2016-10-23 第九周作业
Posted
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了2016-10-23 第九周作业相关的知识,希望对你有一定的参考价值。
1、详细描述一次加密通讯的过程,结合图示最佳。
SSL协议基础: SSL协议位于TCP/IP协议与各种应用层协议之间,本身又分为两层: 1)SSL记录协议:建立在可靠传输层协议(TCP)之上,为上层协议提供数据封装、压缩、加密等基本功能。 2)SSL握手协议:在SSL记录协议之上,用于实际数据传输前,通讯双方进行身份认证、协商加密算法、交换加密密钥等。 SSL协议通信过程: 1)浏览器发送一个连接请求给服务器;服务器将自己的证书(包含服务器公钥S_PuKey)、对称加密算法种类及其他相关信息返回客户端。 2)客户端浏览器检查服务器传送到CA证书是否由自己信赖的CA中心签发。若是,执行第4步;否则,给客户一个警告信息:询问是否继续访问 3)客户端浏览器比较证书里的信息,如证书有效期、服务器域名和公钥S_PK,与服务器传回的信息是否一致;如果一致,则浏览器完成对服务器的身份认证 4)服务器要求客户端发送客户端证书(包含客户端公钥C_PuKey)、支持的对称加密方案及其他相关信息。收到后,服务器进行相同的身份认证,若没有通过验证,则拒绝连接; 5)服务器根据客户端浏览器发送到密码种类,选择一种加密程度最高的方案,用客户端公钥C_PubKey加密后通知到浏览器; 6)客户端通过私钥C_prKey解密后,得知服务器选择的加密方案,并选择一个通话密钥Key,接着用服务器公钥S_PuKey加密后发送服务器; 7)服务器接收到的浏览器传送到消息,用私钥S_PrKey解密,获得通话密钥key。 8)接下来的数据传输都使用该对称密钥Key进行加密。 上面所述的是双向认证SSL协议的具体通讯过程,服务器和用户双方必须都有证书。由此可见,SSL协议是通过非对称密钥机制保证双方身份认证,并完成建立连接,在实际数据通信 时通过对称密钥机制保障数据安全性。
2、描述创建私有CA的过程,以及为客户端发来的证书请求进行办法证书。
配置文件:/etc/pki/tls/openssl.cnf 1)创建所需要的文件 [[email protected] ~]# cd /etc/pki/CA [[email protected] CA]# touch index.txt [[email protected] CA]# echo 01 > serial 2)CA自签证书 [[email protected] CA]# (umask 077;openssl genrsa -out private/cakey.pem 2048) [[email protected] CA]# openssl req -new -x509 -key private/cakey.pem -days 7300 -out cacert.pem -new:生成新证书签署请求; -x509:专用于CA生成自签证书; -key:生成请求时用到的私钥文件; -days n:证书的有效期限; -out /PATH/TO/SOMECERTFILE:证书的保存路径 3)发证 (a)客户端生成证书请求 [[email protected] ~]# mkdir /etc/httpd/ssl [[email protected] ~]# (umask 077;openssl genrsa -out /etc/httpd/ssl/httpd.key 2048) [[email protected] ~]# cd /etc/httpd/ssl/ [[email protected] ssl]# openssl req -new -key httpd.key -days 365 -out httpd.csr (b)把请求文件传输给CA [[email protected] ssl]# scp httpd.csr 192.168.11.161:/tmp/ (c)CA签署证书,并将证书发还给请求者 [[email protected] CA]# openssl ca -in /tmp/httpd.csr -out /etc/pki/CA/certs/httpd.crt -days 365 [[email protected] CA]# scp /etc/pki/CA/certs/httpd.crt 192.168.11.162:/etc/httpd/ssl/
3、搭建一套DNS服务器,负责解析magedu.com域名(自行设定主机名及IP)
(1)、能够对一些主机名进行正向解析和逆向解析;
(2)、对子域cdn.magedu.com进行子域授权,子域负责解析对应子域中的主机名;
(3)、为了保证DNS服务系统的高可用性,请设计一套方案,并写出详细的实施过程
[[email protected] ~]# yum -y install bind 常用的配置文件有: /etc/named.conf #主配置文件 /etc/named.rfc1912.zones #区域配置文件 /etc/rc.d/init.d/named #启动脚本 /var/named #存放区域数据文件 [[email protected] ~]# vim /etc/named.conf options { listen-on port 53 { any; }; listen-on-v6 port 53 { ::1; }; directory "/var/named"; dump-file "/var/named/data/cache_dump.db"; statistics-file "/var/named/data/named_stats.txt"; memstatistics-file "/var/named/data/named_mem_stats.txt"; allow-query { any; }; recursion yes; // dnssec-enable yes; // dnssec-validation yes; /* Path to ISC DLV key */ bindkeys-file "/etc/named.iscdlv.key"; managed-keys-directory "/var/named/dynamic"; }; logging { channel default_debug { file "data/named.run"; severity dynamic; }; }; zone "." IN { type hint; file "named.ca"; }; include "/etc/named.rfc1912.zones"; listen-on port 53 { any; }; 表示监听本地IP的53端口,允许所用地址访问本地53端口 allow-query { any; }; 允许所有地址查询 recursion yes; 是否递归,如果是no那么这台DNS服务器将不会递归解析,yes或注释掉不写,表是允许,默认是允许的 include "/etc/named.rfc1912.zones"; 加载区域配置文件 正向和反向区域解析 [[email protected] ~]# vim /etc/named.rfc1912.zones 在配置文件的末尾添加正向和反向配置 zone "magedu.com" IN { type master; file "magedu.com.zone"; allow-transfer { 192.168.11.165; }; }; zone "11.168.192.in-addr.arpa" IN { type master; file "11.168.192.zone"; allow-transfer { 192.168.11.165; }; }; allow-transfer { 192.168.11.165; };表示只允许192.168.11.165这个主机同步数据,也就是作它的辅助DNS,多个IP用“;”隔开; 编辑正向解析的zone文件 [[email protected] ~]# vim /var/named/magedu.com.zone $TTL 86400 $ORIGIN magedu.com. @ IN SOA ns1.magedu.com. admin.magedu.com. ( 2016092101 1H 5M 7D 1D ) IN NS ns1 IN NS ns2 IN MX 10 mx1 IN MX 20 mx2 IN A 192.168.11.164 ns1 IN A 192.168.11.164 ns2 IN A 192.168.11.165 mx1 IN A 192.168.11.166 mx2 IN A 192.168.11.167 www IN A 192.168.11.164 www IN A 192.168.11.165 ftp IN CNAME www 反向解析zone文件 [[email protected] ~]# vim /var/named/11.168.192.zone $TTL 86400 $ORIGIN 1.168.192.in-addr.arpa. @ IN SOA ns1.magedu.com. admin.magedu.com. ( 2016092101 1H 5M 7D 1D ) IN NS ns1.magedu.com. IN NS ns2.magedu.com. 64 IN PTR ns1.magedu.com. 65 IN PTR ns2.magedu.com. 66 IN PTR mx1.magedu.com. 67 IN PTR mx2.magedu.com. 64 IN PTR www.magedu.com. 65 IN PTR www.magedu.com. [[email protected] ~]# service named start 正向解析: [[email protected] ~]# dig @192.168.11.164 www.magedu.com ; <<>> DiG 9.8.2rc1-RedHat-9.8.2-0.47.rc1.el6 <<>> @192.168.11.161 www.magedu.com ; (1 server found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 54957 ;; flags: qr aa rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 2, ADDITIONAL: 2 ;; QUESTION SECTION: ;www.magedu.com. IN A ;; ANSWER SECTION: www.magedu.com. 86400 IN A 192.168.11.164 www.magedu.com. 86400 IN A 192.168.11.165 ;; AUTHORITY SECTION: magedu.com. 86400 IN NS ns1.magedu.com. magedu.com. 86400 IN NS ns2.magedu.com. ;; ADDITIONAL SECTION: ns1.magedu.com. 86400 IN A 192.168.11.164 ns2.magedu.com. 86400 IN A 192.168.11.165 ;; Query time: 0 msec ;; SERVER: 192.168.11.161#53(192.168.11.164) ;; WHEN: Sat Oct 22 21:15:11 2016 ;; MSG SIZE rcvd: 132 反向解析 [[email protected] ~]# dig -x 192.168.11.164 @192.168.11.164 ; <<>> DiG 9.8.2rc1-RedHat-9.8.2-0.47.rc1.el6 <<>> -x 192.168.11.164 ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 23623 ;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 2, ADDITIONAL: 2 ;; QUESTION SECTION: ;64.1.168.192.in-addr.arpa. IN PTR ;; ANSWER SECTION: 64.1.168.192.in-addr.arpa. 86400 IN PTR ns1.magedu.com. ;; AUTHORITY SECTION: 1.168.192.in-addr.arpa. 86400 IN NS ns2.magedu.com. 1.168.192.in-addr.arpa. 86400 IN NS ns1.magedu.com. ;; ADDITIONAL SECTION: ns1.magedu.com. 86400 IN A 192.168.11.164 ns2.magedu.com. 86400 IN A 192.168.11.165 ;; Query time: 0 msec ;; SERVER: 192.168.11.164#53(192.168.11.164) ;; WHEN: Sat Oct 22 21:56:14 2016 ;; MSG SIZE rcvd: 135 配置主从同步 [[email protected] ~]# vim /etc/named.rfc1912.zones 在末尾添加 zone "magedu.com" IN { type slave; masters { 192.168.11.164; }; file "slaves/magedu.com.zone"; allow-transfer { none; }; }; zone "11.168.192.in-addr.arpa" IN { type slave; masters { 192.168.11.164; }; file "slaves/11.168.192.zone"; allow-transfer { none; }; }; 批定type类型为slave,并指定主服务器为192.168.11.64 [[email protected] ~]# service named start 服务启动后,会在/var/named/slaves/自动添加magedu.com.zone和11.168.192.zone文件 [[email protected] ~]# ll /var/named/slaves/ 总用量 8 -rw-r--r-- 1 named named 436 10月 22 22:13 11.168.192.zone -rw-r--r-- 1 named named 502 10月 22 22:13 magedu.com.zone 子域授权 新增一台IP为192.168.1.61的服务器为子域 在父域的区域文件中添加NS和A记录 [[email protected] ~]# vim /var/named/magedu.com.zone 添加 cdn IN NS ns1.cdn.magedu.com. ns1.cdn IN A 192.168.11.161 [[email protected] ~]# yum -y install bind [[email protected] ~]# scp 192.168.11.164:/etc/named.conf /etc/ [[email protected] ~]# vim /etc/named.rfc1912.zones 在末尾添加 zone "cdn.magedu.com" IN { type master; file "cdn.magedu.com.zone"; }; zone "magedu.com" IN { type forward; forward only; forwarders { 192.168.11.164; }; }; [[email protected] ~]# vim /var/named/cdn.magedu.com.zone $TTL 86400 @ IN SOA ns.cdn.magedu.com. admin.cdn.magedu.com. ( 2016092201 2H 5M 7D 12H ) IN NS ns.cdn.magedu.com. IN MX 10 mx1.cdn.magedu.com. IN A 192.168.11.61 ns IN A 192.168.11.161 mx1 IN A 192.168.11.161 www IN A 192.168.11.161 测试 1)子域测试 [[email protected] ~]# dig @192.168.11.161 www.cdn.magedu.com ; <<>> DiG 9.8.2rc1-RedHat-9.8.2-0.47.rc1.el6 <<>> @192.168.11.165 www.cdn.magedu.com ; (1 server found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 33720 ;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 1, ADDITIONAL: 1 ;; QUESTION SECTION: ;www.cdn.magedu.com. IN A ;; ANSWER SECTION: www.cdn.magedu.com. 86400 IN A 192.168.11.161 ;; AUTHORITY SECTION: cdn.magedu.com. 86400 IN NS ns.cdn.magedu.com. ;; ADDITIONAL SECTION: ns.cdn.magedu.com. 86400 IN A 192.168.11.161 ;; Query time: 0 msec ;; SERVER: 192.168.11.165#53(192.168.11.161) ;; WHEN: Sat Oct 22 22:16:44 2016 ;; MSG SIZE rcvd: 85 2)父域测试 [[email protected] ~]# dig -t www.magedu.com ;; Warning, ignoring invalid type www.magedu.com ; <<>> DiG 9.8.2rc1-RedHat-9.8.2-0.47.rc1.el6 <<>> -t www.magedu.com ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 27354 ;; flags: qr rd ra; QUERY: 1, ANSWER: 13, AUTHORITY: 0, ADDITIONAL: 0 ;; QUESTION SECTION: ;. IN NS ;; ANSWER SECTION: . 518239 IN NS b.root-servers.net. . 518239 IN NS i.root-servers.net. . 518239 IN NS j.root-servers.net. . 518239 IN NS k.root-servers.net. . 518239 IN NS l.root-servers.net. . 518239 IN NS e.root-servers.net. . 518239 IN NS h.root-servers.net. . 518239 IN NS f.root-servers.net. . 518239 IN NS c.root-servers.net. . 518239 IN NS m.root-servers.net. . 518239 IN NS d.root-servers.net. . 518239 IN NS a.root-servers.net. . 518239 IN NS g.root-servers.net. ;; Query time: 0 msec ;; SERVER: 192.168.1.61 #53(192.168.11.165) ;; WHEN: Sat Oct 22 22:18:26 2016 ;; MSG SIZE rcvd: 228
4、请描述一次完整的http请求处理过程;
(1) 建立或处理连接:接收客户端的请求,建立连接,或是拒绝其请求 (2) 接收请求: 接收来自于网络的请求报文中对某资源的一次请求的过程时,web服务器也分几种模型对并发请求进行响应: a. 单进程I/O结构:启动一个进程处理用户请求,而且一次只处理一个;多个请求被串行响应;实质就是排队机制,第一个用户的请求处理完再处理第二个,其它排队等待。这种方式串行执行,效率不高。 b. 多进程I/O结构:并行启动多个进程,每个进程响应一个请求; c. 复用I/O结构:一个进程响应n个请求; d. 多线程模型:一个进程生成N个线程,每个线程响应一个用户请求; e. 复用的多进程I/O结构:启动多个(m)进程,每个进程响应n个请求;此模式实质上为事件驱动:event-driven,效率最高。 (3) 处理请求:对请求报文进行解析,并获取请求的资源及请求方法等相关信息 (4) 访问资源:获取请求报文中请求的资源 (5) 拿到需要的资源之后,就会构建响应报文,准备向用户回复 (6) 发送响应报文,回复请求 (7) 记录日志:对每个请求资源,详细记录访问日志信息,以便于以后的安全审查或数据分析。 以上就是一次完整的http请求的处理过程。
5、httpd所支持的处理模型有哪些,他们的分别使用于哪些环境。
httpd所支持的事务处理模型主要有: prefork worker event 他们分别使用于以下场景:、 prefork: 多进程模型,每个进程负责响应一个请求。prefork模型在工作时,由一个主进程负责生成n个子进程,即工作进程。每个工作进程 响应一个用户请求,即使当前没有用户请求,它亦会预先生成多个空闲进程,随时等待请求连接,这样的好处是,服务器不用等到请求到达时, 才去临时建立进程,缩短了进程创建的时间。提高连接效率。但受限于linux的特性,工作进程数上限为1024个,如超出该数量,服务器性能会急剧降低。 因而,prefork模型的最大并发连接数量最大为1024。由于每个工作进程相对独立,就算崩溃了,也不会对其它进程有明显影响。所以,该模型的特点是稳定可靠, 适合于并发量适中而又追求稳定的用户使用。 worker:多线程模型,每个线程响应一个请求。worker模型在工作时,也有一个主进程负责生成多个子进程,同时每个子进程负责生个多个线程,每个线程响应一个用户 请求。同理,worker模型也会预先创建一些空闲线程来等待用户连接。并发连接数,如果生成进程数为m,线程为n,则并发数可达到m*n个。但由于在linux中,原生不支持 线程,且进程本身就足够轻量化,与线程的区别不是十分巨大,因而,worker模型在linux环境中的实际性能表现与prefork相差无几。 event:事件驱动模型,每个线程响应n个用户请求。event模型工作时,由主进程生成m个子进程,每个单独的子进程可响应n个用户请求。因而,event的并发数量可达到m*n 个,同时,因为event的子进程为一对多,节省了大量CPU进程间切换上下文的时间,也没有了linux系统的1024个进程限制,所以,event模型是三种模型中效率最高的一种。 可以实破c10k的限制(即并发数1w),对海量并发的系统特别适用。
6、建立httpd服务器(基于编译的方式进行),要求:
提供两个基于名称的虚拟主机:
(a)www1.stuX.com,页面文件目录为/web/vhosts/www1;错误日志为/var/log/httpd/www1.err,访问日志为/var/log/httpd/www1.access;
(b)www2.stuX.com,页面文件目录为/web/vhosts/www2;错误日志为/var/log/httpd/www2.err,访问日志为/var/log/httpd/www2.access;
(c)为两个虚拟主机建立各自的主页文件index.html,内容分别为其对应的主机名;
(d)通过www1.stuX.com/server-status输出httpd工作状态相关信息,且只允许提供帐号密码才能访问(status:status);
编译安装httpd 首先编译apr apache portable runtime, [[email protected] LAMP]# cd apr-1.5.2/ [[email protected] apr-1.5.2]# ./configure –prefix=/usr/local/apr [[email protected] apr-1.5.2]# make && make install 然后编译apr-util [[email protected] LAMP]# cd apr-util-1.5.4/ [[email protected] apr-util-1.5.4]# ./configure –prefix=/usr/local/apr-util –with-apr=/usr/local/apr [[email protected] apr-util-1.5.4]# make && make install 开始编译httpd2.4.16 [[email protected] LAMP]# cd httpd-2.4.16/ [[email protected] httpd-2.4.16]# groupadd -r apache [[email protected] httpd-2.4.16]# useradd -r -g apache apache ##mpm选择prefork方式,编译安装 [[email protected] httpd-2.4.16]# ./configure –prefix=/usr/local/apache –sysconf=/etc/httpd24 –enable-so –enable-ssl –enable-cgi –enable-rewrite –with-zlib –with-pcre –with-apr=/usr/local/apr –with-apr-util=/usr/local/apr-util/ –enable-modules=most –enable-mpms-shared=all –with-mpm=prefork [[email protected] httpd-2.4.16]# make && make install ##关闭selinux [[email protected] bin]# setenforce 0 [[email protected] bin]# getenforce Permissive ##关闭防火墙 [[email protected] selinux]# systemctl stop firewalld.service [[email protected] selinux]# systemctl disable firewalld.service Removed symlink /etc/systemd/system/dbus-org.fedoraproject.FirewallD1.service. Removed symlink /etc/systemd/system/basic.target.wants/firewalld.service. [[email protected] selinux]# ##将apache的bin加入PATH变量中 [[email protected] profile.d]# vim /etc/profile.d/httpd.sh PATH=$PATH:/usr/local/apache/bin ##输出头文件 [[email protected] apache]# ln -sv /usr/local/apache/include/ /usr/include/apache a/usr/include/apachea -> a/usr/local/apache/include/a [[email protected] apache]# ##检查帮助文件 [[email protected] etc]# vim man_db.conf MANDB_MAP /usr/local/apache/man ##启动apache [[email protected] httpd]# apachectl start [[email protected] httpd]# ss -ntlp | grep :80 LISTEN 0 128 :::80 :::* users:(("httpd",pid=26283,fd=4),("httpd",pid=26282,fd=4),("httpd",pid=26281,fd=4),("httpd",pid=26280,fd=4)) ##配置网站,添加两个虚拟主机 [[email protected] httpd]# vim /etc/httpd/httpd.conf ##禁用主站的目录 #DocumentRoot "/usr/local/apache/htdocs" ##启用虚拟主机 # Virtual hosts Include /etc/httpd/extra/httpd-vhosts.conf ##测试配置 [[email protected] httpd]# httpd -t AH00112: Warning: DocumentRoot [/web/vhosts/www1] does not exist AH00112: Warning: DocumentRoot [/web/vhosts/www2] does not exist (2)No such file or directory: AH02291: Cannot access directory ‘/var/log/httpd/‘ for error log of vhost defined at /etc/httpd/extra/httpd-vhosts.conf:48 (2)No such file or directory: AH02291: Cannot access directory ‘/var/log/httpd/‘ for error log of vhost defined at /etc/httpd/extra/httpd-vhosts.conf:41 AH00014: Configuration check failed [[email protected] httpd]# ##建好相应的目录 [[email protected] httpd]# mkdir -pv /web/vhosts/{www1,www2} mkdir: created directory a/weba mkdir: created directory a/web/vhostsa mkdir: created directory a/web/vhosts/www1a mkdir: created directory a/web/vhosts/www2 [[email protected] httpd]# mkdir /var/log/httpd -pv mkdir: created directory a/var/log/httpda ##编辑httpd.conf主配置文件,添加两个虚拟主机目录的访问权限 [[email protected] httpd]# vim /etc/httpd/httpd.conf ############################### <Directory "/web/vhosts/www1"> options none allowoverride none Require all granted </Directory> <Directory "/web/vhosts/www2"> options none allowoverride none Require all granted </Directory> ############################### ##编辑httpd-vhosts.conf文件,添加以下内容 [[email protected] extra]# vim /etc/httpd/extra/httpd-vhosts.conf <VirtualHost *:80> DocumentRoot "/web/vhosts/www1" ServerName www1.stuX.com ErrorLog "/var/log/httpd/www1.err" CustomLog "/var/log/httpd/www1.access" common </VirtualHost> <VirtualHost *:80> DocumentRoot "/web/vhosts/www2" ServerName www2.stuX.com ErrorLog "/var/log/httpd/www2.err" CustomLog "/var/log/httpd/www2.cacess" common </VirtualHost> [[email protected] httpd]# [[email protected] httpd]# httpd -t Syntax OK ##重启服务 [[email protected] httpd]# apachectl stop [[email protected] httpd]# apachectl start [[email protected] httpd]# ##构建网站主页文件 [[email protected] www2]# vim /web/vhosts/www1/index.html <h1>www1.stuX.com</h1> [[email protected] www2]# vim /web/vhosts/www2/index.html <h1>www2.stuX.com</h1> ##在其它电脑访问这台主机,检验网站能否正常工作 [[email protected] httpd]# curl http://www1.stuX.com <h1>www1.stuX.com</h1> [[email protected] httpd]# curl http://www2.stuX.com <h1>www2.stuX.com</h1> [[email protected] httpd]# ##构建Server-Status设置 ##在www1.stuX.com里,增加server-status的设置,具体内容如下: <VirtualHost *:80> DocumentRoot "/web/vhosts/www1" ServerName www1.stuX.com ErrorLog "/var/log/httpd/www1.err" CustomLog "/var/log/httpd/www1.access" common <Location /server-status> SetHandler server-status AuthType Basic AuthName "Server-Status" AuthUserFile "/etc/httpd/.htpasswd" Require valid-user </Location> </VirtualHost> ##生成.htpasswd密码验证文件 [[email protected] httpd]# htpasswd -c -m .htpasswd status New password: Re-type new password: Adding password for user status ##重启服务后访问验证
7、为第6题中的第2个虚拟主机提供https服务,使得用户可以通过https安全的访问此web站点;
(1)要求使用证书认证,证书中要求使用的国家(CN)、州(HA)、城市(ZZ)和组织(MageEdu);
(2)设置部门为Ops,主机名为www2.stuX.com,邮件为[email protected];
##演示目的,CA与Web在同一主机上 [[email protected] CA]# touch index.txt [[email protected] CA]# echo 01 > serial [[email protected] CA]# [[email protected] CA]# (umask 077; openssl genrsa -out /etc/pki/CA/private/cakey.pem 2048) Generating RSA private key, 2048 bit long modulus ………………………………………+++ …………………………………………………………………………………………………+++ e is 65537 (0x10001) [[email protected] CA]# openssl req -new -x509 -key /etc/pki/CA/private/cakey.epm -days 7300 -out /etc/pki/CA/cacert.pem Error opening Private Key /etc/pki/CA/private/cakey.epm 140239236687776:error:02001002:system library:fopen:No such file or directory:bss_file.c:398:fopen(‘/etc/pki/CA/private/cakey.epm‘,‘r‘) 140239236687776:error:20074002:BIO routines:FILE_CTRL:system lib:bss_file.c:400: unable to load Private Key [[email protected] CA]# openssl req -new -x509 -key /etc/pki/CA/private/cakey.pem -days 7300 -out /etc/pki/CA/cacert.pem You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter ‘.‘, the field will be left blank. —– Country Name (2 letter code) [XX]:CN State or Province Name (full name) []:HA Locality Name (eg, city) [Default City]:ZZ Organization Name (eg, company) [Default Company Ltd]:MageEdu Organizational Unit Name (eg, section) []:Ops Common Name (eg, your name or your server‘s hostname) []:ca.stuX.com Email Address []:[email protected] [[email protected] CA]# [[email protected] CA]# cd /etc/httpd/ [[email protected] httpd]# mkdir ssl [[email protected] httpd]# (umask 077; openssl genrsa -out /etc/httpd/ssl/httpd.key 2048) Generating RSA private key, 2048 bit long modulus ……………………………………………………………………………………………………………………………………………………………………………+++ ………………………………………………………………………………………………………………………………+++ e is 65537 (0x10001) [[email protected] httpd]# openssl req -new -key /etc/httpd/ssl/httpd.key -days 365 -out /etc/httpd/ssl/httpd.csr You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter ‘.‘, the field will be left blank. —– Country Name (2 letter code) [XX]:CN State or Province Name (full name) []:HA Locality Name (eg, city) [Default City]:ZZ Organization Name (eg, company) [Default Company Ltd]:MageEdu Organizational Unit Name (eg, section) []:Ops Common Name (eg, your name or your server‘s hostname) []:www2.stuX.com Email Address []:[email protected] Please enter the following ‘extra‘ attributes to be sent with your certificate request A challenge password []: An optional company name []: [[email protected] httpd]# [[email protected] httpd]# openssl ca -in /etc/httpd/ssl/httpd.csr -out /etc/pki/CA/certs/httpd.crt -days 365 Using configuration from /etc/pki/tls/openssl.cnf Check that the request matches the signature Signature ok Certificate Details: Serial Number: 1 (0x1) Validity Not Before: Oct 23 10:01:20 2016 GMT Not After : Oct 23 10:01:20 2017 GMT Subject: countryName = CN stateOrProvinceName = HA organizationName = MageEdu organizationalUnitName = Ops commonName = www2.stuX.com emailAddress = [email protected] X509v3 extensions: X509v3 Basic Constraints: CA:FALSE Netscape Comment: OpenSSL Generated Certificate X509v3 Subject Key Identifier: AB:81:27:C8:00:58:44:0E:56:5C:AD:2D:10:4F:5C:0B:02:29:A8:BB X509v3 Authority Key Identifier: keyid:37:98:CA:7C:F9:75:5B:5A:40:4F:95:28:7B:7D:BB:25:BB:26:FC:5B Certificate is to be certified until Oct 23 10:01:20 2017 GMT (365 days) Sign the certificate? [y/n]:y 1 out of 1 certificate requests certified, commit? [y/n]y Write out database with 1 new entries Data Base Updated [[email protected] httpd]# [[email protected] httpd]# ls /etc/pki/CA/certs/httpd.crt /etc/pki/CA/certs/httpd.crt [[email protected] httpd]# cp /etc/pki/CA/certs/httpd.crt /etc/httpd/ssl/ [[email protected] httpd]# ls /etc/httpd/ssl/ httpd.crt httpd.csr httpd.key [[email protected] httpd]# #<VirtualHost _default_:443> <VirtualHost 192.168.11.125:443> # General setup for the virtual host #DocumentRoot "/usr/local/apache/htdocs" #ServerName www.example.com:443 #ServerAdmin [email protected] #ErrorLog "/usr/local/apache/logs/error_log" #TransferLog "/usr/local/apache/logs/access_log" DocumentRoot "/web/vhosts/www2" ServerName www2.stuX.com:443 ErrorLog "/var/log/httpd/www2_ssl.err" SSLCertificateFile "/etc/httpd/ssl/httpd.crt" SSLCertificateKeyFile "/etc/httpd/ssl/httpd.key" ##启用ssl模块 LoadModule ssl_module modules/mod_ssl.so 6、在LAMP架构中,请分别以php编译成httpd模块形式和php以fpm工作为独立守护进程的方式来支持httpd,列出详细的过程。 LAMP架构中php以模块形式或以fpm模式,LAM都是不变的,因而本文重点关注php的安装方法。 PHP以模块方式运行: 安装php ##解压 [[email protected] setup]# tar xf php-5.6.23.tar.bz2 ##编译 [[email protected] php-5.6.23]# ./configure –prefix=/usr/local/php –with-mysql=mysqlnd –with-openssl –with-mysqli=mysqlnd –enable-mbstring –with-freetype-dir –with-jpeg-dir –with-png-dir –with-zlib –with-libxml-dir=/usr/lib64 –enable-xml –enable-sockets –with-apxs2=/usr/local/apache/bin/apxs –with-mcrypt=/usr/local/libmcrypt –with-config-file-path=/etc –with-config-file-scan-dir=/etc/php.d –with-bz2 –enable-maintainer-zts ##php是以模块方式运行,所以需要在编译时指定apache的apxs2的目录路径 –with-apxs2=/usr/local/apache/bin/apxs ##copy配置文件到/etc目录 ## vim /etc/httpd/httpd.conf ##添加php网页类型 AddType application/x-httpd-php .php AddType application/x-httpd-php-source .phps ##定位至DirectoryIndex index.html 修改为: DirectoryIndex index.php index.html ##重启httpd服务 ##安装phpMyAdmin ##解压phpMyAdmin-4.6.3-all-languages 到 htdoc目录下,创建链接文件 [[email protected] htdocs]# ln -sv phpMyAdmin-4.6.3-all-languages pma ‘pma’ -> ‘phpMyAdmin-4.6.3-all-languages’ ##访问phpMyAdmin进行测试 ##以fpm模式运行 ##解压 [[email protected] setup]# tar xf php-5.6.23.tar.bz2 ##编译 [[email protected] php-5.6.23]#./configure –prefix=/usr/local/php5 –with-mysql=mysqlnd –with-openssl –with-mysqli=mysqlnd –enable-mbstring –with-freetype-dir –with-jpeg-dir –with-png-dir –with-zlib –with-libxml-dir=/usr –enable-xml –enable-sockets –enable-fpm –with-mcrypt –with-config-file-path=/etc –with-config-file-scan-dir=/etc/php.d –with-bz2 ##以fpm模式运行,使能fpm选项,–enable-fpm, –with-apxs2一项就不需要启用了 [[email protected] php-5.6.23]#make [[email protected] php-5.6.23]#make install ##copy配置文件到/etc目录 [[email protected] php-5.6.23]# cp php.ini-production /etc/php.ini ##php-fpm配置文件,取消pid的注释 [[email protected] etc]# cp /usr/local/php5/etc/php-fpm.conf.default /usr/local/php5/etc/php-fpm.conf pid = /usr/local/php5/var/run/php-fpm.pid ## [[email protected] fpm]# cp php-fpm.service /lib/systemd/system/ ## [[email protected] system]# systemctl enable php-fpm.service Created symlink from /etc/systemd/system/multi-user.target.wants/php-fpm.service to /usr/lib/systemd/system/php-fpm.service. [[email protected] system]# systemctl enable php-fpm.service ##./php-fpm –nodaemonize –fpm-config /usr/local/php5/etc/php-fpm.conf ##更改httpd.conf配置文件,取消proxy_module及proxy_fcgi_module的注释 LoadModule proxy_module modules/mod_proxy.so LoadModule proxy_fcgi_module modules/mod_proxy_fcgi.so AddType application/x-httpd-php .php AddType application/x-httpd-php-source .phps ##重启httpd服务即可
8、建立samba共享,共享目录为/data,要求:(描述完整的过程)
1)共享名为shared,工作组为magedu;
2)添加组develop,添加用户gentoo,centos和ubuntu,其中gentoo和centos以develop为附加组,ubuntu不属于develop组;密码均为用户名;
3)添加samba用户gentoo,centos和ubuntu,密码均为“mageedu”;
4)此samba共享shared仅允许develop组具有写权限,其他用户只能以只读方式访问;
5)此samba共享服务仅允许来自于172.16.0.0/16网络的主机访问;
先添加用户并创建密码x‘z
[[email protected] ~]# groupadd develop [[email protected] ~]# useradd -G develop gentoo [[email protected] ~]# useradd -G develop centos [[email protected] ~]# useradd ubuntu [[email protected] ~]# echo "gentoo" | passwd --stdin gentoo 更改用户 gentoo 的密码 。 passwd: 所有的身份验证令牌已经成功更新。 [[email protected] ~]# echo "centos" | passwd --stdin centos 更改用户 centos 的密码 。 passwd: 所有的身份验证令牌已经成功更新。 [[email protected] ~]# echo "ubuntu" | passwd --stdin ubuntu 更改用户 ubuntu 的密码 。 passwd: 所有的身份验证令牌已经成功更新。 [[email protected] ~]# smbpasswd -a gentoo New SMB password: Retype new SMB password: Added user gentoo. [[email protected] ~]# smbpasswd -a centos New SMB password: Retype new SMB password: Added user centos. [[email protected] ~]# smbpasswd -a ubuntu New SMB password: Retype new SMB password: Added user ubuntu.
安装samba服务
[[email protected] ~]# yum -y install samba samba-client
然后编辑/etc/samba/smb.conf
[[email protected] ~]# vim /etc/samba/smb.conf workgroup = mageedu hosts allow = 192.168.11.125 [shared] comment = smb path = /data guest = yes writable =no write list = +develop
然后使用service smb restart重启服务
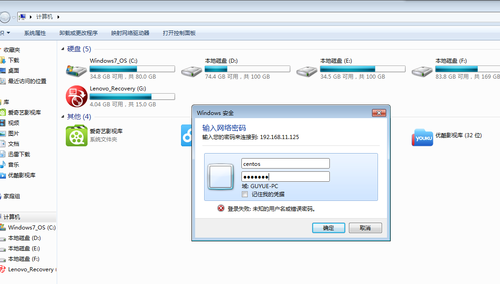
使用windows登录,用有权限的用户centos登录,并创建一个文件
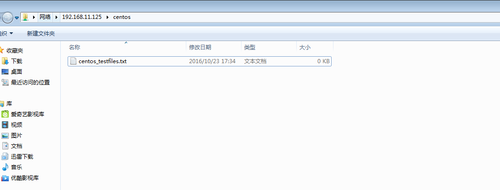
进入共享的/data文件夹,查看刚才在windows系统上创建的文件,存在,说明没有问题
[[email protected] ~]# cd /data [[email protected] data]# ll 总用量 0 -rwxr--r--. 1 centos centos 0 10月 23 17:34 centos_testfiles.txt
如果是使用linux访问的话,使用命令
[[email protected] data]# smbclient //192.168.11.125/centos -U ubuntu Enter ubuntu‘s password: Domain=[MYGROUP] OS=[Unix] Server=[Samba 3.6.23-35.el6_8] smb: \> put /etc/issue NT_STATUS_OBJECT_PATH_NOT_FOUND opening remote file \/etc/issue smb: \> ls . D 0 Sat Oct 23 17:30:22 2016 .. DR 0 Sat Oct 23 17:30:21 2016 centos_testfiles.txt A 0 Sat Oct 23 17:34:12 2016 57807 blocks of size 524288. 51165 blocks available
9、搭建一套文件vsftp文件共享服务,共享目录为/ftproot,要求:(描述完整的过程)
1)基于虚拟用户的访问形式;
2)匿名用户只允许下载,不允许上传;
3)禁锢所有的用户于其家目录当中;
4)限制最大并发连接数为200:;
5)匿名用户的最大传输速率512KB/s
6)虚拟用户的账号存储在mysql数据库当中。
7)数据库通过NFS进行共享。
一、 数据库nfs的共享 在192.168.11.125服务器上安装nfs服务,设置共享目录为nfshare [[email protected] ~]# yum install nfs-utils-1.2.3-39.el6.x86_64.rpm [[email protected] ~]# mkdir /nfshare 创建mysql用户,设置 /nfshare 的所属主,所属组为mysql [[email protected] ~]# groupadd –g 505 mysql [[email protected] ~]# useradd –g 505 –u 505 –s /sbin/nologin –M mysql [[email protected] ~]# chown -R mysql.mysql /nfshare 配置nfs的共享配置文件/etc/exports,/nfshare共享给制定的服务器 /nfshare 192.168.11.124/255.255.255.0(no_root_squash,rw) 启动nfs [[email protected] ~]# service nfs start 在192.168.194.128服务器上安装mysql,创建目录/mydata 用来挂载nfs共享目录。 [[email protected] ~]# yum –y install –y mysql mysql-server mysql-devel 创建mysql用户,设置 /mydata的所属主,所属组为mysql [[email protected] ~]# groupadd –g 505 mysql [[email protected] ~]# useradd –g 505 –u 505 –s /sbin/nologin –M mysql [[email protected] ~]# chown -R mysql.mysql /mydata 挂载nfs共享目录 [[email protected] ~]# mount 192.168.194.125:/nfshare /mydata 修改mysql的配置文件,制定datadir的位置为/mydata [[email protected] ~]# vim /etc/my.cnf [mysqld] datadir=/mydata socket=/var/lib/mysql/mysql.sock user=mysql symbolic-links=0 [mysqld_safe] log-error=/var/log/mysqld.log pid-file=/mydata/mysqld.pid 初始化mysql [[email protected] ~]# mysql_install_db –datadir=/mydata 启动mysql [[email protected] ~]# service mysqld start 二、 vsftp文件共享服务 在192.168.11.124服务器上 创建数据库 mysql> create database vsftpd; 创建数据库用户,授权对vsftpd数据库有查询权限 mysql> grant select on vsftpd.* to [email protected] identified by ‘magedu‘; mysql> grant select on vsftpd.* to [email protected] identified by ‘magedu‘; mysql> flush privileges; 在vsftpd数据库中创建表users mysql> use vsftpd Database changed mysql> create table users (id int AUTO_INCREMENT NOT NULL,name char(20) binary NOT NULL,password char(48) binary NOT NULL,primary key(id)); Query OK, 0 rows affected (0.03 sec) mysql> select * from users; Empty set (0.00 sec) 插入虚拟用户名magedu1,密码magedu mysql> insert into users(name,password) values(‘magedu1‘,password(‘magedu‘)); Query OK, 1 row affected (0.00 sec) mysql> select * from users; +----+---------+-------------------------------------------+ | id | name| password | +----+---------+-------------------------------------------+ | 1 | magedu1 | *6B8CCC83799A26CD19D7AD9AEEADBCD30D8A8664 | +----+---------+-------------------------------------------+ 1 row in set (0.00 sec) 安装开发环境 [[email protected] ~]# yum -y groupinstall "Development Tools" "Server Platform Development" 安装vsftp: yum -y install vsftpd pam-devel openssl-devel 安装pam_mysql [[email protected] ~]# tar xf pam_mysql-0.7RC1.tar.gz [[email protected] ~]# cd pam_mysql-0.7RC1 [[email protected] pam_mysql-0.7RC1]# ./configure --with-mysql=/usr --with-openssl=/usr --with-pam=/usr --with-pam-mods-dir=/lib64/security [[email protected] pam_mysql-0.7RC1]# make && make install [[email protected] pam_mysql-0.7RC1]# ls /lib64/security 查看pm_msyql_so 模式是否安装成功 建立pam认证所需文件 [[email protected] ~]# vim /etc/pam.d/vsftpd.mysql 添加如下两行 auth required /lib64/security/pam_mysql.so user=vsftpd passwd=magedu host=192.168.11.124 db=vsftpd table=users usercolumn=name passwdcolumn=password crypt=2 account required /lib64/security/pam_mysql.so user=vsftpd passwd=magedu host=192.168.11.124 db=vsftpd table=users usercolumn=name passwdcolumn=password crypt=2 建立虚拟用户映射的系统用户及对应的目录 [[email protected] ~]# useradd -s /sbin/nologin -d /ftproot vuser [[email protected] ~]# chmod go+rx /ftproot 修改ftp配置 [[email protected] ~]# vim /etc/vsftpd/vsftpd.conf anonymous_enable=YES #启用匿名用户访问 local_enable=NO write_enable=NO dirmessage_enable=YES xferlog_enable=YES connect_from_port_20=YES xferlog_std_format=YES listen=YES download_enable=YES #允许下载 max_clients=50 #最大并发客户端数目 anon_max_rate=512k #最大下载速率 pam_service_name=vsftpd userlist_enable=YES #针对系统用户访问的控制策略 tcp_wrappers=YES [[email protected] pub]# ftp 127.0.0.1 Connected to 127.0.0.1 (127.0.0.1). 220 (vsFTPd 2.2.2) Name (127.0.0.1:root): anonymous 331 Please specify the password. Password: 230 Login successful. Remote system type is UNIX. Using binary mode to transfer files. ftp> mkdir test 550 Permission denied. ftp> mget index.html mget index.html? y 227 Entering Passive Mode (127,0,0,1,80,144). 150 Opening BINARY mode data connection for index.html (0 bytes). 226 Transfer complete. 重启ftp 服务 service vsftpd restart 在192.168.11.125服务器上测试 [[email protected] ~]# ftp 192.168.11.124 Connected to 192.168.194.124 (192.168.11.124). 220 (vsFTPd 2.2.2) Name (192.168.11.124:root): magedu1 331 Please specify the password. Password: 230 Login successful. Remote system type is UNIX. Using binary mode to transfer files. 匿名用户vsftp的默认根目录为 /var/ftp/ 更多指令请man vsftpd.conf率
以上是关于2016-10-23 第九周作业的主要内容,如果未能解决你的问题,请参考以下文章