Sysmon + NXlog构建简单的windows安全监控
Posted 安全工搬砖笔记
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了Sysmon + NXlog构建简单的windows安全监控相关的知识,希望对你有一定的参考价值。
工具:
Sysmon (sysmon 5.0) ,NXlog(nxlog-ce-2.9.1716.msi) .
Sysmon监控系统并生成windows event log, NXlog将windows event log传输到syslog服务器。
Sysmon可以监控Process create, Process terminate, Driver loaded, File creation time changed, RawAccessRead, CreateRemoteThread, Sysmon service state changed。
配置:
NXlog配置:
## This is a sample configuration file. See the nxlog reference manual about the
## configuration options. It should be installed locally and is also available
## online at http://nxlog.org/docs/
## Please set the ROOT to the folder your nxlog was installed into,
## otherwise it will not start.
#define ROOT C:\\Program Files\\nxlog
define ROOT C:\\Program Files (x86)\\nxlog
Moduledir %ROOT%\\modules
CacheDir %ROOT%\\data
Pidfile %ROOT%\\data\\nxlog.pid
SpoolDir %ROOT%\\data
LogFile %ROOT%\\data\\nxlog.log
<Extension _syslog>
Module xm_syslog
</Extension>
<Input in>
Module im_msvistalog
Query <QueryList> <Query Id="0"> <Select Path="Microsoft-Windows-Sysmon/Operational">*</Select> </Query></QueryList>
</Input>
<Output out>
Module om_udp
Host security-log.syslogserver.com
Port 639
Exec to_syslog_snare();
</Output>
<Route 1>
Path in => out
</Route>
Sysmon配置:
<Sysmon schemaversion="3.20">
<!-- Capture all hashes -->
<HashAlgorithms>*</HashAlgorithms>
<EventFiltering>
<!-- Log all drivers except if the signature -->
<!-- contains Microsoft or Windows -->
<DriverLoad onmatch="exclude">
<Signature condition="contains">Microsoft</Signature>
<Signature condition="contains">Windows</Signature>
</DriverLoad>
<ProcessTerminate onmatch="include" >
<Image condition="end with">MsMpEng.exe</Image>
</ProcessTerminate>
<!-- Log network connection if the destination port equal 443 -->
<!-- or 80, and process isn\'t InternetExplorer -->
<!--NetworkConnect onmatch="include">
<DestinationPort>443</DestinationPort>
<DestinationPort>80</DestinationPort >
</NetworkConnect -->
<FileCreateTime onmatch="exclude" >
<Image condition="end with">chrome.exe</Image>
</FileCreateTime>
<ImageLoad onmatch="include">
<Signed condition="is">false</Signed>
</ImageLoad>
<!-- Log access rights for lsass.exe or winlogon.exe is not PROCESS_QUERY_INFORMATION -->
<ProcessAccess onmatch="exclude">
<GrantedAccess condition="is">0x1400</GrantedAccess>
</ProcessAccess>
<ProcessAccess onmatch="include">
<TargetImage condition="end with">lsass.exe</TargetImage>
<TargetImage condition="end with">winlogon.exe</TargetImage>
</ProcessAccess>
<NetworkConnect onmatch="exclude">
<Image condition="end with">chrome.exe</Image>
<SourcePort condition="is">137</SourcePort>
<SourcePortName condition="is">llmnr</SourcePortName>
<DestinationPortName condition="is">llmnr</DestinationPortName>
</NetworkConnect>
<CreateRemoteThread onmatch="include">
<TargetImage condition="end with">explorer.exe</TargetImage>
<TargetImage condition="end with">svchost.exe</TargetImage>
<TargetImage condition="end with">winlogon.exe</TargetImage>
<SourceImage condition="end with">powershell.exe</SourceImage>
</CreateRemoteThread>
</EventFiltering>
</Sysmon>
测试案例:
安装:
- sysmon -i config.conf 。
- nxlog双击运行,记得启动服务。(NXlog可命令行安装 msiexec /i nxlog-ce-2.9.1716.msi AGREETOLIECENSE="yes" ACCEPT=YES /qr+)
使用mimikatz抓取hash:
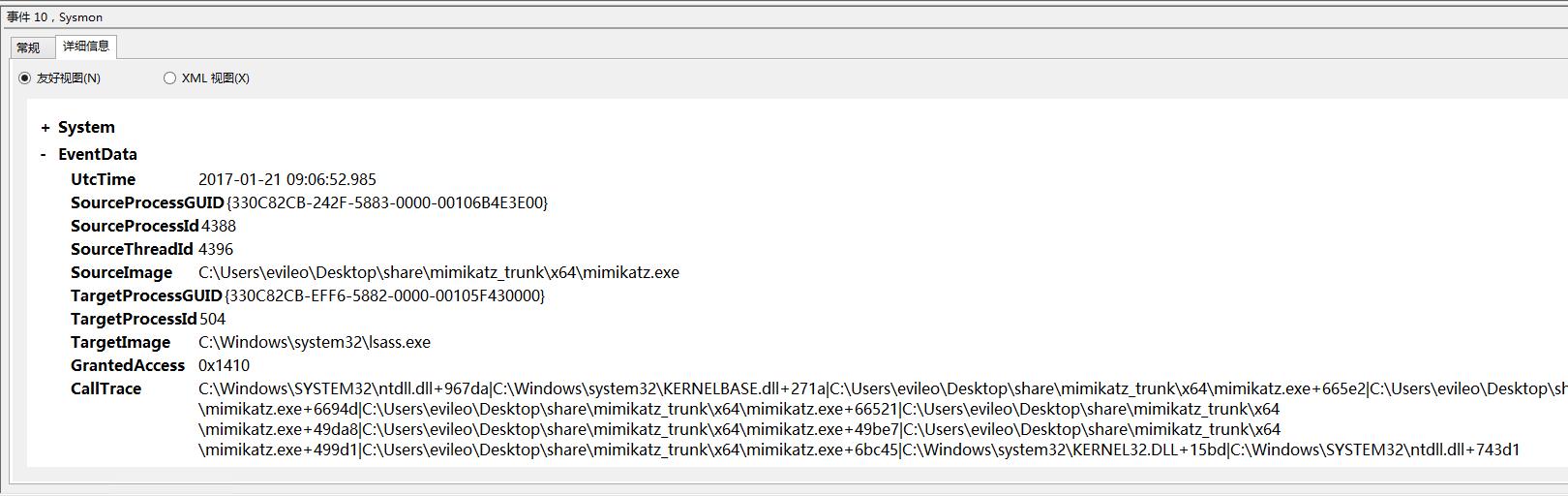
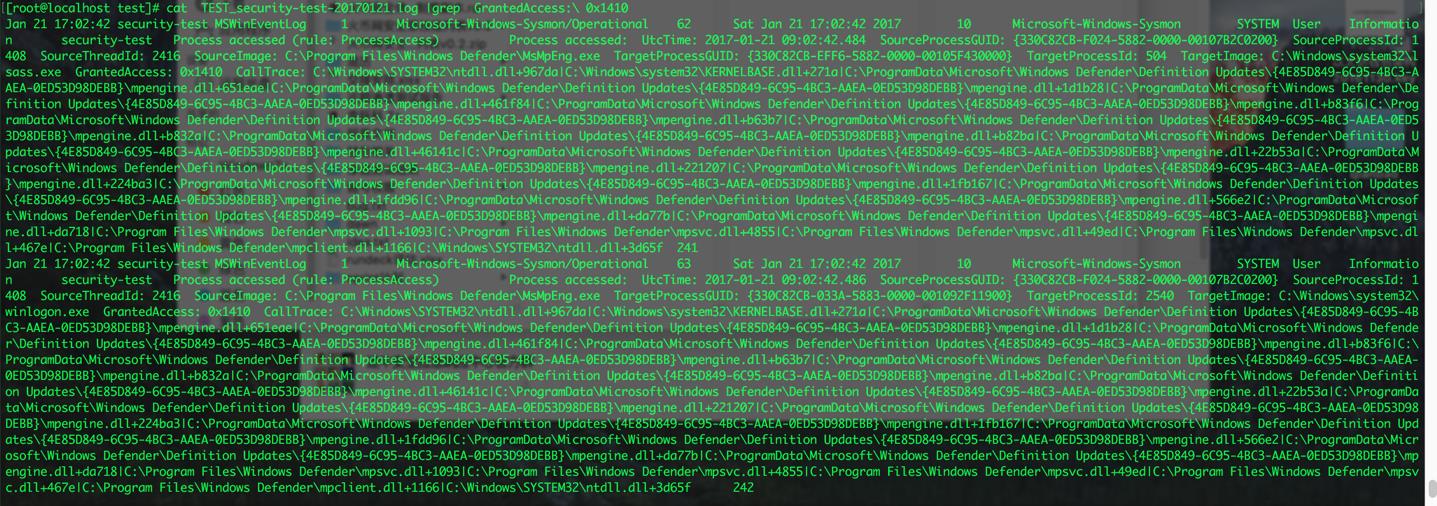
附NXlog完整配置样例:
## This is a basic configuration file for Windows Server 2008 * 2012 ## to GrayLog2 with GELF support and filtering. ## See the nxlog reference manual about the configuration options. ## It should be installed locally and is also available ## online at http://nxlog.org/nxlog-docs/en/nxlog-reference-manual.html ## Please set the ROOT to the folder your nxlog was installed into, ## otherwise it will not start. define ROOT C:\\Program Files (x86)\\nxlog # define ROOT C:\\Program Files\\nxlog Moduledir %ROOT%\\modules CacheDir %ROOT%\\data Pidfile %ROOT%\\data\\nxlog.pid SpoolDir %ROOT%\\data LogFile %ROOT%\\data\\nxlog.log <Extension gelf> Module xm_gelf </Extension> <Input pr_mseventlog> Module im_msvistalog ReadFromLast True # http://msdn.microsoft.com/en-us/library/aa385231.aspx # http://msdn.microsoft.com/en-us/library/ff604025(v=office.14).aspx # Level 1 (ID=30 Critical) severity level events # Level 2 (ID=40 Error) severity level events # Level 3 (ID=50 Warning) severity level events # Level 4 (ID=80 Information) severity level events # Level 5 (ID=100 Verbose) severity level events # All channels are included by default which are listed in the registry under these: # HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\WINEVT\\Channels # HKEY_LOCAL_MACHINE\\SYSTEM\\CurrentControlSet\\services\\eventlog\\System # # <Select Path=\'Key Management Service\'>*</Select></Query>\\ # <Select Path=\'Internet Explorer\'>*</Select></Query>\\ # <Select Path=\'HardwareEvents\'>*</Select></Query>\\ # Query <QueryList>\\ <Query Id="0">\\ <Select Path="Security">*</Select>\\ <Select Path="System">*[System/Level=4]</Select>\\ <Select Path="Application">*[Application/Level=2]</Select>\\ <Select Path="Setup">*[System/Level=3]</Select>\\ <Select Path=\'Windows PowerShell\'>*</Select>\\ </Query>\\ </QueryList> # REGEX EXAMPLES: # "\\s" equals one white space character, and ".*" equals any one char # Line Contains both "bubble" and "gum" # Search pattern: ^(?=.*?\\bbubble\\b)(?=.*?\\bgum\\b).* # Line does Not Contain "boy" # Search pattern: ^(?!.*boy).* # Line Contains "bubble" but Neither "gum" Nor "bath" # Search pattern: ^(?=.*bubble)(?!.*gum)(?!.*bath).* # Uncomment next line to view all logs, we can view output to help # create the regex, next line shows my $raw_event data to parse: # 2013-11-18 15:23:02 INFO 2013-12-18 15:23:01 ahost.adomain.local INFO 62464 UVD Information # Exec log_info($raw_event) ; Exec if ($raw_event =~ /INFO\\s+62464/) drop(); </Input> <Output out> Module om_udp Host 10.247.x.x Port 12201 OutputType GELF </Output> <Route 1> Path pr_mseventlog => out </Route>
参考:
http://www.freebuf.com/sectool/122779.html
https://technet.microsoft.com/en-us/sysinternals/dn798348
https://nxlog.co/docs/sysmon/audit-logging-on-windows-with-sysmon-and-nxlog.html
http://www.ilanni.com/?p=595
以上是关于Sysmon + NXlog构建简单的windows安全监控的主要内容,如果未能解决你的问题,请参考以下文章