登录触发器之控制IP与用户登录记录登录日志
Posted 低级程序人员
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了登录触发器之控制IP与用户登录记录登录日志相关的知识,希望对你有一定的参考价值。
USE [Logon_DB]
GO
/****** Object: Table [dbo].[LogonLog] Script Date: 2016/9/10 17:24:11 ******/
SET ANSI_NULLS ON
GO
SET QUOTED_IDENTIFIER ON
GO
SET ANSI_PADDING ON
GO
CREATE TABLE [dbo].[LogonLog](
[Id] [int] IDENTITY(1,1) NOT NULL,
[session_id] [smallint] NULL,
[login_time] [datetime] NULL,
[host_name] [nvarchar](128) NULL,
[original_login_name] [nvarchar](128) NULL,
[client_net_address] [varchar](48) NULL,
[XmlEvent] [xml] NULL,
[blocked] [smallint] NULL,
CONSTRAINT [PK_LogonLog1] PRIMARY KEY CLUSTERED
(
[Id] ASC
)WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON) ON [PRIMARY]
) ON [PRIMARY] TEXTIMAGE_ON [PRIMARY]
GO
SET ANSI_PADDING OFF
GO
USE [Logon_DB]
GO
/****** Object: Table [dbo].[ValidLogOn] Script Date: 2016/9/10 17:24:07 ******/
SET ANSI_NULLS ON
GO
SET QUOTED_IDENTIFIER ON
GO
CREATE TABLE [dbo].[ValidLogOn](
[Id] [int] IDENTITY(1,1) NOT NULL,
[LoginName] [sysname] NOT NULL,
[ValidIP] [nvarchar](15) NOT NULL,
CONSTRAINT [PK_ValidLogOn] PRIMARY KEY CLUSTERED
(
[Id] ASC
)WITH (PAD_INDEX = OFF, STATISTICS_NORECOMPUTE = OFF, IGNORE_DUP_KEY = OFF, ALLOW_ROW_LOCKS = ON, ALLOW_PAGE_LOCKS = ON) ON [PRIMARY]
) ON [PRIMARY]
GO
--插入测试数据
INSERT [dbo].[ValidLogOn] ([LoginName], [ValidIP]) VALUES (N\'sa\', N\'192.168.1.200\')
INSERT [dbo].[ValidLogOn] ([LoginName], [ValidIP]) VALUES (N\'heqianjin-PC\\Administrator\', N\'127.0.0.1\')
INSERT [dbo].[ValidLogOn] ([LoginName], [ValidIP]) VALUES (N\'nightworker\', N\'<local machine>\')
INSERT [dbo].[ValidLogOn] ([LoginName], [ValidIP]) VALUES (N\'nightworker\', N\'192.168.1.48\')
INSERT [dbo].[ValidLogOn] ([LoginName], [ValidIP]) VALUES (N\'sa\', N\'<local machine>\')
INSERT [dbo].[ValidLogOn] ([LoginName], [ValidIP]) VALUES (N\'sa\', N\'127.0.0.1\')
--创建登录触发器
-- =============================================
-- Author: <听风吹雨>
-- Create date: <2013.05.21>
-- Description: <登陆名和IP过滤,支持IP范围规范>
-- Blog: <http://www.cnblogs.com/gaizai/>
-- =============================================
CREATE TRIGGER [tr_logon_CheckLogOn_RangeIP]
ON ALL SERVER WITH EXECUTE AS \'sa\'
FOR LOGON
AS
BEGIN
DECLARE @LoginName sysname
DECLARE @IP NVARCHAR(15)
DECLARE @ValidIP NVARCHAR(15)
DECLARE @len INT
DECLARE @data XML
DECLARE @blocked BIT;
SET @len = 0
SET @blocked = 0
SET @LoginName = ORIGINAL_LOGIN();
SET @data = EVENTDATA();
SET @IP = @data.value(\'(/EVENT_INSTANCE/ClientHost)[1]\', \'NVARCHAR(15)\');
--判断登录名和IP
IF NOT EXISTS(SELECT [ValidIP] FROM [Logon_DB].[dbo].[ValidLogOn] WHERE [LoginName] = @LoginName AND [ValidIP] = @IP)
BEGIN
--是否存在IP范围匹配
SET @ValidIP = (SELECT TOP 1 [ValidIP] FROM [Logon_DB].[dbo].[ValidLogOn]
WHERE [LoginName] = @LoginName AND [ValidIP] LIKE \'%[*]\');
--如果存在就替换Client的IP
IF (CHARINDEX(\'*\',@ValidIP) > 0 AND @IP <> \'<local machine>\' AND @IP <> \'127.0.0.1\')
BEGIN
DECLARE @SubValidIP NVARCHAR(15)
SET @SubValidIP = SUBSTRING(@ValidIP,0,CHARINDEX(\'*\',@ValidIP))
SET @len = LEN(@SubValidIP) + 1
IF(SUBSTRING(@IP,0,@len) != @SubValidIP)
BEGIN
ROLLBACK;
SET @blocked = 1
END
END
ELSE
BEGIN
ROLLBACK;
SET @blocked = 1
END
END
--日志记录
INSERT INTO [Logon_DB].[dbo].[LogonLog]
([session_id]
,[login_time]
,[host_name]
,[original_login_name]
,[client_net_address]
,[XmlEvent]
,[Blocked])
SELECT
@data.value(\'(/EVENT_INSTANCE/SPID)[1]\', \'smallint\'),
GETDATE(),
@data.value(\'(/EVENT_INSTANCE/ServerName)[1]\', \'sysname\'),
@data.value(\'(/EVENT_INSTANCE/LoginName)[1]\', \'sysname\'),
@data.value(\'(/EVENT_INSTANCE/ClientHost)[1]\', \'NVARCHAR(15)\'),
@data,@blocked
END;
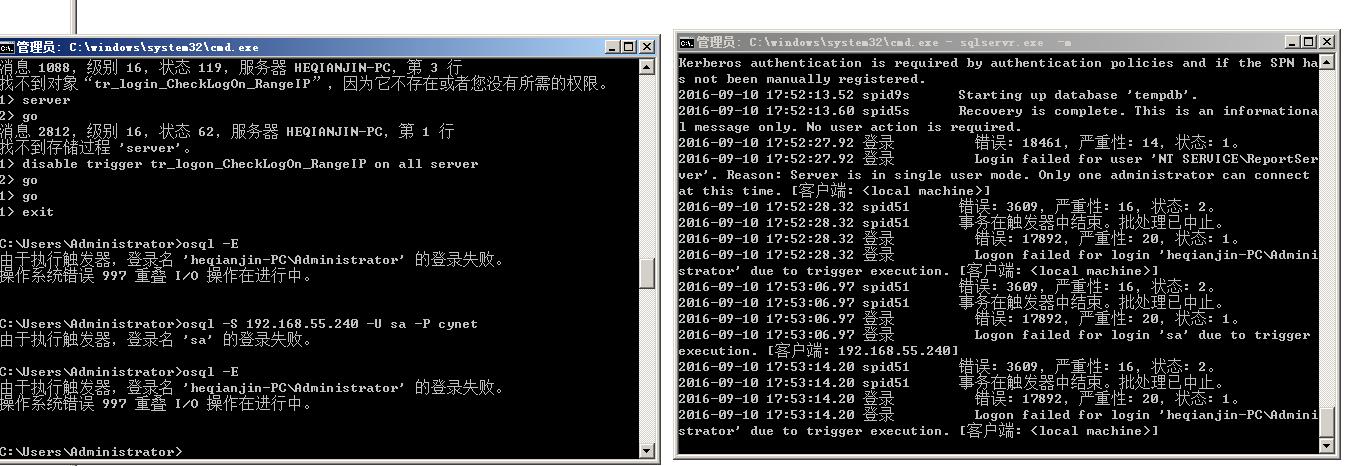
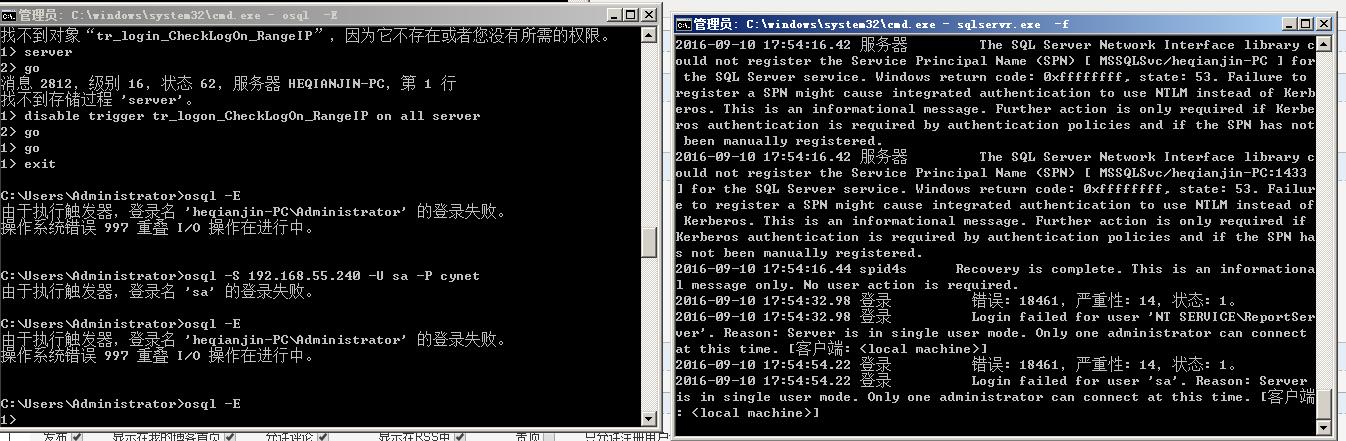
----以上只是记录本人的工作学习记录,仅供参考,所有的东西都是来自互联网,如有侵犯片权请联系我删除。
---请测试出现问题,后果自负。
----如果运行了这个触发器,登录不了。
---可以用sqlcmd -f参数运行数据库,再用osql连上数据库,把触发器禁用即可。(用sqlcmd运行的时候先禁用mssql服务)
---- -m是不行的!!!!
-f
以上是关于登录触发器之控制IP与用户登录记录登录日志的主要内容,如果未能解决你的问题,请参考以下文章