2(感谢@S_ven 评论于 2016-10-17)
在/etc/ipsec.conf 的 conn L2TP-PSK-noNAT 下加入
leftnexthop defaultroute rightnexthop defaultroute
然后重启 IPSec 和 xl2tpd 服务应该可以解决同一局域下多人连接的时候,出现连接不上的情况。
如果还是不行,就得看下这个链接里面的配置:
https://segmentfault.com/a/1190000005626927
我就是根据这个里面的配置和你的对比改好了。
更新日志
2016 年 04 月 18 日更新
1、目前在 Debian 7 上测试的结果,因为 libnss3 和 libnspr4 的版本过低而导致编译 libreswan 失败。临时解决办法是 dpkg 安装 libnss3_3.17.2 和 libnspr4_4.10.7 的 deb 包后重试
参考链接:https://libreswan.org/wiki/3.14_on_Debian_Wheezy
2016 年 04 月 19 日更新
2、修复了在 Debian 7 下因为 libnss3 和 libnspr4 的版本过低而导致编译 libreswan 失败的问题。
2016 年 04 月 22 日更新
3、修复了在 Ubuntu 16.04 下因为默认缺少 python 命令而导致 ipsec verify 等命令不能用的问题。
2016 年 04 月 25 日更新
4、在 Vultr 的 Debian 7 的系统模板下安装时,软件包 libcurl4-nss-dev 会出现依赖错误。如下所示:
The following packages have unmet dependencies:
libcurl4-nss-dev : Depends: libldap2-dev but it is not going to be installed
Depends: librtmp-dev but it is not going to be installed
而 libldap2-dev 和 librtmp-dev 又依赖了其他几种软件包。总之最后的依赖关系如下:
libldap2-dev : Depends: libldap-2.4-2 (= 2.4.31-2+deb7u1) but 2.4.31+really2.4.40+dfsg-1+deb8u1~bpo70+1 is to be installed
librtmp-dev : Depends: libgnutls-dev but it is not going to be installed
libgnutls-dev : Depends: libp11-kit-dev (>= 0.4) but it is not going to be installed
libp11-kit-dev : Depends: libp11-kit0 (= 0.12-3) but 0.20.7-1~bpo70+1 is to be installed
那么解决办法就是把最底层的依赖包 libp11-kit0 先卸载掉,然后再安装 libcurl4-nss-dev 即可。
apt-get -y remove libp11-kit0 apt-get -y --no-install-recommends install libcurl4-nss-dev wget
然后再运行脚本安装即可。
2016 年 06 月 10 日更新
脚本在安装完成后,新增了几个命令,便于操作用户
l2tp -a 新增用户
l2tp -d 删除用户
l2tp -l 列出所有用户
l2tp -h 列出帮助信息
2016 年 08 月 05 日更新
升级 libreswan 到版本 3.18。
2016 年 08 月 13 日更新
修正 Debian 8 下的 sd-daemon.h: No such file or directory 问题,是由于缺少依赖包 libsystemd-daemon-dev 导致的。
2016 年 09 月 12 日更新
修正了在 CentOS 6 下 libevent2 依赖的问题;
新增了一个 -m 选项,用以修改现有用户的密码。
附带安装脚本内容如下:
#!/usr/bin/env bash PATH=/bin:/sbin:/usr/bin:/usr/sbin:/usr/local/bin:/usr/local/sbin:~/bin export PATH #=======================================================================# # System Supported: CentOS 6+ / Debian 7+ / Ubuntu 12+ # # Description: L2TP VPN Auto Installer # # Author: Teddysun <[email protected]> # # Intro: https://teddysun.com/448.html # #=======================================================================# cur_dir=`pwd` libevent2_src_filename="libevent-2.0.22-stable" libreswan_filename="libreswan-3.18" rootness(){ if [[ $EUID -ne 0 ]]; then echo "Error:This script must be run as root!" 1>&2 exit 1 fi } tunavailable(){ if [[ ! -e /dev/net/tun ]]; then echo "Error:TUN/TAP is not available!" 1>&2 exit 1 fi } disable_selinux(){ if [ -s /etc/selinux/config ] && grep ‘SELINUX=enforcing‘ /etc/selinux/config; then sed -i ‘s/SELINUX=enforcing/SELINUX=disabled/g‘ /etc/selinux/config setenforce 0 fi } get_opsy(){ [ -f /etc/redhat-release ] && awk ‘{print ($1,$3~/^[0-9]/?$3:$4)}‘ /etc/redhat-release && return [ -f /etc/os-release ] && awk -F‘[= "]‘ ‘/PRETTY_NAME/{print $3,$4,$5}‘ /etc/os-release && return [ -f /etc/lsb-release ] && awk -F‘[="]+‘ ‘/DESCRIPTION/{print $2}‘ /etc/lsb-release && return } get_os_info(){ IP=$( ip addr | egrep -o ‘[0-9]{1,3}\.[0-9]{1,3}\.[0-9]{1,3}\.[0-9]{1,3}‘ | egrep -v "^192\.168|^172\.1[6-9]\.|^172\.2[0-9]\.|^172\.3[0-2]\.|^10\.|^127\.|^255\.|^0\." | head -n 1 ) if [ -z ${IP} ]; then IP=$( wget -qO- -t1 -T2 ipv4.icanhazip.com ) fi local cname=$( awk -F: ‘/model name/ {name=$2} END {print name}‘ /proc/cpuinfo | sed ‘s/^[ \t]*//;s/[ \t]*$//‘ ) local cores=$( awk -F: ‘/model name/ {core++} END {print core}‘ /proc/cpuinfo ) local freq=$( awk -F: ‘/cpu MHz/ {freq=$2} END {print freq}‘ /proc/cpuinfo | sed ‘s/^[ \t]*//;s/[ \t]*$//‘ ) local tram=$( free -m | awk ‘/Mem/ {print $2}‘ ) local swap=$( free -m | awk ‘/Swap/ {print $2}‘ ) local up=$( awk ‘{a=$1/86400;b=($1%86400)/3600;c=($1%3600)/60;d=$1%60} {printf("%ddays, %d:%d:%d\n",a,b,c,d)}‘ /proc/uptime ) local load=$( w | head -1 | awk -F‘load average:‘ ‘{print $2}‘ | sed ‘s/^[ \t]*//;s/[ \t]*$//‘ ) local opsy=$( get_opsy ) local arch=$( uname -m ) local lbit=$( getconf LONG_BIT ) local host=$( hostname ) local kern=$( uname -r ) echo "########## System Information ##########" echo echo "CPU model : ${cname}" echo "Number of cores : ${cores}" echo "CPU frequency : ${freq} MHz" echo "Total amount of ram : ${tram} MB" echo "Total amount of swap : ${swap} MB" echo "System uptime : ${up}" echo "Load average : ${load}" echo "OS : ${opsy}" echo "Arch : ${arch} (${lbit} Bit)" echo "Kernel : ${kern}" echo "Hostname : ${host}" echo "IPv4 address : ${IP}" echo echo "########################################" } check_sys(){ local checkType=$1 local value=$2 local release=‘‘ local systemPackage=‘‘ if [[ -f /etc/redhat-release ]];then release="centos" systemPackage="yum" elif cat /etc/issue | grep -q -E -i "debian";then release="debian" systemPackage="apt" elif cat /etc/issue | grep -q -E -i "ubuntu";then release="ubuntu" systemPackage="apt" elif cat /etc/issue | grep -q -E -i "centos|red hat|redhat";then release="centos" systemPackage="yum" elif cat /proc/version | grep -q -E -i "debian";then release="debian" systemPackage="apt" elif cat /proc/version | grep -q -E -i "ubuntu";then release="ubuntu" systemPackage="apt" elif cat /proc/version | grep -q -E -i "centos|red hat|redhat";then release="centos" systemPackage="yum" fi if [[ ${checkType} == "sysRelease" ]]; then if [ "$value" == "$release" ];then return 0 else return 1 fi elif [[ ${checkType} == "packageManager" ]]; then if [ "$value" == "$systemPackage" ];then return 0 else return 1 fi fi } rand() { index=0 str="" for i in {a..z}; do arr[index]=${i}; index=`expr ${index} + 1`; done for i in {A..Z}; do arr[index]=${i}; index=`expr ${index} + 1`; done for i in {0..9}; do arr[index]=${i}; index=`expr ${index} + 1`; done for i in {1..10}; do str="$str${arr[$RANDOM%$index]}"; done echo ${str} } is_64bit(){ if [ `getconf WORD_BIT` = ‘32‘ ] && [ `getconf LONG_BIT` = ‘64‘ ] ; then return 0 else return 1 fi } download_file(){ local download_root_url="http://dl.teddysun.com/files" if [ -s ${1} ]; then echo "$1 [found]" else echo "$1 not found!!!download now..." if ! wget -c -t3 -T60 ${download_root_url}/${1};then echo "Failed to download $1, please download it to ${cur_dir} directory manually and try again." exit 1 fi fi } versionget(){ if [[ -s /etc/redhat-release ]];then grep -oE "[0-9.]+" /etc/redhat-release else grep -oE "[0-9.]+" /etc/issue fi } centosversion(){ if check_sys sysRelease centos;then local code=${1} local version="`versionget`" local main_ver=${version%%.*} if [ "${main_ver}" == "${code}" ];then return 0 else return 1 fi else return 1 fi } debianversion(){ if check_sys sysRelease debian;then local version=$( get_opsy ) local code=${1} local main_ver=$( echo ${version} | sed ‘s/[^0-9]//g‘) if [ "${main_ver}" == "${code}" ];then return 0 else return 1 fi else return 1 fi } version_check(){ if check_sys packageManager yum; then if centosversion 5; then echo "Error: CentOS 5 is not supported, Please re-install OS and try again." exit 1 fi fi } preinstall_l2tp(){ echo if [ -d "/proc/vz" ]; then echo -e "\033[41;37m WARNING: \033[0m Your VPS is based on OpenVZ, and IPSec might not be supported by the kernel." echo "Continue installation? (y/n)" read -p "(Default: n)" agree [ -z ${agree} ] && agree="n" if [ "${agree}" == "n" ]; then echo echo "L2TP installation cancelled." echo exit 0 fi fi echo echo "Please enter IP-Range:" read -p "(Default Range: 192.168.18):" iprange [ -z ${iprange} ] && iprange="192.168.18" echo "Please enter PSK:" read -p "(Default PSK: teddysun.com):" mypsk [ -z ${mypsk} ] && mypsk="teddysun.com" echo "Please enter Username:" read -p "(Default Username: teddysun):" username [ -z ${username} ] && username="teddysun" password=`rand` echo "Please enter ${username}‘s password:" read -p "(Default Password: ${password}):" tmppassword [ ! -z ${tmppassword} ] && password=${tmppassword} get_char(){ SAVEDSTTY=`stty -g` stty -echo stty cbreak dd if=/dev/tty bs=1 count=1 2> /dev/null stty -raw stty echo stty $SAVEDSTTY } echo echo "ServerIP:${IP}" echo "Server Local IP:${iprange}.1" echo "Client Remote IP Range:${iprange}.2-${iprange}.254" echo "PSK:${mypsk}" echo echo "Press any key to start... or press Ctrl + C to cancel." char=`get_char` } install_l2tp(){ mknod /dev/random c 1 9 if check_sys packageManager apt;then apt-get -y update if debianversion 7;then if is_64bit;then local libnspr4_filename1="libnspr4_4.10.7-1_amd64.deb" local libnspr4_filename2="libnspr4-0d_4.10.7-1_amd64.deb" local libnspr4_filename3="libnspr4-dev_4.10.7-1_amd64.deb" local libnspr4_filename4="libnspr4-dbg_4.10.7-1_amd64.deb" local libnss3_filename1="libnss3_3.17.2-1.1_amd64.deb" local libnss3_filename2="libnss3-1d_3.17.2-1.1_amd64.deb" local libnss3_filename3="libnss3-tools_3.17.2-1.1_amd64.deb" local libnss3_filename4="libnss3-dev_3.17.2-1.1_amd64.deb" local libnss3_filename5="libnss3-dbg_3.17.2-1.1_amd64.deb" else local libnspr4_filename1="libnspr4_4.10.7-1_i386.deb" local libnspr4_filename2="libnspr4-0d_4.10.7-1_i386.deb" local libnspr4_filename3="libnspr4-dev_4.10.7-1_i386.deb" local libnspr4_filename4="libnspr4-dbg_4.10.7-1_i386.deb" local libnss3_filename1="libnss3_3.17.2-1.1_i386.deb" local libnss3_filename2="libnss3-1d_3.17.2-1.1_i386.deb" local libnss3_filename3="libnss3-tools_3.17.2-1.1_i386.deb" local libnss3_filename4="libnss3-dev_3.17.2-1.1_i386.deb" local libnss3_filename5="libnss3-dbg_3.17.2-1.1_i386.deb" fi rm -rf ${cur_dir}/l2tp mkdir -p ${cur_dir}/l2tp cd ${cur_dir}/l2tp download_file "${libnspr4_filename1}" download_file "${libnspr4_filename2}" download_file "${libnspr4_filename3}" download_file "${libnspr4_filename4}" download_file "${libnss3_filename1}" download_file "${libnss3_filename2}" download_file "${libnss3_filename3}" download_file "${libnss3_filename4}" download_file "${libnss3_filename5}" dpkg -i ${libnspr4_filename1} ${libnspr4_filename2} ${libnspr4_filename3} ${libnspr4_filename4} dpkg -i ${libnss3_filename1} ${libnss3_filename2} ${libnss3_filename3} ${libnss3_filename4} ${libnss3_filename5} apt-get -y install wget gcc ppp flex bison make pkg-config libpam0g-dev libcap-ng-dev libcap-ng-utils libunbound-dev libevent-dev libcurl4-nss-dev libsystemd-daemon-dev else apt-get -y install wget gcc ppp flex bison make python libnss3-dev libnspr4-dev pkg-config libpam0g-dev libcap-ng-dev libcap-ng-utils libunbound-dev libnss3-tools libevent-dev libcurl4-nss-dev libsystemd-daemon-dev fi apt-get -y --no-install-recommends install xmlto apt-get -y install xl2tpd compile_install elif check_sys packageManager yum; then if centosversion 7; then yum -y install epel-release yum -y install ppp libreswan xl2tpd firewalld yum_install elif centosversion 6; then yum -y install epel-release yum -y install gcc gcc-c++ ppp iptables make gmp-devel xmlto bison flex libpcap-devel lsof yum -y install xl2tpd curl-devel nss-devel nspr-devel pkgconfig pam-devel unbound-devel libcap-ng-devel compile_install fi fi } compile_install(){ rm -rf ${cur_dir}/l2tp mkdir -p ${cur_dir}/l2tp cd ${cur_dir}/l2tp download_file "${libreswan_filename}.tar.gz" tar -zxf ${libreswan_filename}.tar.gz if centosversion 6; then download_file "${libevent2_src_filename}.tar.gz" tar -zxf ${libevent2_src_filename}.tar.gz cd ${libevent2_src_filename} ./configure make && make install if [ $? -eq 0 ]; then if is_64bit;then ln -sf /usr/local/lib/libevent-2.0.so.5 /usr/lib64/libevent-2.0.so.5 ln -sf /usr/local/lib/libevent_pthreads-2.0.so.5 /usr/lib64/libevent_pthreads-2.0.so.5 else ln -sf /usr/local/lib/libevent-2.0.so.5 /usr/lib/libevent-2.0.so.5 ln -sf /usr/local/lib/libevent_pthreads-2.0.so.5 /usr/lib/libevent_pthreads-2.0.so.5 fi echo "/usr/local/lib" > /etc/ld.so.conf.d/local.conf ldconfig else echo "libevent2 install failed..." exit 1 fi fi cd ${cur_dir}/l2tp/${libreswan_filename} echo "WERROR_CFLAGS =" > Makefile.inc.local make programs && make install /usr/local/sbin/ipsec --version >/dev/null 2>&1 if [ $? -ne 0 ];then echo "${libreswan_filename} install failed." exit 1 fi cat > /etc/ipsec.conf<<EOF config setup nat_traversal=yes protostack=netkey oe=off interfaces="%defaultroute" dumpdir=/var/run/pluto/ virtual_private=%v4:10.0.0.0/8,%v4:192.168.0.0/16,%v4:172.16.0.0/12,%v4:25.0.0.0/8,%v4:100.64.0.0/10,%v6:fd00::/8,%v6:fe80::/10 conn L2TP-PSK-NAT rightsubnet=vhost:%priv also=L2TP-PSK-noNAT conn L2TP-PSK-noNAT authby=secret pfs=no auto=add keyingtries=3 rekey=no ikelifetime=8h keylife=1h type=transport left=${IP} leftid=${IP} leftprotoport=17/1701 right=%any rightprotoport=17/%any dpddelay=40 dpdtimeout=130 dpdaction=clear EOF cat > /etc/ipsec.secrets<<EOF ${IP} %any: PSK "${mypsk}" EOF cat > /etc/xl2tpd/xl2tpd.conf<<EOF [global] listen-addr = ${IP} [lns default] ip range = ${iprange}.2-${iprange}.254 local ip = ${iprange}.1 require chap = yes refuse pap = yes require authentication = yes name = LinuxVPNserver ppp debug = yes pppoptfile = /etc/ppp/options.xl2tpd length bit = yes EOF cat > /etc/ppp/options.xl2tpd<<EOF ipcp-accept-local ipcp-accept-remote require-mschap-v2 ms-dns 8.8.8.8 ms-dns 8.8.4.4 noccp auth crtscts hide-password idle 1800 mtu 1410 mru 1410 nodefaultroute name l2tpd debug lock proxyarp connect-delay 5000 EOF rm -f /etc/ppp/chap-secrets cat > /etc/ppp/chap-secrets<<EOF # Secrets for authentication using CHAP # client server secret IP addresses ${username} l2tpd ${password} * EOF cp -pf /etc/sysctl.conf /etc/sysctl.conf.bak sed -i ‘s/net.ipv4.ip_forward = 0/net.ipv4.ip_forward = 1/g‘ /etc/sysctl.conf for each in `ls /proc/sys/net/ipv4/conf/` do echo "net.ipv4.conf.${each}.accept_source_route=0" >> /etc/sysctl.conf echo "net.ipv4.conf.${each}.accept_redirects=0" >> /etc/sysctl.conf echo "net.ipv4.conf.${each}.send_redirects=0" >> /etc/sysctl.conf echo "net.ipv4.conf.${each}.rp_filter=0" >> /etc/sysctl.conf done sysctl -p if centosversion 6; then [ -f /etc/sysconfig/iptables ] && cp -pf /etc/sysconfig/iptables /etc/sysconfig/iptables.old.`date +%Y%m%d` if [ "`/sbin/iptables-save | grep -c ‘^\-‘`" = "0" ]; then cat > /etc/sysconfig/iptables <<EOF # Added by L2TP VPN script *filter :INPUT ACCEPT [0:0] :FORWARD ACCEPT [0:0] :OUTPUT ACCEPT [0:0] -A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT -A INPUT -p icmp -j ACCEPT -A INPUT -i lo -j ACCEPT -A INPUT -p tcp --dport 22 -j ACCEPT -A INPUT -p udp -m multiport --dports 500,4500,1701 -j ACCEPT -A FORWARD -m state --state RELATED,ESTABLISHED -j ACCEPT -A FORWARD -s ${iprange}.0/24 -j ACCEPT COMMIT *nat :PREROUTING ACCEPT [0:0] :OUTPUT ACCEPT [0:0] :POSTROUTING ACCEPT [0:0] -A POSTROUTING -s ${iprange}.0/24 -j SNAT --to-source ${IP} COMMIT EOF else iptables -I INPUT -p udp -m multiport --dports 500,4500,1701 -j ACCEPT iptables -I FORWARD -m state --state RELATED,ESTABLISHED -j ACCEPT iptables -I FORWARD -s ${iprange}.0/24 -j ACCEPT iptables -t nat -A POSTROUTING -s ${iprange}.0/24 -j SNAT --to-source ${IP} /etc/init.d/iptables save fi if [ ! -f /etc/ipsec.d/cert9.db ]; then echo > /var/tmp/libreswan-nss-pwd certutil -N -f /var/tmp/libreswan-nss-pwd -d /etc/ipsec.d rm -f /var/tmp/libreswan-nss-pwd fi chkconfig --add iptables chkconfig iptables on chkconfig --add ipsec chkconfig ipsec on chkconfig --add xl2tpd chkconfig xl2tpd on /etc/init.d/iptables restart /etc/init.d/ipsec start /etc/init.d/xl2tpd start else [ -f /etc/iptables.rules ] && cp -pf /etc/iptables.rules /etc/iptables.rules.old.`date +%Y%m%d` if [ "`/sbin/iptables-save | grep -c ‘^\-‘`" = "0" ]; then cat > /etc/iptables.rules <<EOF # Added by L2TP VPN script *filter :INPUT ACCEPT [0:0] :FORWARD ACCEPT [0:0] :OUTPUT ACCEPT [0:0] -A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT -A INPUT -p icmp -j ACCEPT -A INPUT -i lo -j ACCEPT -A INPUT -p tcp --dport 22 -j ACCEPT -A INPUT -p udp -m multiport --dports 500,4500,1701 -j ACCEPT -A FORWARD -m state --state RELATED,ESTABLISHED -j ACCEPT -A FORWARD -s ${iprange}.0/24 -j ACCEPT COMMIT *nat :PREROUTING ACCEPT [0:0] :OUTPUT ACCEPT [0:0] :POSTROUTING ACCEPT [0:0] -A POSTROUTING -s ${iprange}.0/24 -j SNAT --to-source ${IP} COMMIT EOF else iptables -I INPUT -p udp -m multiport --dports 500,4500,1701 -j ACCEPT iptables -I FORWARD -m state --state RELATED,ESTABLISHED -j ACCEPT iptables -I FORWARD -s ${iprange}.0/24 -j ACCEPT iptables -t nat -A POSTROUTING -s ${iprange}.0/24 -j SNAT --to-source ${IP} /sbin/iptables-save > /etc/iptables.rules fi cat > /etc/network/if-up.d/iptables <<EOF #!/bin/sh /sbin/iptables-restore < /etc/iptables.rules EOF chmod +x /etc/network/if-up.d/iptables if [ ! -f /etc/ipsec.d/cert9.db ]; then echo > /var/tmp/libreswan-nss-pwd certutil -N -f /var/tmp/libreswan-nss-pwd -d /etc/ipsec.d rm -f /var/tmp/libreswan-nss-pwd fi update-rc.d -f xl2tpd defaults cp -f /etc/rc.local /etc/rc.local.old.`date +%Y%m%d` sed --follow-symlinks -i -e ‘/^exit 0/d‘ /etc/rc.local cat >> /etc/rc.local <<EOF # Added by L2TP VPN script echo 1 > /proc/sys/net/ipv4/ip_forward /usr/sbin/service ipsec start exit 0 EOF chmod +x /etc/rc.local echo 1 > /proc/sys/net/ipv4/ip_forward /sbin/iptables-restore < /etc/iptables.rules /usr/sbin/service ipsec start /usr/sbin/service xl2tpd restart fi } yum_install(){ rm -f /etc/ipsec.conf cat > /etc/ipsec.conf<<EOF config setup nat_traversal=yes protostack=netkey oe=off interfaces="%defaultroute" dumpdir=/var/run/pluto/ virtual_private=%v4:10.0.0.0/8,%v4:192.168.0.0/16,%v4:172.16.0.0/12,%v4:25.0.0.0/8,%v4:100.64.0.0/10,%v6:fd00::/8,%v6:fe80::/10 conn L2TP-PSK-NAT rightsubnet=vhost:%priv also=L2TP-PSK-noNAT conn L2TP-PSK-noNAT authby=secret pfs=no auto=add keyingtries=3 rekey=no ikelifetime=8h keylife=1h type=transport left=${IP} leftid=${IP} leftprotoport=17/1701 right=%any rightprotoport=17/%any dpddelay=40 dpdtimeout=130 dpdaction=clear EOF rm -f /etc/ipsec.secrets cat > /etc/ipsec.secrets<<EOF ${IP} %any: PSK "${mypsk}" EOF rm -f /etc/xl2tpd/xl2tpd.conf cat > /etc/xl2tpd/xl2tpd.conf<<EOF [global] listen-addr = ${IP} [lns default] ip range = ${iprange}.2-${iprange}.254 local ip = ${iprange}.1 require chap = yes refuse pap = yes require authentication = yes name = LinuxVPNserver ppp debug = yes pppoptfile = /etc/ppp/options.xl2tpd length bit = yes EOF rm -f /etc/ppp/options.xl2tpd cat > /etc/ppp/options.xl2tpd<<EOF ipcp-accept-local ipcp-accept-remote require-mschap-v2 ms-dns 8.8.8.8 ms-dns 8.8.4.4 noccp auth crtscts hide-password idle 1800 mtu 1410 mru 1410 nodefaultroute name l2tpd debug lock proxyarp connect-delay 5000 EOF rm -f /etc/ppp/chap-secrets cat > /etc/ppp/chap-secrets<<EOF # Secrets for authentication using CHAP # client server secret IP addresses ${username} l2tpd ${password} * EOF cp -pf /etc/sysctl.conf /etc/sysctl.conf.bak echo "# Added by L2TP VPN" >> /etc/sysctl.conf echo "net.ipv4.ip_forward=1" >> /etc/sysctl.conf echo "net.ipv4.tcp_syncookies=1" >> /etc/sysctl.conf echo "net.ipv4.icmp_echo_ignore_broadcasts=1" >> /etc/sysctl.conf echo "net.ipv4.icmp_ignore_bogus_error_responses=1" >> /etc/sysctl.conf for each in `ls /proc/sys/net/ipv4/conf/` do echo "net.ipv4.conf.${each}.accept_source_route=0" >> /etc/sysctl.conf echo "net.ipv4.conf.${each}.accept_redirects=0" >> /etc/sysctl.conf echo "net.ipv4.conf.${each}.send_redirects=0" >> /etc/sysctl.conf echo "net.ipv4.conf.${each}.rp_filter=0" >> /etc/sysctl.conf done sysctl -p cat > /usr/lib/firewalld/services/xl2tpd.xml<<EOF <?xml version="1.0" encoding="utf-8"?> <service> <short>xl2tpd</short> <description>L2TP IPSec</description> <port protocol="udp" port="4500"/> <port protocol="udp" port="1701"/> </service> EOF chmod 640 /usr/lib/firewalld/services/xl2tpd.xml systemctl enable ipsec systemctl enable xl2tpd systemctl enable firewalld systemctl status firewalld > /dev/null 2>&1 if [ $? -eq 0 ];then echo "Checking firewalld status..." firewall-cmd --list-all echo "add firewalld rules..." firewall-cmd --permanent --add-service=ipsec firewall-cmd --permanent --add-service=xl2tpd firewall-cmd --permanent --add-masquerade firewall-cmd --reload else echo "Firewalld looks like not running, trying to start..." systemctl start firewalld if [ $? -eq 0 ];then echo "Firewalld start successfully..." echo "Checking firewalld status..." firewall-cmd --list-all echo "adding firewalld rules..." firewall-cmd --permanent --add-service=ipsec firewall-cmd --permanent --add-service=xl2tpd firewall-cmd --permanent --add-masquerade firewall-cmd --reload else echo "Failed to start firewalld. please enable port 500 4500 manually if necessary." fi fi systemctl restart ipsec systemctl restart xl2tpd echo "Checking ipsec status..." systemctl -a | grep ipsec echo "Checking xl2tpd status..." systemctl -a | grep xl2tpd echo "Checking firewalld status..." firewall-cmd --list-all firewall-cmd --list-all | grep xl2tpd > /dev/null 2>&1 if [ $? -ne 0 ];then firewall-cmd --permanent --add-service=xl2tpd firewall-cmd --reload fi } finally(){ cd ${cur_dir} rm -fr ${cur_dir}/l2tp # create l2tp command cp -f ${cur_dir}/`basename $0` /usr/bin/l2tp echo "Please wait a moment..." sleep 5 ipsec verify echo echo "###############################################################" echo "# L2TP VPN Auto Installer #" echo "# System Supported: CentOS 6+ / Debian 7+ / Ubuntu 12+ #" echo "# Intro: https://teddysun.com/448.html #" echo "# Author: Teddysun <[email protected]> #" echo "###############################################################" echo "If there is no [FAILED] above, you can connect to your L2TP " echo "VPN Server with the default Username/Password is below:" echo echo "ServerIP:${IP}" echo "PSK:${mypsk}" echo "Username:${username}" echo "Password:${password}" echo echo "If you want to modify user settings, please use command(s):" echo "l2tp -a (Add a user)" echo "l2tp -d (Delete a user)" echo "l2tp -l (List all users)" echo "l2tp -m (Modify a user password)" echo echo "Welcome to visit https://teddysun.com/448.html" echo "Enjoy it!" echo } l2tp(){ clear echo echo "###############################################################" echo "# L2TP VPN Auto Installer #" echo "# System Supported: CentOS 6+ / Debian 7+ / Ubuntu 12+ #" echo "# Intro: https://teddysun.com/448.html #" echo "# Author: Teddysun <[email protected]> #" echo "###############################################################" echo rootness tunavailable disable_selinux version_check get_os_info preinstall_l2tp install_l2tp finally } list_users(){ if [ ! -f /etc/ppp/chap-secrets ];then echo "Error: /etc/ppp/chap-secrets file not found." exit 1 fi local line="+-------------------------------------------+\n" local string=%20s printf "${line}|${string} |${string} |\n${line}" Username Password grep -v "^#" /etc/ppp/chap-secrets | awk ‘{printf "|‘${string}‘ |‘${string}‘ |\n", $1,$3}‘ printf ${line} } add_user(){ while : do read -p "Please input your Username:" user if [ -z ${user} ]; then echo "Username can not be empty" else grep -w "${user}" /etc/ppp/chap-secrets > /dev/null 2>&1 if [ $? -eq 0 ];then echo "Username (${user}) already exists. Please re-enter your username." else break fi fi done pass=`rand` echo "Please input ${user}‘s password:" read -p "(Default Password: ${pass}):" tmppass [ ! -z ${tmppass} ] && pass=${tmppass} echo "${user} l2tpd ${pass} *" >> /etc/ppp/chap-secrets echo "Username (${user}) add completed." } del_user(){ while : do read -p "Please input Username you want to delete it:" user if [ -z ${user} ]; then echo "Username can not be empty" else grep -w "${user}" /etc/ppp/chap-secrets >/dev/null 2>&1 if [ $? -eq 0 ];then break else echo "Username (${user}) is not exists. Please re-enter your username." fi fi done sed -i "/^\<${user}\>/d" /etc/ppp/chap-secrets echo "Username (${user}) delete completed." } mod_user(){ while : do read -p "Please input Username you want to change password:" user if [ -z ${user} ]; then echo "Username can not be empty" else grep -w "${user}" /etc/ppp/chap-secrets >/dev/null 2>&1 if [ $? -eq 0 ];then break else echo "Username (${user}) is not exists. Please re-enter your username." fi fi done pass=`rand` echo "Please input ${user}‘s new password:" read -p "(Default Password: ${pass}):" tmppass [ ! -z ${tmppass} ] && pass=${tmppass} sed -i "/^\<${user}\>/d" /etc/ppp/chap-secrets echo "${user} l2tpd ${pass} *" >> /etc/ppp/chap-secrets echo "Username ${user}‘s password has been changed." } # Main process action=$1 if [ -z ${action} ] && [ "`basename $0`" != "l2tp" ]; then action=install fi case ${action} in install) l2tp 2>&1 | tee /root/l2tp.log ;; -l|--list) list_users ;; -a|--add) add_user ;; -d|--del) del_user ;; -m|--mod) mod_user ;; -h|--help) echo "Usage: `basename $0` -l,--list List all users" echo " `basename $0` -a,--add Add a user" echo " `basename $0` -d,--del Delete a user" echo " `basename $0` -m,--mod Modify a user password" echo " `basename $0` -h,--help Print this help information" ;; *) echo "Usage: `basename $0` [-l,--list|-a,--add|-d,--del|-m,--mod|-h,--help]" && exit ;; esac
转载请注明:秋水逸冰 L2TP/IPSec一键安装脚本
本文出自 “RichyLu____记录” 博客,请务必保留此出处http://richylu.blog.51cto.com/1481674/1893986
以上是关于L2TP/IPSec一键安装脚本的主要内容,如果未能解决你的问题,请参考以下文章