[Notes] AWS Automation using script and AWS CLI
Posted
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了[Notes] AWS Automation using script and AWS CLI相关的知识,希望对你有一定的参考价值。
(c) 2014 Amazon Web Services, Inc. and its afflialtes, All rights reserved.
The content in this file is copied from qwikLABS
Please respect the rights.
Putty: a Secure Shell(SSH) client that will provide a command-line interface to my Linux EC2 instance.
http://the.earth.li/~sgtatham/putty/latest/x86/putty.exe
Discover my own public IP address:
Amazon Elastic Compute Cloud (Amazon EC2) provides scalable computing capacity in the AWS cloud. Using Amazon EC2 eliminates your need to invest in hardware upfront, so you can develop and deploy applications faster. You can use Amazon EC2 to launch as many virtual machines as you need, configure security and networking, and manage storage.
Amazon incurs a charge for every hour that an instance is running. Thus, the easiest way to save money is to turn off instances that are not required.
The <Stopinator> is a simple script that can turn off EC2 instances. It can be triggered by CRON(Linux) or Scheduled Task (Windows) and if it finds a specific tag, it either stops or terminates them.
(The following file should be run in a EC2 Linux instance.)
- Stopinator.py
import boto.ec2, os
# Connect to EC2 in this region
region = os.environ.get(‘EC2_REGION’)
connection = boto.ec2.connect_to_region(region)
# Get a list of all instances
reservations = connection.get_all_instance()
# Loop through each instance
for r in reservavtions:
for i in r.instances:
# Check for the ‘stopinator’ tag on running instances
if ‘ stopinator’ in i.tags.keys():
action = i.tags[‘stopinator’].lower()
# Stop?
if action == ‘stop’ and i.state == ‘running’:
print “Stopping instance”, i.id
connection.stop_instances([i.id])
# Terminate?
elif action == ‘terminate’ and i.state != ‘terminated’:
print “Terminating instance”, i,id
connection.terminate_instances([i.id])
############CODE TERMINATES#############
Ideas for implementing stopinator:
- Schedule the stopinator to stop machines each evening, to save money
- Mark instances that you want to keep running, then have the stopinator stop only the unknown instances (but don’t terminates them – they might be important)
- Have another instances script that turns on the instances in the morning
- Set different actions for weekdays and weekends
- Use another tag to identify how many hours you want an instance to run, which is ideal for instances you just want to use for an experiments. Schedule the stopinator to run hourly and configure it to terminate instances that run longer than the indicated number of hours.
connection = boto.ec2.connect_to_region(region)
connection.put_metric_data(namespace=”Lab”, name=”highlow”, value=seconds)
While you’re taking this lab, you may have noticed that there’s no prompt for security credentials. You were able to copy data, take snapshots and start/stop instances without having to identify yourself. You were able to copy data, take snapshot and start/stop/terminate instances without having identify yourself. (except when connection, we open PPK for PuTTy and set up the SSH)
Instance Metadata Service
Instance metadata is data about your instance that you can use to configure or manage the running instance. Included in the data is a set of security credentials that was used for all your commands during this lab.
It works as follows:
- A role called scripts was created with appropriate permissions to run the lab.
- The Amazon EC2 instance you have been using was launched with the scripts role.
- The AWS CLI and Python SDK automatically retrieved the security credentials via the Instance Metadata Service.
Run ./show-credentials
A large block of text will appear:
{
“Code” : “Success”
“LastUpdated”: <Time>
“Type” : ”AWS-HMAC”
“AccessKeyId”
“SecretAccessKey”
“Token”
“Expiration”
}
The metadata contains an Access Key and Secret Key, which authorizes the AWS CLI and scripts on your EC2 instance to call AWS services.
- Three ways to acess AWS ~ CLI, browser management, Programming (Py, Ruby…)
- Access Amazon S3, copy and paste
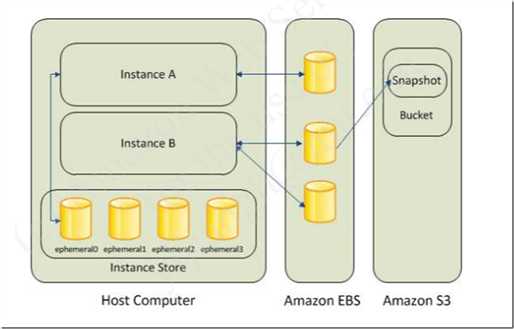
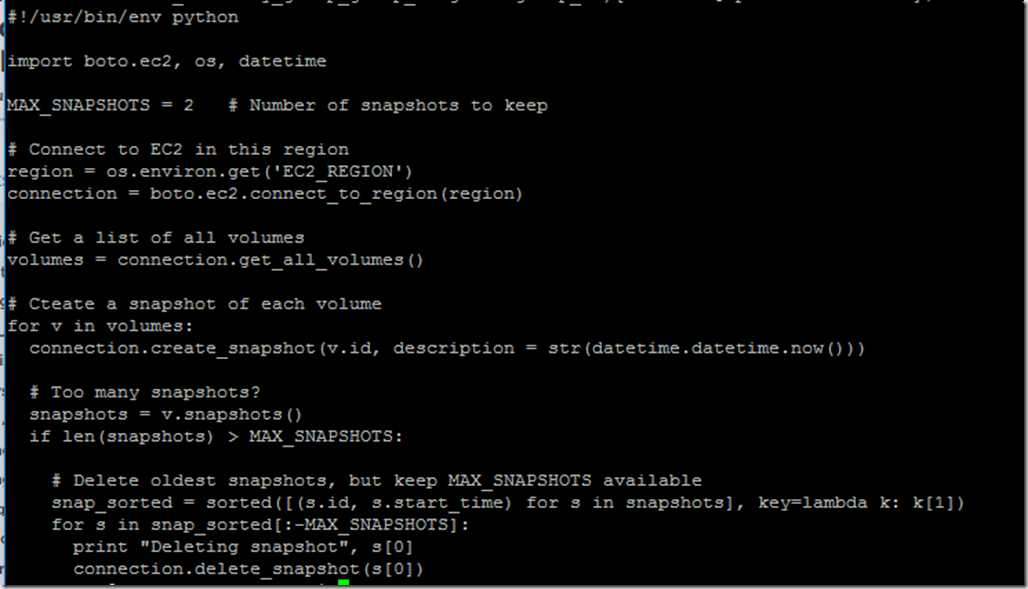
- Automate EBS snapshot
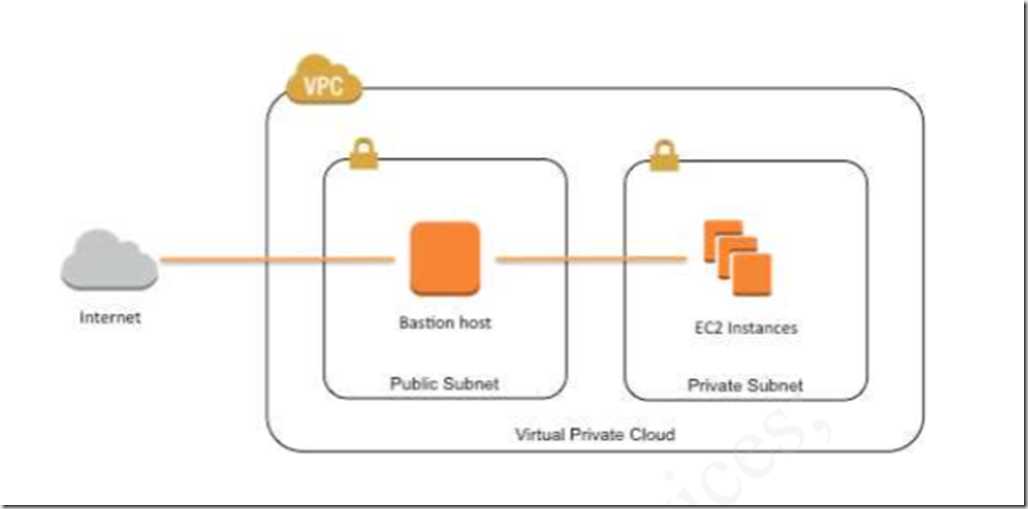
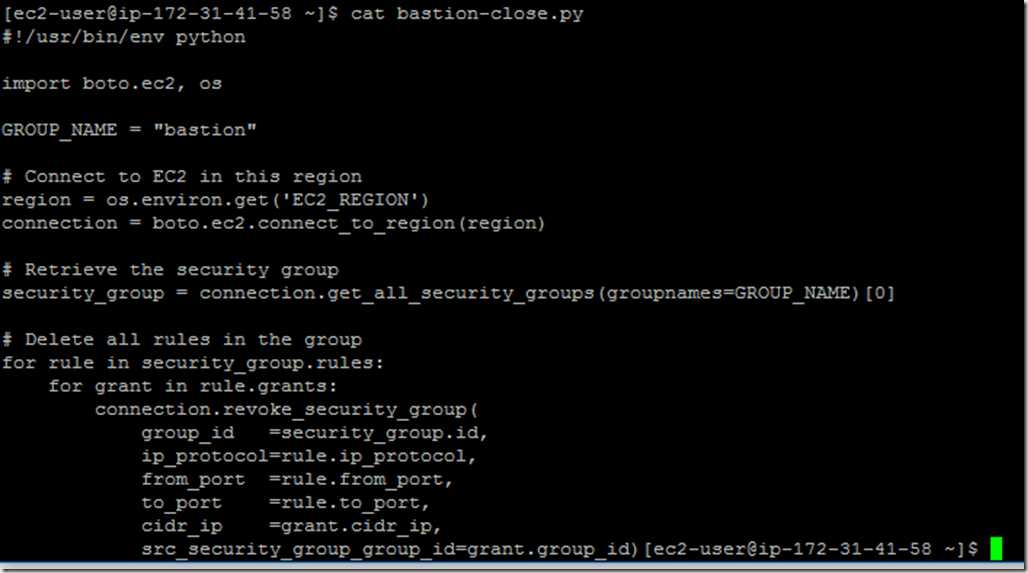
- Automate Bastion security
- Automate CloudWatch Metrics
以上是关于[Notes] AWS Automation using script and AWS CLI的主要内容,如果未能解决你的问题,请参考以下文章
Enable Azure Disk Encryption for Windows Notes